[Infographic] 2019: ENTERPRISE MOBILITY TRENDS, CHALLENGES & THE WAY FORWARD
•
0 likes•51 views
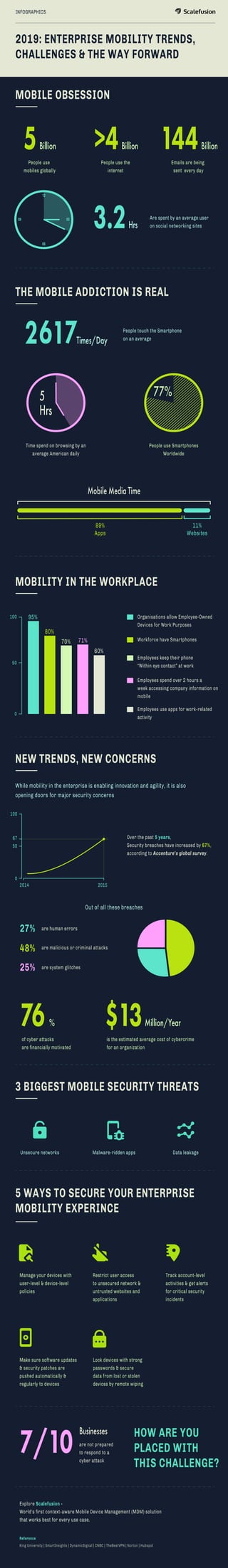
Mobile device usage is ubiquitous, with over 5 billion people using mobiles globally. The average user spends 3.2 hours on social networking sites per day and touches their smartphone over 2,500 times per day. Many organizations now allow employee-owned devices to be used for work purposes, but this brings new security challenges as mobility opens doors for cyber attacks. Common mobile security threats include unsecure networks, malware-ridden apps, and data leakage.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
How Aligned Are IT, Employees and Security Practices in Today's Mobile World?

How Aligned Are IT, Employees and Security Practices in Today's Mobile World?
Mobile Security: The 5 Questions Modern Organizations Are Asking

Mobile Security: The 5 Questions Modern Organizations Are Asking
Internet of Things - Desire for Convenience Brings Multiple New Attack Vectors

Internet of Things - Desire for Convenience Brings Multiple New Attack Vectors
Primend Pilvekonverents - Mobiilne ettevõte mobiilsete andmetega

Primend Pilvekonverents - Mobiilne ettevõte mobiilsete andmetega
Similar to [Infographic] 2019: ENTERPRISE MOBILITY TRENDS, CHALLENGES & THE WAY FORWARD
Similar to [Infographic] 2019: ENTERPRISE MOBILITY TRENDS, CHALLENGES & THE WAY FORWARD (20)
Infographic: Mobile is growing and so are security threats

Infographic: Mobile is growing and so are security threats
The impact of mobile devices on information security

The impact of mobile devices on information security
“The Impact of Mobile Devices on Information Security: A Survey of IT and Sec...

“The Impact of Mobile Devices on Information Security: A Survey of IT and Sec...
Users and behaviors social internet: Safety & Security

Users and behaviors social internet: Safety & Security
Surviving the mobile invasion - They're spreading fast and they're vulnerable

Surviving the mobile invasion - They're spreading fast and they're vulnerable
Adjusting Your Security Controls: It’s the New Normal

Adjusting Your Security Controls: It’s the New Normal
[Infographic] 5 Security Threats in Healthcare Industry ![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] 5 Security Threats in Healthcare Industry
Insightful Research: The State of Mobile Application Insecurity 

Insightful Research: The State of Mobile Application Insecurity
Recently uploaded
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptxnull - The Open Security Community
Recently uploaded (20)
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi

FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi
"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...

"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
Scanning the Internet for External Cloud Exposures via SSL Certs

Scanning the Internet for External Cloud Exposures via SSL Certs
Transcript: New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC BiblioShare - Tech Forum 2024
Vulnerability_Management_GRC_by Sohang Sengupta.pptx

Vulnerability_Management_GRC_by Sohang Sengupta.pptx
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
[Infographic] 2019: ENTERPRISE MOBILITY TRENDS, CHALLENGES & THE WAY FORWARD
- 1. 5Billion Times/Day Billion Billion>4 144People use mobiles globally INFOGRAPHICS 3.2Hrs Are spent by an average user on social networking sites People touch the Smartphone on an average Organisations allow Employee-Owned Devices for Work Purposes Mobile Media Time 100 95% 80% 70% 71% 60% 50 0 People use the internet Emails are being sent every day MOBILE OBSESSION 2019: ENTERPRISE MOBILITY TRENDS, CHALLENGES & THE WAY FORWARD THE MOBILE ADDICTION IS REAL MOBILITY IN THE WORKPLACE NEW TRENDS, NEW CONCERNS 3 BIGGEST MOBILE SECURITY THREATS 5 WAYS TO SECURE YOUR ENTERPRISE MOBILITY EXPERINCE People use Smartphones Worldwide Time spend on browsing by an average American daily 5 Hrs 77% 89% Apps 11% Websites Workforce have Smartphones Employees keep their phone “Within eye contact” at work 27% are human errors 48% are malicious or criminal attacks 25% are system glitches Employees spend over 2 hours a week accessing company information on mobile Employees use apps for work-related activity Over the past 5 years, Security breaches have increased by 67%, according to Accenture’s global survey. Out of all these breaches While mobility in the enterprise is enabling innovation and agility, it is also opening doors for major security concerns 100 20152014 50 67 0 76% of cyber attacks are financially motivated $13Million/Year is the estimated average cost of cybercrime for an organization Unsecure networks Malware-ridden apps Data leakage Manage your devices with user-level & device-level policies Restrict user access to unsecured network & untrusted websites and applications Make sure software updates & security patches are pushed automatically & regularly to devices Explore Scalefusion - World’s first context-aware Mobile Device Management (MDM) solution that works best for every use case. Reference King University | SmartInsights | DynamicSignal | CNBC | TheBestVPN | Norton | Hubspot Track account-level activities & get alerts for critical security incidents Lock devices with strong passwords & secure data from lost or stolen devices by remote wiping 7/10 Businesses are not prepared to respond to a cyber attack HOW ARE YOU PLACED WITH THIS CHALLENGE?
