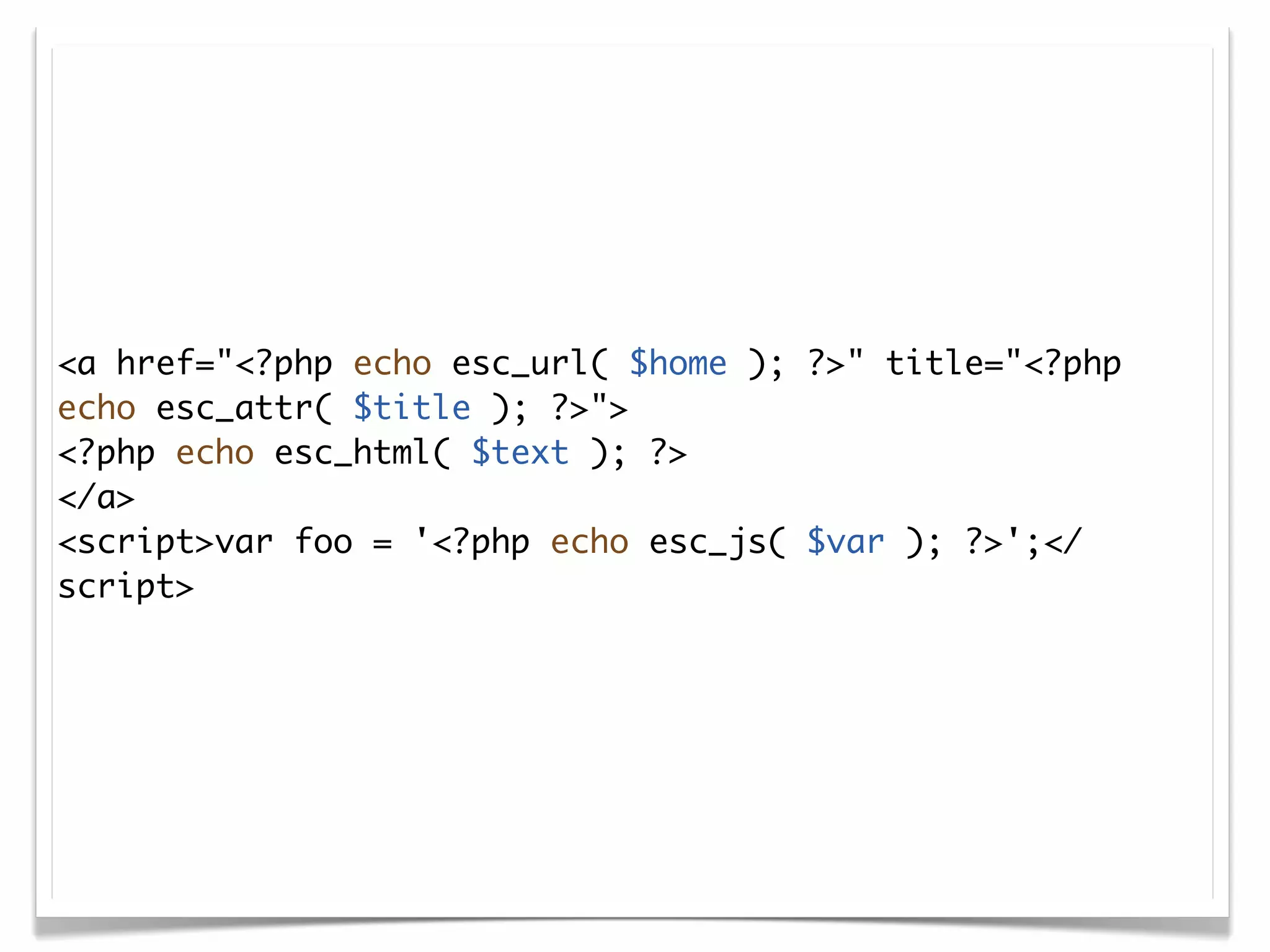
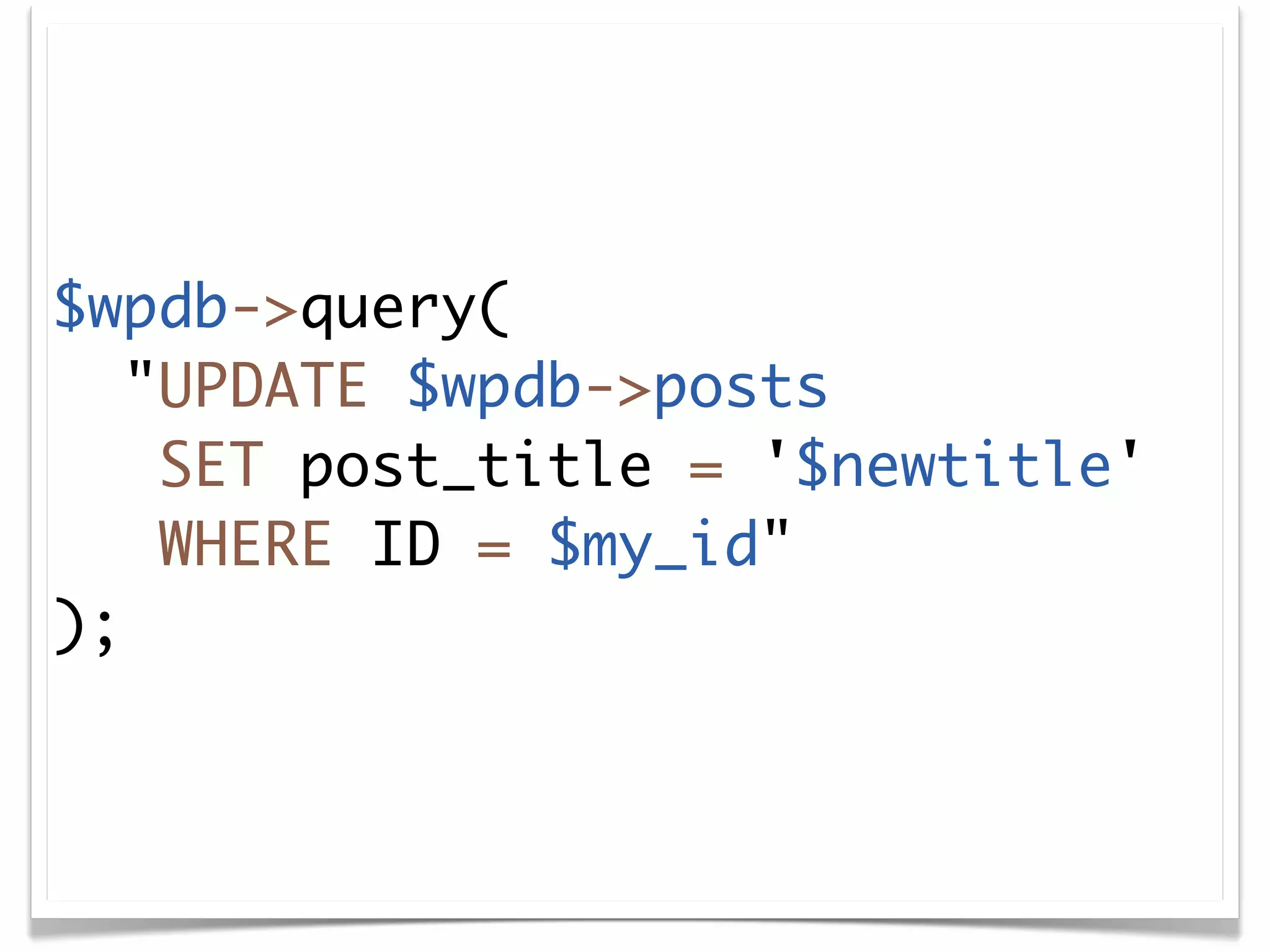
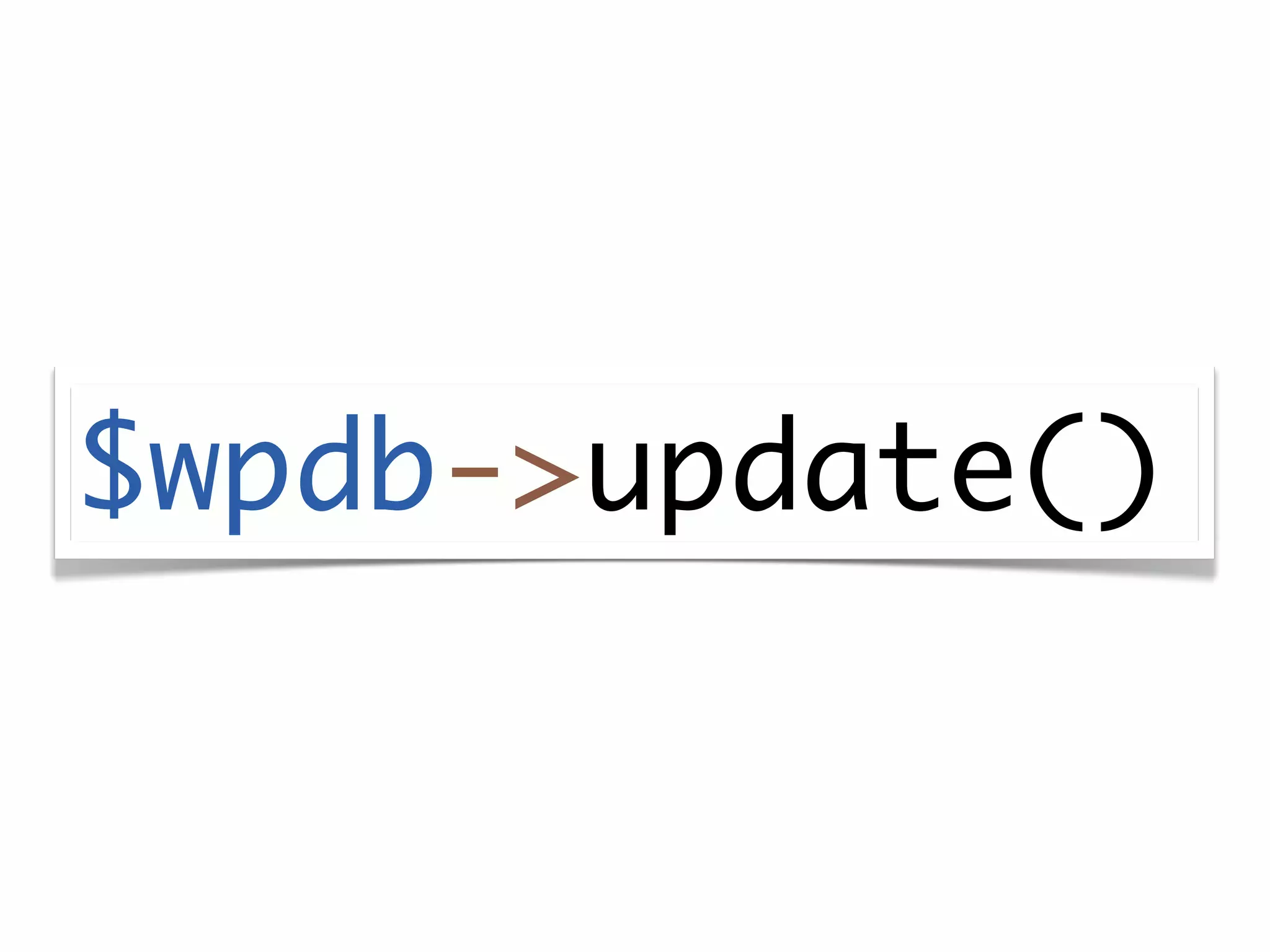
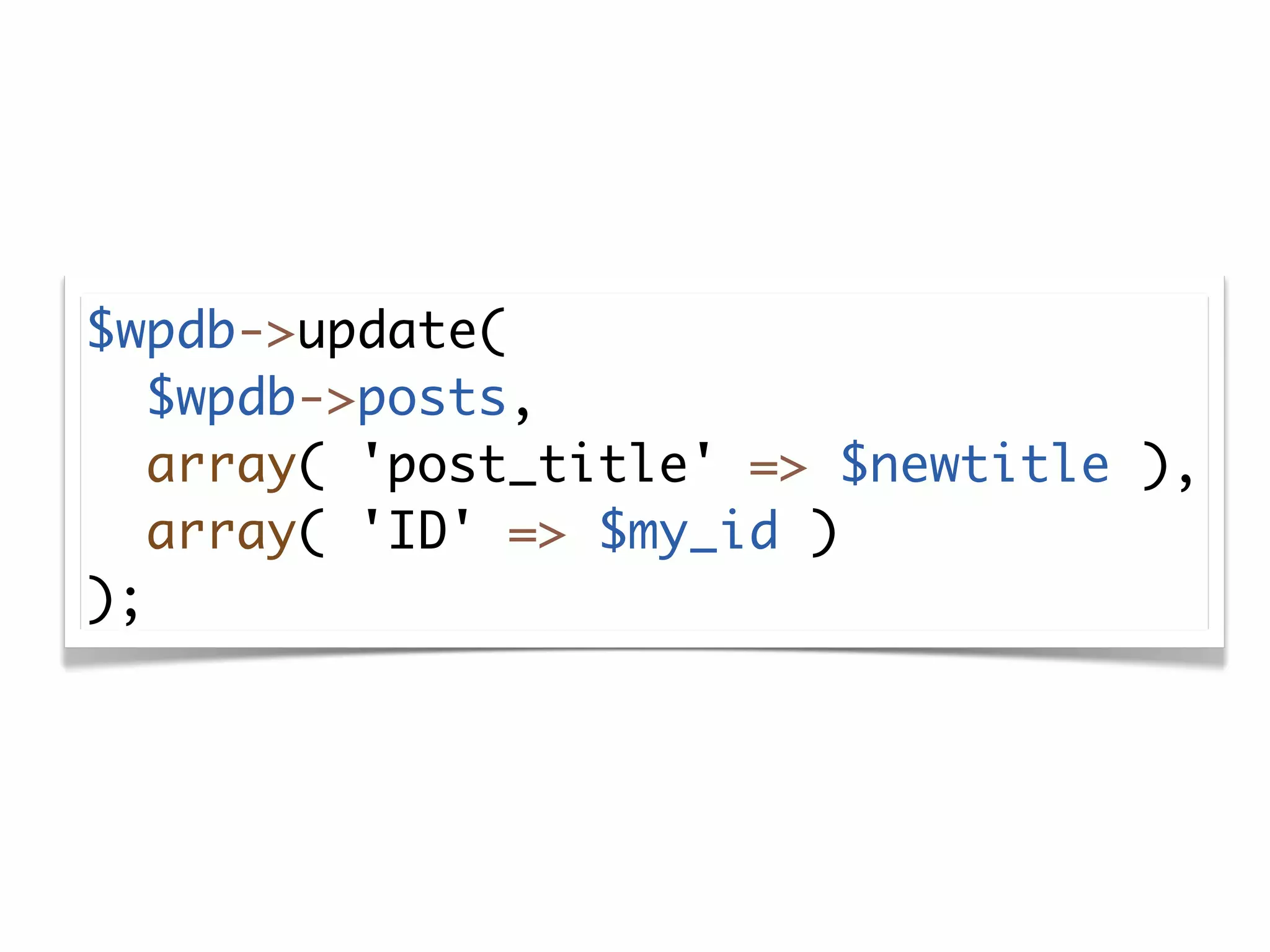
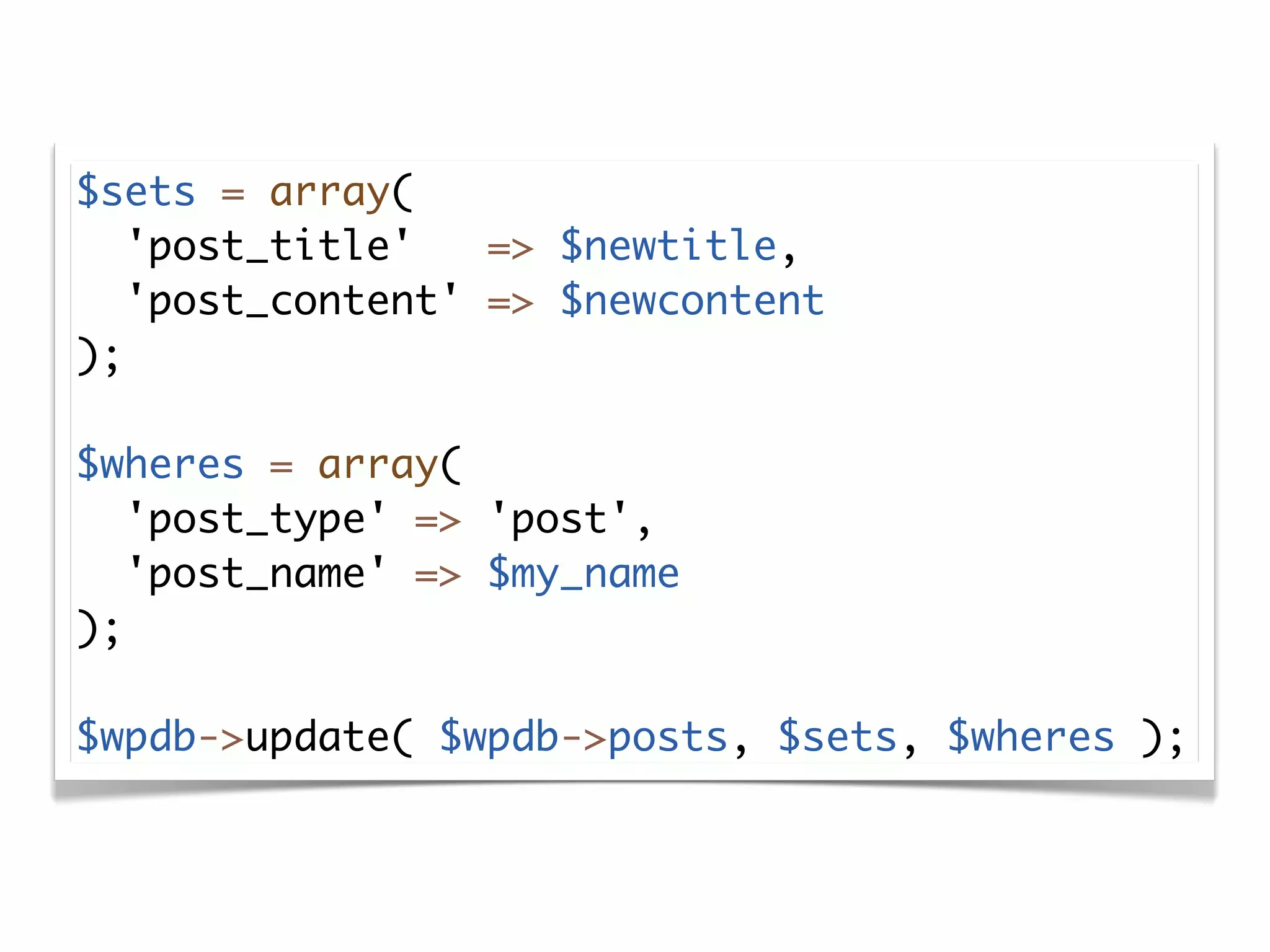
