Ransomware Explained
•
0 likes•103 views
Ransomware attacks—a type of malware (a.k.a. malicious software)— are proliferating around the globe at a blistering pace. In this infographic, learn what to do if you fall prey to an attack, and how data can be protected with cloud backups and disaster recovery.
Report
Share
Report
Share
Download to read offline
Recommended
What Businesses Entrepreneurs Are Imperative To Know About Ransomware

What Businesses Entrepreneurs Are Imperative To Know About RansomwareMavrickHost - Reliable Hosting Partner
More Related Content
Similar to Ransomware Explained
What Businesses Entrepreneurs Are Imperative To Know About Ransomware

What Businesses Entrepreneurs Are Imperative To Know About RansomwareMavrickHost - Reliable Hosting Partner
Similar to Ransomware Explained (20)
Are ransomware attacks the problem for web hosting firms?

Are ransomware attacks the problem for web hosting firms?
The Most Common Enterprise Malware and how to identify them

The Most Common Enterprise Malware and how to identify them
Corporations - the new victims of targeted ransomware

Corporations - the new victims of targeted ransomware
What Businesses Entrepreneurs Are Imperative To Know About Ransomware

What Businesses Entrepreneurs Are Imperative To Know About Ransomware
Advanced Threats in the Enterprise: Finding an Evil in the Haystack

Advanced Threats in the Enterprise: Finding an Evil in the Haystack
Panda Adaptive Defense 360 - Cyber Extortion Guide

Panda Adaptive Defense 360 - Cyber Extortion Guide
Recently uploaded
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptxnull - The Open Security Community
Recently uploaded (20)
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service

WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service
How to Remove Document Management Hurdles with X-Docs?

How to Remove Document Management Hurdles with X-Docs?
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
Next-generation AAM aircraft unveiled by Supernal, S-A2

Next-generation AAM aircraft unveiled by Supernal, S-A2
Ransomware Explained
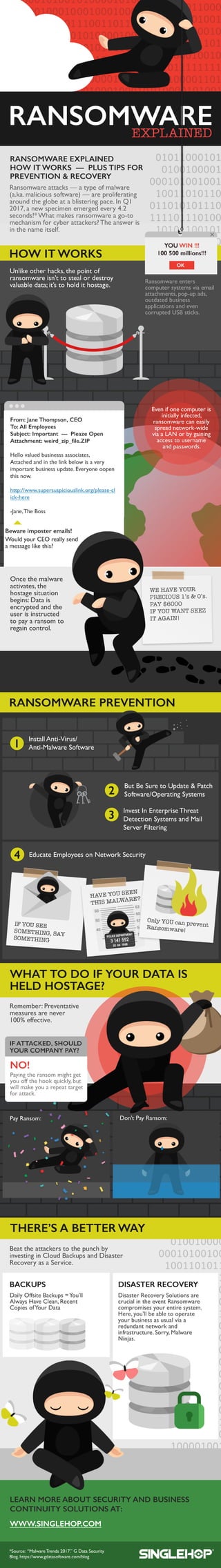
- 1. Unlikeotherhacks,thepointof ransomwareisn’ttostealordestroy valuabledata;it’stoholdithostage. HOW ITWORKS RANSOMWAREPREVENTION RANSOMWAREEXPLAINED HOW ITWORKS— PLUSTIPSFOR PREVENTION&RECOVERY Ransomwareenters computersystemsviaemail attachments,pop-upads, outdatedbusiness applicationsandeven corruptedUSBsticks. Ransomwareattacks— atypeofmalware (a.ka.malicioussoftware)— areproliferating aroundtheglobeatablisteringpace.InQ1 2017,anewspecimenemergedevery4.2 seconds!*Whatmakesransomwareago-to mechanismforcyberattackers?Theansweris inthenameitself. Beattheattackerstothepunchby investinginCloudBackupsandDisaster RecoveryasaService. PayRansom: DailyOffsiteBackups=You’ll AlwaysHaveClean,Recent CopiesofYourData Don’tPayRansom: poster poster poster RANSOMWARE WEHAVEYOUR PRECIOUS1’s&0’s. PAY$6000 IFYOUWANTSEEZ ITAGAIN! 1 2 3 4 IFYOUSEE SOMETHING,SAY SOMETHING HAVEYOUSEEN THISMALWARE? Remember:Preventative measuresarenever 100%effective. WHATTODOIFYOURDATAIS HELDHOSTAGE? DisasterRecoverySolutionsare crucialintheeventRansomware compromisesyourentiresystem. Here,you’llbeabletooperate yourbusinessasusualviaa redundantnetworkand infrastructure.Sorry,Malware NinjasNinjas. THERE’SABETTERWAY BACKUPS DISASTERRECOVERY *Source:“MalwareTrends2017.”GDataSecurity Blog.https://www.gdatasoftware.com/blog Evenifonecomputeris initiallyinfected, ransomwarecaneasily spreadnetwork-wide viaaLANorbygaining accesstousername andpasswords. Bewareimposteremails! WouldyourCEOreallysend amessagelikethis? Oncethemalware activates,the hostagesituation begins:Datais encryptedandthe userisinstructed topayaransomto regaincontregaincontrol. ButBeSuretoUpdate&Patch Software/OperatingSystems EducateEmployeesonNetworkSecurity InstallAnti-Virus/ Anti-MalwareSoftware InvestInEnterpriseThreat DetectionSystemsandMail ServerFiltering Payingtheransommightget youoffthehookquickly,but willmakeyouarepeattarget forattack. IFATTACKED,SHOULD YOURCOMPANYPAY? NO! RANSOMWAREEXPLAINED OnlyYOUcanpreventRansomware!
