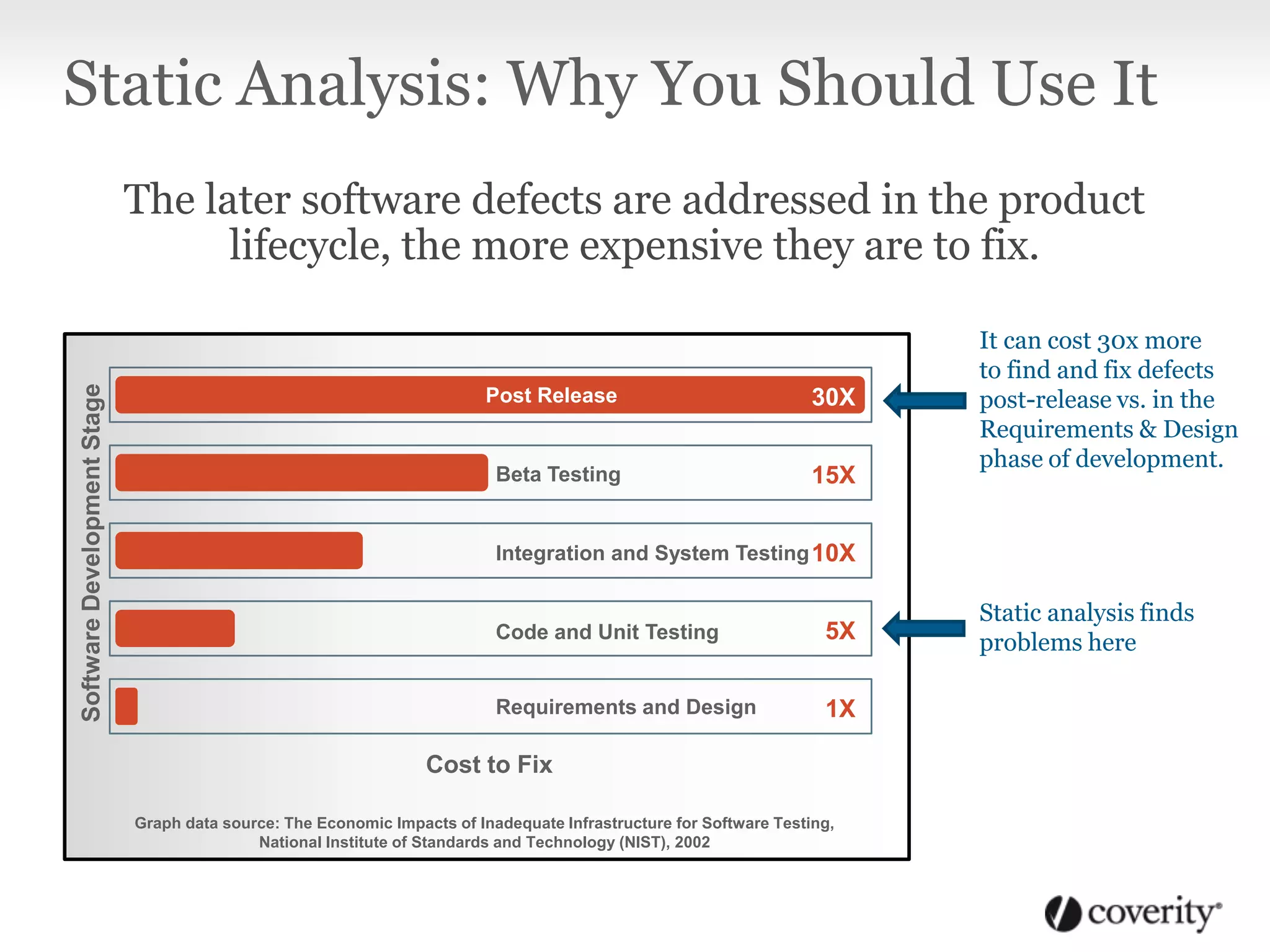
