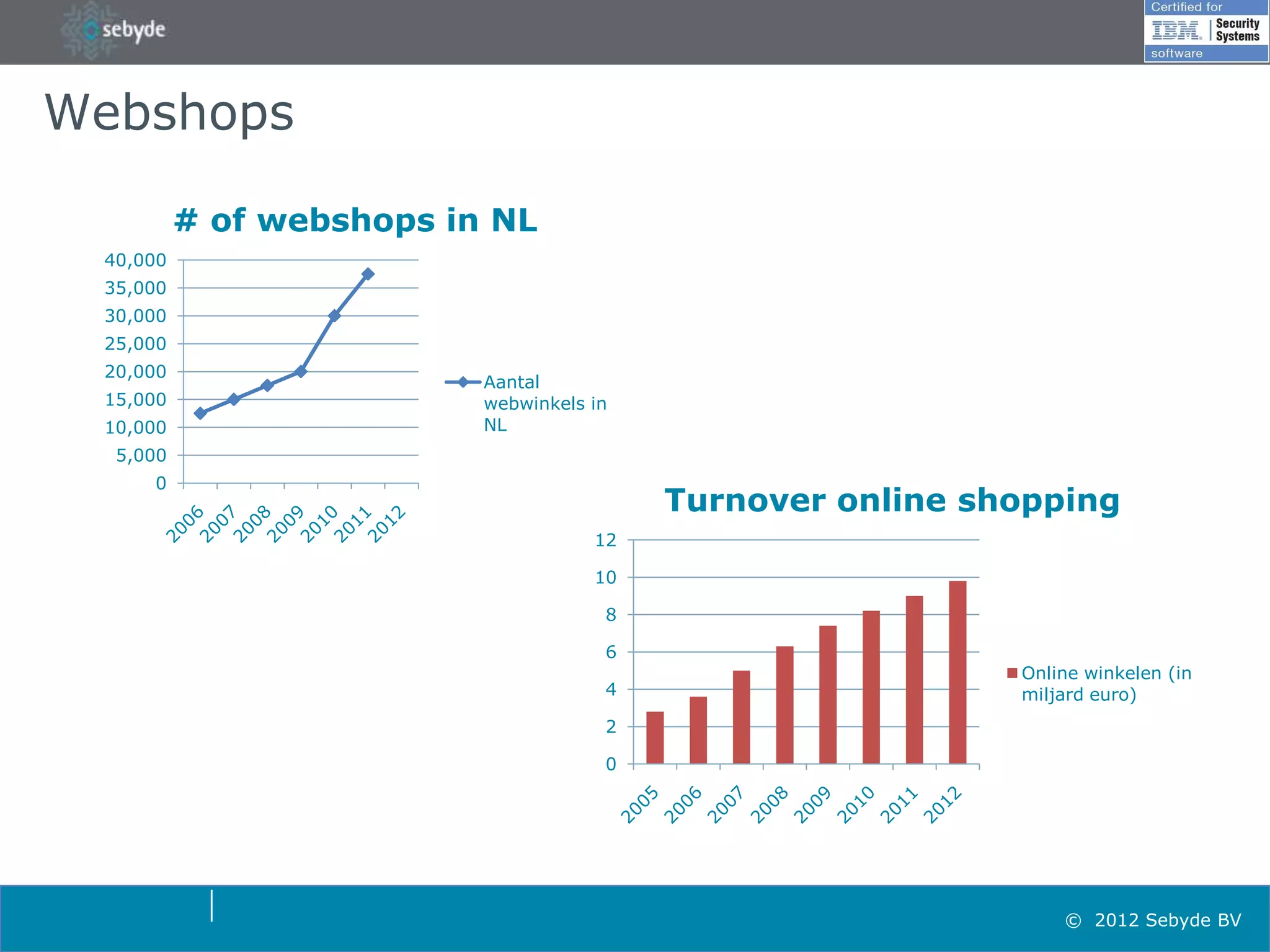
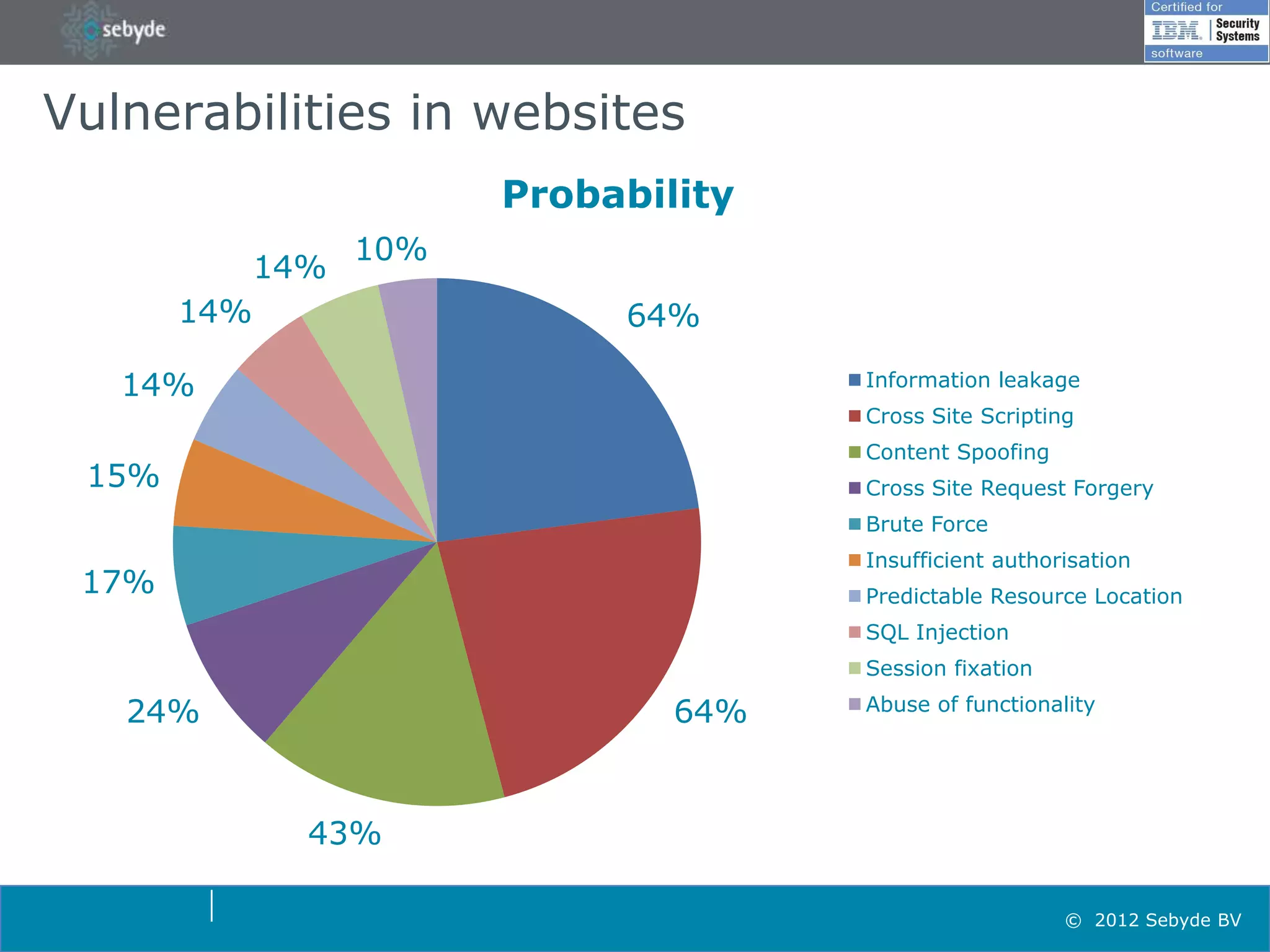
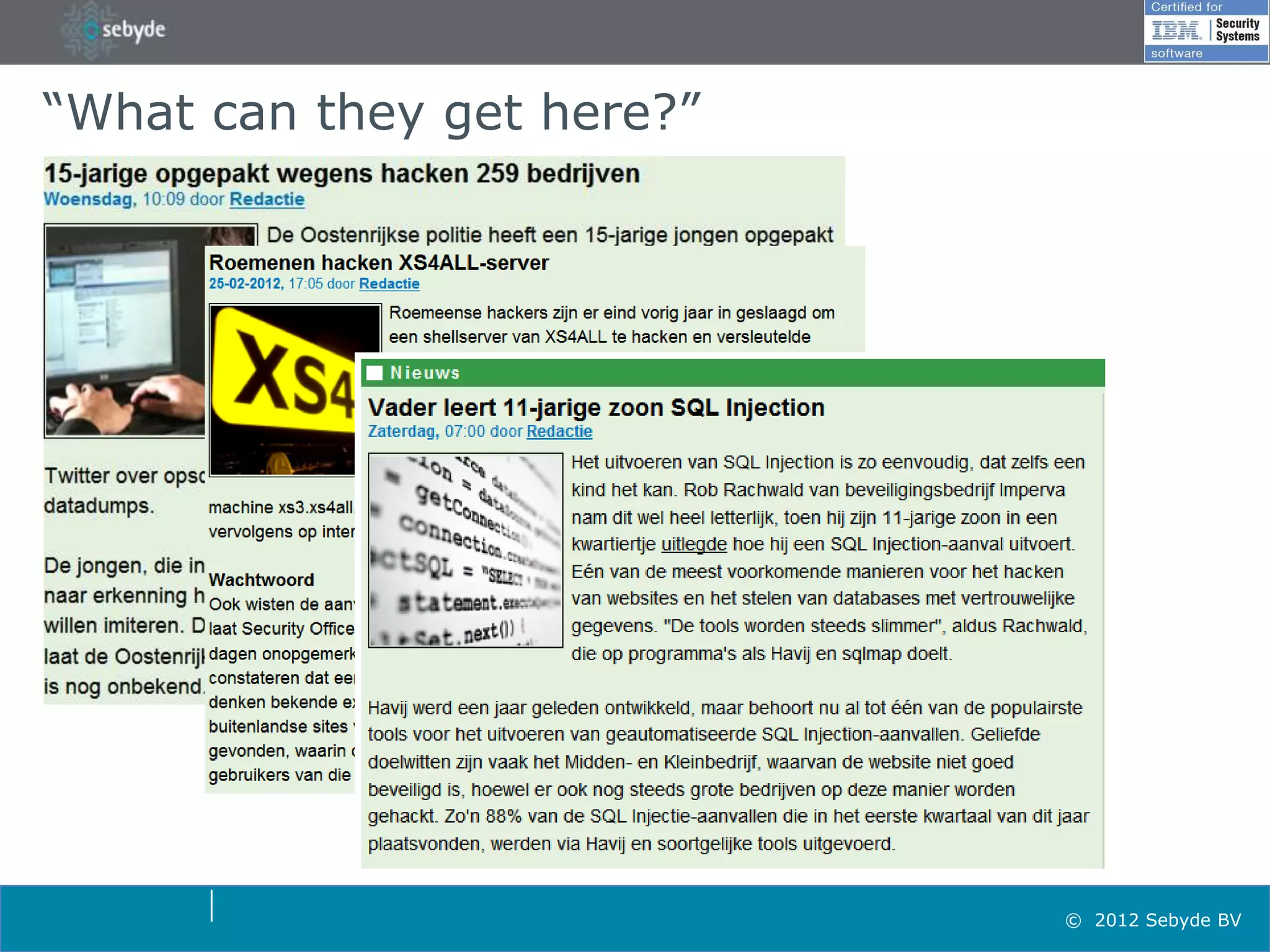
