Set up data sync in dest
•Download as PPTX, PDF•
0 likes•11 views
Set up DataSync in destination account - For Medium post
Report
Share
Report
Share
Recommended
ITB2019 Build Fine-Grained Control of Amazon Web Services in Your CFML App - ...

ITB2019 Build Fine-Grained Control of Amazon Web Services in Your CFML App - ...Ortus Solutions, Corp
More Related Content
Similar to Set up data sync in dest
ITB2019 Build Fine-Grained Control of Amazon Web Services in Your CFML App - ...

ITB2019 Build Fine-Grained Control of Amazon Web Services in Your CFML App - ...Ortus Solutions, Corp
Similar to Set up data sync in dest (20)
Best Practices for Active Directory with AWS Workloads

Best Practices for Active Directory with AWS Workloads
Securing Data in Serverless Applications and Messaging Services (API317-R2) -...

Securing Data in Serverless Applications and Messaging Services (API317-R2) -...
Claims based authentication in share point 2010 .new

Claims based authentication in share point 2010 .new
ABD317_Building Your First Big Data Application on AWS - ABD317

ABD317_Building Your First Big Data Application on AWS - ABD317
BDA309 Build Your First Big Data Application on AWS

BDA309 Build Your First Big Data Application on AWS
Deploying Business Analytics at Enterprise Scale - AWS Online Tech Talks

Deploying Business Analytics at Enterprise Scale - AWS Online Tech Talks
ITB2019 Build Fine-Grained Control of Amazon Web Services in Your CFML App - ...

ITB2019 Build Fine-Grained Control of Amazon Web Services in Your CFML App - ...
Financial Svcs: Mine Actionable Insights from Customer Interactions Using Mac...

Financial Svcs: Mine Actionable Insights from Customer Interactions Using Mac...
Build high performing mobile apps, faster with AWS

Build high performing mobile apps, faster with AWS
Analyze Image Meta-Data with Amazon Rekognition + Athena

Analyze Image Meta-Data with Amazon Rekognition + Athena
GPSTEC310_IAM Best Practices and Becoming an IAM Ninja

GPSTEC310_IAM Best Practices and Becoming an IAM Ninja
Become an IAM Policy Master in 60 Minutes or Less (SEC316-R1) - AWS reInvent ...

Become an IAM Policy Master in 60 Minutes or Less (SEC316-R1) - AWS reInvent ...
Easily Transform Compliance to Code using AWS Config, Config Rules, and the R...

Easily Transform Compliance to Code using AWS Config, Config Rules, and the R...
Customizing Data Lakes to Work for Your Enterprise with Sysco (STG340) - AWS ...

Customizing Data Lakes to Work for Your Enterprise with Sysco (STG340) - AWS ...
Recently uploaded
Recently uploaded (20)
How to Check GPS Location with a Live Tracker in Pakistan

How to Check GPS Location with a Live Tracker in Pakistan
Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx

Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx
The Zero-ETL Approach: Enhancing Data Agility and Insight

The Zero-ETL Approach: Enhancing Data Agility and Insight
Frisco Automating Purchase Orders with MuleSoft IDP- May 10th, 2024.pptx.pdf

Frisco Automating Purchase Orders with MuleSoft IDP- May 10th, 2024.pptx.pdf
Event-Driven Architecture Masterclass: Challenges in Stream Processing

Event-Driven Architecture Masterclass: Challenges in Stream Processing
Tales from a Passkey Provider Progress from Awareness to Implementation.pptx

Tales from a Passkey Provider Progress from Awareness to Implementation.pptx
Event-Driven Architecture Masterclass: Integrating Distributed Data Stores Ac...

Event-Driven Architecture Masterclass: Integrating Distributed Data Stores Ac...
Six Myths about Ontologies: The Basics of Formal Ontology

Six Myths about Ontologies: The Basics of Formal Ontology
Introduction to FIDO Authentication and Passkeys.pptx

Introduction to FIDO Authentication and Passkeys.pptx
WebRTC and SIP not just audio and video @ OpenSIPS 2024

WebRTC and SIP not just audio and video @ OpenSIPS 2024
JavaScript Usage Statistics 2024 - The Ultimate Guide

JavaScript Usage Statistics 2024 - The Ultimate Guide
Microsoft CSP Briefing Pre-Engagement - Questionnaire

Microsoft CSP Briefing Pre-Engagement - Questionnaire
Intro to Passkeys and the State of Passwordless.pptx

Intro to Passkeys and the State of Passwordless.pptx
Hyatt driving innovation and exceptional customer experiences with FIDO passw...

Hyatt driving innovation and exceptional customer experiences with FIDO passw...
TEST BANK For, Information Technology Project Management 9th Edition Kathy Sc...

TEST BANK For, Information Technology Project Management 9th Edition Kathy Sc...
ChatGPT and Beyond - Elevating DevOps Productivity

ChatGPT and Beyond - Elevating DevOps Productivity
Set up data sync in dest
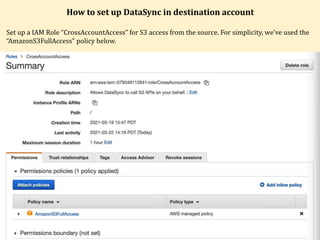
- 1. How to set up DataSync in destination account Set up a IAM Role “CrossAccountAccess” for S3 access from the source. For simplicity, we’ve used the “AmazonS3FullAccess” policy below.
- 2. How to set up DataSync in destination account Set up a IAM Role “CrossAccountAccess” for S3 access from the source. For simplicity, we’ve used the “AmazonS3FullAccess” policy below.
- 3. How to set up DataSync in destination account Click on the “Trust relationships” tab.
- 4. How to set up DataSync in destination account Click “Edit trust relationship.”
- 5. How to set up DataSync in destination account Add the following Trust Policy, which will show up under “Trusted entities.” { "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Service": "datasync.amazonaws.com" }, "Action": "sts:AssumeRole" } ] }
- 6. How to set up DataSync in destination account Next, create a S3 bucket (“trellis-datasync-dst1”) in the destination account/region with default attributes. Create the cross account s3 location (for source A), from destination B using the AWS CLI below: ❯ aws datasync create-location-s3 --s3-bucket-arn arn:aws:s3:::trellis-datasync-src1 --s3-config '{"BucketAccessRoleArn":"arn:aws:iam::5555555555:role/C rossAccountAccess"}' --region eu-west-1
- 7. How to set up DataSync in destination account If the command works, the output below will be displayed: { "LocationArn": "arn:aws:datasync:eu-west- 1:079349112641:location/loc-054160bbd934e32c9" }