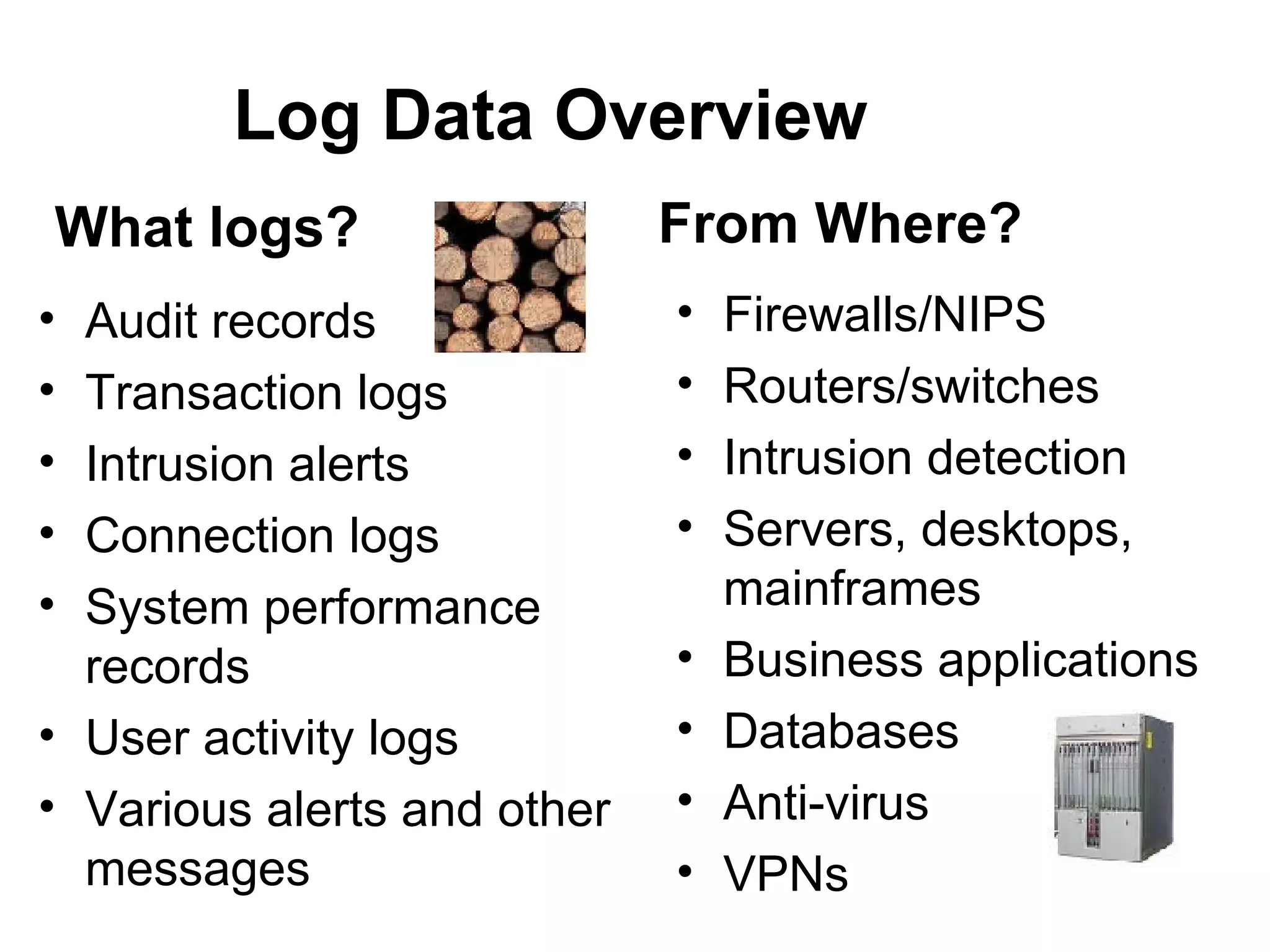
The document discusses six common mistakes in log management: 1) Not logging at all, 2) Not looking at the logs, 3) Storing logs for too short a time, 4) Prioritizing log records before collection, 5) Ignoring logs from applications, and 6) Only looking at what is known to be bad. It provides an overview of why logs are important, what types of events are typically logged, and regulations around logging. Basic approaches to log analysis are also outlined.