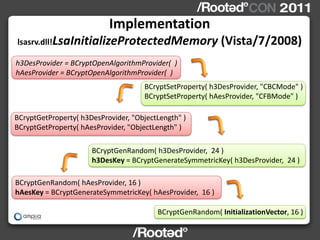
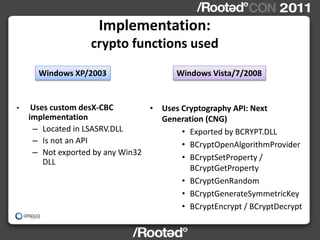
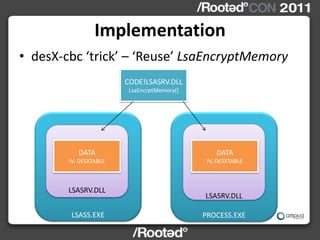
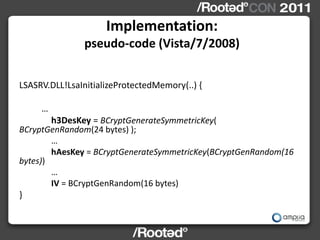
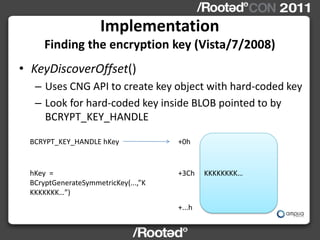
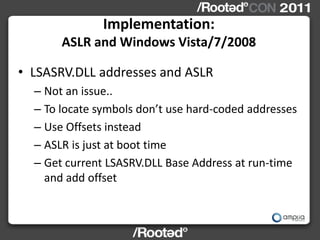
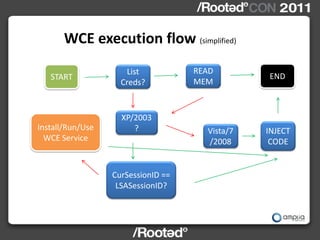
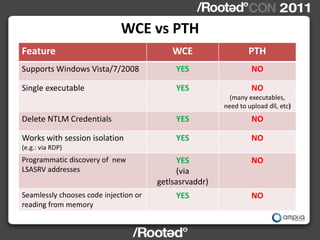
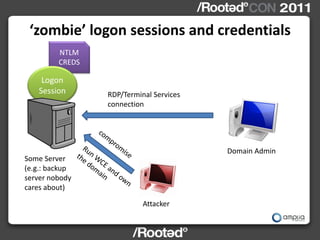
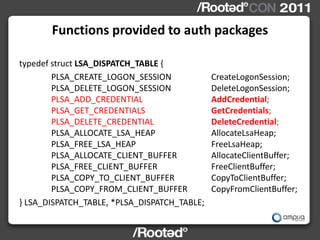
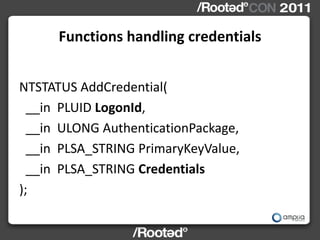
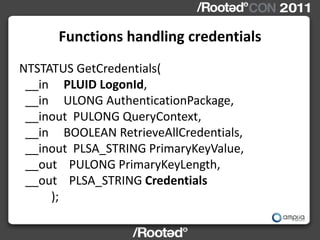
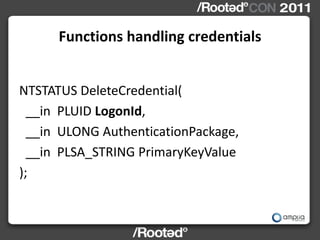
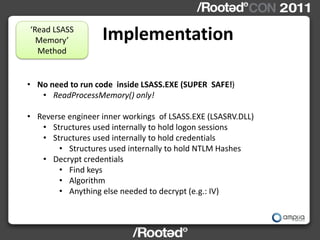
This document describes Windows Credentials Editor (WCE), a tool that can dump and manipulate Windows logon session credentials from memory without requiring code injection. It discusses two implementation methods - using the authentication package API or directly reading LSASS process memory. The memory reading method is safer as it does not require running code in LSASS. It works by reversing the LSASS data structures to find logon sessions and credentials, then decrypting credentials using encryption keys and initialization vectors read from LSASS memory.




