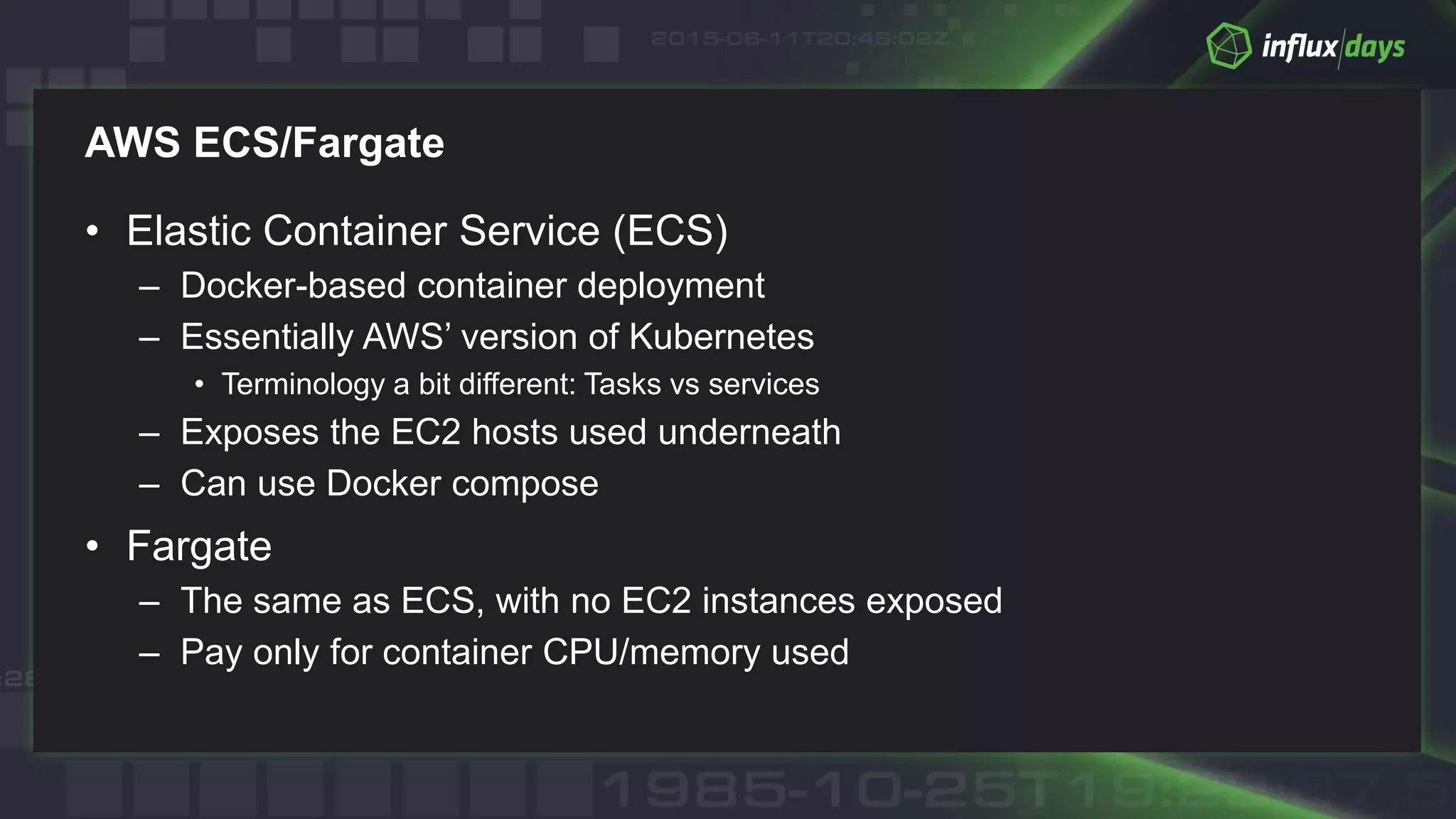
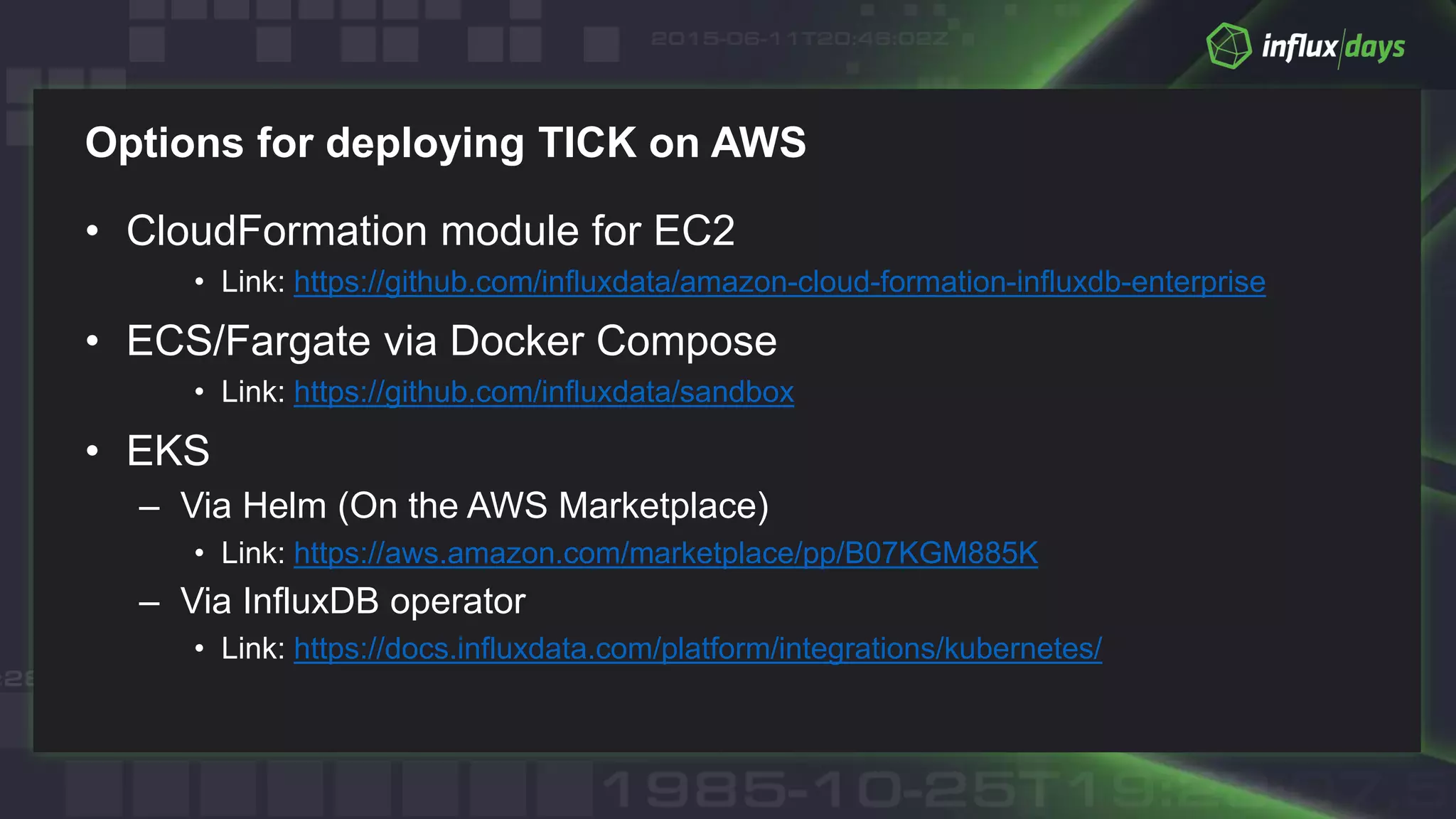
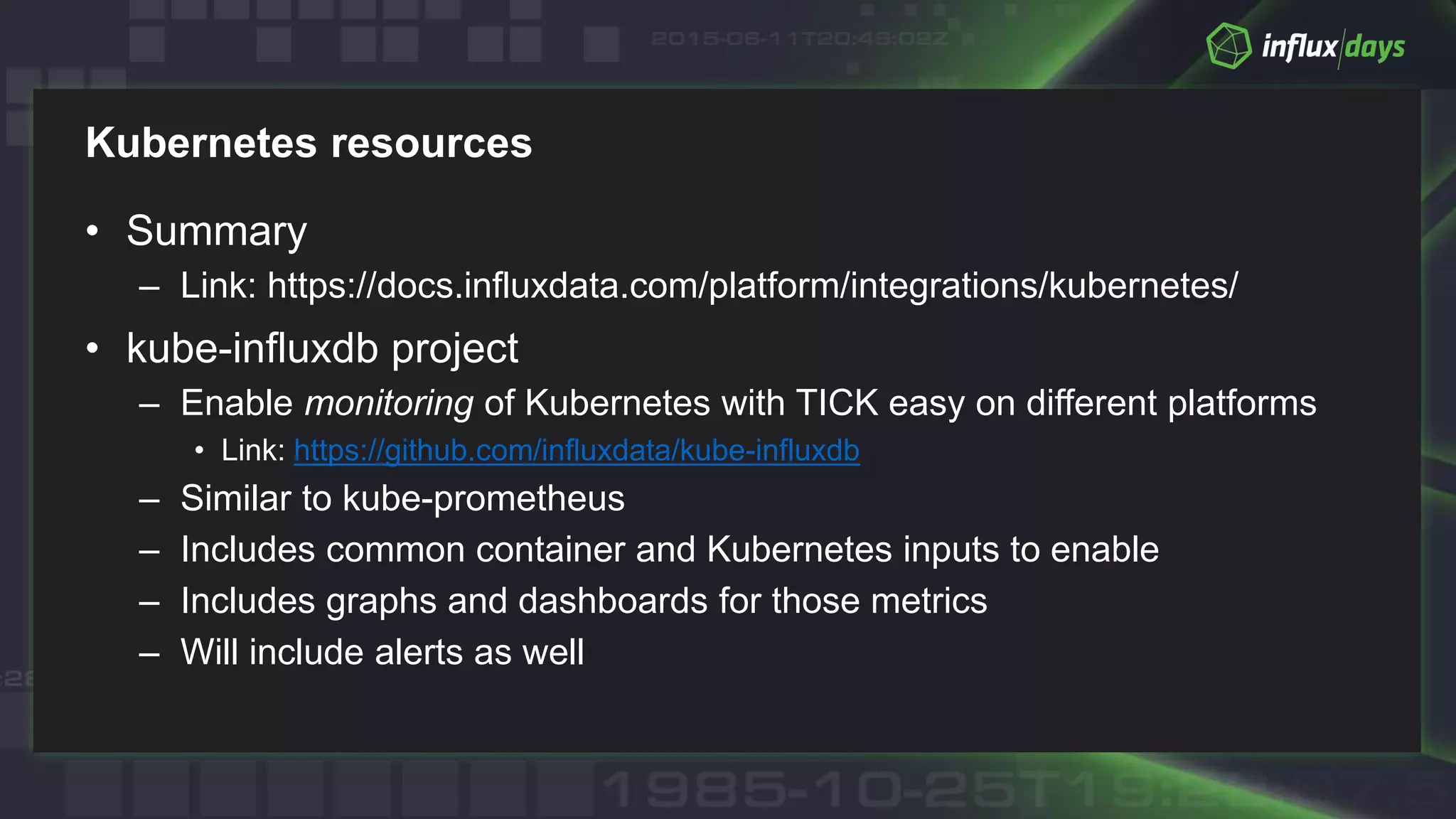
