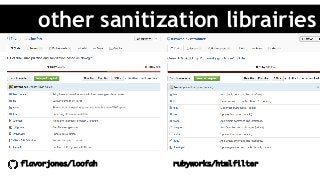
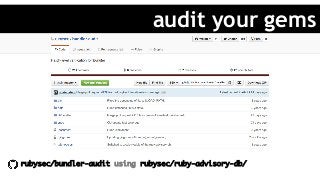
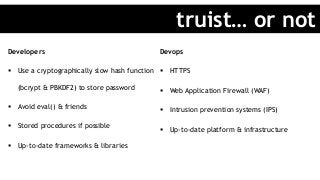
In today’s world, it's easier than ever to innovate and create great web applications. You release often, but let’s be honest, if you're like most developers out there, you don't spend your days worrying about security. You know it’s important, but you aren’t security savvy. So ask yourself, is your Ruby application secure? Come learn some of the different ways a hacker (cracker) can attack your code, and some of the best practices out there. In the end, your security is your users’ security.












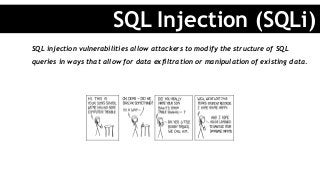








![# unsafe
Project.where("login='#{params[:name]}' AND password='#{params[:password]}'").first
# safe - array or hash w/ ActiveRecord
Project.where("login = ? AND password = ?", name, password).first
Project.where(login: name, password: password).first
no strings attached](https://image.slidesharecdn.com/isyourrubyapplicationsecure-montreal-151217193015/85/Is-your-ruby-application-secure-Montreal-rb-2015-12-15-23-320.jpg?cb=1450380685)