http://ssimeetup.org/overview-proposed-pan-canadian-trust-framework-ssi-tim-bouma-webinar-19/
Tim Bouma is a Senior Analyst with Government of Canada, specializing in digital identity and the development of the Pan-Canadian Trust Framework. This presentation provides an overview of the Pan-Canadian Trust Framework (PCTF) and the latest iteration, building on policy and standards that have been in development in Canada for more than a decade.
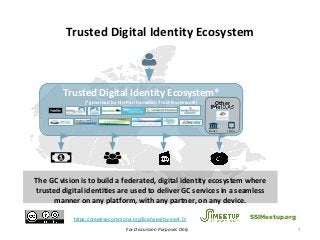
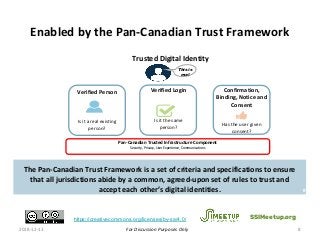
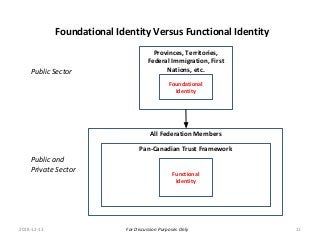
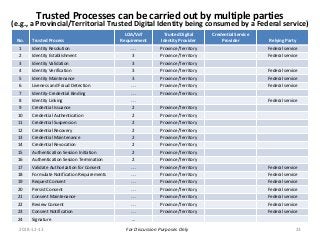
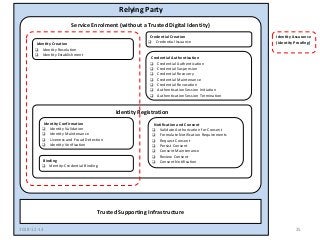
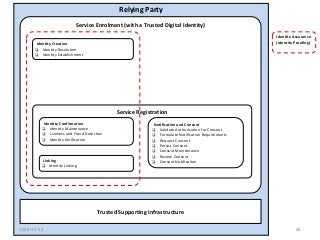
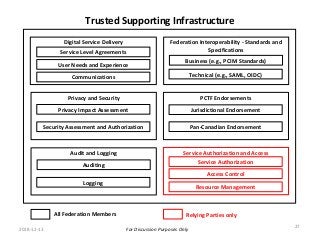
Within Canada, there is no national identity program. Rather it is a shared responsibility across all jurisdictions. The PCTF is being developed to enable a pan-Canadian approach – a collective approach that serves the needs for all jurisdictions – federal, provincial and territorial, and in collaboration of the private sector.
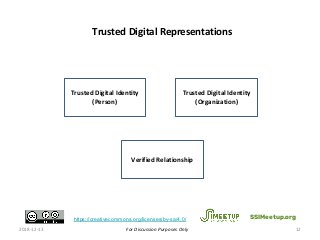
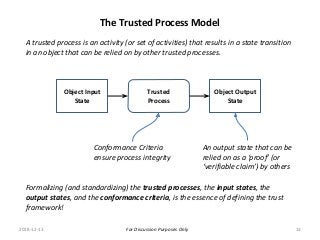
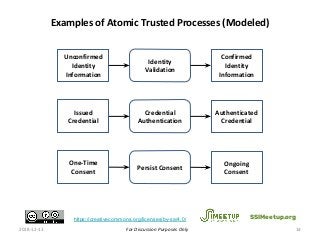
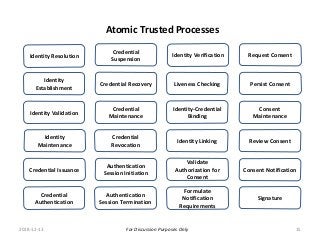
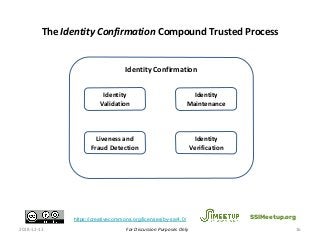
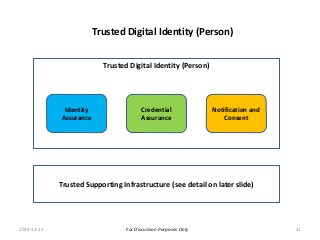
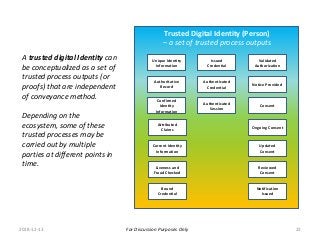
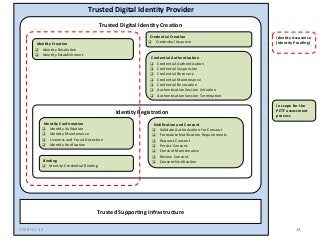
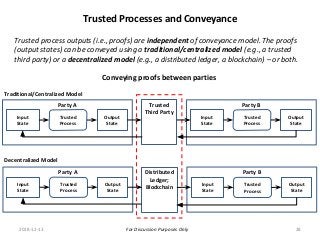
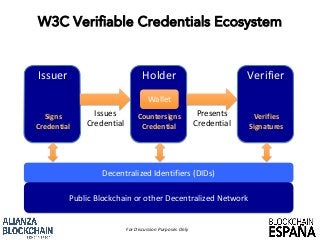
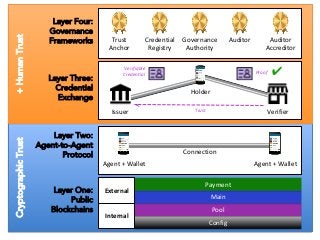
The PCTF is being designed to work across many contexts (legal, business, program and services) and to provide a consistent method to assess digital identity programs, the integrity of their trusted processes, and enabling solutions. The PCTF is also being designed to take advantage of new and emerging technologies, namely self-sovereign identity, verifiable credentials, and decentralized identifiers.




![For Discussion Purposes Only
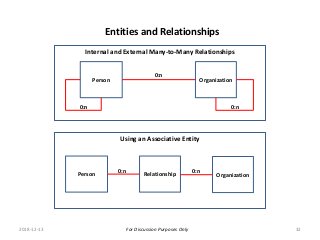
Context (Goals, Rules, Facts)
Basics of a ‘ [Digital] Trust Framework’
55
SSIMeetup.orghttps://creativecommons.org/licenses/by-sa/4.0/
[Digital]
Representation
A tool to answer the question:
[Within a given context] what do I need to hold true to rely on ?](https://image.slidesharecdn.com/webinar19pancanadiantrustframeworkforssi-timbouma-190116225640/85/Overview-of-the-Proposed-PanCanadian-Trust-Framework-for-SSI-Tim-Bouma-5-320.jpg?cb=1547680545)