Virus
•Download as PPTX, PDF•
1 like•85 views
virus and types of virus
Report
Share
Report
Share
Recommended
More Related Content
What's hot
What's hot (20)
Presentation Virus (salami attack and trojan horse)

Presentation Virus (salami attack and trojan horse)
Similar to Virus
Similar to Virus (20)
More from preetikapri1
More from preetikapri1 (20)
structures in C and Union in C, enumerated datatype

structures in C and Union in C, enumerated datatype
Recently uploaded
Recently uploaded (20)
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Virus
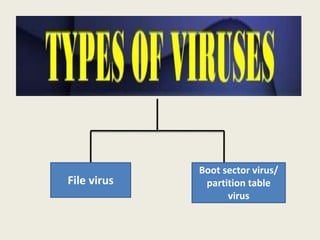
- 1. File virus Boot sector virus/ partition table virus
- 2. 1. File virus • The file virus affects executable programs (.exe) • It replaces a part of original code file with a malicious code, thus destroying the file
- 3. 2. Boot sector virus • The 1st sector of the outermost track in floppy disk contained a small program known as bootstrap loader program. • when computer was switched on, this program used to load OS from floppy disk to the main memory of the computer. • A boot sector virus substitutes itself for bootstrap loader. Virus gets automatic loaded into main memory. • Once loaded it starts affecting all files on disk.
- 6. 1. Trojan Horse: damages files by merging unwarranted program code with authorized programs. 2. Worms: this program duplicates its own code. 3. Salami techniques: robs small amount of money from user account and user remains unaware. 4. Eaves Dropping: allows a person to observe some message transmitted to other people.
- 7. 5. Wire tapping: it has special transmission path to divert flow of data from original user to unauthorized user. 6. Stealth virus: these virus avoids self detection by antivirus. 7. Logic bombs: these cause computer to malfunction. 8. Data diddling: performs unauthorized modifications of data and user is not aware of it.
- 8. Antivirus software are computer programs that attempt to identify, neutralize or eliminate malicious software.