1) WordPress themes and plugins are often vulnerable to security issues like SQL injection and XSS due to a lack of sanitization and escaping of user input.
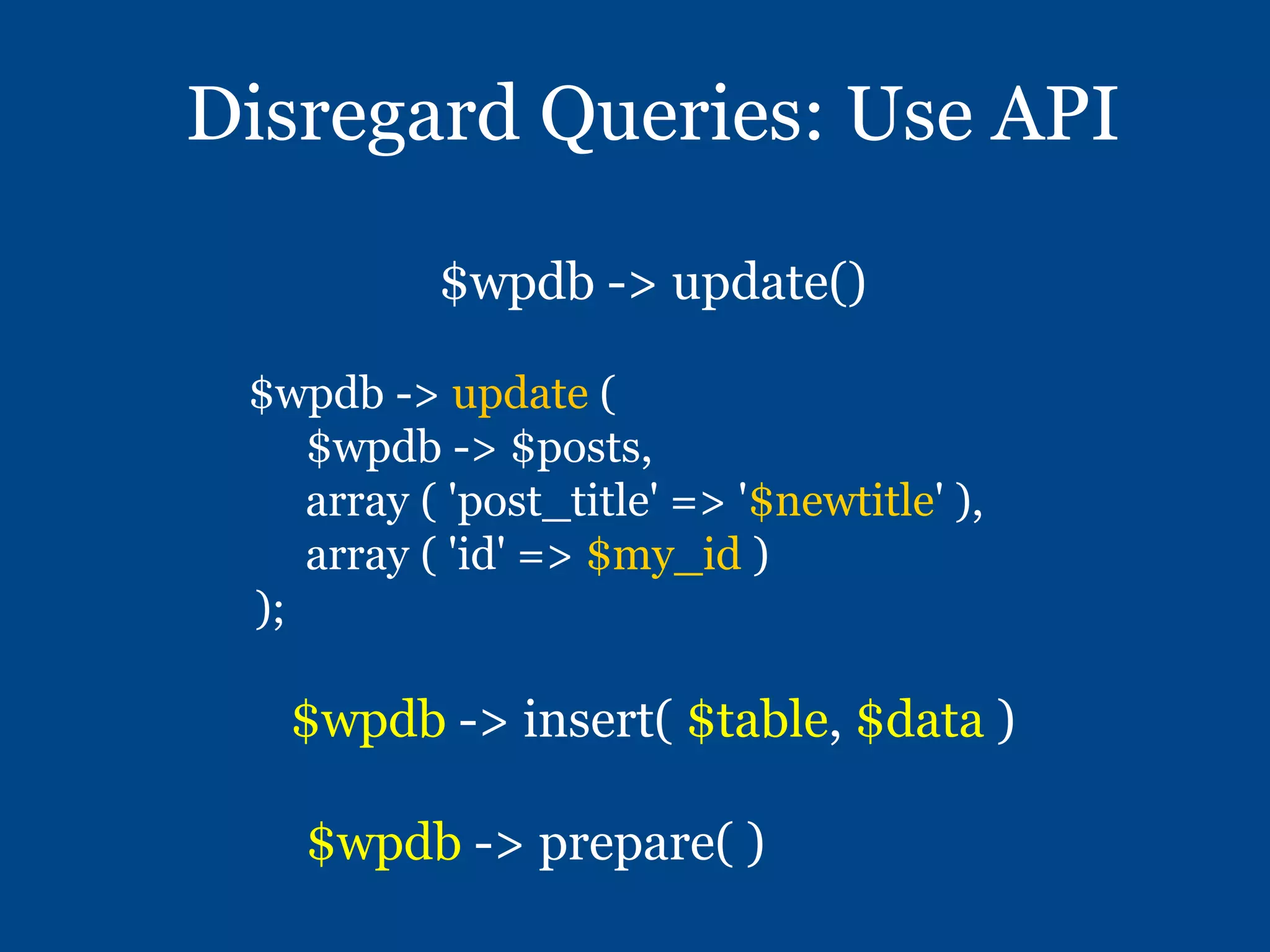
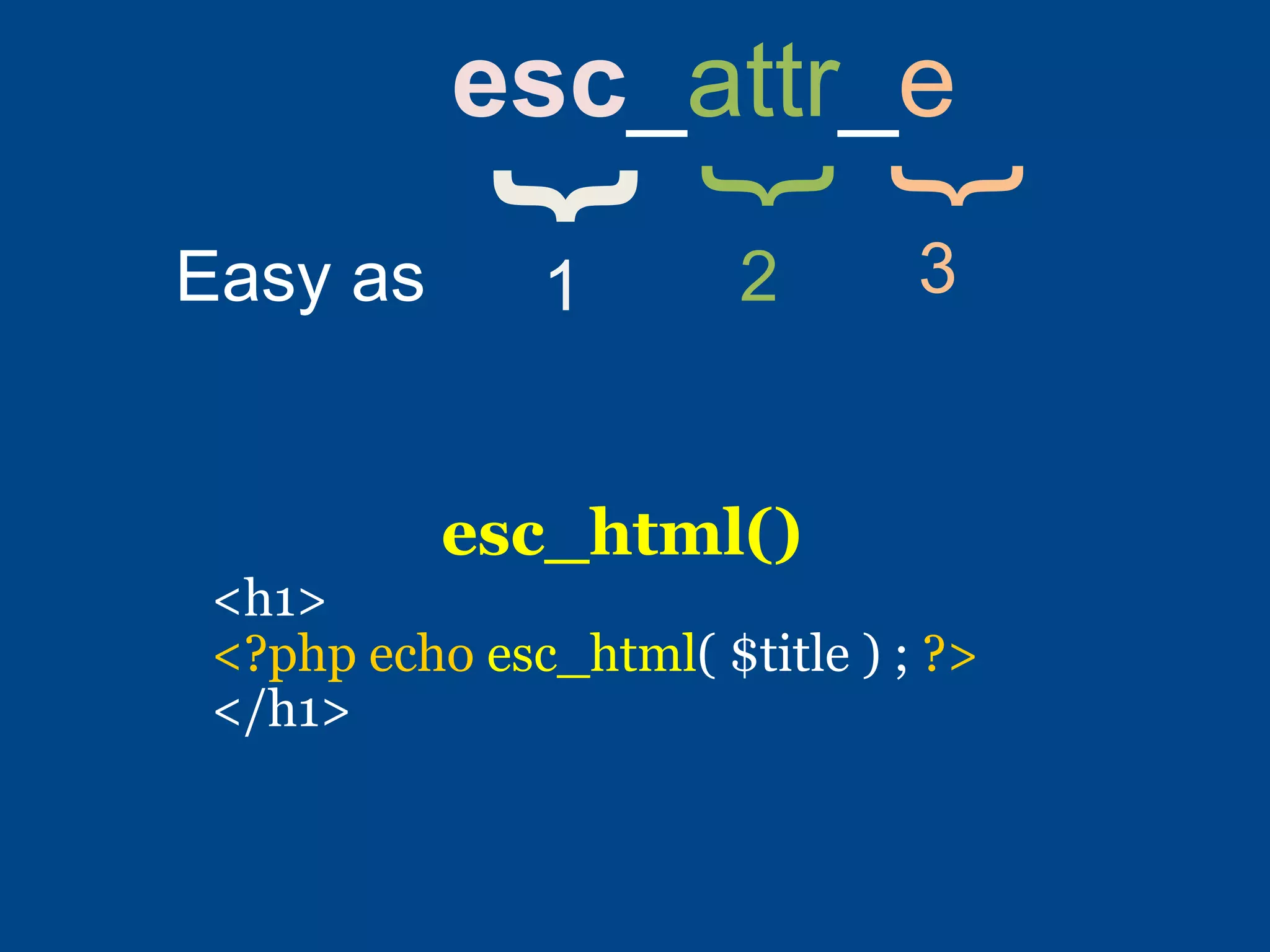
2) Proper sanitization and output escaping is important - sanitize early and escape late. The WPDB class and esc_* functions help prevent SQL injection, while esc_html(), esc_attr(), esc_url() and related functions help prevent XSS.
3) Nonces should be used for authentication and verification of intentions for actions like form submissions to prevent CSRF attacks. Common mistakes like eval() and revealing server variables can also cause vulnerabilities.
















![Some mistakes
eval()
<form action= '' <?php echo
$_SERVER['REQURES_URI']; ?> '' >](https://image.slidesharecdn.com/buildingsecuredwordpressthemesandplugins-180501070631/75/Building-secured-wordpress-themes-and-plugins-19-2048.jpg)


