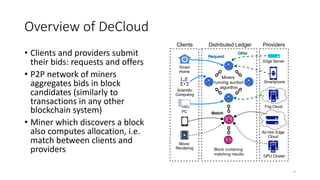
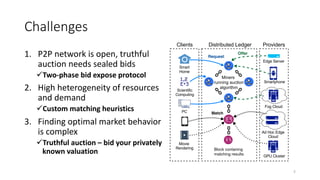
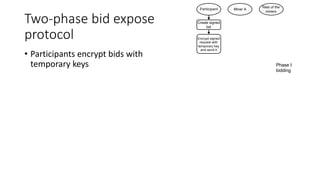
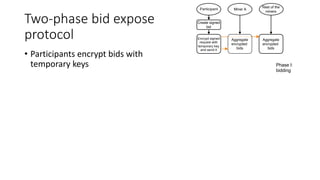
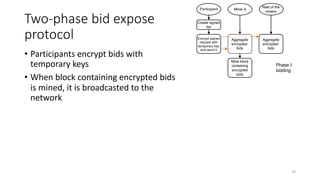
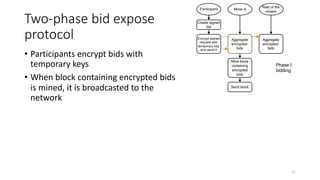
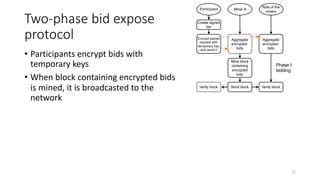
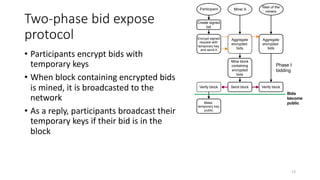
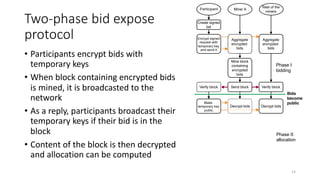
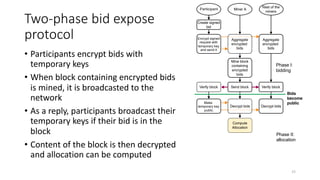
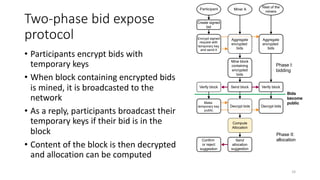
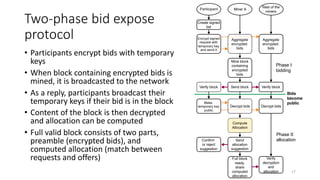
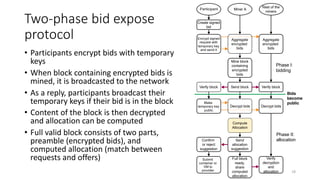
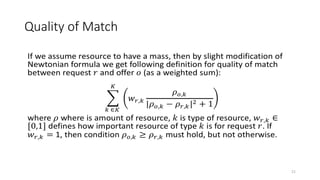
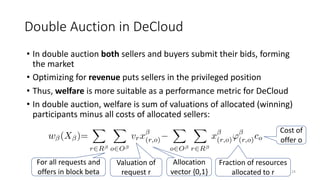
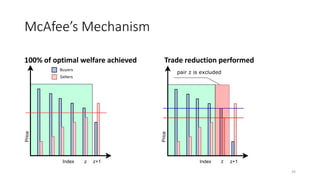
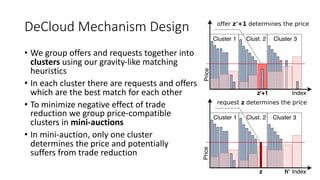
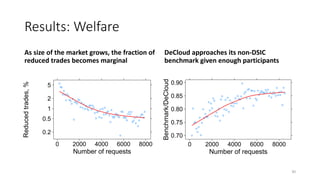
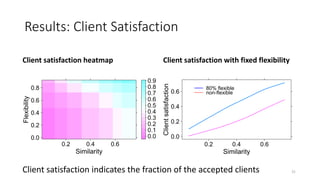
The document presents 'decloud', a decentralized double auction model designed for edge computing environments, aiming to reduce dependency on large cloud providers. It proposes a truthful market model that allows participants to achieve optimal payoffs through a two-phase bidding protocol on a distributed ledger, enabling diverse resources to be matched with varying demands. The model emphasizes minimization of market complexities and encourages underutilized resources at the edge of networks to be utilized effectively.