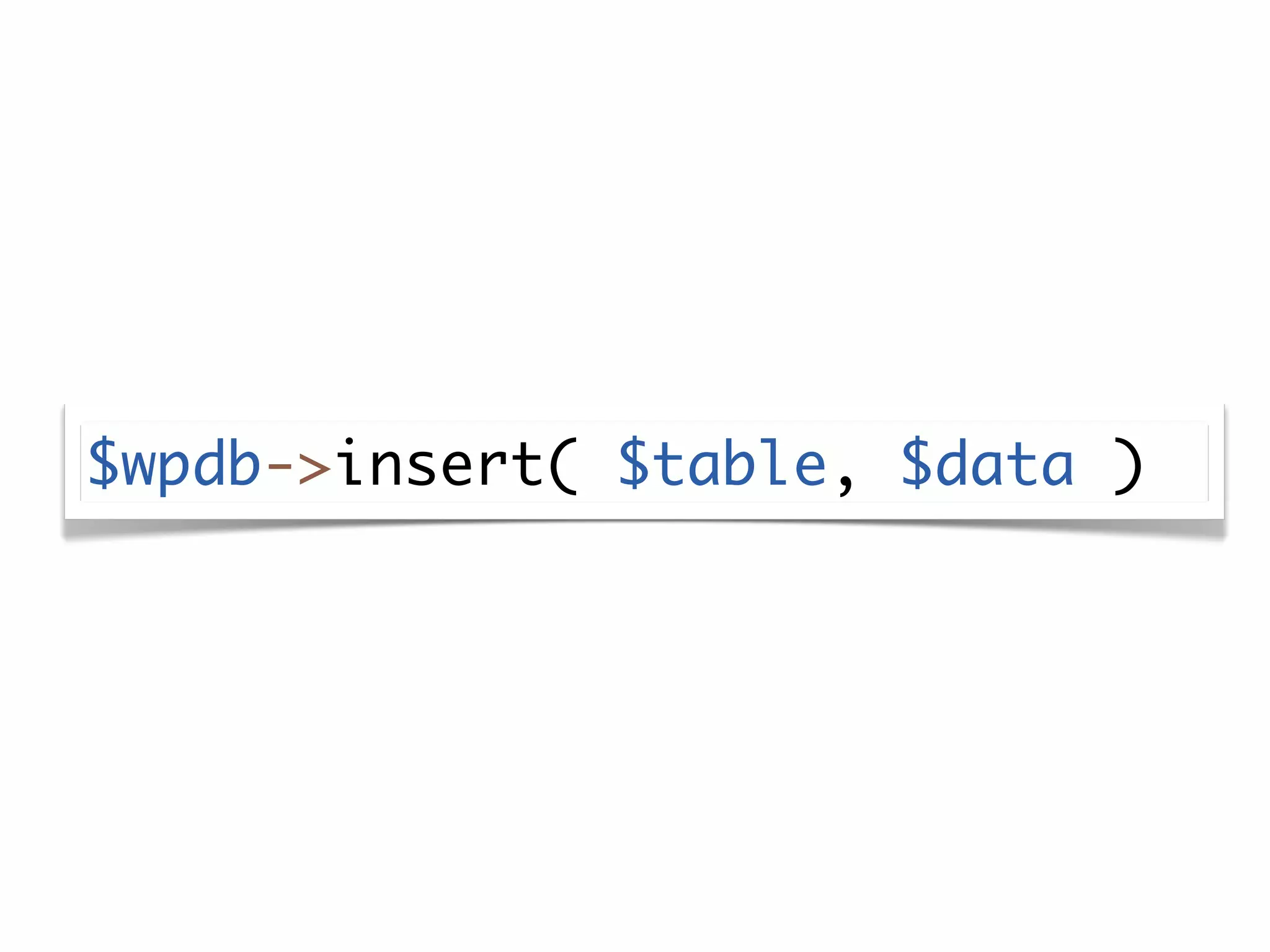
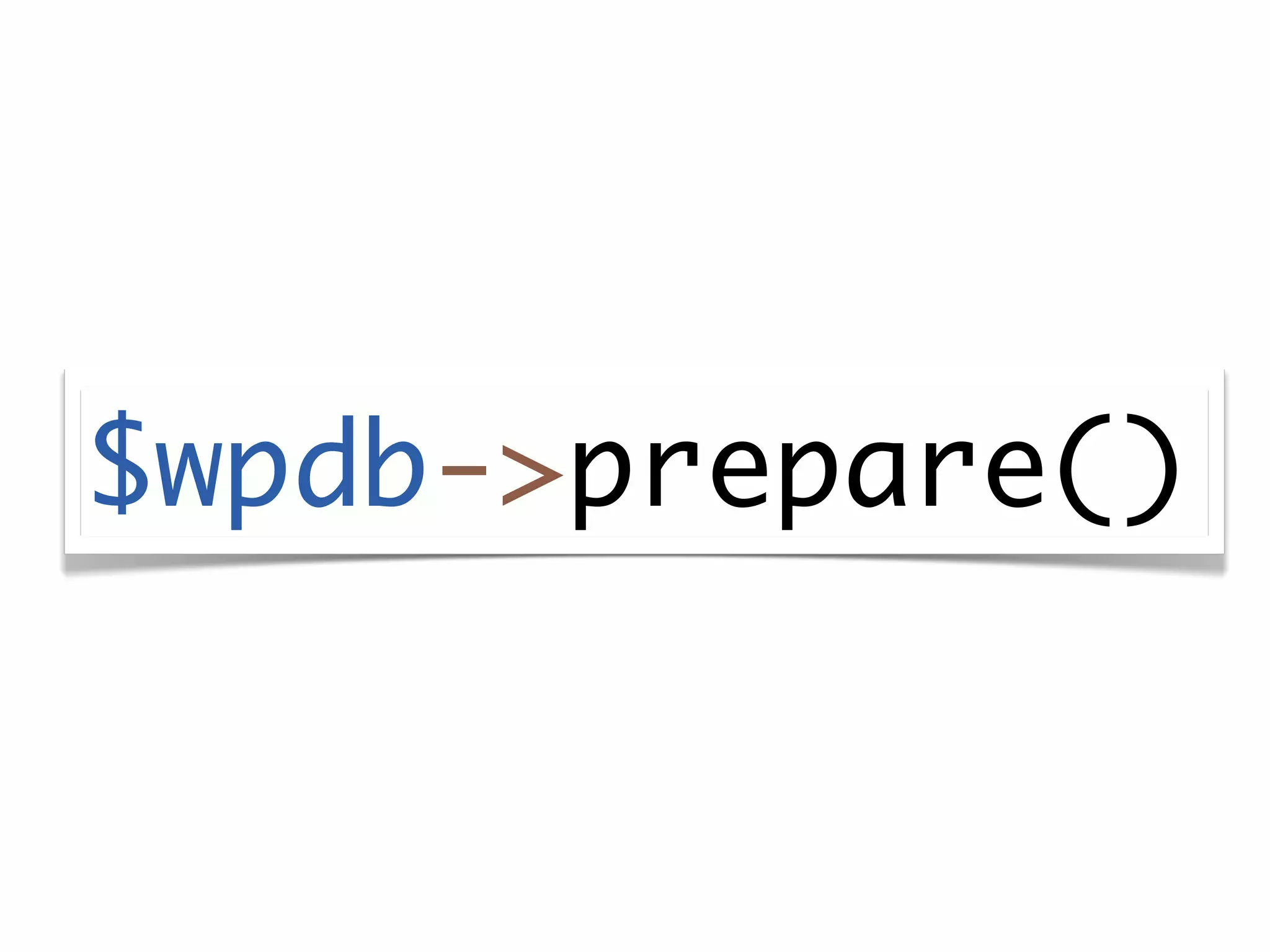
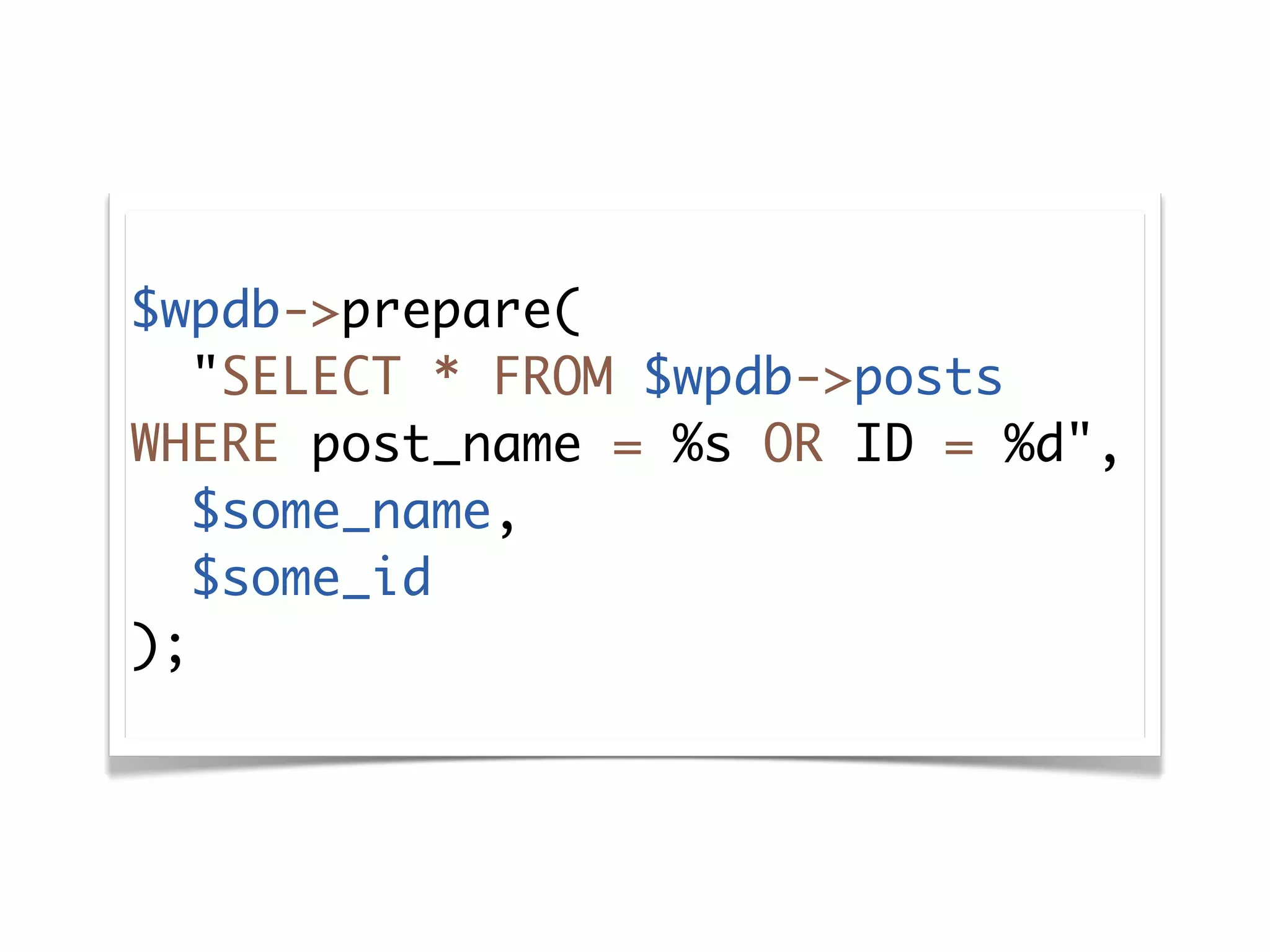
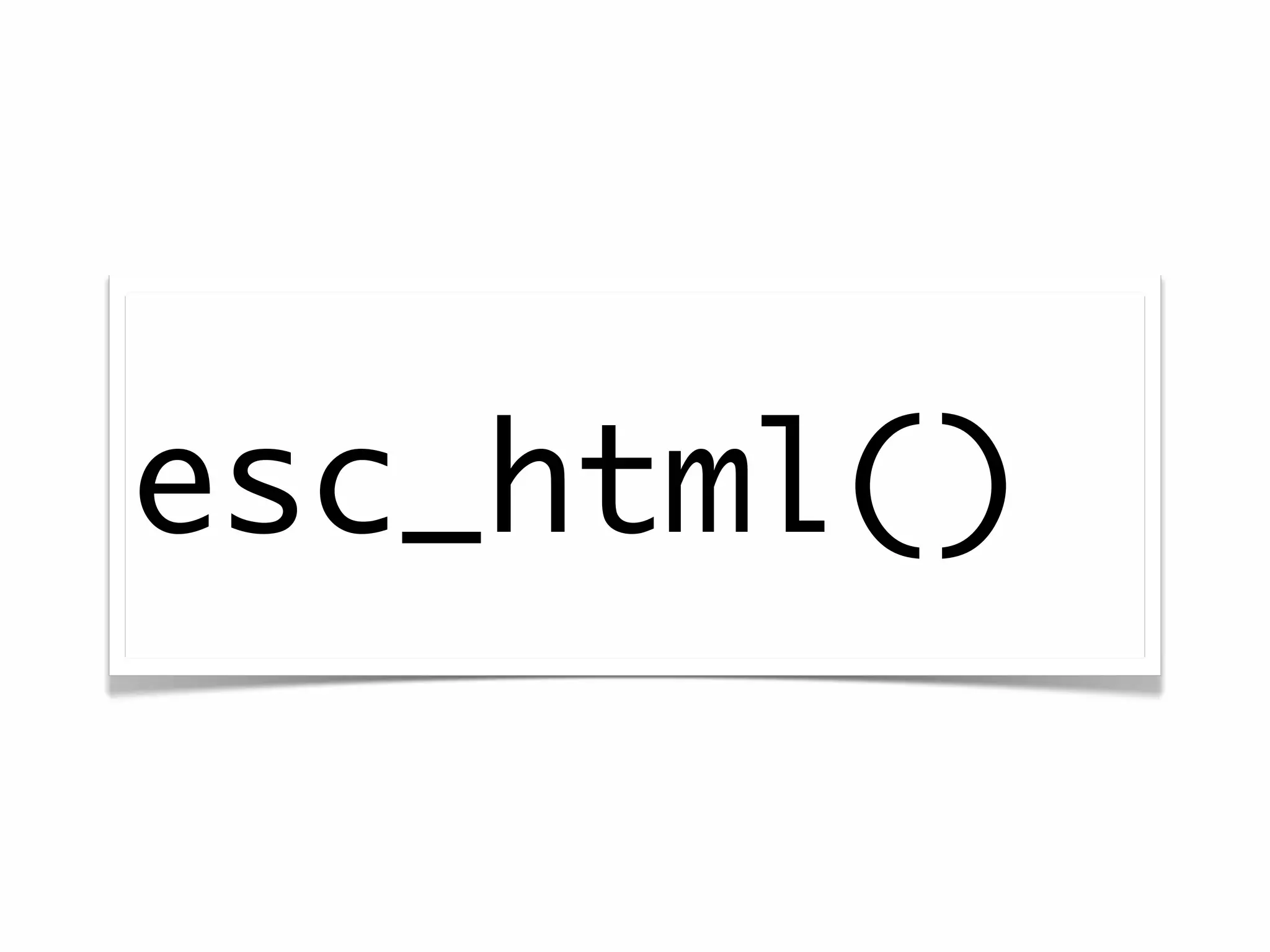
