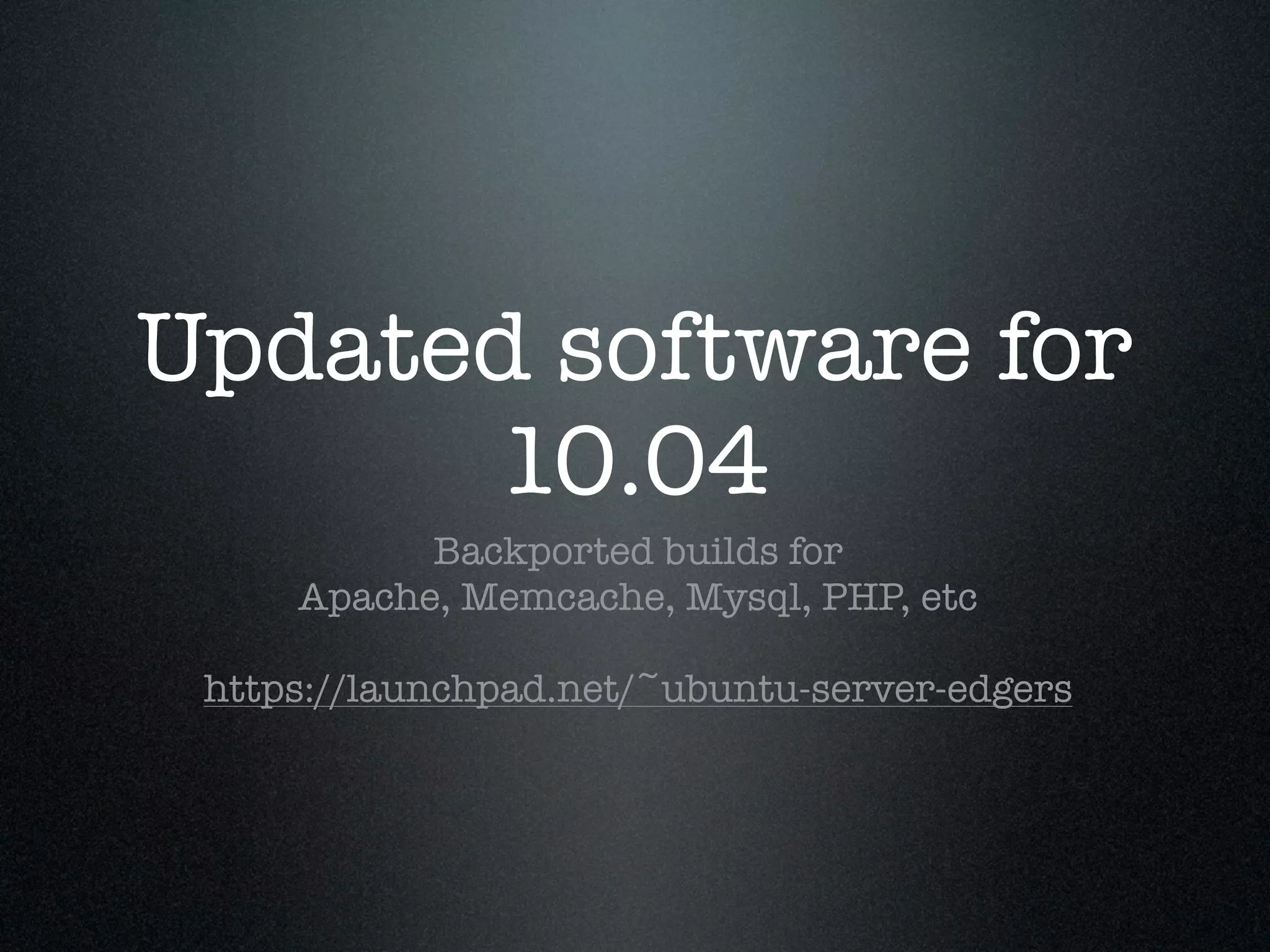
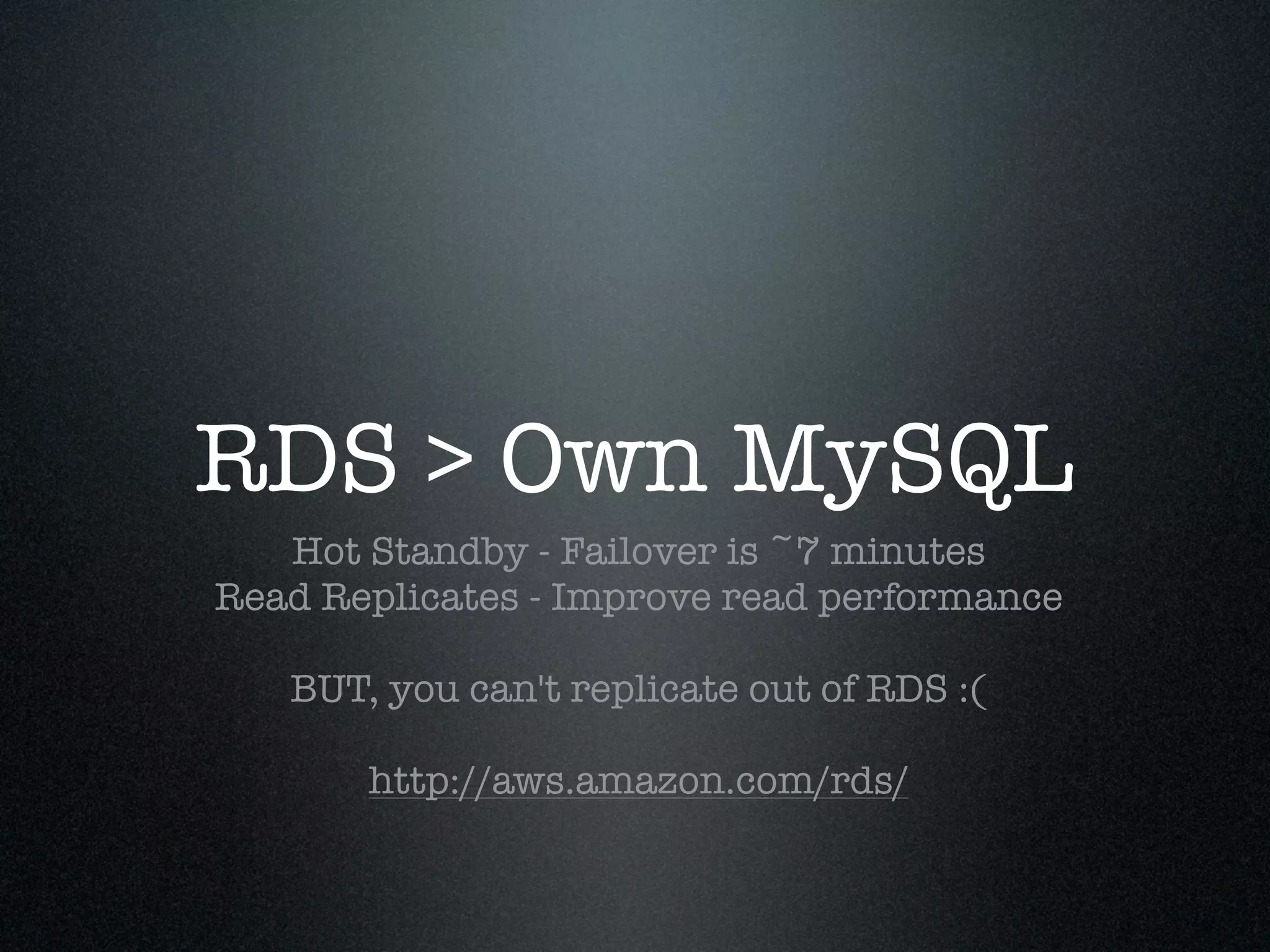
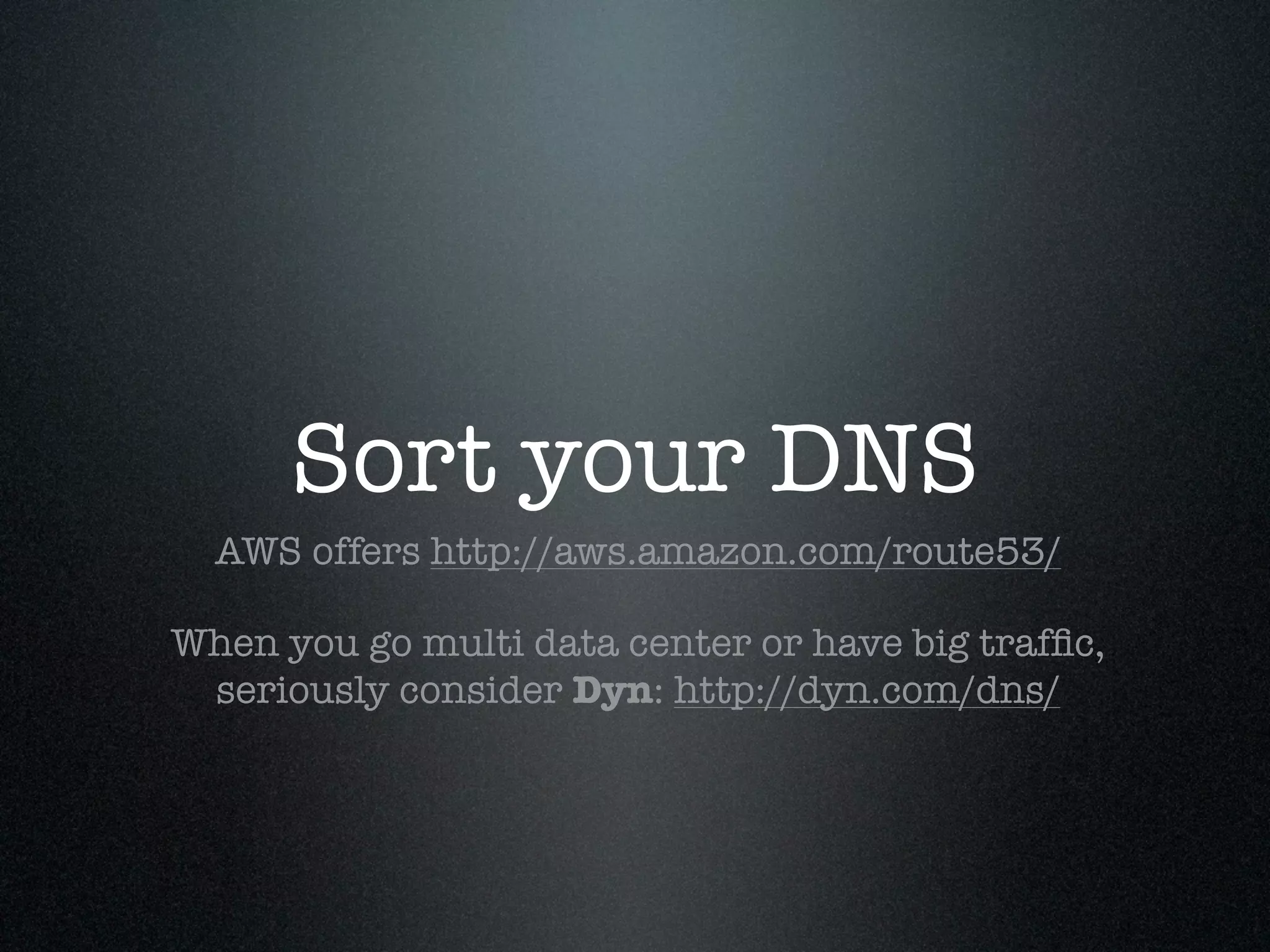
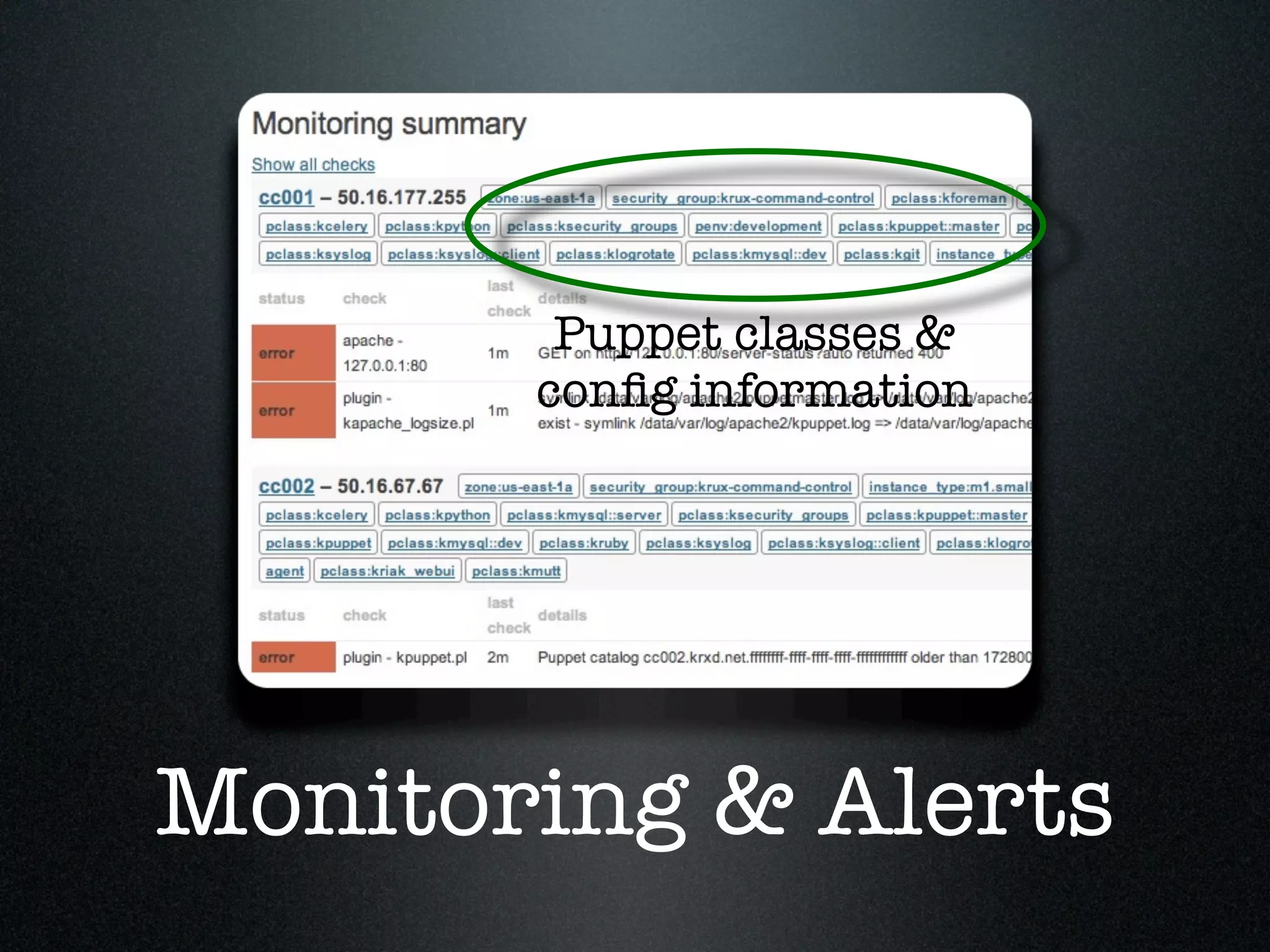
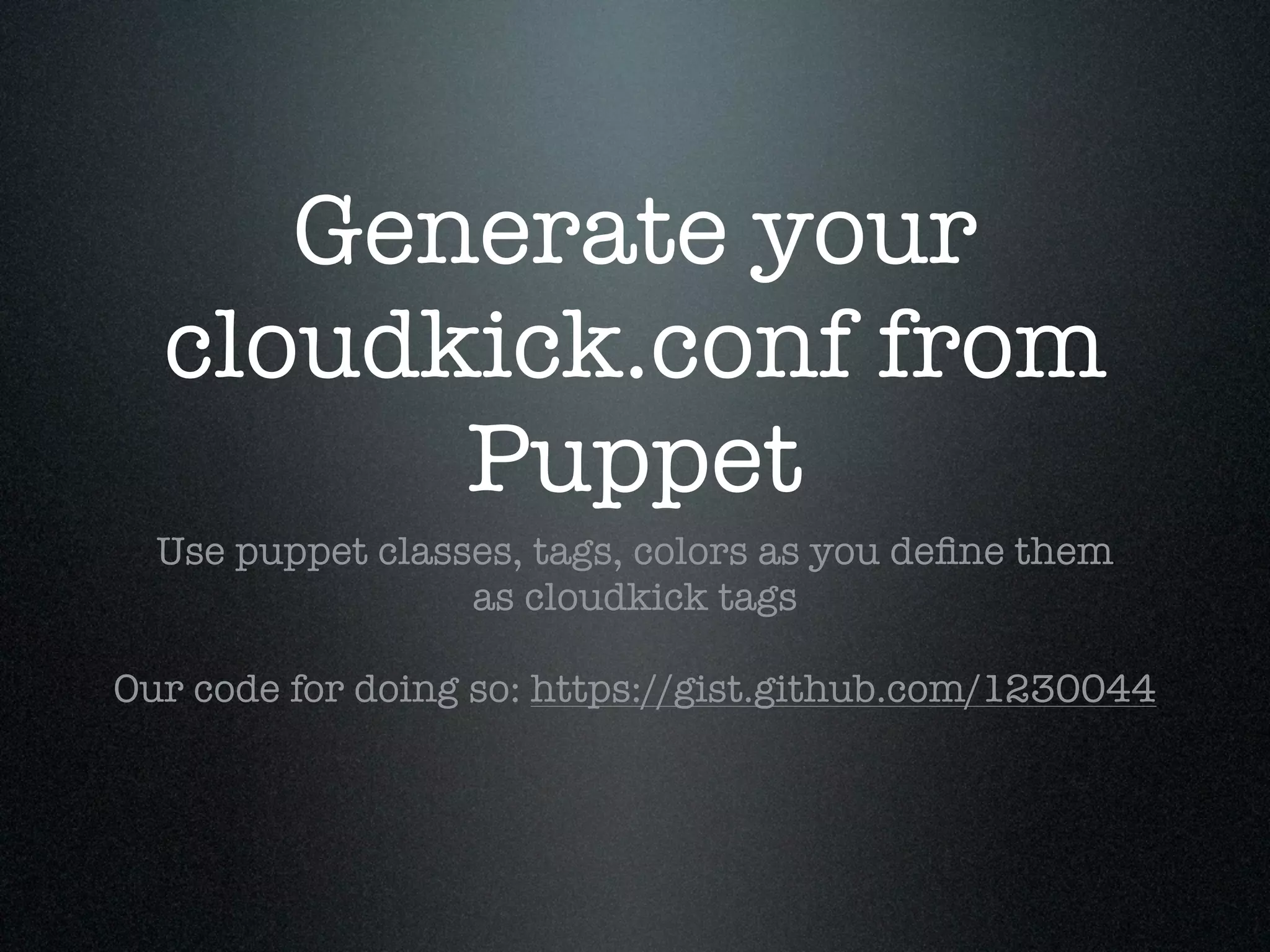
Krux operates a large infrastructure serving thousands of user requests per second. They use Puppet and tools like Cloudkick, Foreman, Boto, and Vagrant to manage their infrastructure in an automated and scalable way. Their Puppet configuration is split into modules, environments, and datacenters. They launch AWS nodes programmatically and configure them with Puppet. Cloudkick is used for monitoring and parallel SSH. Boto allows full Python API access to AWS. Vagrant allows consistently provisioning development machines locally. Automation and external configuration enable their small operations team to manage a large, dynamic infrastructure.































