The document discusses RAiDiAM and its Open Banking Identity product. It summarizes:
- RAiDiAM was created to help with identity challenges of Open Banking and PSD2 regulations. It provides consulting and modular/scalable identity architecture services.
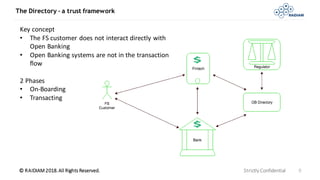
- The Open Banking Directory was developed as a trust framework "hub" to enable secure transactions between authorized financial companies using standards like OAuth2 and OIDC.
- It describes the Directory's key components, onboarding process to issue credentials to companies, and role in later transactions to validate claims between financial entities.