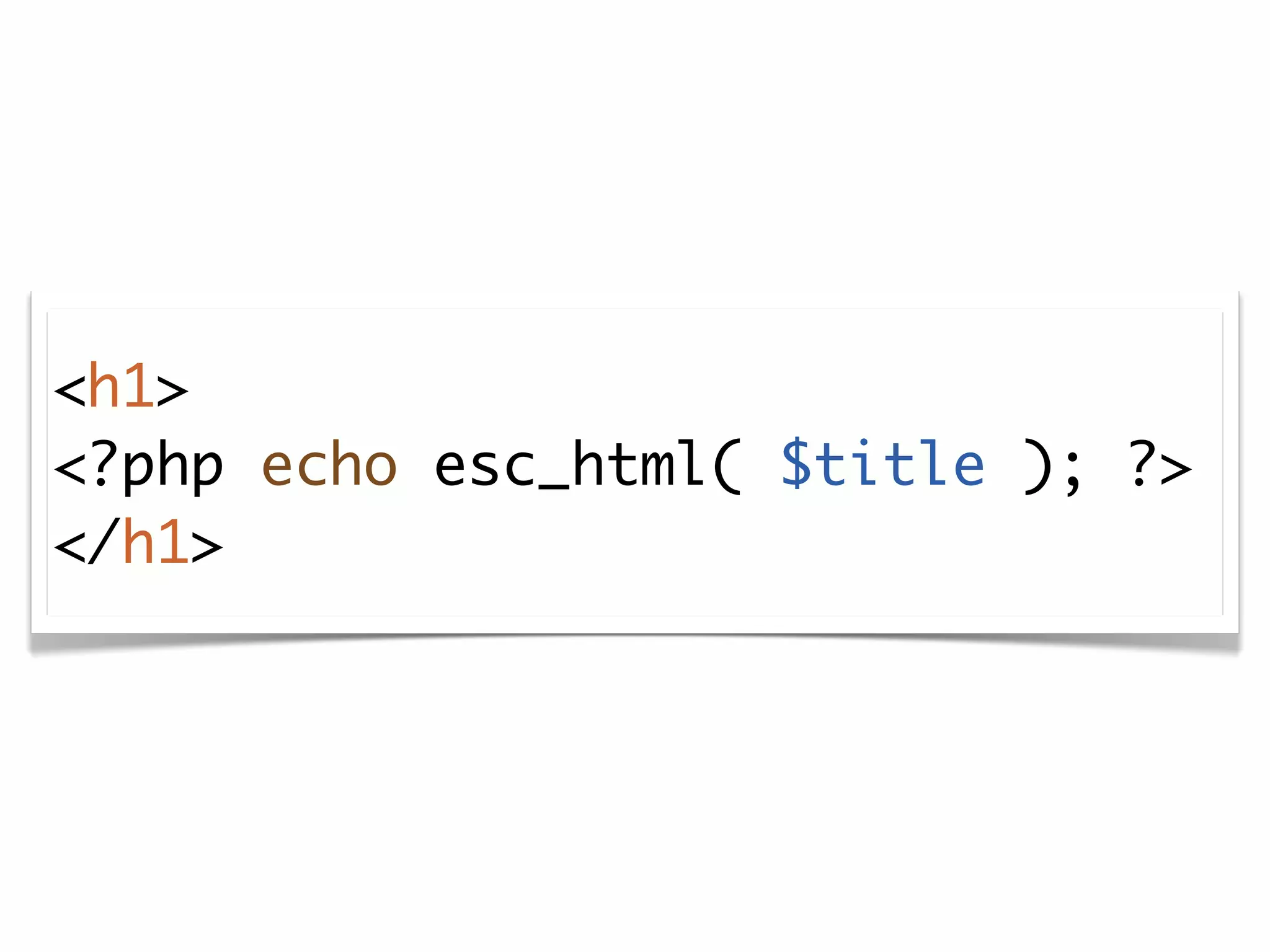
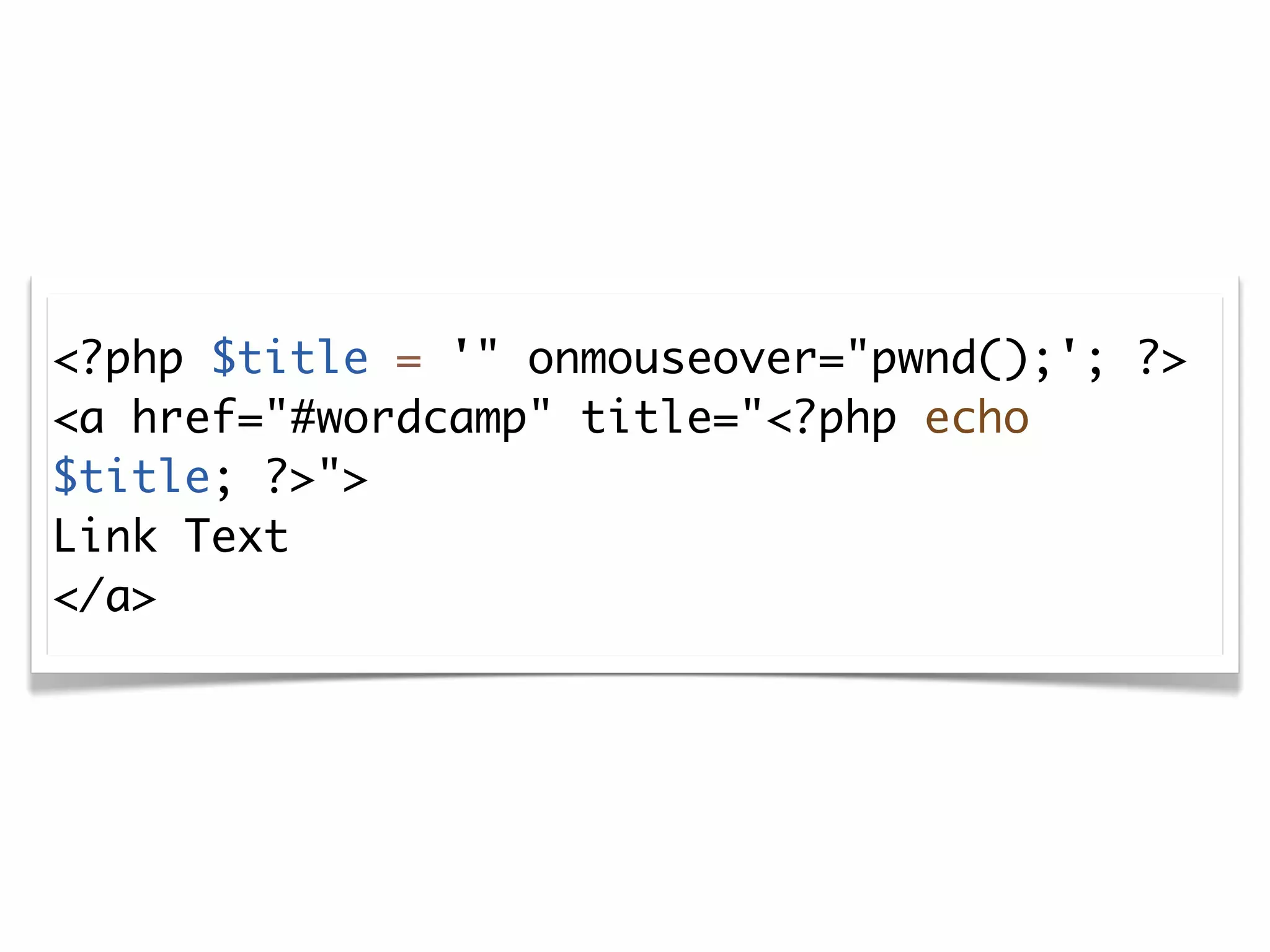
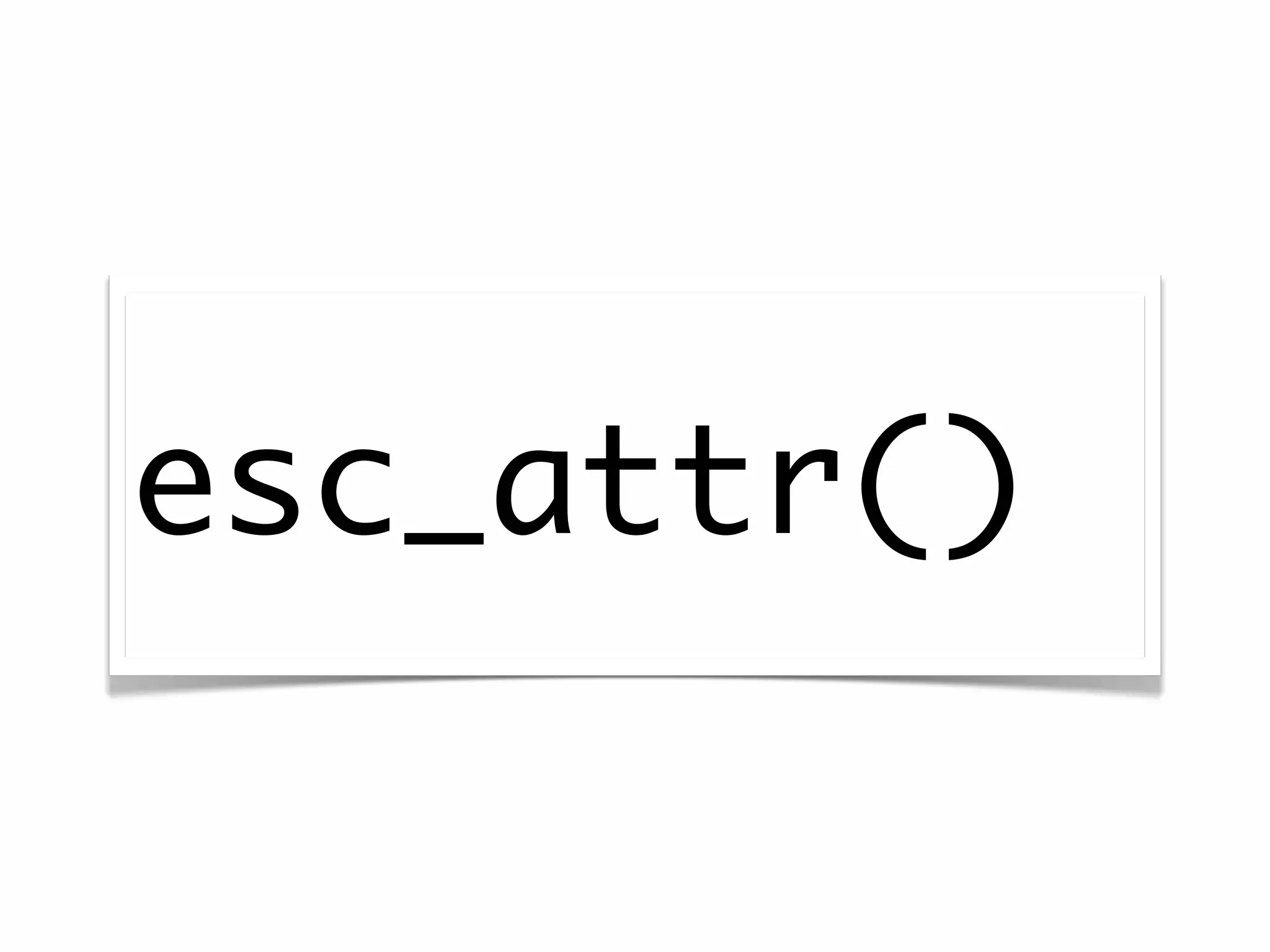
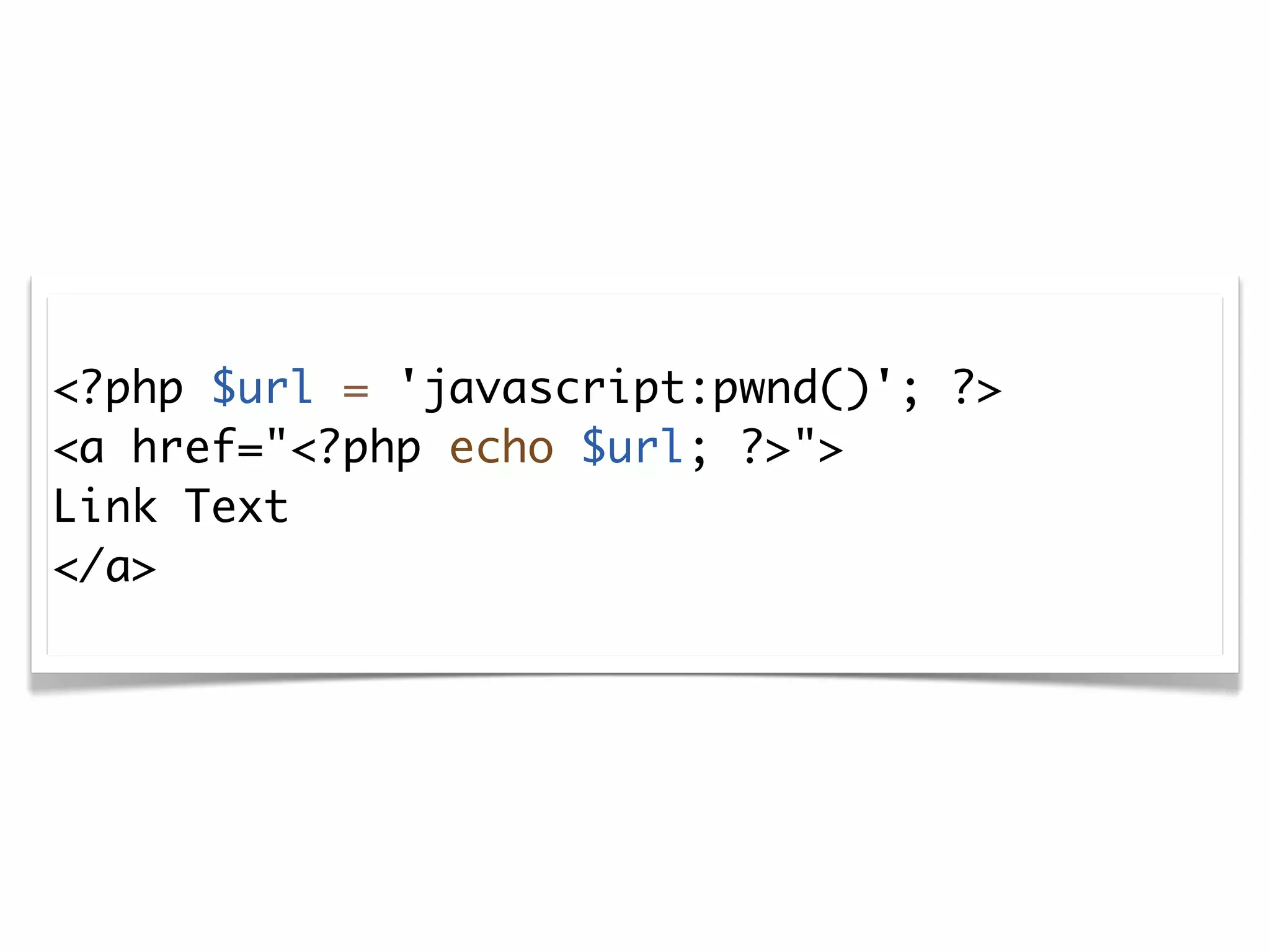
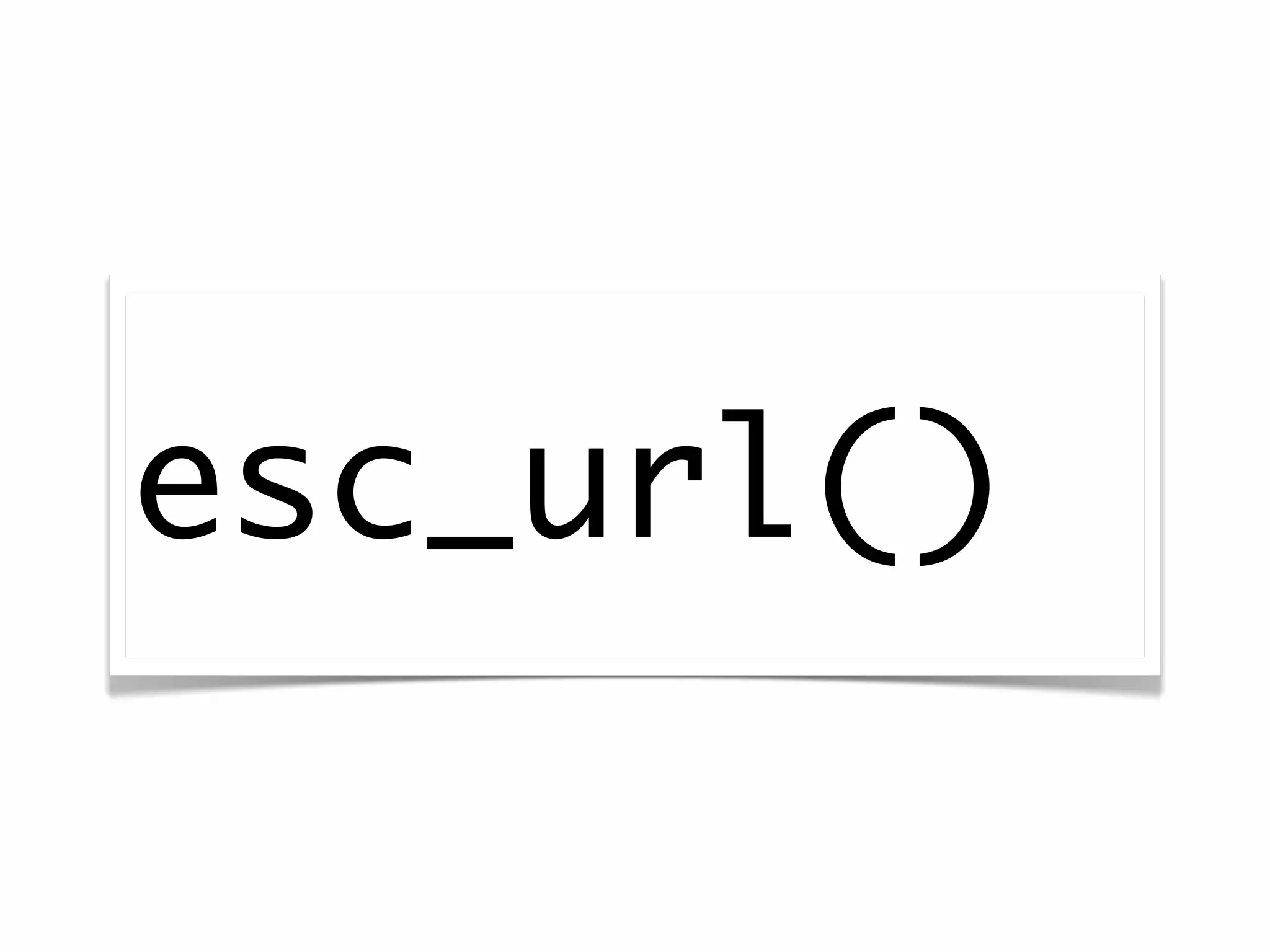
The document discusses secure coding practices for WordPress plugins. It outlines three common attacks - SQL injection, XSS (cross-site scripting), and CSRF (cross-site request forgery). For each attack, it provides examples of insecure code and explains how to make the code secure using techniques like escaping output, validating input, and using nonces. It also discusses some common mistakes to avoid, like using eval() and not sanitizing variables before output. The goal is to teach developers how to thwart attacks and code more securely.















