Penetration testing 5 reasons Why Organizations Should Adopt it
•
0 likes•30 views
Penetration testing is one type of security testing that should be taken up to detect recently discovered or any previously known vulnerabilities or weaknesses in their network, computer systems and applications.There are many reasons why organizations should focus on penetration testing.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
Cyber Security Testing - Protect Your Business From Cyber Threats

Cyber Security Testing - Protect Your Business From Cyber Threats
Survival of the Fittest: How to Build a Cyber Resilient Organization

Survival of the Fittest: How to Build a Cyber Resilient Organization
Third party risk management with cyber threat intelligence

Third party risk management with cyber threat intelligence
Similar to Penetration testing 5 reasons Why Organizations Should Adopt it
Similar to Penetration testing 5 reasons Why Organizations Should Adopt it (20)
Vulnerability Assessment and Penetration Testing Framework by Falgun Rathod

Vulnerability Assessment and Penetration Testing Framework by Falgun Rathod
What is VAPT & Why is it Important for Your Business.pptx

What is VAPT & Why is it Important for Your Business.pptx
(VAPT) Vulnerability Assessment And Penetration Testing

(VAPT) Vulnerability Assessment And Penetration Testing
Project Quality-SIPOCSelect a process of your choice and creat.docx

Project Quality-SIPOCSelect a process of your choice and creat.docx
Phi 235 social media security users guide presentation

Phi 235 social media security users guide presentation
Ethicalhackingalicencetohack 120223062548-phpapp01

Ethicalhackingalicencetohack 120223062548-phpapp01
More from TestingXperts
More from TestingXperts (20)
Agile vs devops : Learn The Differences Between Agile & Devops

Agile vs devops : Learn The Differences Between Agile & Devops
Accessibility testing - 5 tricks you can do right now

Accessibility testing - 5 tricks you can do right now
Recently uploaded
Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...

Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...MyIntelliSource, Inc.
Recently uploaded (20)
Adobe Marketo Engage Deep Dives: Using Webhooks to Transfer Data

Adobe Marketo Engage Deep Dives: Using Webhooks to Transfer Data
ODSC - Batch to Stream workshop - integration of Apache Spark, Cassandra, Pos...

ODSC - Batch to Stream workshop - integration of Apache Spark, Cassandra, Pos...
Building Real-Time Data Pipelines: Stream & Batch Processing workshop Slide

Building Real-Time Data Pipelines: Stream & Batch Processing workshop Slide
Advancing Engineering with AI through the Next Generation of Strategic Projec...

Advancing Engineering with AI through the Next Generation of Strategic Projec...
Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...

Try MyIntelliAccount Cloud Accounting Software As A Service Solution Risk Fre...
Short Story: Unveiling the Reasoning Abilities of Large Language Models by Ke...

Short Story: Unveiling the Reasoning Abilities of Large Language Models by Ke...
XpertSolvers: Your Partner in Building Innovative Software Solutions

XpertSolvers: Your Partner in Building Innovative Software Solutions
why an Opensea Clone Script might be your perfect match.pdf

why an Opensea Clone Script might be your perfect match.pdf
Alluxio Monthly Webinar | Cloud-Native Model Training on Distributed Data

Alluxio Monthly Webinar | Cloud-Native Model Training on Distributed Data
Project Based Learning (A.I).pptx detail explanation

Project Based Learning (A.I).pptx detail explanation
Penetration testing 5 reasons Why Organizations Should Adopt it
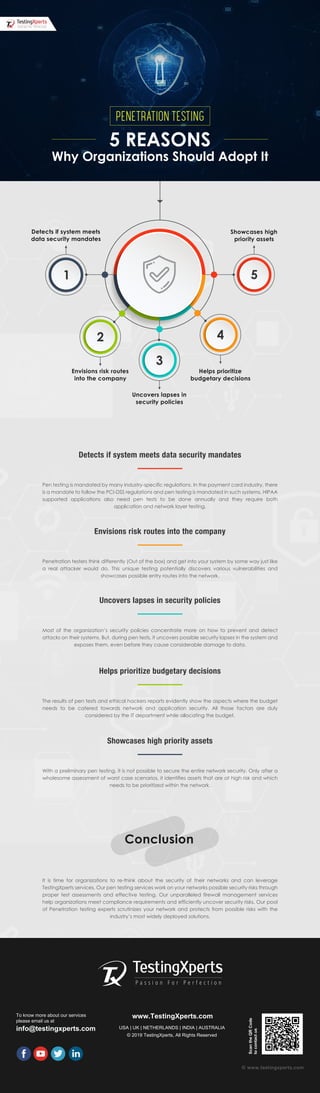
- 1. 5 REASONS Why Organizations Should Adopt It Pen testing is mandated by many industry-specific regulations. In the payment card industry, there is a mandate to follow the PCI-DSS regulations and pen testing is mandated in such systems. HIPAA supported applications also need pen tests to be done annually and they require both application and network layer testing. Conclusion Detects if system meets data security mandates Penetration testers think differently (Out of the box) and get into your system by some way just like a real attacker would do. This unique testing potentially discovers various vulnerabilities and showcases possible entry routes into the network. Envisions risk routes into the company Most of the organization’s security policies concentrate more on how to prevent and detect attacks on their systems. But, during pen tests, it uncovers possible security lapses in the system and exposes them, even before they cause considerable damage to data. Uncovers lapses in security policies The results of pen tests and ethical hackers reports evidently show the aspects where the budget needs to be catered towards network and application security. All those factors are duly considered by the IT department while allocating the budget. Helps prioritize budgetary decisions With a preliminary pen testing, it is not possible to secure the entire network security. Only after a wholesome assessment of worst case scenarios, it identifies assets that are at high risk and which needs to be prioritized within the network. It is time for organizations to re-think about the security of their networks and can leverage TestingXperts services. Our pen testing services work on your networks possible security risks through proper test assessments and effective testing. Our unparalleled firewall management services help organizations meet compliance requirements and efficiently uncover security risks. Our pool of Penetration testing experts scrutinizes your network and protects from possible risks with the industry’s most widely deployed solutions. Showcases high priority assets To know more about our services please email us at info@testingxperts.com www.TestingXperts.com USA | UK | NETHERLANDS | INDIA | AUSTRALIA © 2019 TestingXperts, All Rights Reserved ScantheQRCode tocontactus © www.testingxperts.com Detects if system meets data security mandates Showcases high priority assets Envisions risk routes into the company Uncovers lapses in security policies Helps prioritize budgetary decisions
