Adding credentials
•Download as DOCX, PDF•
0 likes•160 views
Add credentials to Active Directory Health Profiler
Report
Share
Report
Share
Recommended
More Related Content
Viewers also liked
Viewers also liked (13)
windows server 2008 active directory recovery step by step

windows server 2008 active directory recovery step by step
Chapter 4 configuring and managing the dns server role

Chapter 4 configuring and managing the dns server role
Step by Step Installation of Microsoft SQL Server 2012 

Step by Step Installation of Microsoft SQL Server 2012
Similar to Adding credentials
Similar to Adding credentials (9)
Healthcare Dashboards: 3 Keys for Creating Effective and Insightful Executive...

Healthcare Dashboards: 3 Keys for Creating Effective and Insightful Executive...
Recently uploaded
Recently uploaded (20)
How to Check CNIC Information Online with Pakdata cf

How to Check CNIC Information Online with Pakdata cf
Event-Driven Architecture Masterclass: Integrating Distributed Data Stores Ac...

Event-Driven Architecture Masterclass: Integrating Distributed Data Stores Ac...
The Ultimate Prompt Engineering Guide for Generative AI: Get the Most Out of ...

The Ultimate Prompt Engineering Guide for Generative AI: Get the Most Out of ...
AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)

AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)
Frisco Automating Purchase Orders with MuleSoft IDP- May 10th, 2024.pptx.pdf

Frisco Automating Purchase Orders with MuleSoft IDP- May 10th, 2024.pptx.pdf
The Zero-ETL Approach: Enhancing Data Agility and Insight

The Zero-ETL Approach: Enhancing Data Agility and Insight
Design and Development of a Provenance Capture Platform for Data Science

Design and Development of a Provenance Capture Platform for Data Science
Event-Driven Architecture Masterclass: Challenges in Stream Processing

Event-Driven Architecture Masterclass: Challenges in Stream Processing
Microsoft CSP Briefing Pre-Engagement - Questionnaire

Microsoft CSP Briefing Pre-Engagement - Questionnaire
Six Myths about Ontologies: The Basics of Formal Ontology

Six Myths about Ontologies: The Basics of Formal Ontology
Intro to Passkeys and the State of Passwordless.pptx

Intro to Passkeys and the State of Passwordless.pptx
WebRTC and SIP not just audio and video @ OpenSIPS 2024

WebRTC and SIP not just audio and video @ OpenSIPS 2024
Adding credentials
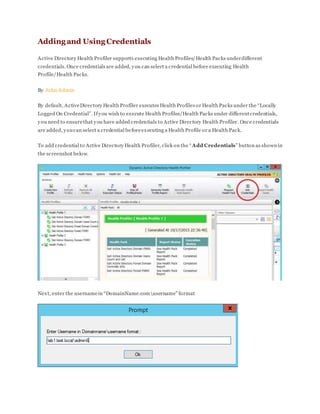
- 1. Adding and Using Credentials Active Directory Health Profiler supports executing Health Profiles/Health Packs underdifferent credentials. Once credentials are added, you can select a credential before executing Health Profile/Health Packs. By John Admin By default, ActiveDirectory Health Profiler executes Health Profiles or Health Packs under the “Locally Logged On Credential”. Ifyou wish to execute Health Profiles/Health Packs under differentcredentials, you need to ensurethat you have added credentials to Active Directory Health Profiler. Once credentials are added, youcan select a credential beforeexecuting a Health Profile or a Health Pack. To add credential to Active Directory Health Profiler, click on the “Add Credentials” button as shown in the screenshot below. Next, enter the usernamein “DomainName.comusername” format
- 2. And user password. In case you need to add multiple credentials, please repeat above steps. Using Credential: To executea Health Profile or a Health Pack under different credential, follow below steps: 1. Select Health Profile or Health Pack. 2. Select the credential as shown in the red circle ofthe below screenshot 3. Right Click on the Health Profile/Health Pack and then click o n the “Execute” action to execute Health Profile/Health Pack under the selected credential.
- 3. Note:Active Directory Health Profiler stores credentials in an encryptedfile that is stored in .DPConfig folder. ***