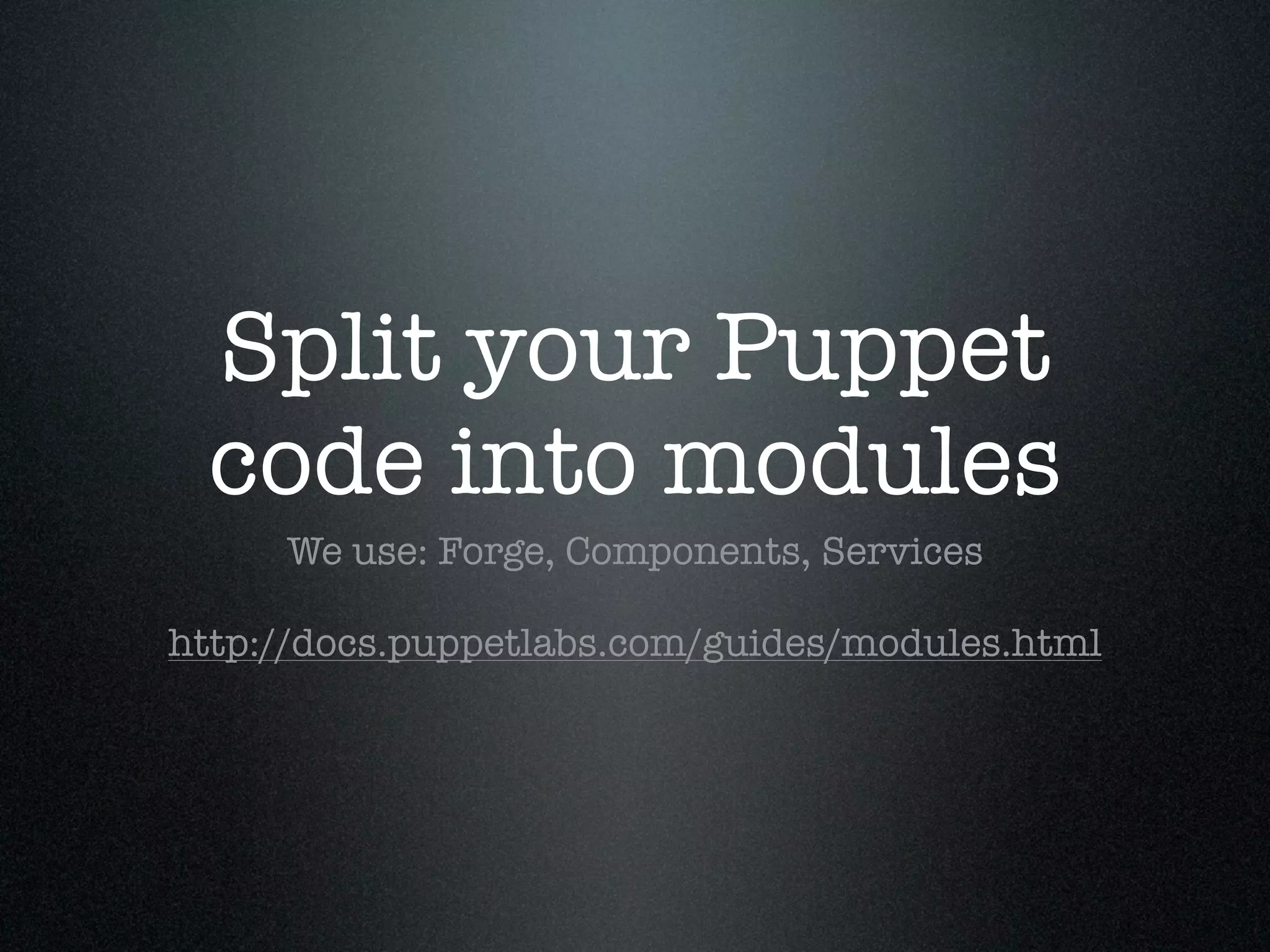
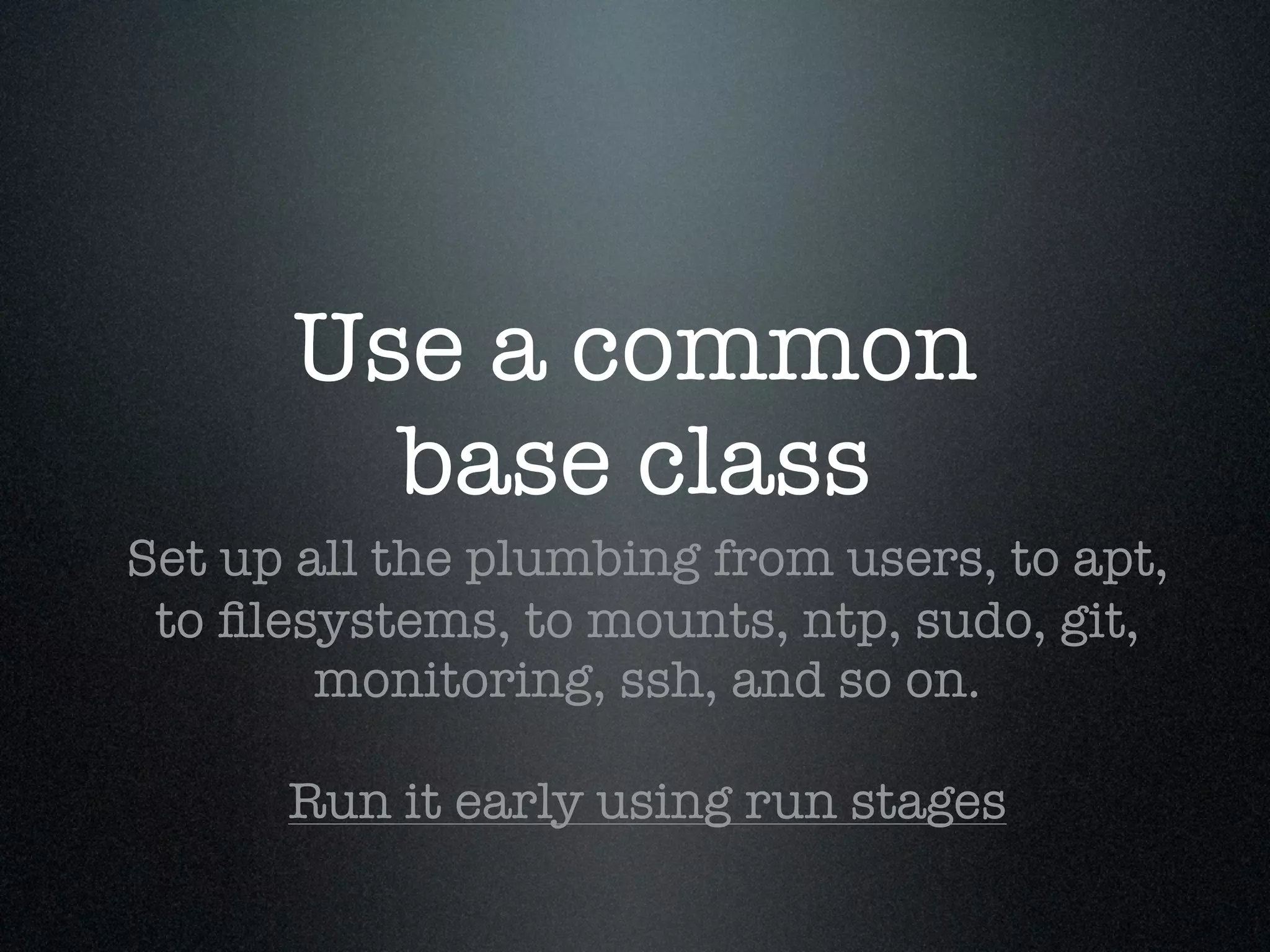
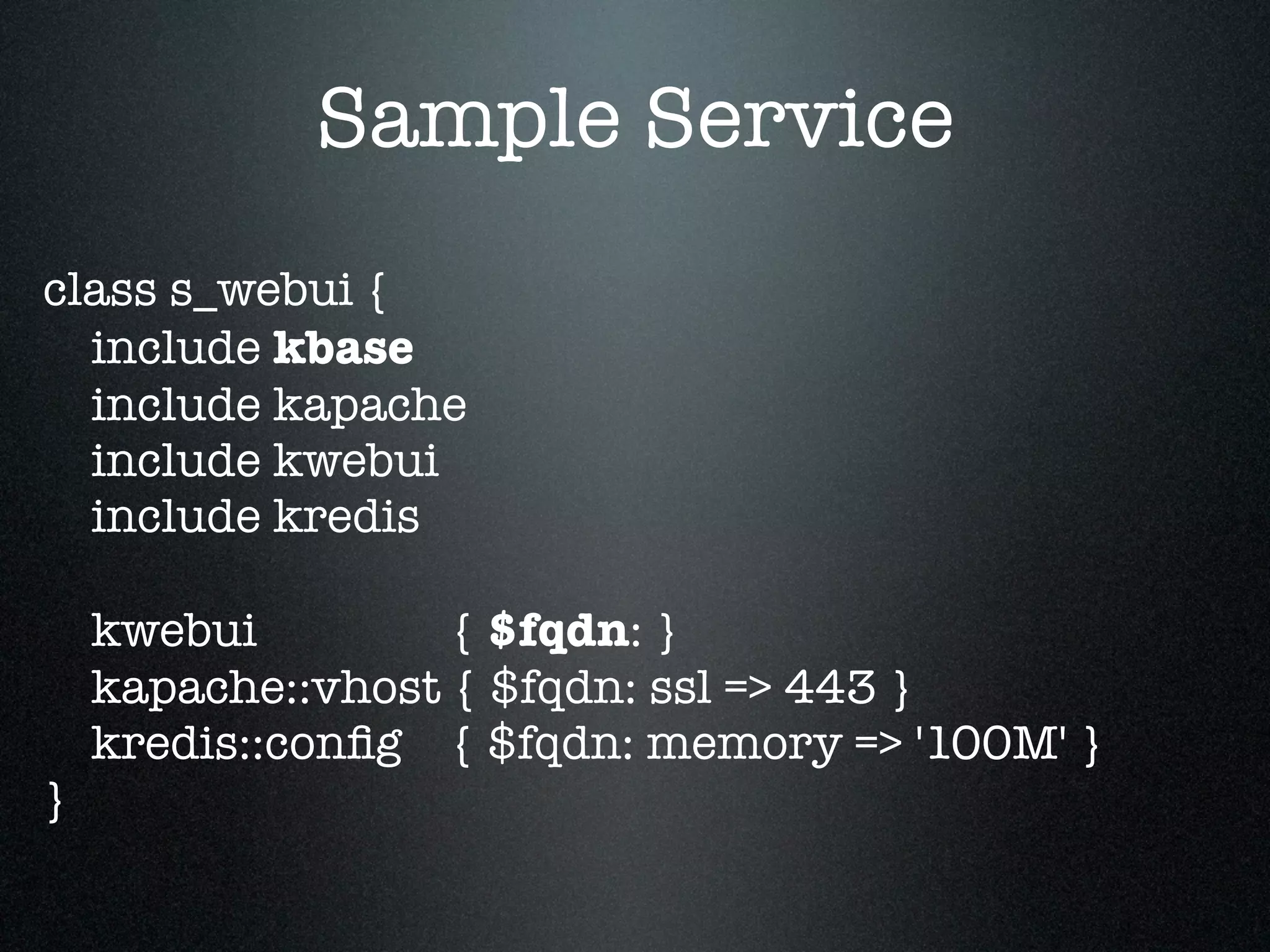
![Use seperate init.pp,
params.pp & config.pp
Params.pp so you can include variables from elsewhere
Config.pp lets you specify:
kfoo::config { $fqdn } in a service
and require:
Kfoo::Config[ $fqdn ] in the component
http://docs.puppetlabs.com/guides/modules.html](https://image.slidesharecdn.com/aws101-110922174148-phpapp01/75/One-Man-Ops-41-2048.jpg)





