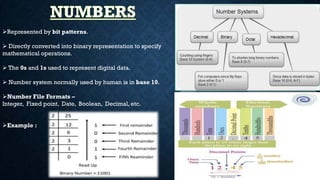
This document discusses data representation in computer networks. It defines data and describes how all data inside computers must be converted to binary form to be processed. It then discusses various forms of data representation including numbers, text, images, audio and video. The document outlines goals of understanding how data is represented and converted to machine language for numbers and text. It provides examples of binary representation of numbers and the ASCII code for representing text characters. Finally, it discusses calculating file sizes based on the number of ASCII characters.