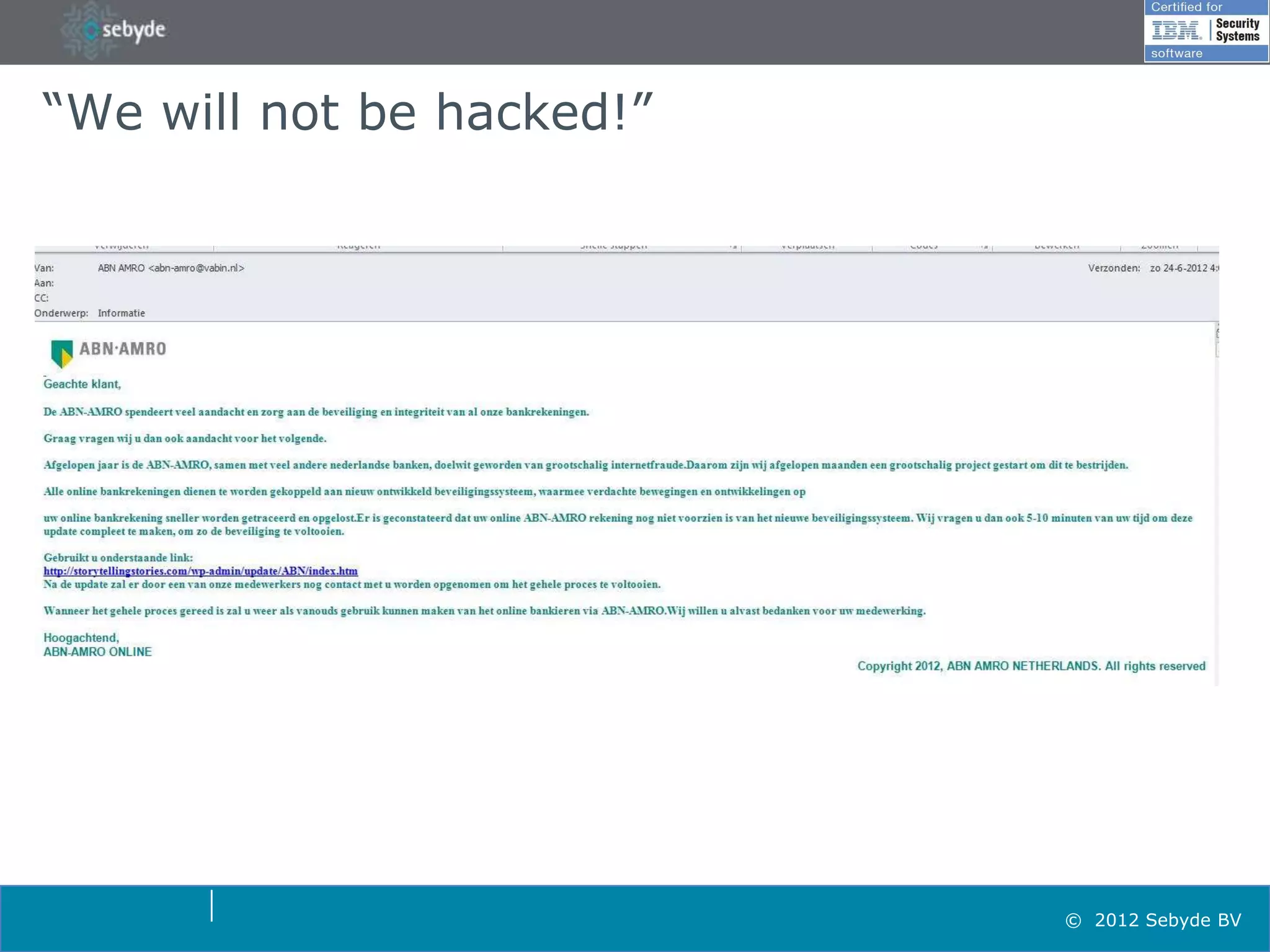
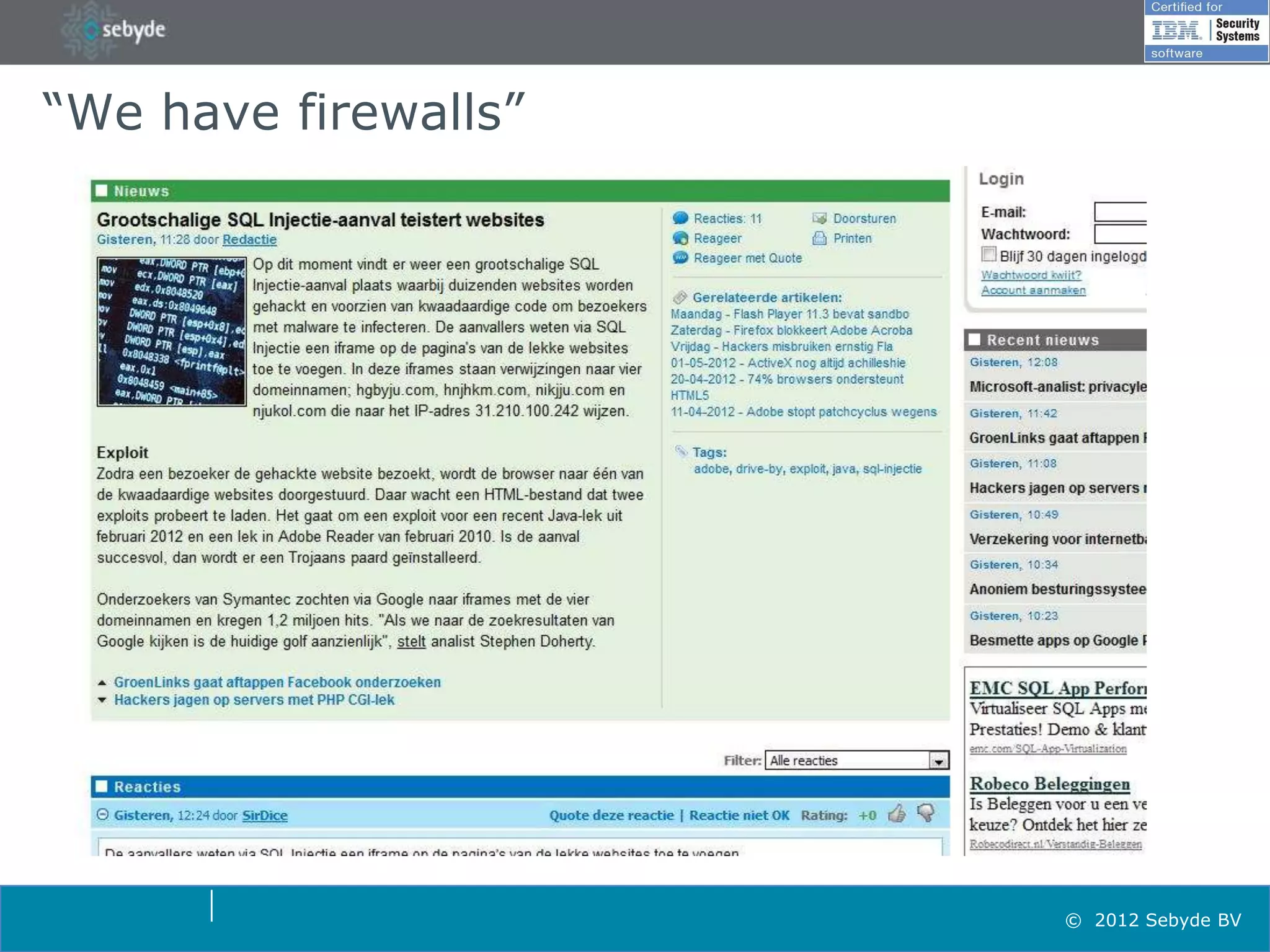
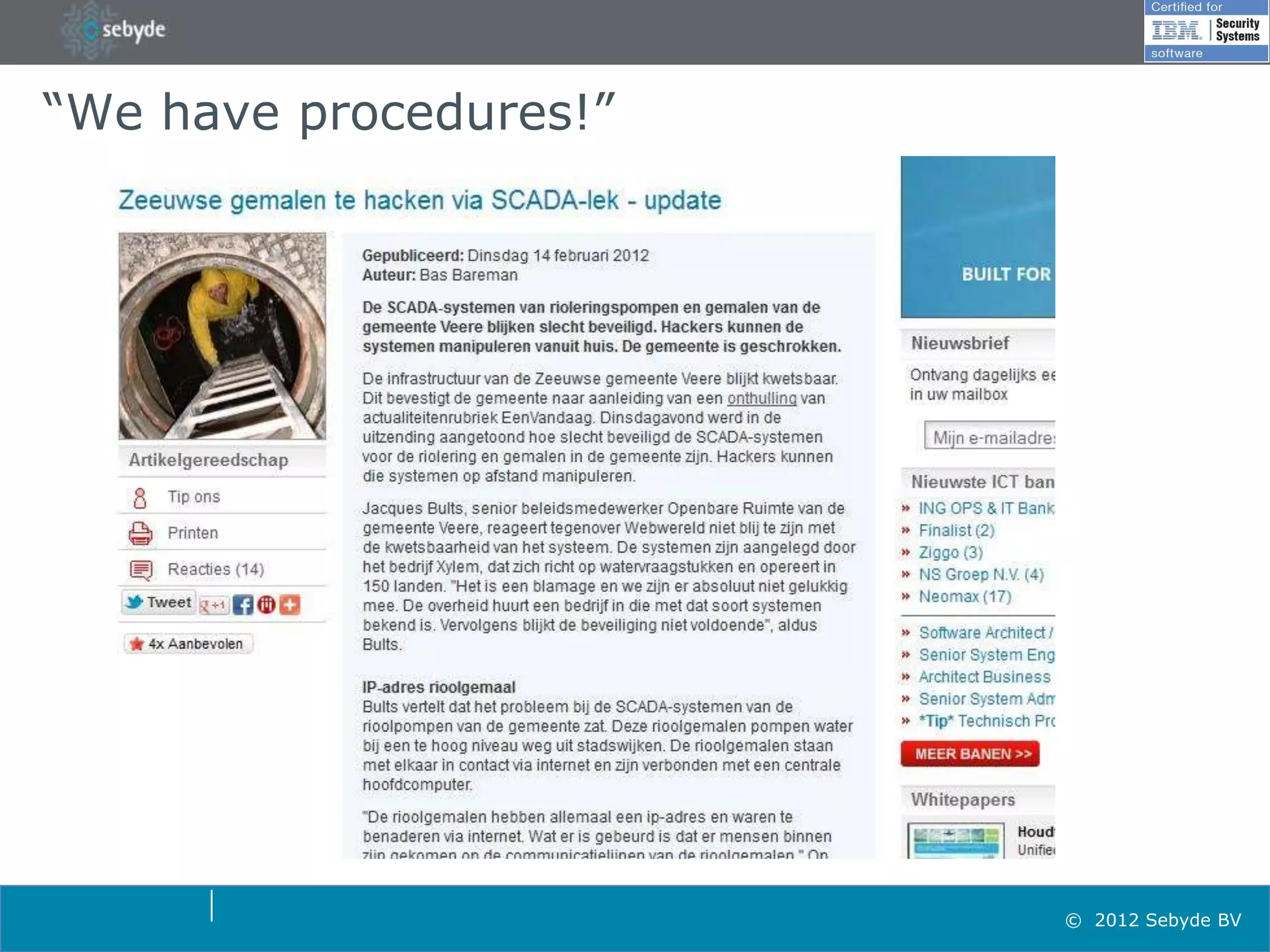
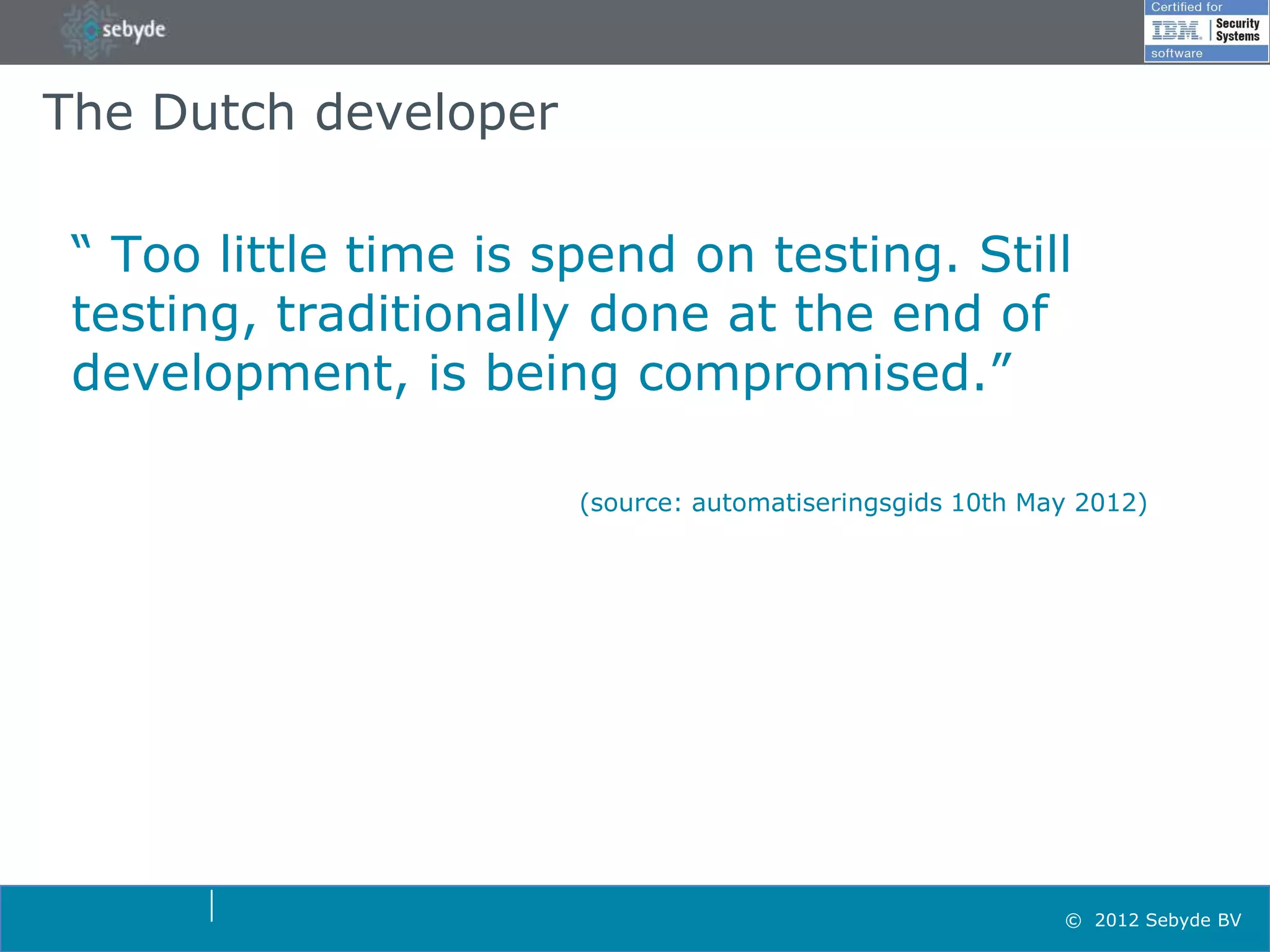
