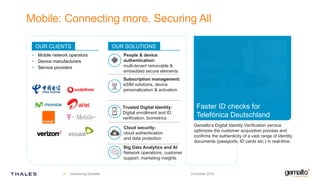
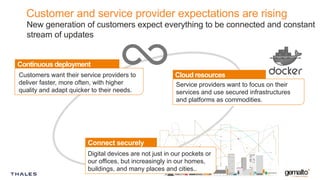
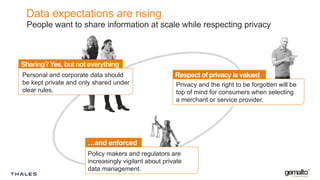
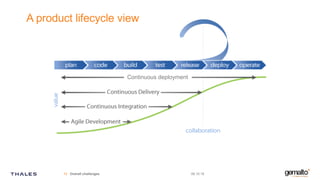
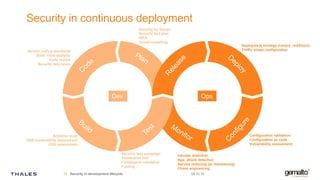
Gemalto focuses on providing security solutions across various sectors, including government, banking, and mobile IoT, to enhance connectivity and data protection. The document highlights the importance of integrating security into the development lifecycle through empowered engineering teams and continuous deployment practices. Furthermore, it addresses the rising expectations for fast, secure, and privacy-respecting services from both customers and service providers in an increasingly connected world.