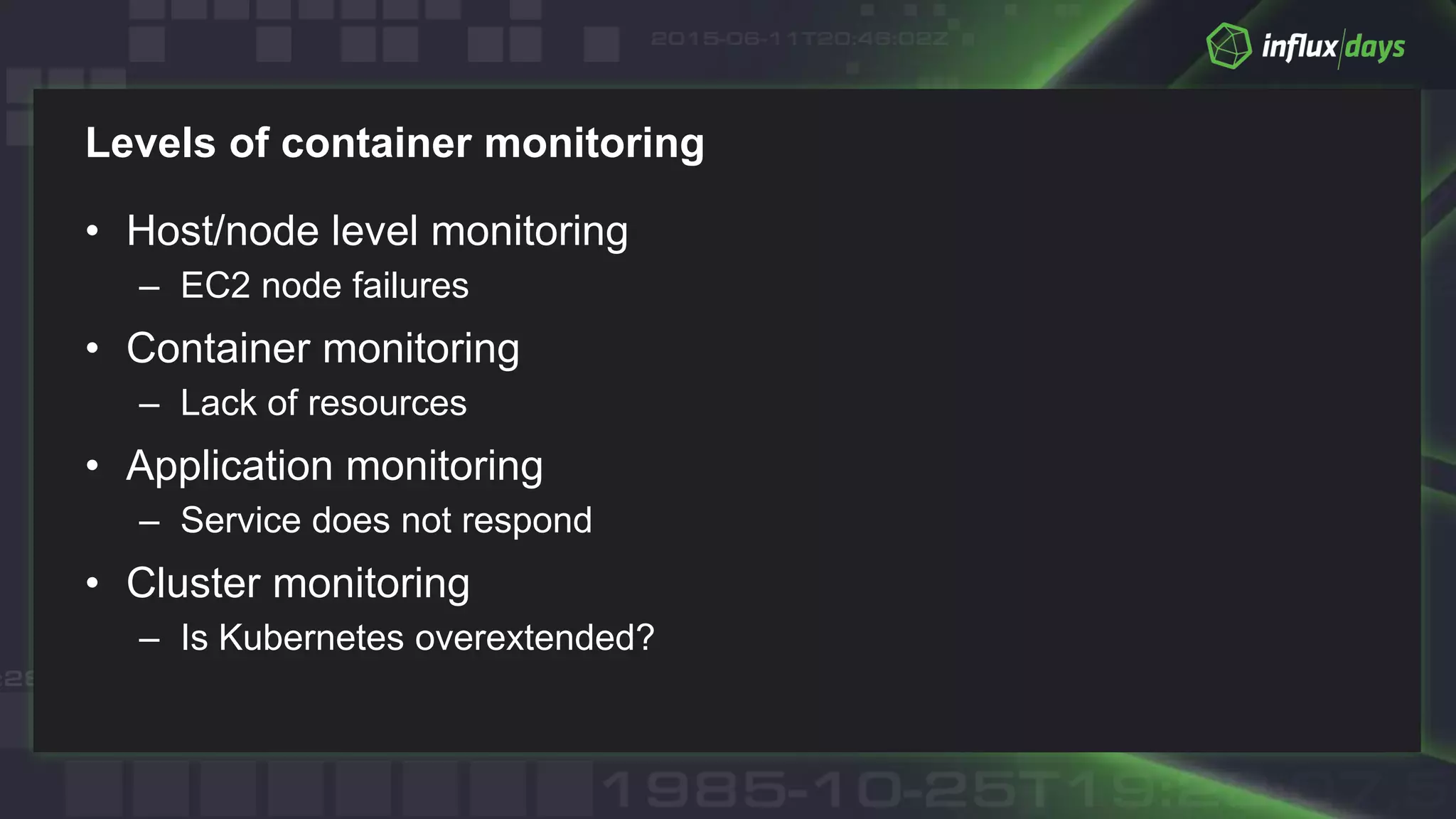
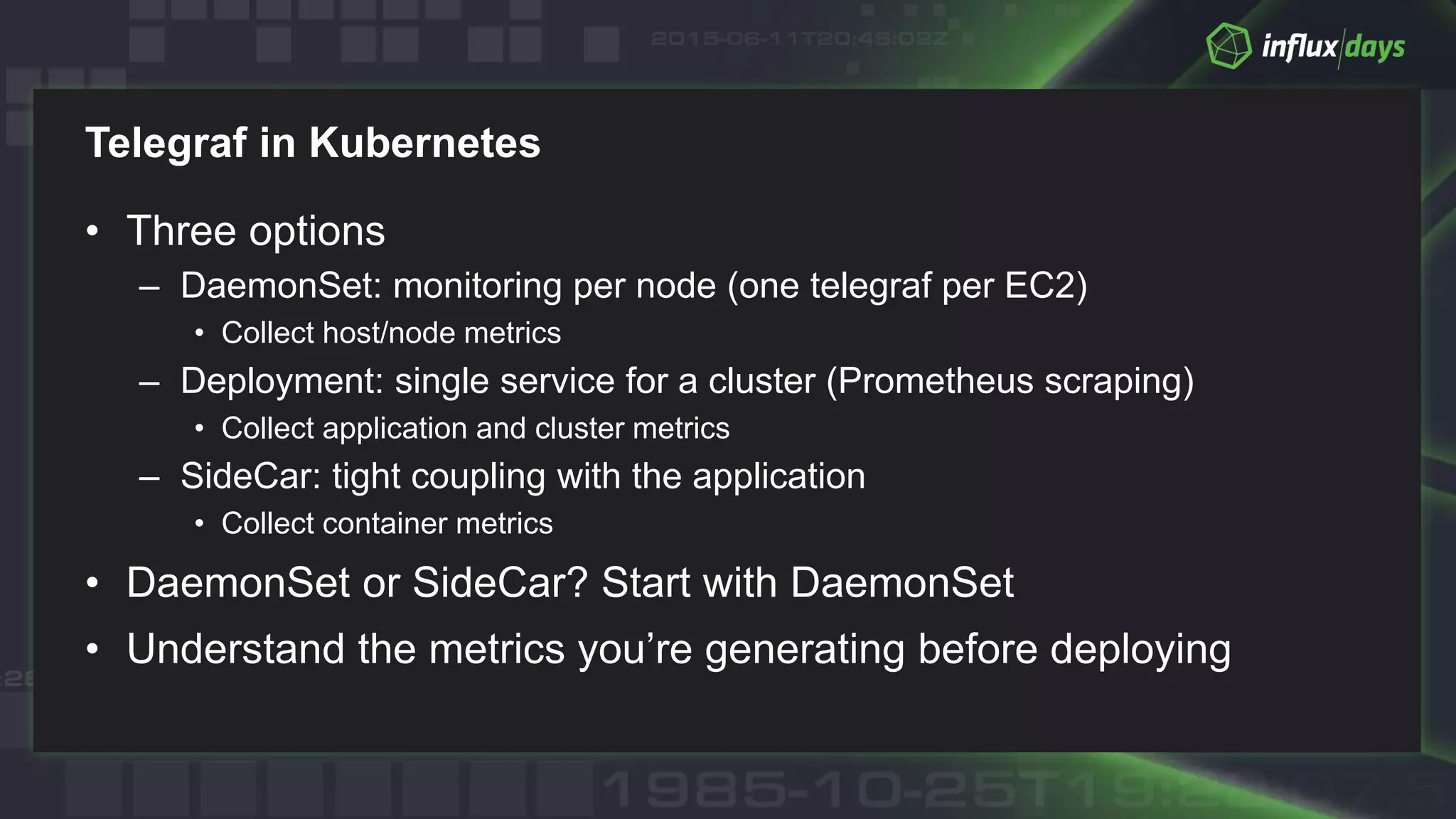