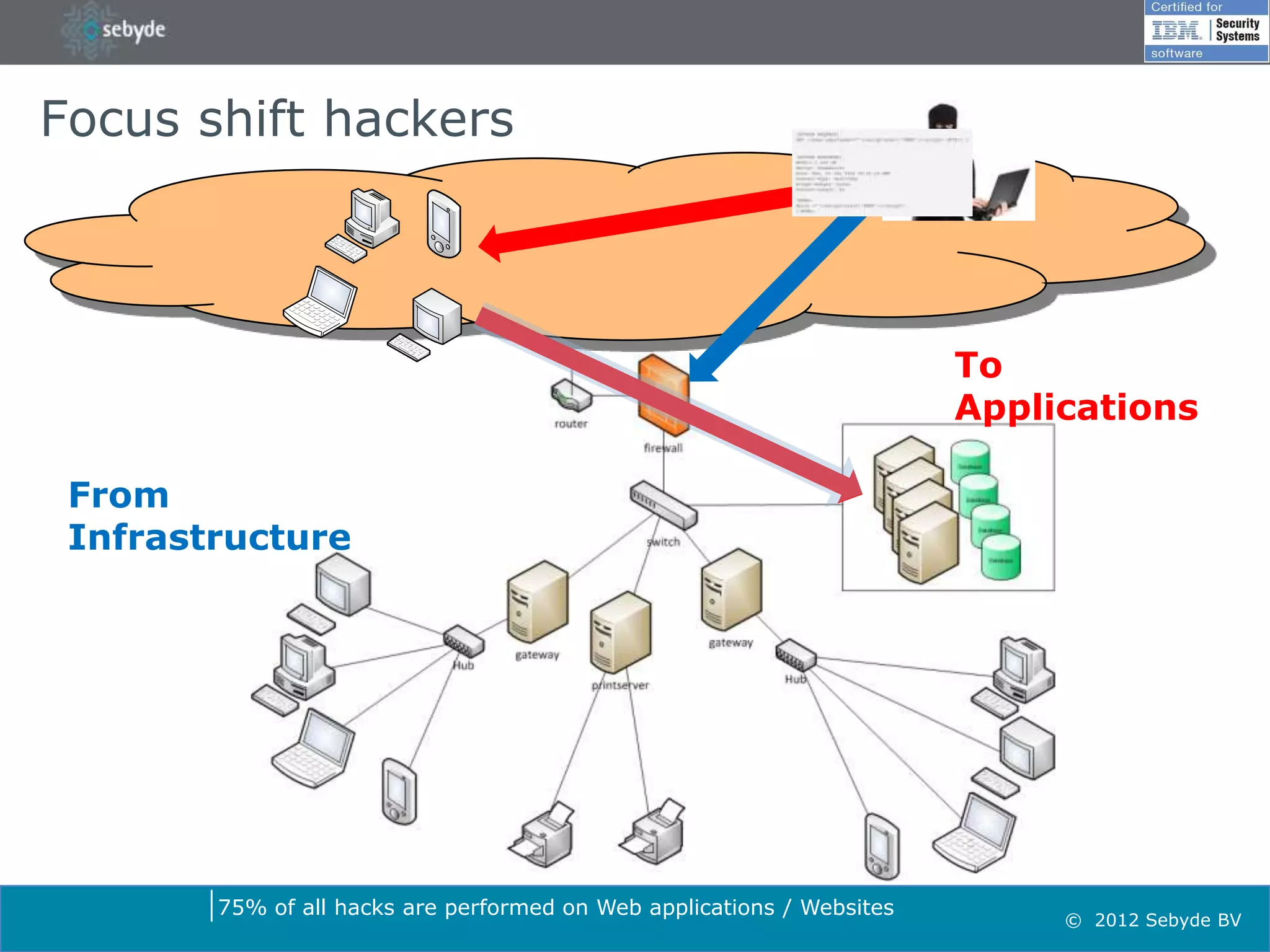
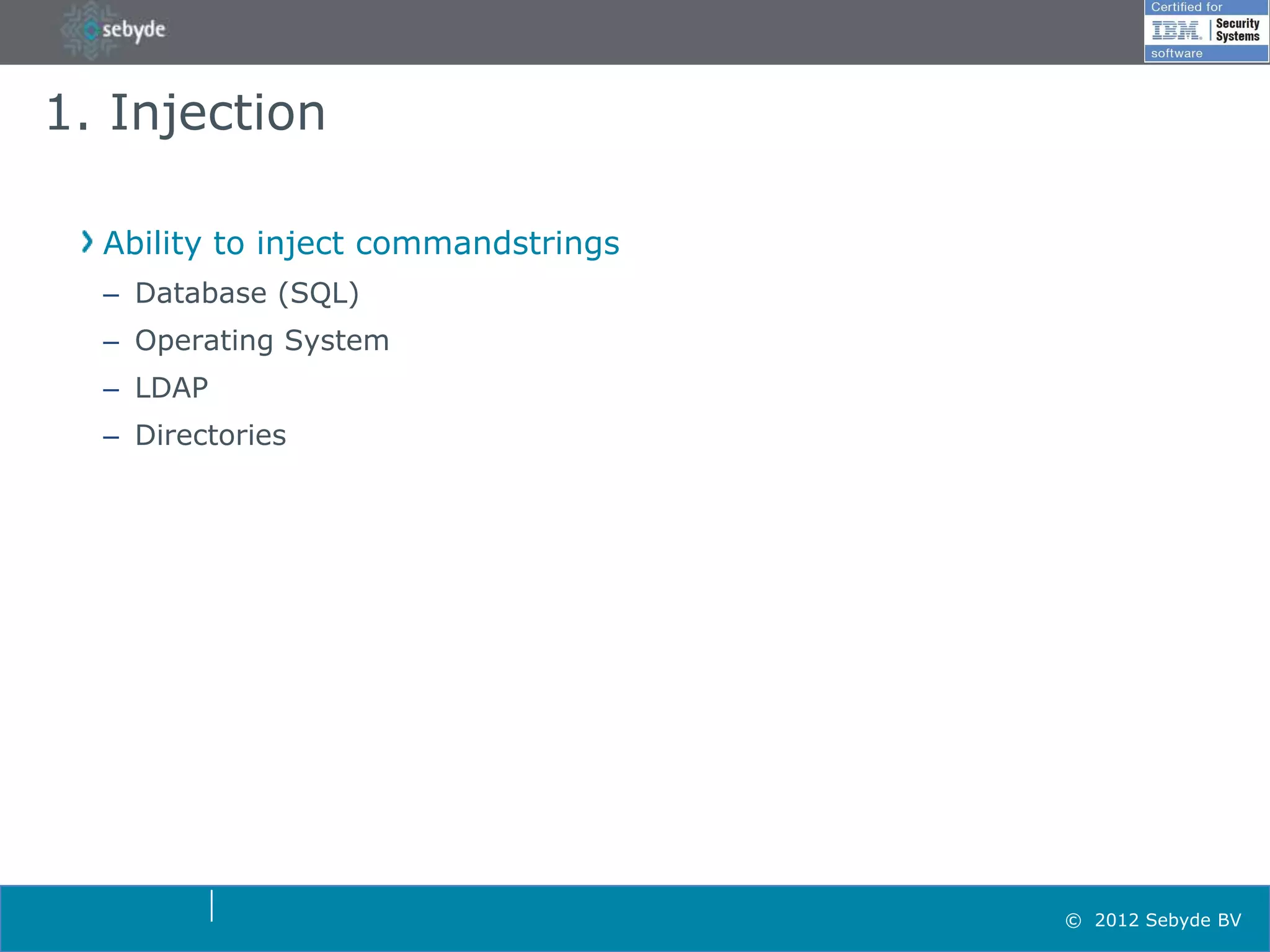
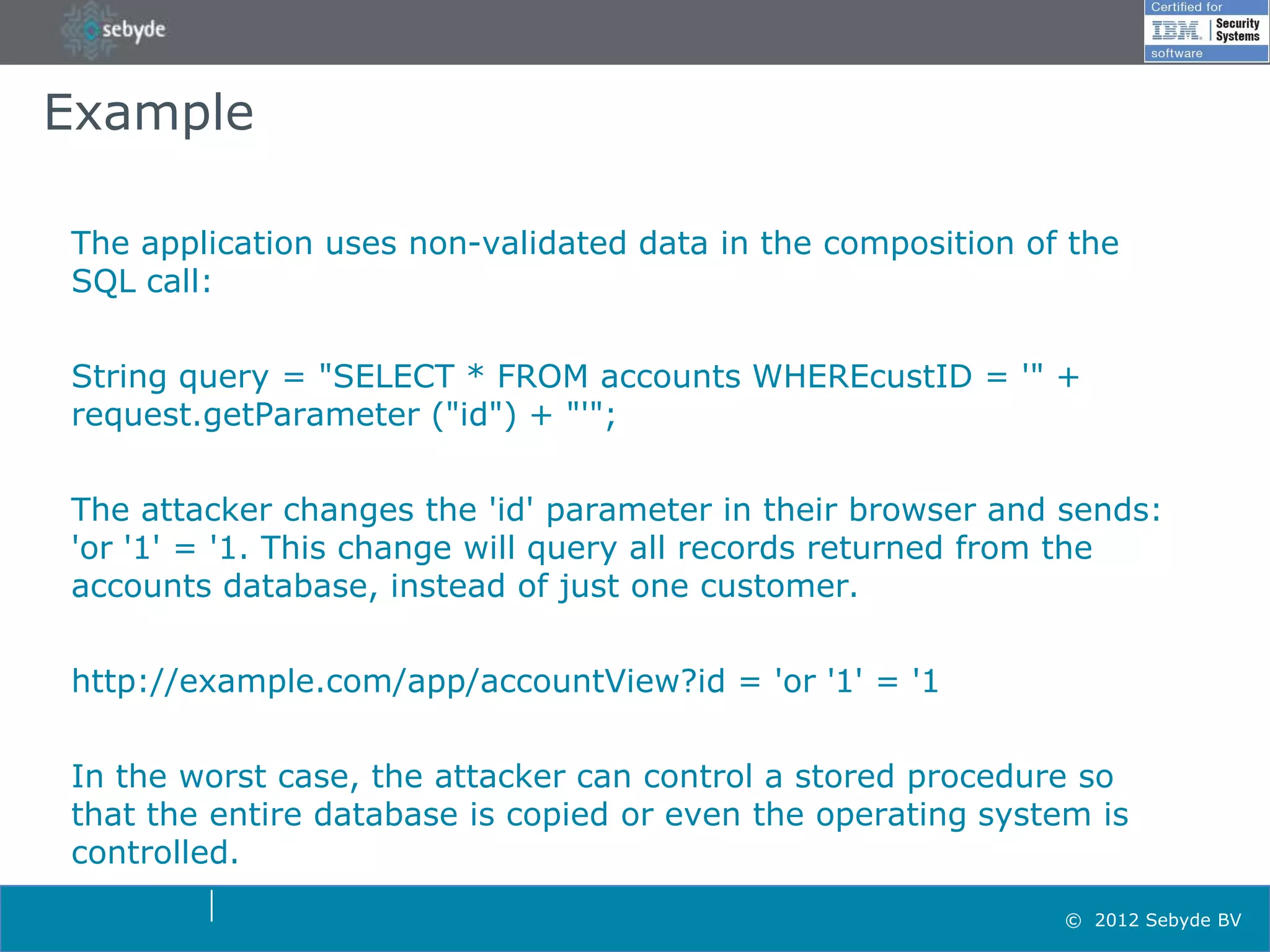