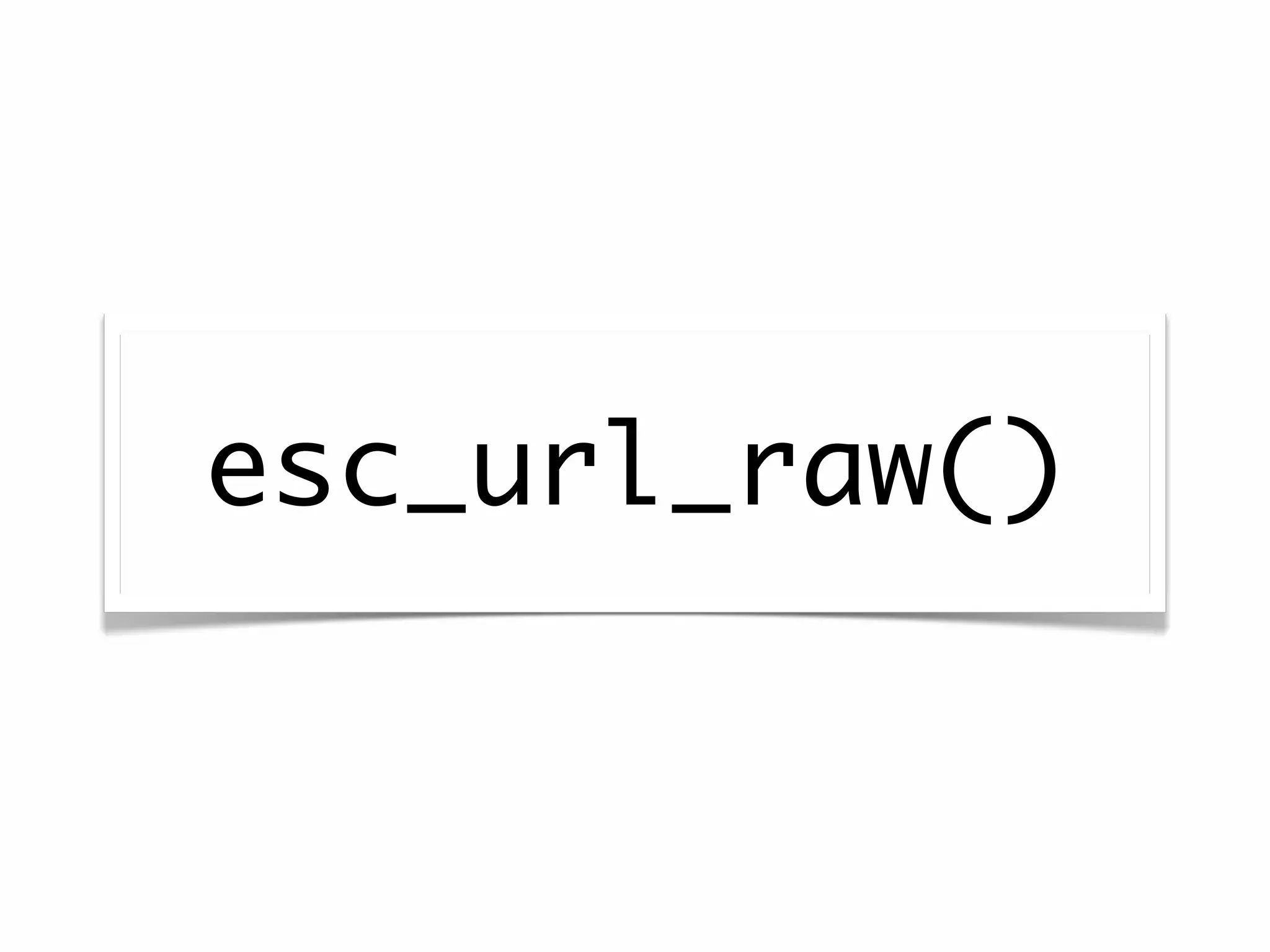

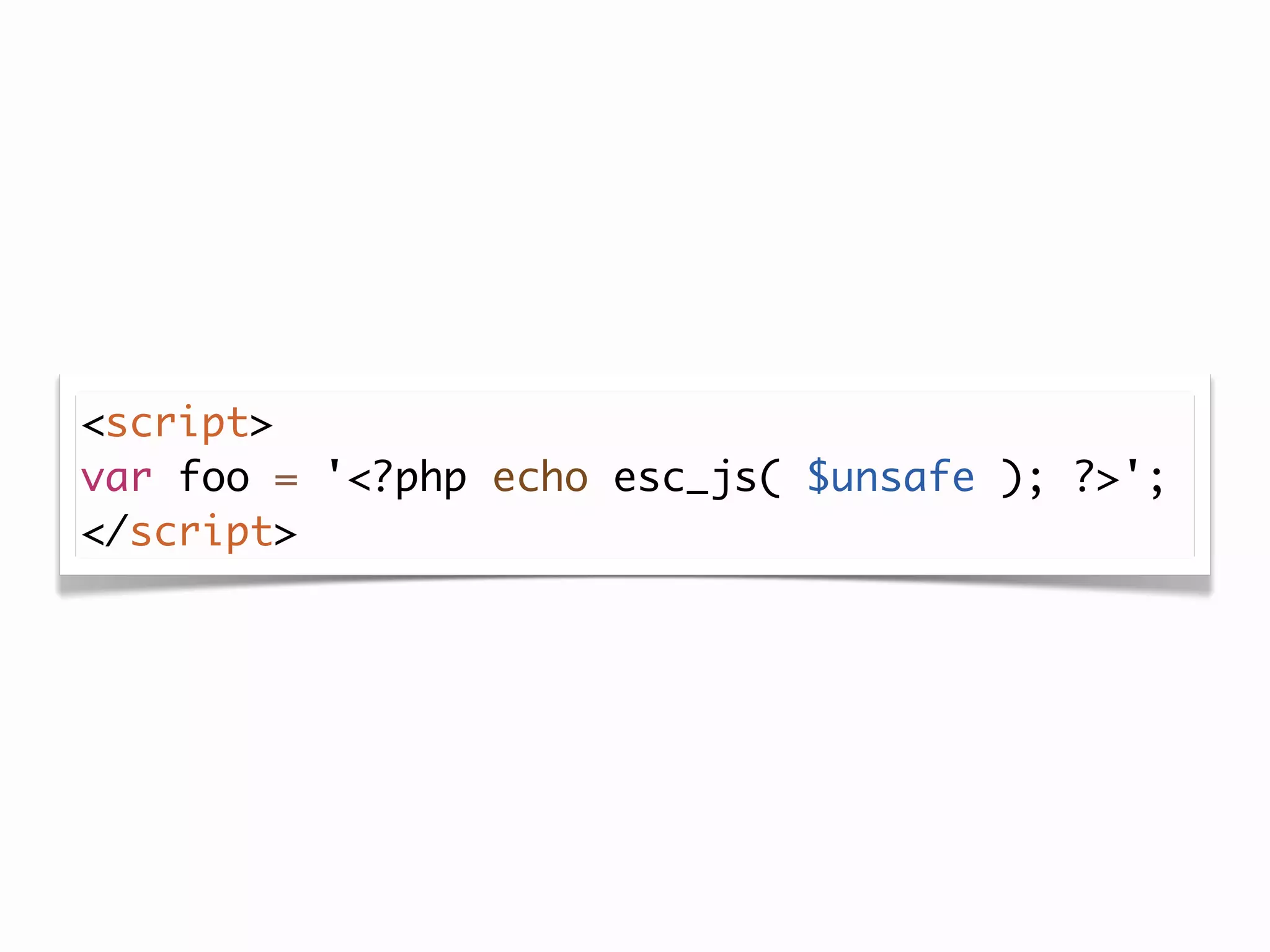
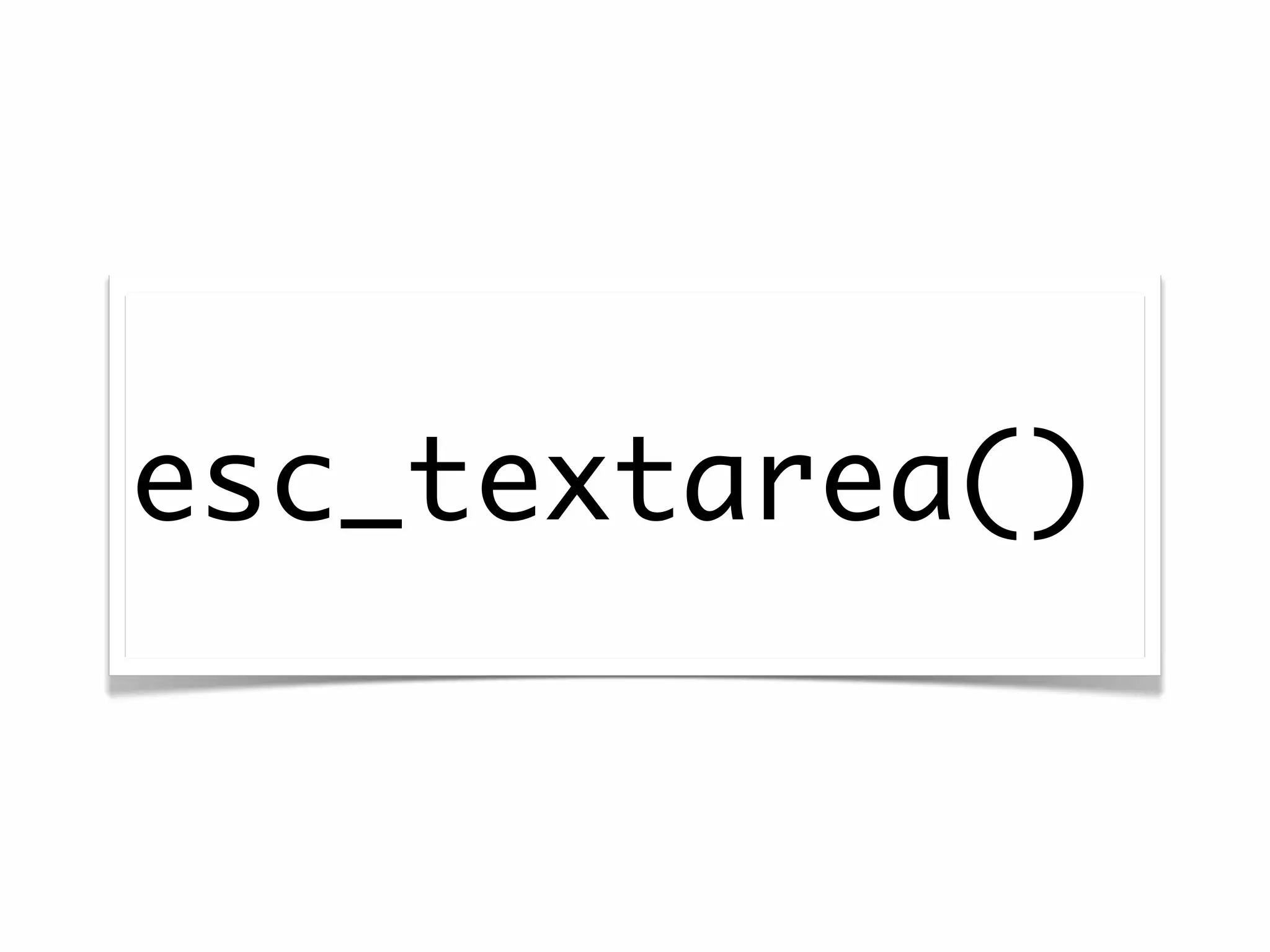
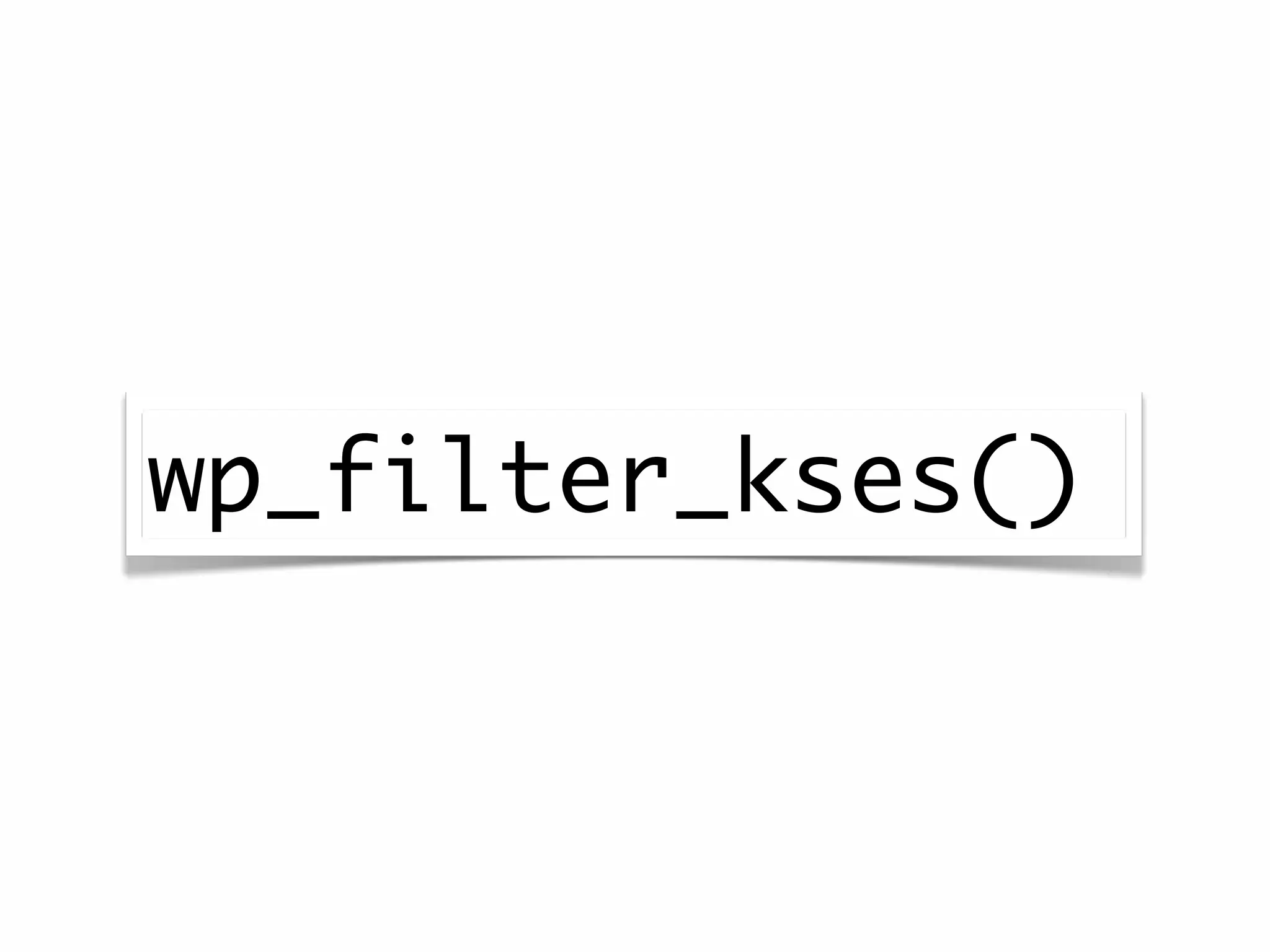








![<form action="<?php echo $_SERVER['REQUEST_URI']; ?>">](https://image.slidesharecdn.com/wordpresssecurity-wordcampphoenix-110129131232-phpapp02/75/WordPress-Security-WordCamp-Phoenix-48-2048.jpg)