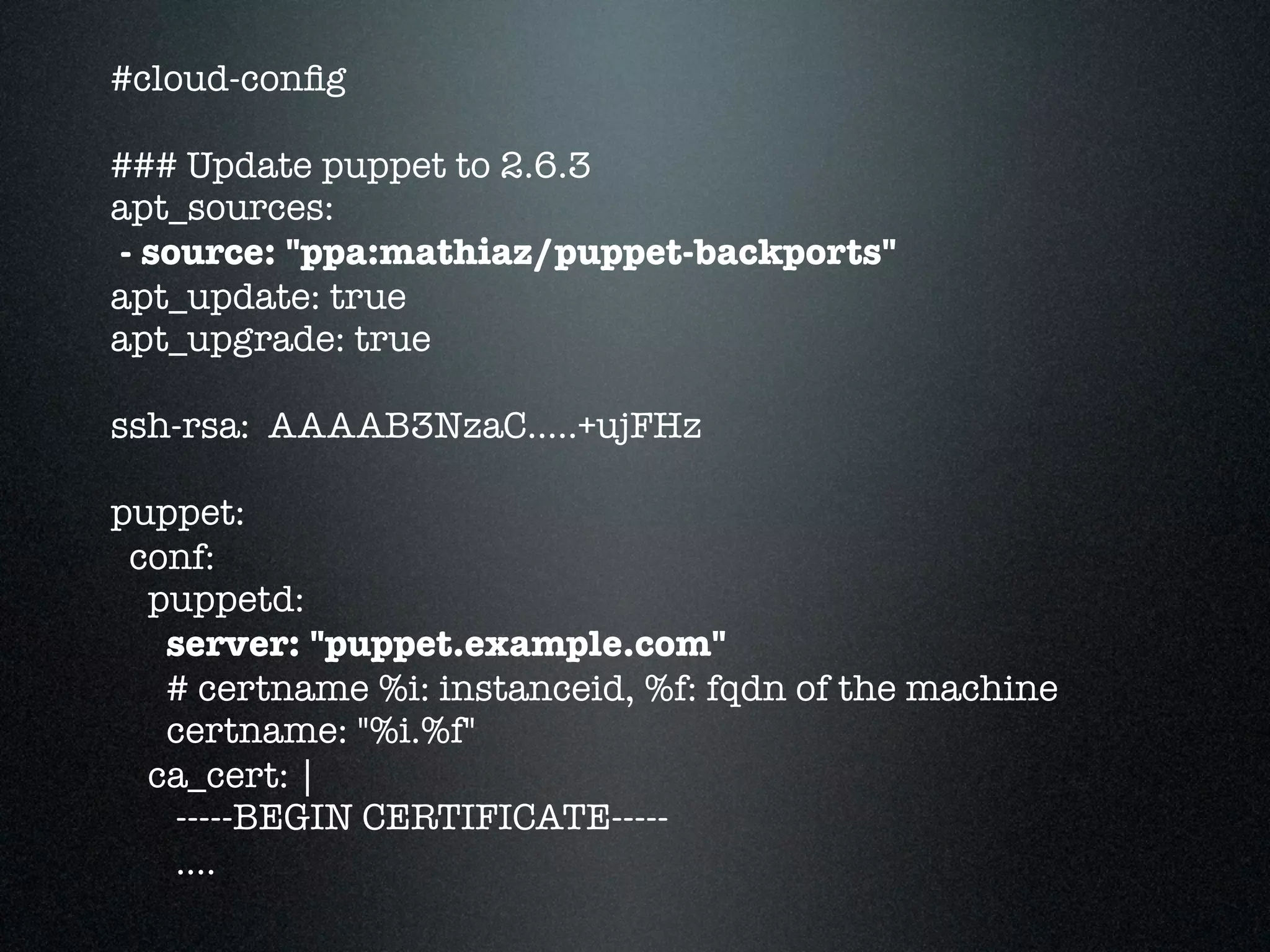
![Master Puppet.conf
[master]
.......
node_terminus = exec
external_nodes = /usr/bin/node_classifier.py --bucket instances
reports = http, store, foreman
### different puppet environments: development, staging, production
[development]
templatedir = $confdir/env/development/templates
modulepath = $confdir/env/development/krux-modules:
$confdir/env/development/forge:
$confdir/env/development/services
[....]](https://image.slidesharecdn.com/aws101-110922174148-phpapp01/75/One-Man-Ops-50-2048.jpg)
![Sample Configuration
{ 'classes': ['s_sandbox::jib'],
'parameters': {
'zone': 'us-east-1c',
'instance_type': 'c1.medium',
'instance_id': 'i-23a3d042',
'security_group': 'krux-ops-dev',
'puppet_environment': 'development',
'puppet_master_port': 8180,
'kredis_save_to_disk': 0
'certname': 'ops-dev003.example.com.
