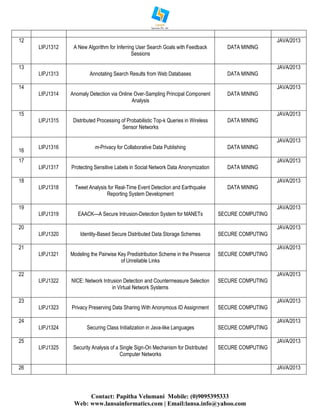
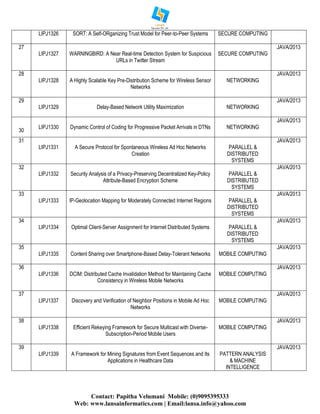
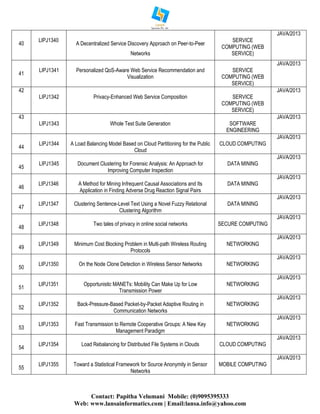
The document lists various IEEE projects from the years 2013-2014, focusing on multiple domains such as cloud computing, data mining, secure computing, networking, mobile computing, and service computing. Each project is identified with a unique code and title, along with the programming language used, which is predominantly Java. Additionally, it provides contact information for project support services offered by Lansa Informatics, including publication assistance and placement support.