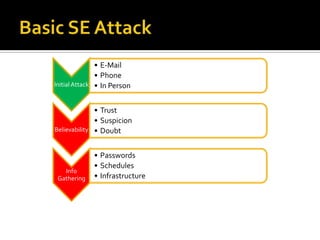
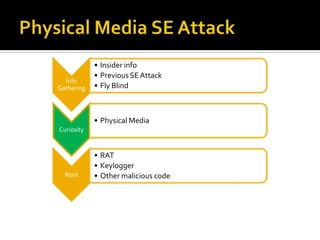
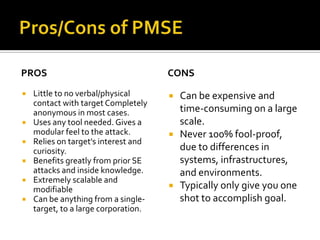
Physical media social engineering (PMSE) involves using removable media like CDs and USB drives to gain access to information on a target system or network. It acts as a physical Trojan by dropping malicious payloads onto client systems. PMSE plays on people's curiosity by providing interesting media that also installs malware without direct contact. The presenter tested a PMSE attack using 100 infected CDs containing malware that provided a meterpreter shell on 53 machines, with admin access on 37 XP systems without security software. While PMSE provides anonymity and flexibility, it also requires resources and may only succeed the first try against a target.