6 ways to manage IT Security
•
0 likes•23 views
workspace suite provides an integrated approach to application and data security, allowing access to resources anywhere anytime. It protects company data while enabling employee productivity. The suite offers advanced web filtering, monitoring of workspaces, and secure collaboration to help address challenges from new mobile work behaviors. IT needs solutions to manage mobility and security issues while providing a consistent user experience across devices and keeping sensitive data encrypted.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
[de Jager] Classify, Label and Protect your data with Azure Information Prote...![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[de Jager] Classify, Label and Protect your data with Azure Information Prote...European Collaboration Summit
More Related Content
What's hot
[de Jager] Classify, Label and Protect your data with Azure Information Prote...![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[de Jager] Classify, Label and Protect your data with Azure Information Prote...European Collaboration Summit
What's hot (20)
Decriminalize Your Colleagues - How to Address Shadow IT in the Enterprise

Decriminalize Your Colleagues - How to Address Shadow IT in the Enterprise
Protect your business with identity and access management in the cloud

Protect your business with identity and access management in the cloud
[de Jager] Classify, Label and Protect your data with Azure Information Prote...![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[de Jager] Classify, Label and Protect your data with Azure Information Prote...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[de Jager] Classify, Label and Protect your data with Azure Information Prote...
Leading Trends in IAM Webinar 2: Minimizing Complexities in IT Operations

Leading Trends in IAM Webinar 2: Minimizing Complexities in IT Operations
How to protect your corporate from advanced attacks

How to protect your corporate from advanced attacks
Identity and Data protection with Enterprise Mobility Security in ottica GDPR

Identity and Data protection with Enterprise Mobility Security in ottica GDPR
Leading Trends in IAM Webinar 3: Optimizing User Experience in Cloud Initiatives

Leading Trends in IAM Webinar 3: Optimizing User Experience in Cloud Initiatives
Cloud Computing Risks by Ravi Namboori Cisco Evangelist

Cloud Computing Risks by Ravi Namboori Cisco Evangelist
Similar to 6 ways to manage IT Security
Similar to 6 ways to manage IT Security (20)
Service now is a software platform that supports IT service manag.docx

Service now is a software platform that supports IT service manag.docx
Xylos Clients Day - Public cloud and security go hand in hand, if you approac...

Xylos Clients Day - Public cloud and security go hand in hand, if you approac...
Growth Uninterrupted with Security, Scalability and Simplicity

Growth Uninterrupted with Security, Scalability and Simplicity
Softchoice & Microsoft: Public Cloud Security Webinar

Softchoice & Microsoft: Public Cloud Security Webinar
the_role_of_resilience_data_in_ensuring_cloud_security.pptx

the_role_of_resilience_data_in_ensuring_cloud_security.pptx
Recently uploaded
Recently uploaded (20)
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
Artificial intelligence in the post-deep learning era

Artificial intelligence in the post-deep learning era
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Hyderabad Call Girls Khairatabad ✨ 7001305949 ✨ Cheap Price Your Budget

Hyderabad Call Girls Khairatabad ✨ 7001305949 ✨ Cheap Price Your Budget
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Snow Chain-Integrated Tire for a Safe Drive on Winter Roads

Snow Chain-Integrated Tire for a Safe Drive on Winter Roads
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Vulnerability_Management_GRC_by Sohang Sengupta.pptx

Vulnerability_Management_GRC_by Sohang Sengupta.pptx
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
6 ways to manage IT Security
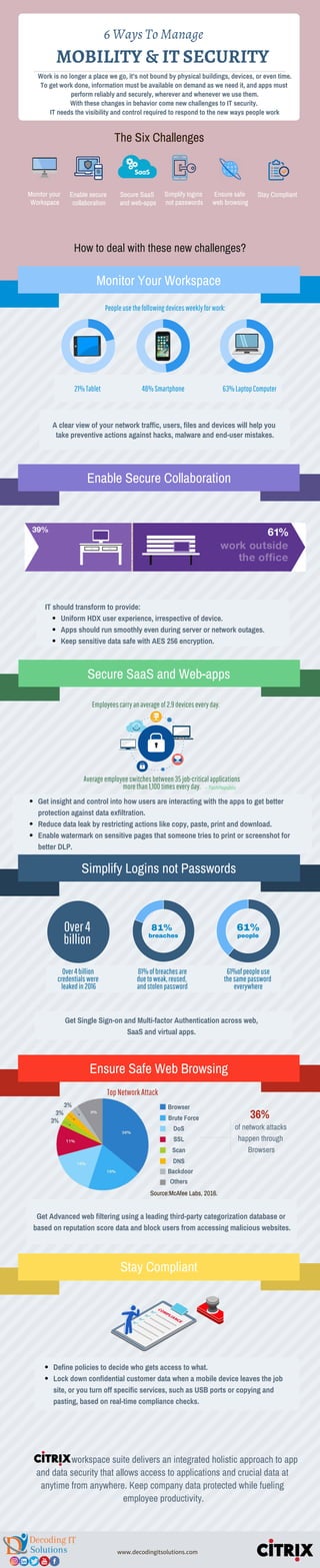
- 1. workspace suite delivers an integrated holistic approach to app and data security that allows access to applications and crucial data at anytime from anywhere. Keep company data protected while fueling employee productivity. Get Advanced web filtering using a leading third-party categorization database or based on reputation score data and block users from accessing malicious websites. How to deal with these new challenges? Monitor Your Workspace Enable Secure Collaboration Work is no longer a place we go, it’s not bound by physical buildings, devices, or even time. To get work done, information must be available on demand as we need it, and apps must perform reliably and securely, wherever and whenever we use them. With these changes in behavior come new challenges to IT security. IT needs the visibility and control required to respond to the new ways people work 6 Ways To Manage MOBILITY & IT SECURITY Secure SaaS and Web-apps Averageemployeeswitchesbetween35job-criticalapplications morethan1,100timeseveryday. Simplify Logins not Passwords Ensure Safe Web Browsing Stay Compliant Enable secure collaboration Monitor your Workspace Secure SaaS and web-apps Simplify logins not passwords Ensure safe web browsing Stay Compliant A clear view of your network traffic, users, files and devices will help you take preventive actions against hacks, malware and end-user mistakes. IT should transform to provide: Uniform HDX user experience, irrespective of device. Apps should run smoothly even during server or network outages. Keep sensitive data safe with AES 256 encryption. Get insight and control into how users are interacting with the apps to get better protection against data exfiltration. Reduce data leak by restricting actions like copy, paste, print and download. Enable watermark on sensitive pages that someone tries to print or screenshot for better DLP. TopNetworkAttack Get Single Sign-on and Multi-factor Authentication across web, SaaS and virtual apps. Define policies to decide who gets access to what. Lock down confidential customer data when a mobile device leaves the job site, or you turn off specific services, such as USB ports or copying and pasting, based on real-time compliance checks. The Six Challenges www.decodingitsolutions.com Browser SSL DoS Brute Force Others Backdoor DNS Scan 3% 3% 3% 61%81% 61%ofpeopleuse thesamepassword everywhere Over4billion credentialswere leakedin2016 81%ofbreachesare duetoweak,reused, andstolenpassword 36% Source:McAfee Labs, 2016. breaches people Over4 billion Employeescarryanaverageof2.9deviceseveryday. - TechRepublic Peopleusethefollowingdevicesweeklyforwork: 63%LaptopComputer48%Smartphone21%Tablet of network attacks happen through Browsers
