ACL Tutorial
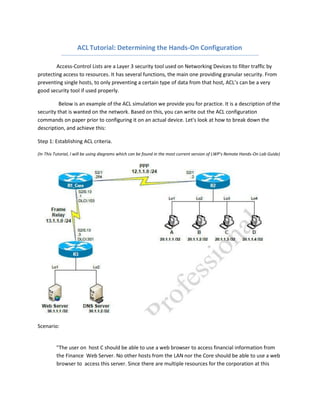
- 1. ACLTutorial: Determining the Hands-On Configuration Access-Control Lists are a Layer 3 security tool used on Networking Devices to filter traffic by protecting access to resources. It has several functions, the main one providing granular security. From preventing single hosts, to only preventing a certain type of data from that host, ACL’s can be a very good security tool if used properly. Below is an example of the ACL simulation we provide you for practice. It is a description of the security that is wanted on the network. Based on this, you can write out the ACL configuration commands on paper prior to configuring it on an actual device. Let's look at how to break down the description, and achieve this: Step 1: Establishing ACL criteria. (In This Tutorial, I will be using diagrams which can be found in the most current version of LWP's Remote Hands-On Lab Guide) Scenario: "The user on host C should be able to use a web browser to access financial information from the Finance Web Server. No other hosts from the LAN nor the Core should be able to use a web browser to access this server. Since there are multiple resources for the corporation at this
- 2. location including other resources on the Finance Web Server, all other traffic should be allowed. " Based on the above description, we know that the criteria for the ACL is the following: 1. Only Three Statements allowed in ACL 2. Only Host C will have WEB access to the Finance Web Server. 3. No other hosts will have WEB access to the Finance Web Server 4. All other Traffic is permitted. 5. Implement the ACL Based on the following example description, and the criteria that is asked, we can configure each line now that we have the criteria drawn out. The easiest way, is to verify each criteria as your configuring the access list. For example: 1. Only Three Statements Allowed in ACL = An Extended ACL is required. Three statements is all we need to implement the ACL. 2. Only Host C will have WEB Access to the Finance Web Server = access-list 101 [100 and above for Extended ACLs] permit [Since we are allowing only 1 address access to the Server] tcp [TCP in this case, since HTTP is a TCP protocol, not UDP] host [specifies single host] [Source-Address of Host C] host [Destination- Address of Finance Web Server] eq [equal to: for specifying which type of traffic] 80 (or HTTP, 80 is the port # for HTTP) 3. No other hosts will have WEB access to the Finance Web Server: access-list 101 deny [Deny this time, since we are denying all other hosts] tcp any [any is selected so that no hosts can bypass this statement] host [Destination-Address of Finance Web Server] eq 80 [HTTP is specified again, as it asks for only WEB access to be denied] 4. All other traffic is permitted: access-list 101 permit ip any any [This statement is possibly the most important, as all ACLs, when created, generate a explicit command "access-list [ACL #] deny ip any any" that must be negated by using the command "access-list 101 permit ip any any," unless the description for the ACL specifically requests all traffic blocked.] 5. Apply it to the interface: ip access-group 101 out
- 3. Beyond Steps 1- 4, the only other thing that is needed is for it to be applied to the interface, or step 5. Since ACL’s are used to protect information, the general best practice is to apply it as close to the information you are trying to protect as possible. In the case of the example diagram, we want it to affect only the data going towards the finance and web server. Depending on what the business is trying to achieve, determines how much data will be checked for the above ACL shown in the example. Usually, there will be specific instructions on where to configure the device. An example of such instruction would be: “Configure a security measure (ACL, in this case) on the default gateway router…” The default gateway router, in the case of the diagram, being R1_Core, as R1 connects the two different networks for connectivity (since the diagram doesn’t clearly define it as the gateway). The instruction might not always be that black and white in the job environment. However in the job environment, you would have specific instructions on where to configure it, unless you are a Network Administrator (in which case, you would specify it yourself). Going back to step 5 in the sample scenario above, R3 would be the Networking Device to apply it to. Since R3 is a Router, an ACL can be applied to the interfaces directly connected to the Server. In a on the job scenario, the servers would most likely be connected to a Switch. Therefore, the closest Layer 3 Device to the Server would have the ACL applied to it. In the example in the previous page, either R3's inbound interface towards the servers or the outbound interface towards R1 will work for ACL implementation. Since we have no physical interface going towards the servers (The DNS and Web Server are simulated using Loopback interfaces.), we will have to apply it to the interface connected towards R1. The ACL will be applied to check inbound traffic, as per the criteria of the question. (Remember: The goal is to prevent access from hosts to server, not server to hosts.) R3(config-if)# ip access-group 101 in (in for inbound, or out for outbound. Specifying the packets of data to check for the ACL rules) Now, see if you can configure one, using the format from the actual CCNA E-ACL SIM: “A network associate is adding security to the configuration of the Corp1 router. The user on host C should be able to use a web browser to access financial information from the Finance Web Server. No other hosts from the LAN nor the Core should be able to use a web browser to access this server. Since there are multiple resources for the corporation at this location including other resources on the Finance Web Server, all other traffic should be allowed.” The task is to create and apply a numbered access-list with no more than three statements that will allow ONLY host C web access to the Finance Web Server. No other hosts will have web access to the Finance Web Server. All other traffic is permitted.
- 4. The Core connection uses an IP address of 198.18.196.65 The computers in the Hosts LAN have been assigned addresses of 192.168.45.1 – 192.168.45.254 Host A 192.168.45.1 Host B 192.168.45.2 Host C 192.168.45.3 Host D 192.168.45.4 The servers in the Server LAN have been assigned addresses of 172.30.245.17 – 172.30.245.30 The Finance Web Server is assigned an IP address of 172.30.45.23. The Public Web Server is assigned an IP address of 172.30.45.17 Using what you have learned, you know the following requirements need to be met: 1. A numbered ACL with no more than 3 statements 2. ONLY allow Host C access to the Finance Web Server 3. No Other Hosts will have access to the Finance Web Server 4. All other traffic is permitted Also, remember the general best practice: as close to the information as possible. Based on this rule, the access-list will be configured on the outbound interface towards the Finance Web Server. Knowing the above, the configuration will be: 1. Access-list 100 permit tcp host 192.168.45.3 host 172.30.245.23 eq 80 2. Access-list 100 deny tcp any host 172.30.45.23 eq 80 3. Access-list 100 permit ip any any 4. ip access-group 100 out (interface on Corp1 going towards SW-1. SW-1 is a switch) REMEMBER ! Apply it to the interface. If it is not done, the ACL will not be counted as “implemented” on any network. The Access-List will exist, but not affect any data.