IT Compliance: Shifting from Cost Center to Profit Center
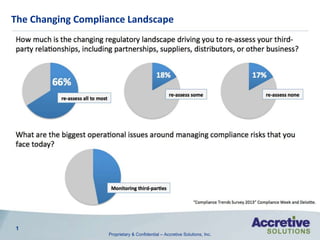
- 1. Proprietary & Confidential – Accretive Solutions, Inc. How much is the changing regulatory landscape driving you to re-assess your third- party relationships, including partnerships, suppliers, distributors, or other business? 1 The Changing Compliance Landscape What are the biggest operational issues around managing compliance risks that you face today? 66% 18% 17% re-assess all to most re-assess some re-assess none 47% Monitoring third-parties “Compliance Trends Survey 2013” Compliance Week and Deloitte.
- 2. Proprietary & Confidential – Accretive Solutions, Inc. IT Compliance as a Growth Accelerator Connecting Problems with Problem Solvers WELCOME
- 3. Proprietary & Confidential – Accretive Solutions, Inc. Webinar Features 3 Presentation Window Use the buttons in the top-right of the presentation window to maximize or minimize a widget. CPE CERTIFICATION To qualify for CPE Credit you must answer all of the polling questions as well as fill out the CPE Evaluation. Click this icon in the dock to access the evaluation. Q&A If you have a question during the presentation you may enter it here. Resources • Copy of Presentation • Presenter Bios Dock Provides control of the on-screen widgets.
- 4. Proprietary & Confidential – Accretive Solutions, Inc. CPE Credit 4 Two requirements: 1) Answer 4 polling questions throughout the presentation 2) Fill out the CPE Evaluation anytime during the presentation Click this icon to take Evaluation
- 5. Proprietary & Confidential – Accretive Solutions, Inc. CPE Credit 5 Two requirements: 1) Answer 4 polling questions throughout the presentation 2) Fill out the CPE Evaluation anytime during the presentation
- 6. Proprietary & Confidential – Accretive Solutions, Inc. CPE Credit 6 Two requirements: 1) Answer 4 polling questions throughout the presentation 2) Fill out the CPE Evaluation anytime during the presentation
- 7. Proprietary & Confidential – Accretive Solutions, Inc. CPE Credit 7 YOUR NAME Click this icon to print CPE certificate
- 8. Proprietary & Confidential – Accretive Solutions, Inc. Agenda Overview: Insights on structuring a more strategic IT Compliance organization. Deploying an integrated framework to address multiple compliance requirements while mitigating risks and driving efficiencies. Lessons From the Trenches: Sajeev Prelis Practice Director of IT Strategy & Compliance, Accretive Solutions Gary Pennington Southwest Practice Director, SSAE-16 Professionals Blake Holman Senior Vice President, Chief Information Officer, Ryan, Inc. CPE Evaluation 8
- 9. Proprietary & Confidential – Accretive Solutions, Inc. Learning Objectives for this Webinar How an IT Compliance organization can be a catalyst for change and a driver for growth Insights on how to positively contribute to the bottom line Practical examples of how an integrated framework impacts organizations 9
- 10. Proprietary & Confidential – Accretive Solutions, Inc. Sajeev Prelis 10 Practice Director of IT Strategy and Compliance Accretive Solutions
- 11. Proprietary & Confidential – Accretive Solutions, Inc. The Changing Compliance Landscape Old compliance environment IT an Afterthought Nice to have Differentiator Selling point 11 Current compliance environment IT an Integral Part Must have Expected Deal breaker
- 12. Proprietary & Confidential – Accretive Solutions, Inc. Why Comply: Fulfills contractual obligations Provides a competitive advantage Secures a seat at the table Increases client confidence in internal controls Prevents audits/questionnaires throughout the year Increases investor confidence in internal controls Enhances internal operational control that would facilitate controlled growth …and, it’s the law! 12 The Changing Compliance Landscape
- 13. Proprietary & Confidential – Accretive Solutions, Inc. SSAE16 (SOC 1) - The Statement on Standards for Attestation Engagements (SSAE) No. 16 SOC 2 & 3 – Service Organization Control 2 & 3 PCI DSS – Payment Card Industry Data Security Standard SOX – Sarbanes-Oxley 404 HIPAA – Health Insurance Portability and Accountability Act ISO – International Organization for Standardization FCPA – Foreign Corrupt Practices Act FISMA – Federal Information Security Management Act FFIEC - The Federal Financial Institutions Examination Council ………. 13 The Changing Compliance Landscape
- 14. Proprietary & Confidential – Accretive Solutions, Inc. Pain Points: Cost of multiple compliance assessments Direct monetary cost Opportunity cost of internal resource time Managing multiple service providers Hiring internal resources with skillsets to manage multiple efforts Maintaining multiple control lists • Responding to multiple PBC lists 14 The Changing Compliance Landscape
- 15. Proprietary & Confidential – Accretive Solutions, Inc. “Test once - comply with many” approach: Enable one test to cover multiple compliance initiatives Leverage common requirements across standards Aligns controls to cover multiple compliance initiatives Consolidates service providers • Same team to test controls • Retain tribal knowledge • Deal with one point of contact Achieve reduction in overall assessment resources for the environment 15 Alleviating the Compliance Burden