47334fd8-1516-451d-bd5a-8760ab2a36c0',
}}](https://image.slidesharecdn.com/aws101-110922174148-phpapp01/75/One-Man-Ops-51-2048.jpg)












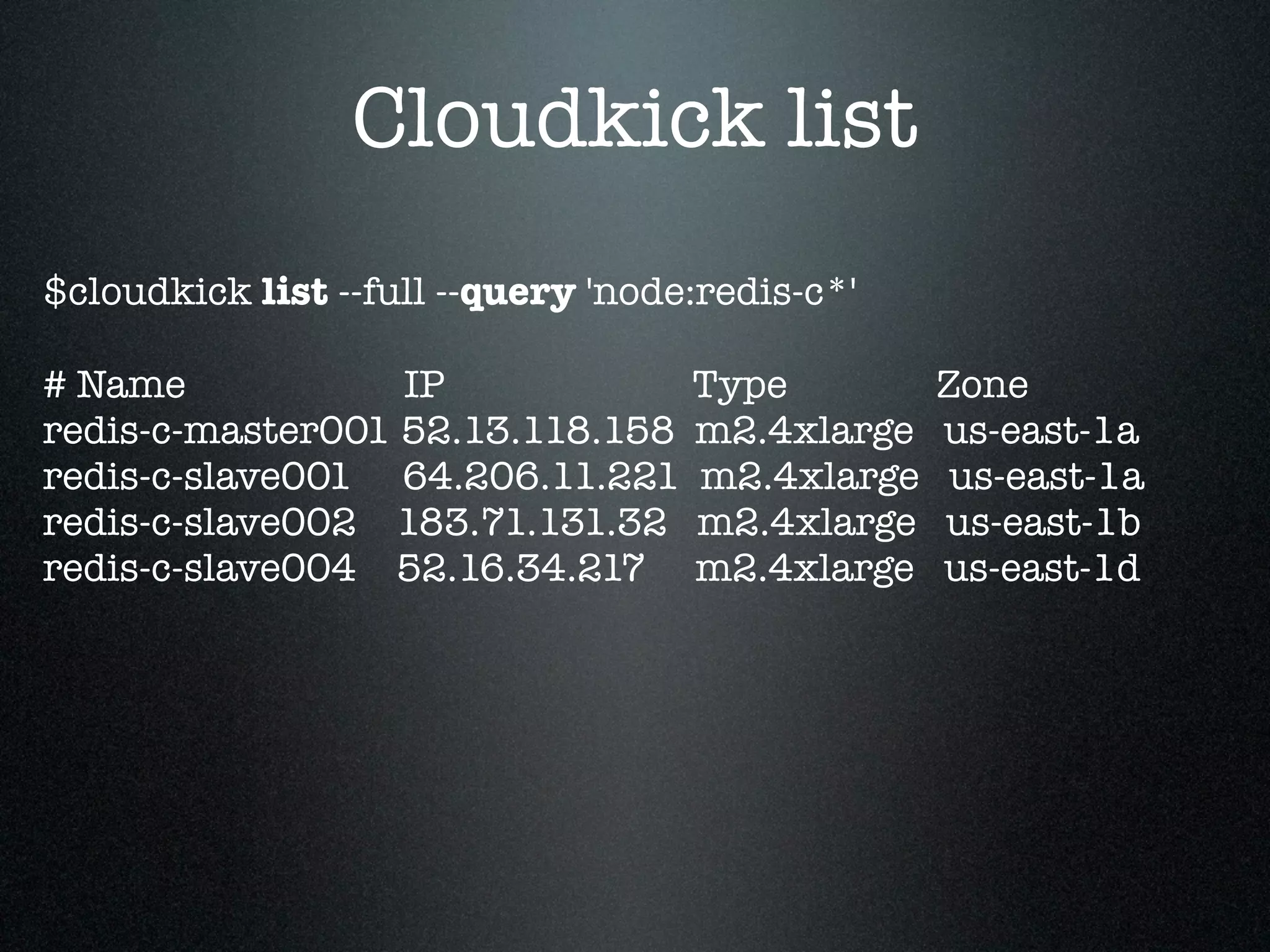
![Cloudkick pssh
$ cloudkick pssh --query 'node:redis-c*' 'hostname'
[1] 18:38:23 [SUCCESS] 64.206.11.221
redis-c-slave001.example.com
[2] 18:38:23 [SUCCESS] 52.13.118.158
redis-c-master001.example.com
[3] 18:38:24 [SUCCESS] 52.16.34.217
redis-c-slave004.example.com
[4] 18:38:24 [SUCCESS] 183.71.131.32
redis-c-slave002.example.com](https://image.slidesharecdn.com/aws101-110922174148-phpapp01/75/One-Man-Ops-71-2048.jpg)