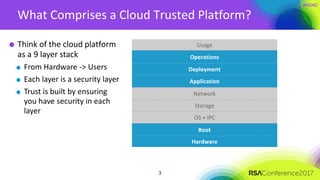
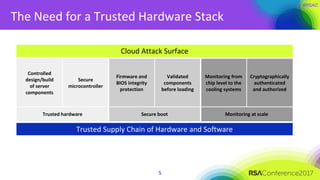
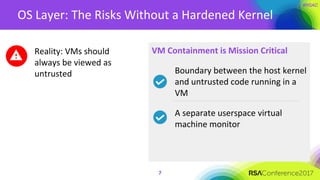
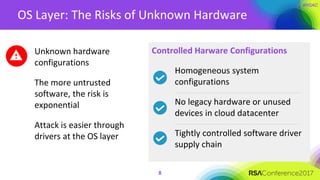
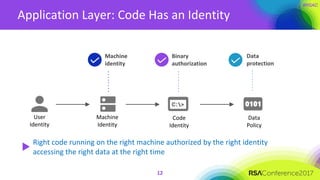
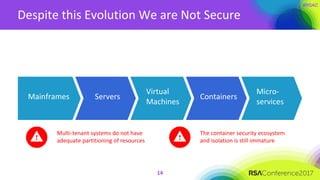
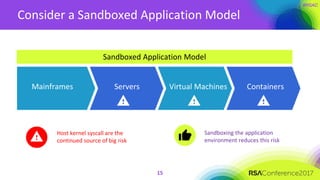
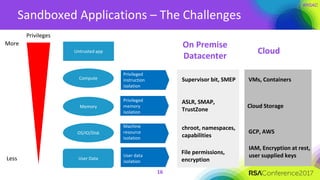
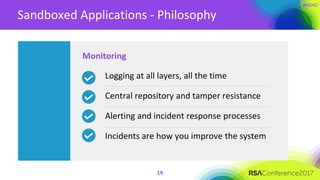
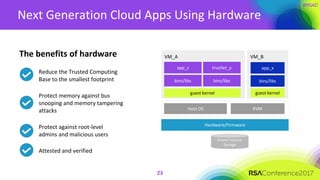
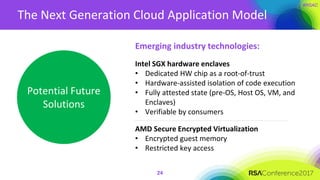
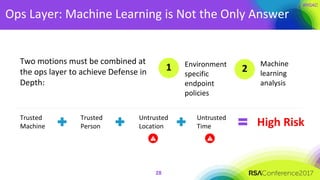
The document discusses the essential elements of a next-generation cloud trusted platform, emphasizing the importance of a multi-layered security approach that includes hardware, operating system, application, and deployment layers. Key points include the need for trusted hardware and software supply chains, continuous monitoring, and sandboxed applications to mitigate risks, particularly in the evolving landscape of cloud security. It concludes by highlighting the importance of robust authentication measures and best practices for moving to the cloud securely.