- 16. Proprietary & Confidential – Accretive Solutions, Inc. Benefits: Promotes efficiency by reducing internal resource audit support responsibilities and frees up time to concentrate on business needs Reduces compliance cost if performed by one provider Simplifies identification of control gaps and unmitigated risks Streamlines policy and procedure and control updates 16 Alleviating the Compliance Burden
- 17. Proprietary & Confidential – Accretive Solutions, Inc. Appoint internal champion who has executive support: Bring the different stakeholders and business units together (IA, IT, Finance, Legal, Procurement) Identify geographic considerations Reevaluate timing of reports: Movable vs. immovable compliance initiatives External stakeholder considerations 17 Implementation – Practical Considerations
- 18. Proprietary & Confidential – Accretive Solutions, Inc. Choose the service provider: One provider Multiple vendors managed internally Take it slow, include one compliance initiative at a time. 18 Implementation – Practical Considerations
- 19. Proprietary & Confidential – Accretive Solutions, Inc. Southwest Practice Director Gary Pennington 19
- 20. Proprietary & Confidential – Accretive Solutions, Inc. SSAE 16 Professionals, LLP Licensed CPA firm with offices throughout the USA Registered with the PCAOB Specialized focus on SSAE 16 (SOC 1), SOC 2, & other IT Compliance services Strategic alliance partner of Accretive Solutions Personnel comprised of former Big 4 and other large international accounting firm personnel 20 Company Overview
- 21. Proprietary & Confidential – Accretive Solutions, Inc. Password Control 21 PCI SSAE16 / SOC2&3 ISO 27001 SOX 8.2.4 - Change passwords at least every 90 days 8.2.3 - Passwords must be at least seven characters long 8.1.6/8.1.7 - Lockout threshold and duration 8.2.3 - Passwords must contain both alphabetic and numeric characters 8.2.5 - History of at least four passwords remembered Security Principal 3.2.5 The internal network domain is configured to enforce the following password requirements: •Maximum Password Age •Minimum Password Length •Invalid Password Lockout •Complexity •Password History 9.4.1 – Access to information and application system functions shall be restricted in accordance with the access control policy. 9.4.2 – Where required by the access control policy, access to systems and applications shall be controlled by a secure log- in procedure. 9.4.3 – Password management systems shall be interactive and shall ensure quality passwords. Applications and systems are configured to comply with password parameters as defined in the Safe Computing Policy. Practical Example – Compliance Consolidation
- 22. Proprietary & Confidential – Accretive Solutions, Inc. 22 PCI SSAE16 / SOC2&3 ISO 27001 SOX 9.1 - Controls to limit and monitor physical access - video cameras and/or access- control mechanisms in place, protected from tampering, monitored/reviewed and correlated with other entries, and data stored for at least three months. 9.3 - Visitors authorized, distinguishable, badge expiration controls. 9.4 - Visitor log Security Principal 3.3.2 Physical access to the onsite data center is restricted to authorized personnel. 11.1.1 – Security perimeters shall be defined and used to protect areas that contain either sensitive or critical information and information processing facilities. 11.1.2 – Secure areas shall be protected by appropriate entry controls to ensure that only authorized personnel are allowed access. Physical access to the data center is restricted to authorized IT Operations staff only. Practical Example – Compliance Consolidation Physical Access to Datacenter
- 23. Proprietary & Confidential – Accretive Solutions, Inc. 23 PCI SSAE16 / SOC2&3 ISO 27001 SOX 5.1 Deploy anti-virus software on all systems commonly affected by malicious software (particularly personal computers and servers). 5.1.1 Ensure that anti-virus programs are capable of detecting, removing, and protecting against all known types of malicious software. 5.1.2 For systems considered to be not commonly affected by malicious software, perform periodic evaluations to identify and evaluate evolving malware threats in order to confirm whether such systems continue to not require anti-virus software. 5.2 Ensure that all anti-virus mechanisms are maintained as follows: Are kept current Perform periodic scans Generate audit logs which are retained per PCI DSS Requirement 10.7 5.3 Ensure that anti-virus mechanisms are actively running and cannot be disabled or altered by users, unless specifically authorized by management on a case-by-case basis for a limited time period. 3.5.1 - Anti-virus software with up to date virus signatures are used to protect all Company network devices. Scans are performed on a daily basis. 3.5.2 -Anti-virus software security updates are applied based on automatic update timelines. 12.2.1 Detection, prevention and recovery controls to protect against malware shall be implemented, combined with appropriate user awareness. Virus protection software at the Network/Gateway level is configured to scan and filter the incoming and outgoing network traffic (Email, HTTP, FTP and other messaging) for real-time detection and quarantine of malicious code. Practical Example – Anti-virus Protection
