Fall 2015 Worldwide Netskope Cloud Report
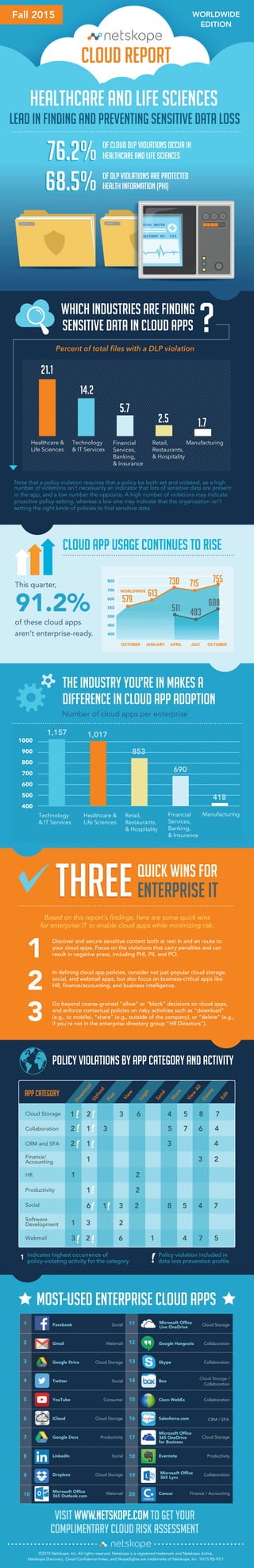
- 1. Cloud Storage Collaboration CRM and SFA Finance/ Accounting HR Productivity Social Software Development Webmail Dow nload Upload Post View Login Send Share View All APP CATEGORY 1 2 3 6 4 5 2 2 1 1 3 2 6 1 4 7 5 3 2 2 1 1 6 1 3 2 8 5 4 7 1 2 3 2 3 4 1 3 5 7 6 4 8 7 Delete Edit Indicates highest occurrence of policy-violating activity for the category Policy violation included in data loss prevention profile 1 Policy Violations by App Category and Activity CLOUD REPORT of DLP violations are protected health information (PHI) healthcare and life sciences of cloud DLP violations occur in 76.2% 68.5% HEALTHCARE AND LIFE SCIENCES 76.2% 68.5% JOHN SMITH PATIENT NO. 234 LEAD IN FINDING AND PREVENTING SENSITIVE DATA LOSS Healthcare & Life Sciences Technology & IT Services Financial Services, Banking, & Insurance Retail, Restaurants, & Hospitality Manufacturing 21.1 14.2 5.7 2.5 1.7 WHICH INDUSTRIES ARE FINDING SENSITIVE DATA IN CLOUD APPS Percent of total files with a DLP violation Note that a policy violation requires that a policy be both set and violated, so a high number of violations isn’t necessarily an indicator that lots of sensitive data are present in the app, and a low number the opposite. A high number of violations may indicate proactive policy-setting, whereas a low one may indicate that the organization isn’t setting the right kinds of policies to find sensitive data. ? CLOUD REPORT CLOUD APP USAGE CONTINUES TO RISE This quarter, of these cloud apps aren’t enterprise-ready. OCTOBER JANUARY APRIL JULY OCTOBER 579 613 730 511 483 608 715 755 WORLDWIDE 400 450 500 550 600 700 800 91.2% THE INDUSTRY YOU’RE IN MAKES A DIFFERENCE IN CLOUD APP ADOPTION 400 500 600 700 800 900 1000 Technology & IT Services Healthcare & Life Sciences Retail, Restaurants, & Hospitality Financial Services, Banking, & Insurance Manufacturing 1,157 1,017 853 690 418 Number of cloud apps per enterprise 1 2 quick wins FOR enterprise IT 3 Based on this report’s findings, here are some quick wins for enterprise IT to enable cloud apps while minimizing risk: Discover and secure sensitive content both at rest in and en route to your cloud apps. Focus on the violations that carry penalties and can result in negative press, including PHI, PII, and PCI. In defining cloud app policies, consider not just popular cloud storage, social, and webmail apps, but also focus on business-critical apps like HR, finance/accounting, and business intelligence. Go beyond coarse-grained “allow” or “block” decisions on cloud apps, and enforce contextual policies on risky activities such as “download” (e.g., to mobile), “share” (e.g., outside of the company), or “delete” (e.g., if you’re not in the enterprise directory group “HR Directors”). THREETHREE Facebook Gmail Google Drive Twitter YouTube iCloud Google Docs LinkedIn Dropbox Microsoft Office 365 Outlook.com Social Webmail Cloud Storage Social Consumer Cloud Storage Productivity Social Cloud Storage Webmail Cloud Storage Collaboration Collaboration Cloud Storage / Collaboration Collaboration CRM / SFA Productivity Collaboration Finance / Accounting Google Hangouts Skype Box Cisco WebEx Salesforce.com Evernote Concur 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 Microsoft Office 365 OneDrive for Business Microsoft Office 365 Lync Microsoft Office Live OneDrive Cloud Storage MOST-USED ENTERPRISE CLOUD APPS ©2015 Netskope, Inc. All rights reserved. Netskope is a registered trademark and Netskope Active, Netskope Discovery, Cloud Confidence Index, and SkopeSights are trademarks of Netskope, Inc. 10/15 RS-93-1 VISIT WWW.NETSKOPE.COM TO GET YOUR COMPLIMENTARY CLOUD RISK ASSESSMENT Fall 2015 WORLDWIDE EDITION