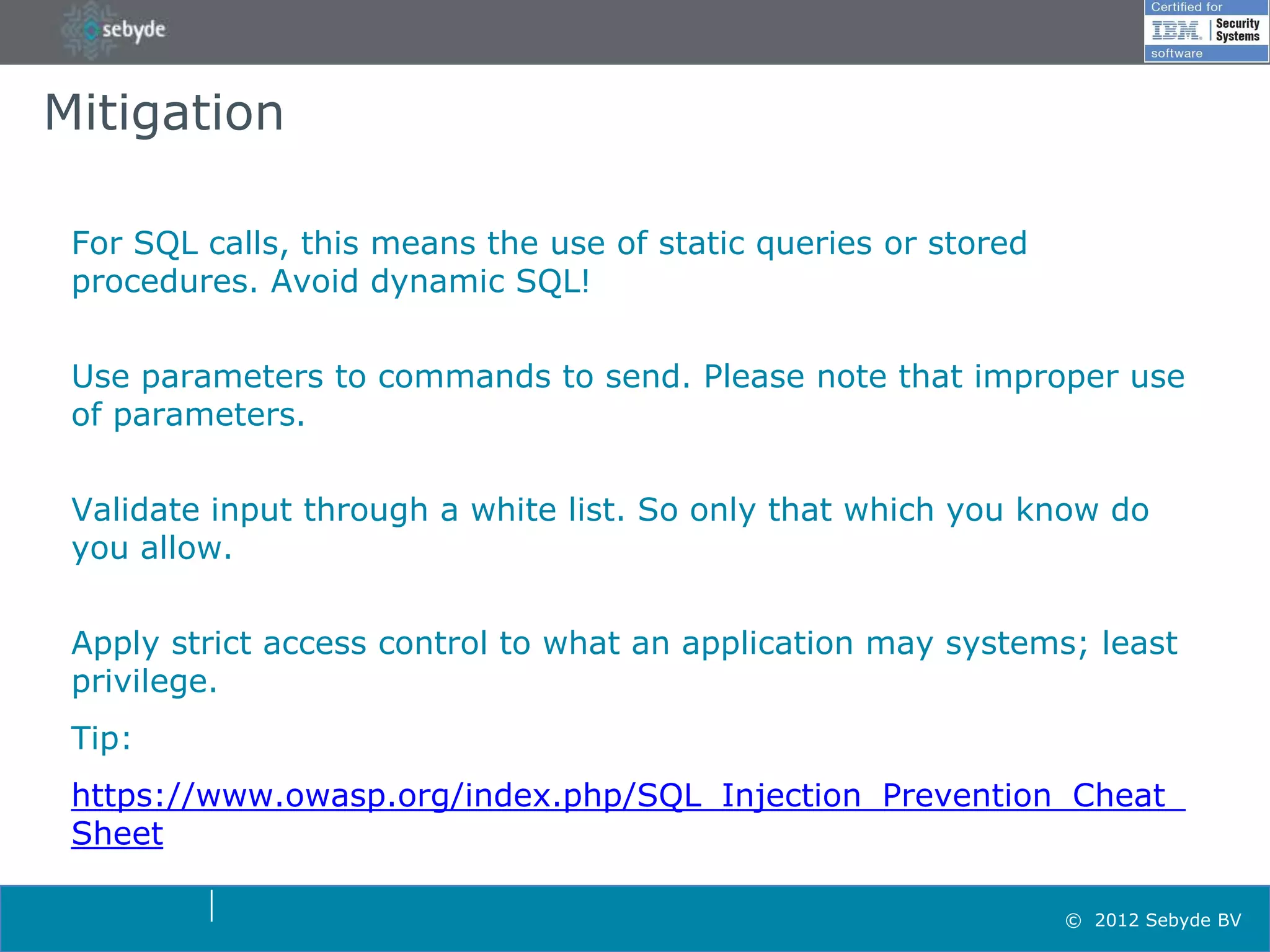
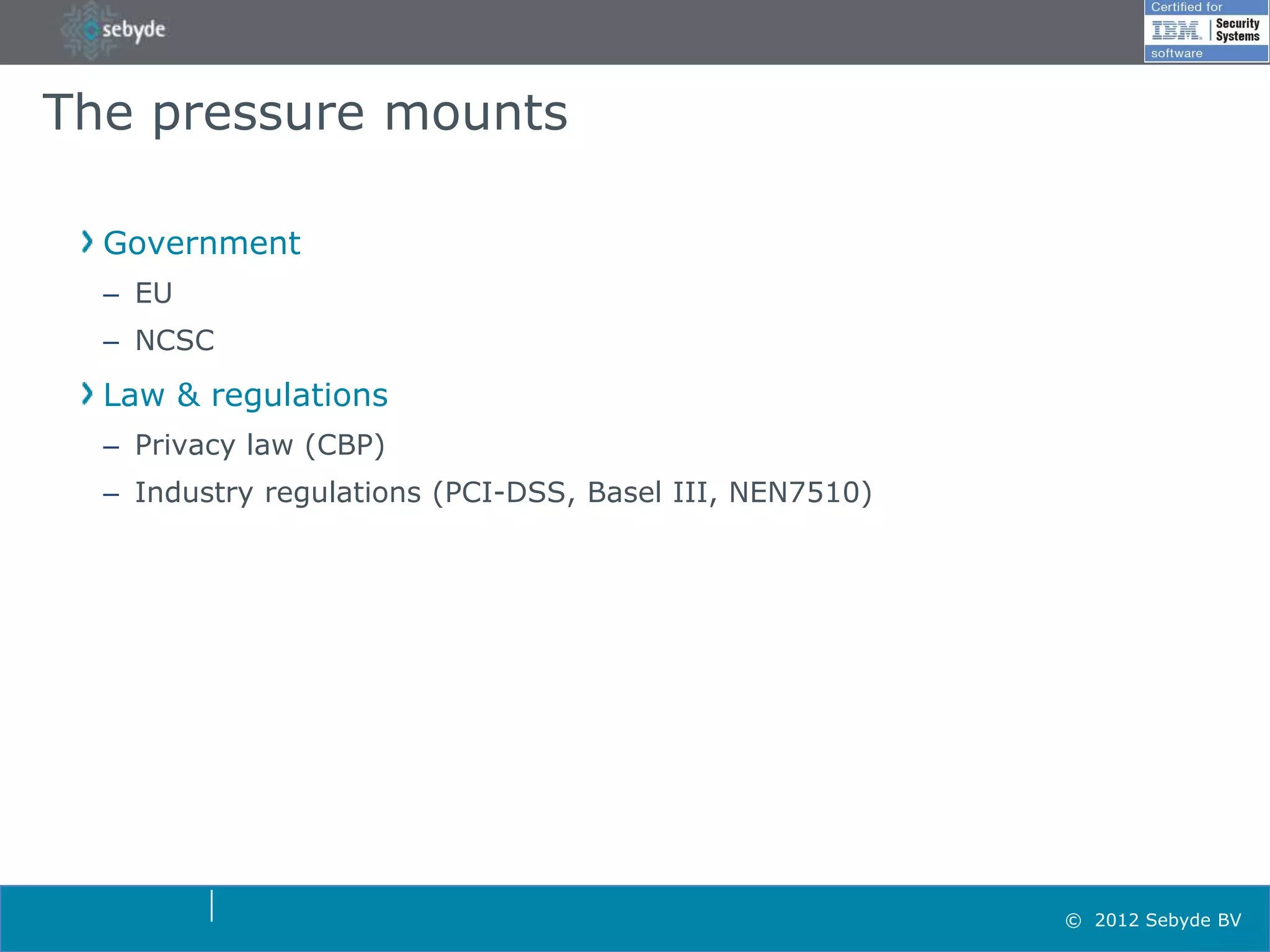
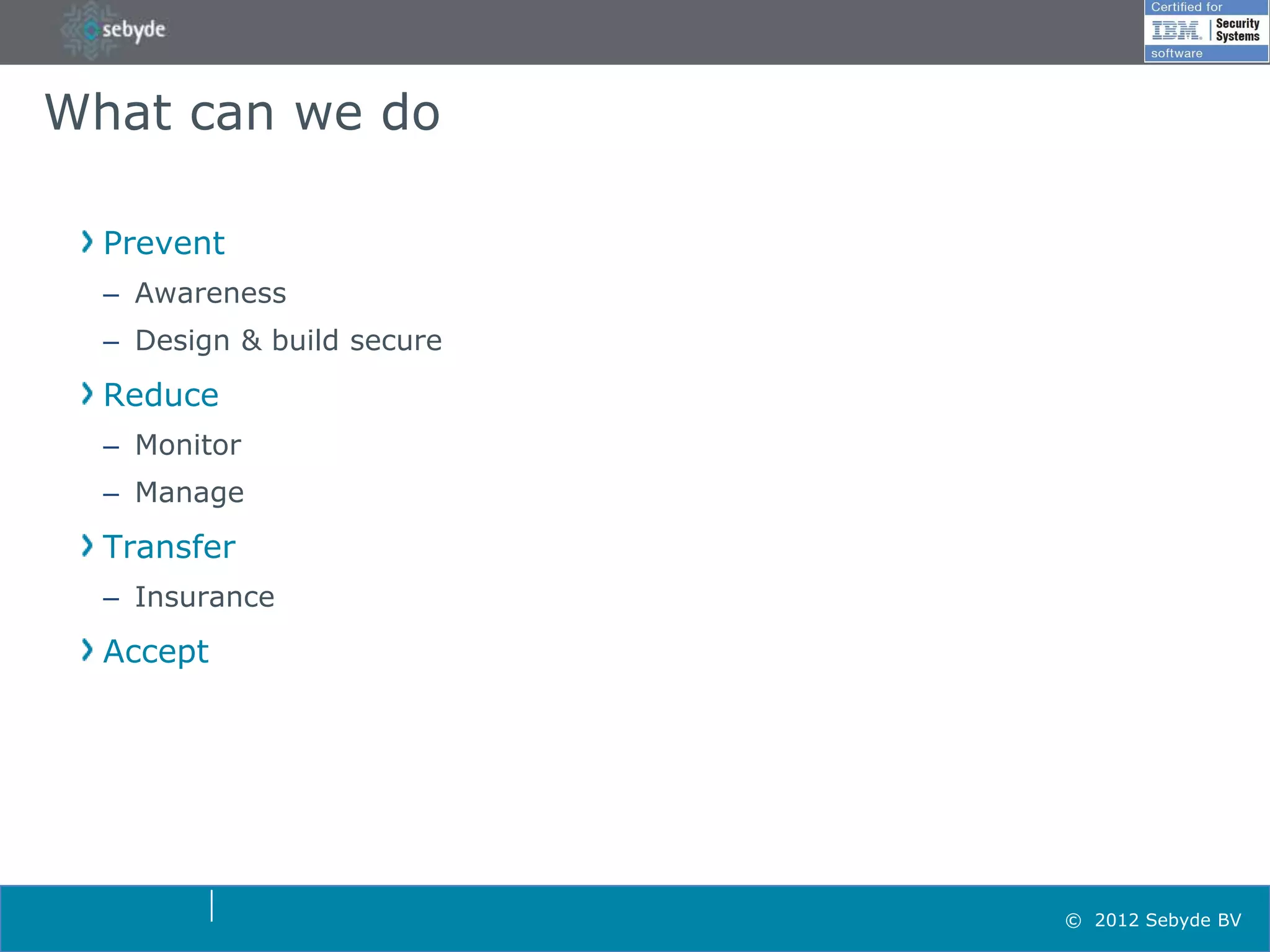