- 24. Proprietary & Confidential – Accretive Solutions, Inc. Map controls: Identify control overlap Force adherence to the stricter control Standardize sample selection methodology Acquire applications that map multiple standards Good in theory, but not always practical Good starting point, but need experienced personnel to properly execute Not always compatible with SSAE 16 since a standardized set of controls has not been created by the AICPA 24 Implementation – Practical Considerations
- 25. Proprietary & Confidential – Accretive Solutions, Inc. Additional potential efficiency: Flexibility of control activities in SOC 1 and SOC 2 audits enables the overlay of other compliance frameworks, including: PCI ISO HIPAA NIST Cloud Controls Matrix 25 Implementation – Practical Considerations
- 26. Proprietary & Confidential – Accretive Solutions, Inc. Blake Holman 26 Senior Vice President, Chief Information Officer
- 27. Proprietary & Confidential – Accretive Solutions, Inc. Ryan, LLC Global tax services firm founded in 1991 The largest indirect tax practice in North America and the seventh largest corporate tax practice in the United States Offices in 70 cities across 12 countries Provides a comprehensive range of state, local, federal, and international tax advisory and consulting services, including: • Audit defense • Tax recovery • Credits and Incentives • Tax process improvement and automation • Tax appeals • Tax compliance • Strategic planning 27 Company Overview
- 28. Proprietary & Confidential – Accretive Solutions, Inc. Tax recovery work involving credit card transactions (PCI) Tax compliance services work (SAS70 and now SSAE16) • Sales and Use Tax compliance services • Property Tax compliance services 28 IT Compliance Situation
- 29. Proprietary & Confidential – Accretive Solutions, Inc. Security Questionnaires are cumbersome 29 Challenges Audits Costly and time consuming (and they can consume you, if you let them!)
- 30. Proprietary & Confidential – Accretive Solutions, Inc. IT controls are conceptually and fundamentally the same Differences in controls often have to do with the level of rigor you employ in satisfying the controls Poor planning results in burning lots and lots of employee and auditor hours that can simply be avoided IT compliance doesn’t have to be hard Most security questionnaires are similar, though there are some exceptions 30 Lessons Learned
- 31. Proprietary & Confidential – Accretive Solutions, Inc. Line up the strictest standards and controls that you have to comply, and set your program from those Decide when you want to be doing audits Try to get one provider to do as much of your audit work for you as you can to gain economies of scale • The IT Controls scale VERY well Work with your auditor to streamline the process Don’t release security information without a mutual NDA Save the answers to security questionnaires Prepare a security position document, if you can – it may help streamline inquiries 31 Takeaways
- 32. Proprietary & Confidential – Accretive Solutions, Inc. 1 annual PCI audit 2 annual SSAE16 audits PCI controls govern vast majority of the IT controls work Kick off in early September, fieldwork in October/November and reports produced in December Result – focused audit efforts, fieldwork is done once for all three audits, and the IT controls reporting for SSAE16 is leveraged for both reports, enabling many other benefits, including being: • Cost effective • Scalable • Improved profit margin for the firm 32 At Ryan
- 33. Proprietary & Confidential – Accretive Solutions, Inc. Moving towards a more strategic IT Compliance organization and deploying an integrated framework to address multiple compliance requirements will: Drive sales / revenue by: • Providing a competitive advantage and securing a seat at the table • Increasing client and investor confidence in internal controls • Enhancing internal operational control to facilitate growth Increase bottom line by: • Reducing compliance costs • Freeing up staff audit support time to concentrate on business needs 33 Wrap Up
- 34. Proprietary & Confidential – Accretive Solutions, Inc. 34 REMINDER You must fill out the CPE Evaluation for credit. UPCOMING WEBINARS Latest SEC Initiatives and Impacts Relating to Accounting and Audit Practices Techniques to avoid having financial reports flagged for investigation by the SEC Cloud Security Understanding key security implications of the migration of software to the cloud, both as a seller and a user of cloud technologies. Organizational Change Management Locking down big hidden costs of Company Change Thank You