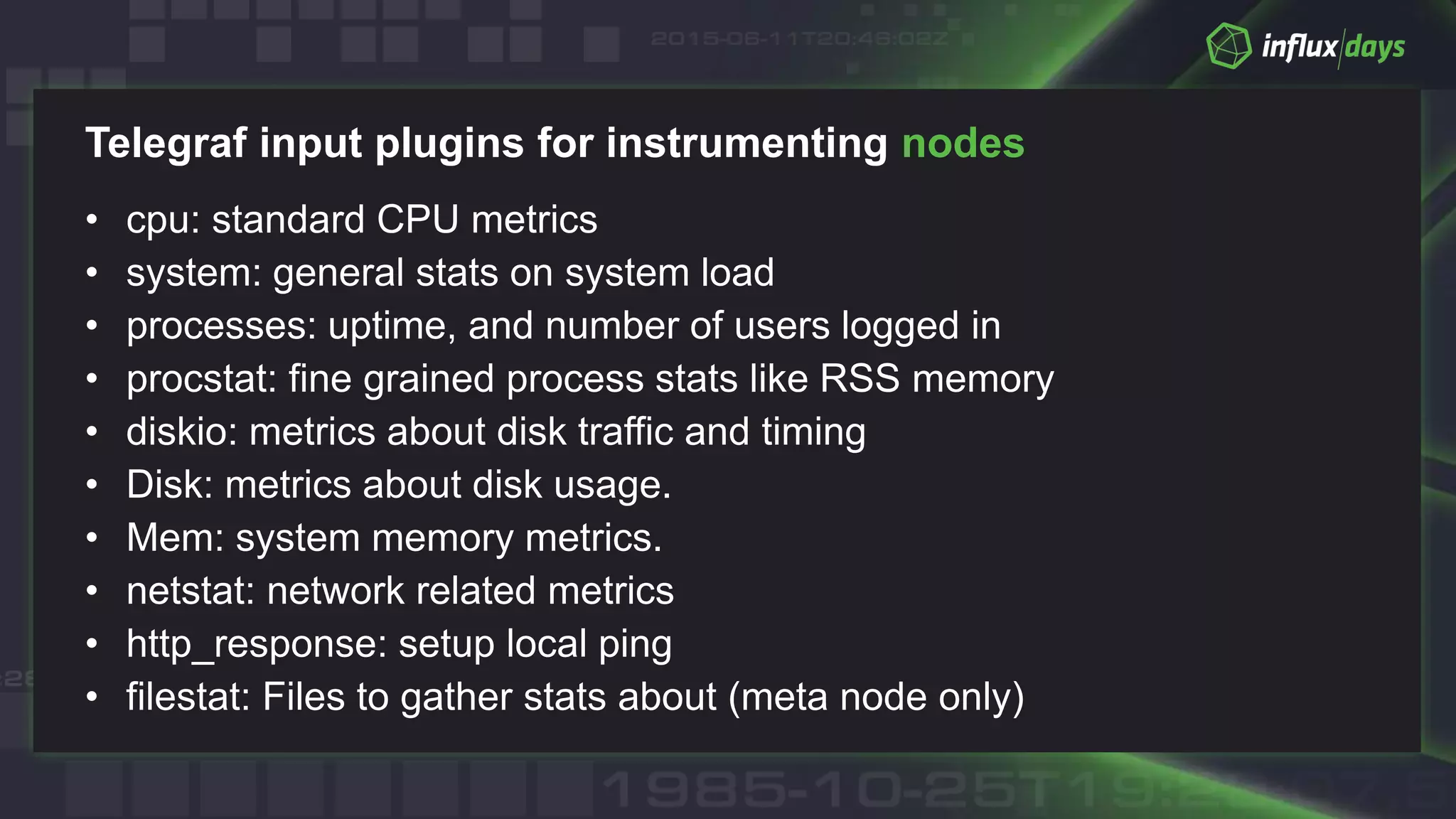
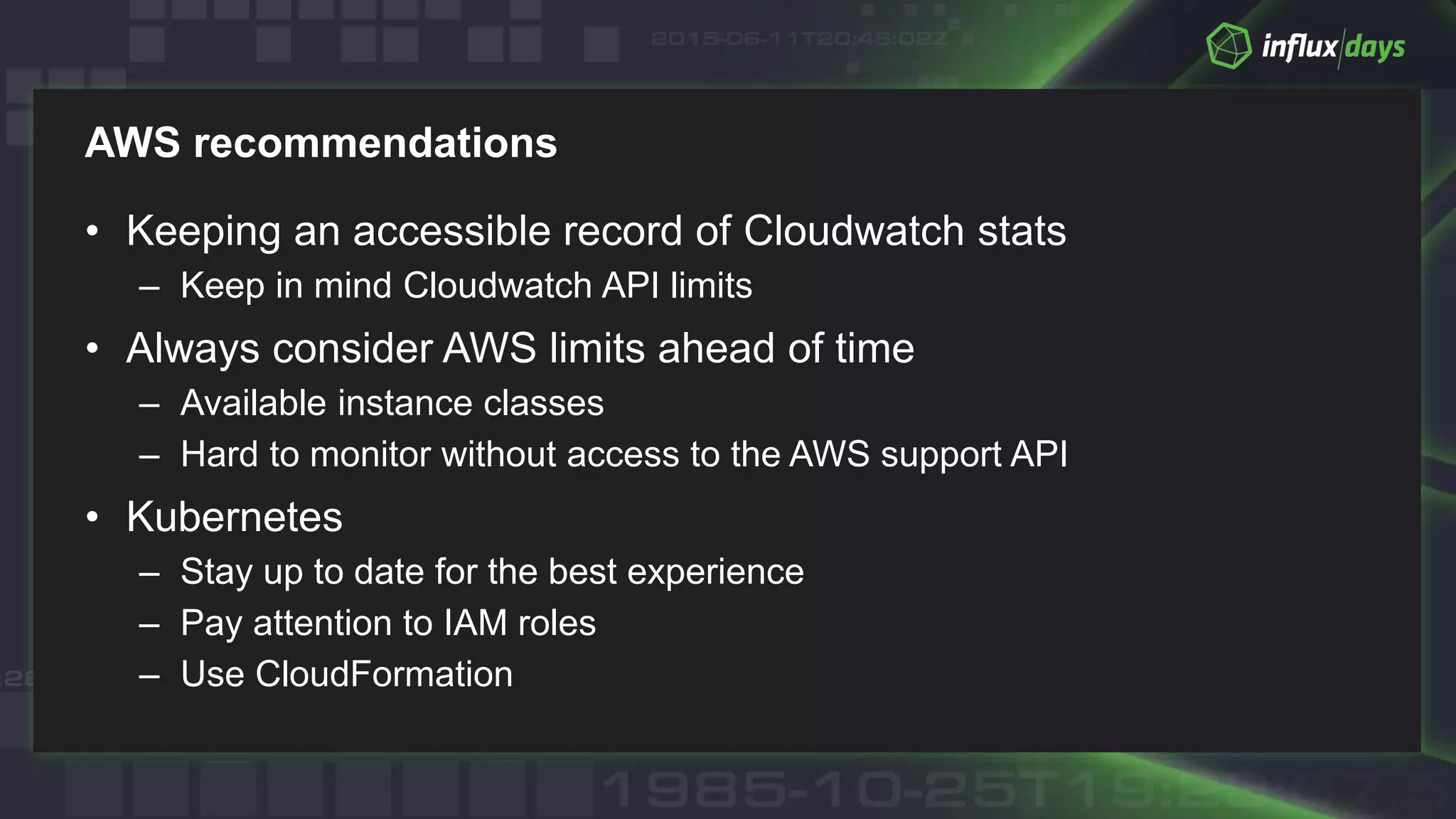
The document outlines best practices for container monitoring using AWS and InfluxData's TICK stack. It discusses deployment options on AWS, including ECS, Fargate, and EKS, while recommending various monitoring strategies and tools for tracking container performance and cluster health. Additionally, it emphasizes the need for comprehensive observability, including logging and tracing, to ensure effective monitoring in containerized environments.