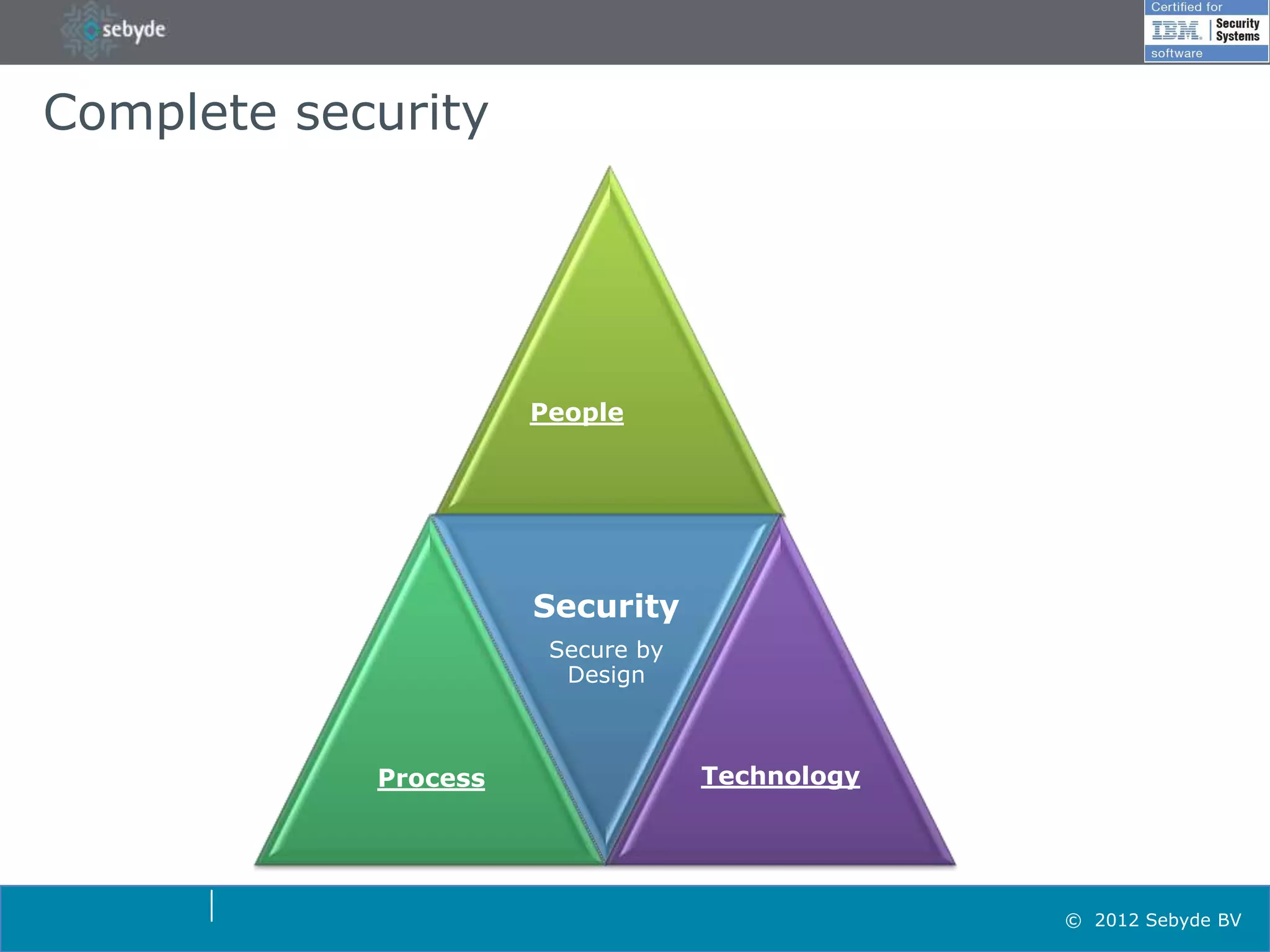
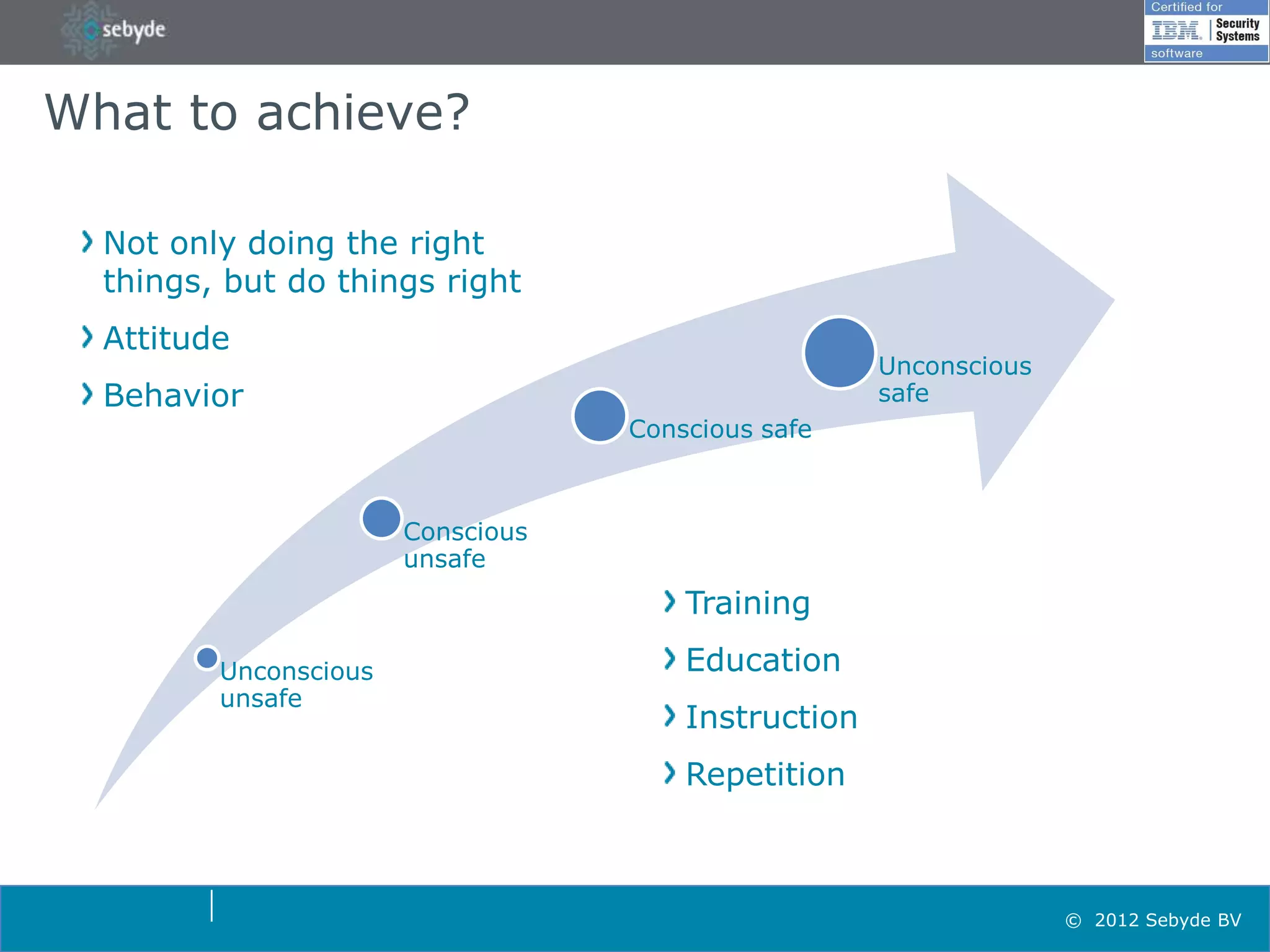
This document discusses application security and summarizes key points about securing web applications. It notes that 75% of attacks target applications rather than infrastructure. Dutch developers often take an agile approach and do not use many formal methods or tools in development. Cybercrime now surpasses illegal drug trafficking and identity theft occurs every 3 seconds. The document recommends focusing on application security and testing to address these growing threats.