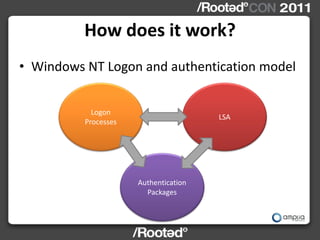
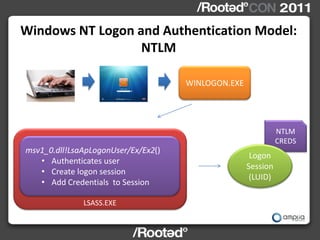
![Windows NT Logon and Authentication Model:
NTLM in detail
WINLOGON.EXE
LUID luid = LsaLogonUser( …,MSV1_0_PACKAGE_ID,… )
msv1_0.dll!LsaApLogonUser/Ex/Ex2()
• Create logon session
• Authenticates against local sam or AD
• msv1_0.dll!NlpAddPrimaryAddCredential(LUID, [username, domain,
LM/NT hashes],…)
• Lsasrv.dll!AddCredential(LUID,…)](https://image.slidesharecdn.com/wceinternalsrootedcon2011ampliasecurity-110307133648-phpapp01/85/Hernan-Ochoa-WCE-Internals-RootedCON-2011-17-320.jpg)
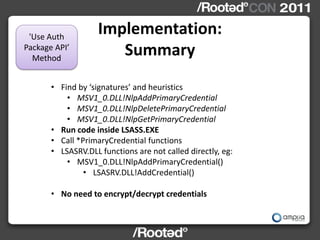
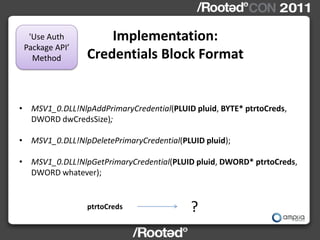
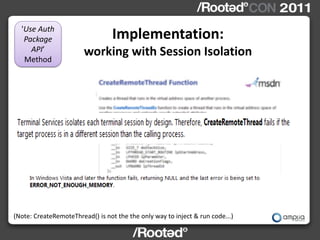
!['Use Auth
Implementation:
Package API’ Credentials Block Format
Method
ptrtoCreds
typedef struct {
UNICODE_STR ustr_domain;
UNICODE_STR ustr_username;
BYTE NThash[16];
BYTE LMhash[16];
BYTE Udomain[MAX_DOMAIN_LEN];
BYTE Uuser[MAX_USERNAME_LEN];
} CREDSBLOCK;](https://image.slidesharecdn.com/wceinternalsrootedcon2011ampliasecurity-110307133648-phpapp01/85/Hernan-Ochoa-WCE-Internals-RootedCON-2011-20-320.jpg)
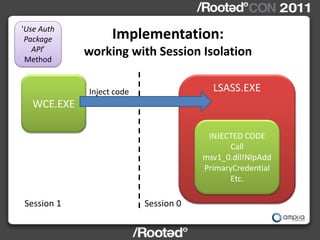

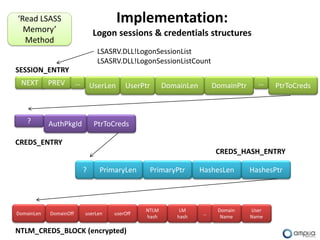
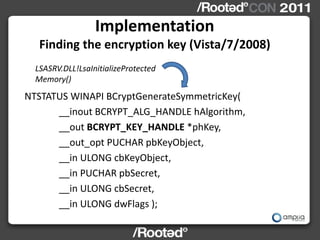
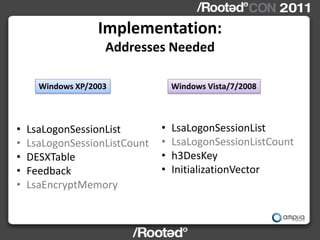
![‘Read LSASS Implementation:
Memory’
Method changes in SESSION_ENTRY
Windows XP/2003 Windows Vista/7/2008
struct SESSION_ENTRY { struct SESSION_ENTRY {
DWORD nextEntry; DWORD nextEntry;
DWORD prevEntry; DWORD prevEntry;
DWORD unk1; DWORD UNKNOWN[18];
DWORD unk2; DWORD userSize;
DWORD userSize; DWORD userNamePtrUnicode;
DWORD machineSize;
DWORD userNamePtrUnicode;
DWORD machinePtrUnicode;
DWORD machineSize;
…
DWORD machinePtrUnicode;
….
+0x48 DWORD PtrToCreds; +0x88 DWORD PtrToCreds;
}; };](https://image.slidesharecdn.com/wceinternalsrootedcon2011ampliasecurity-110307133648-phpapp01/85/Hernan-Ochoa-WCE-Internals-RootedCON-2011-31-320.jpg)
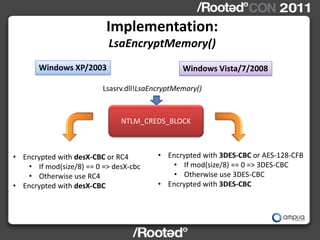
![Implementation
lsasrv.dll!LsaInitializeProtectedMemory (XP/2003)
0 190h
VirtualAlloc()
90h 8 8 8
cbRandomKey = 100h
pDESXTable
pRandomKey
struct DESXTable {
SystemFunction036( byte byte inWhitening[8];
Feedback[8],8) byte outWhitening[8];
DESTable desTable;
}
desxkey( pDESXTable ,
pRandomKey ) struct DESTable {
unsigned long keys[16][2];
}
SystemFunction036(
pRandomKey, cbRandomKey )](https://image.slidesharecdn.com/wceinternalsrootedcon2011ampliasecurity-110307133648-phpapp01/85/Hernan-Ochoa-WCE-Internals-RootedCON-2011-33-320.jpg)