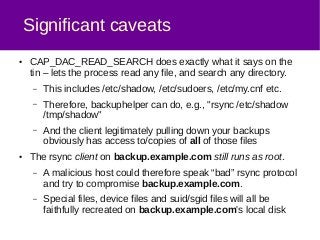
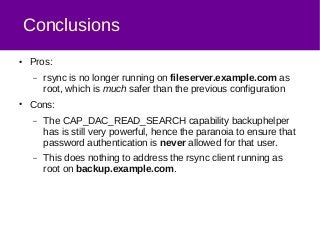
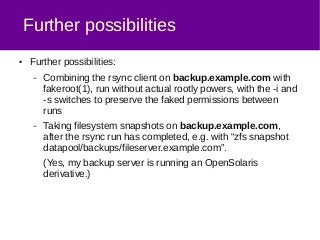
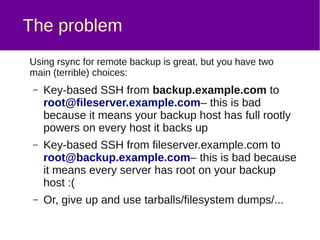
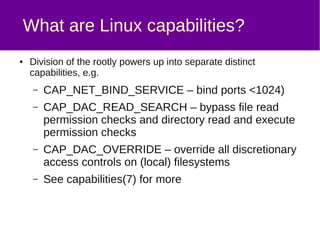
The document discusses a method for securely backing up a filesystem using rsync over SSH without granting root access, implementing a user called 'backuphelper' with specific filesystem capabilities. It covers configurations and the use of PAM modules to allow 'backuphelper' to perform backups while limiting potential security risks. The document also addresses precautions and considerations regarding the powerful capabilities granted to the 'backuphelper' user and the risks associated with running rsync on the backup host as root.






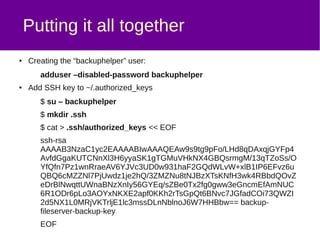

![Putting it all together
● Adding pam_cap.so to /etc/pam.d/common-auth:
auth [success=1 default=ignore] pam_unix.so nullok_secure
auth requisite pam_deny.so
auth required pam_permit.so
auth required pam_cap.so](https://image.slidesharecdn.com/rsyncsetcap-150207083952-conversion-gate01/85/Using-filesystem-capabilities-with-rsync-11-320.jpg)