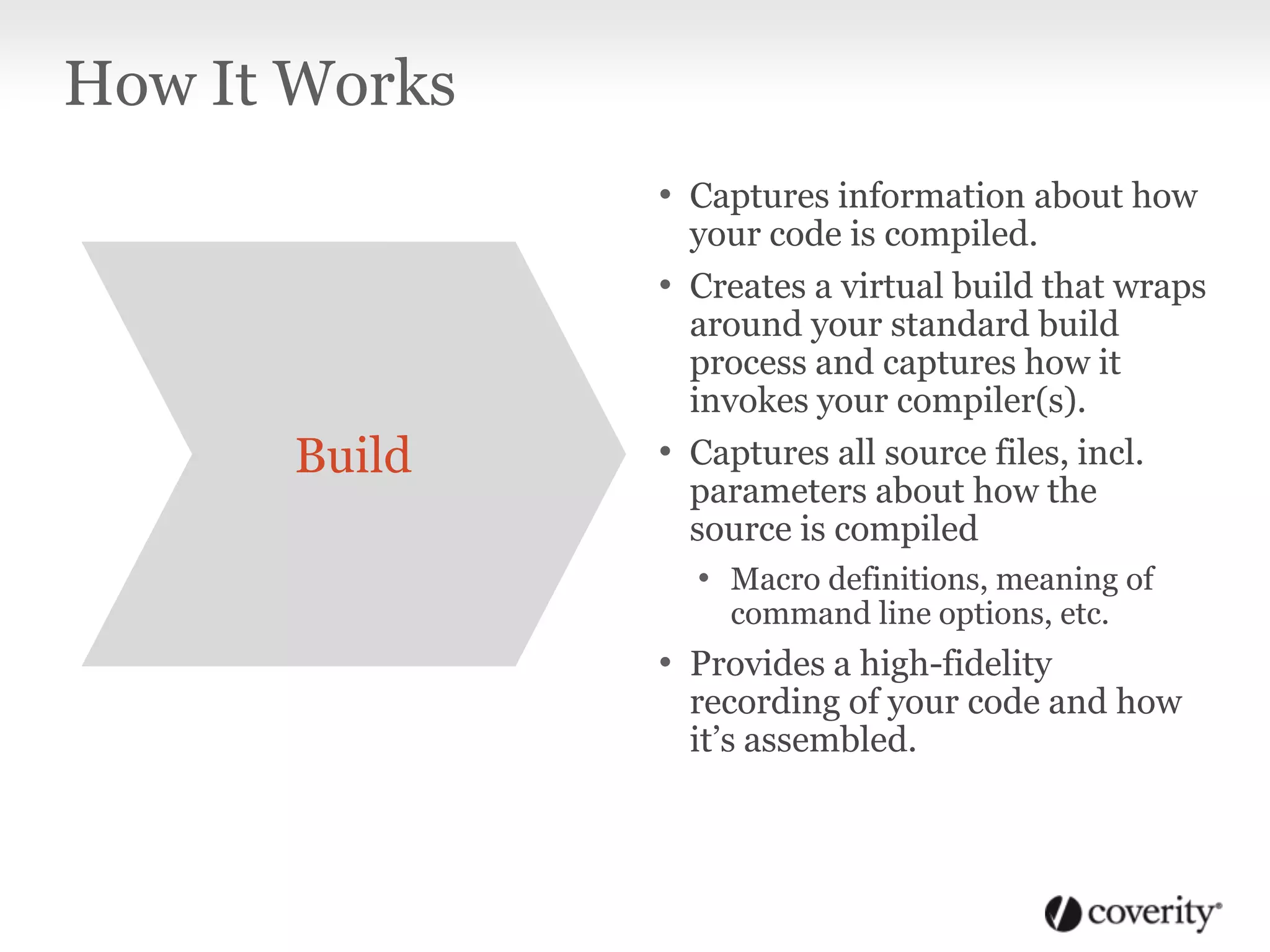
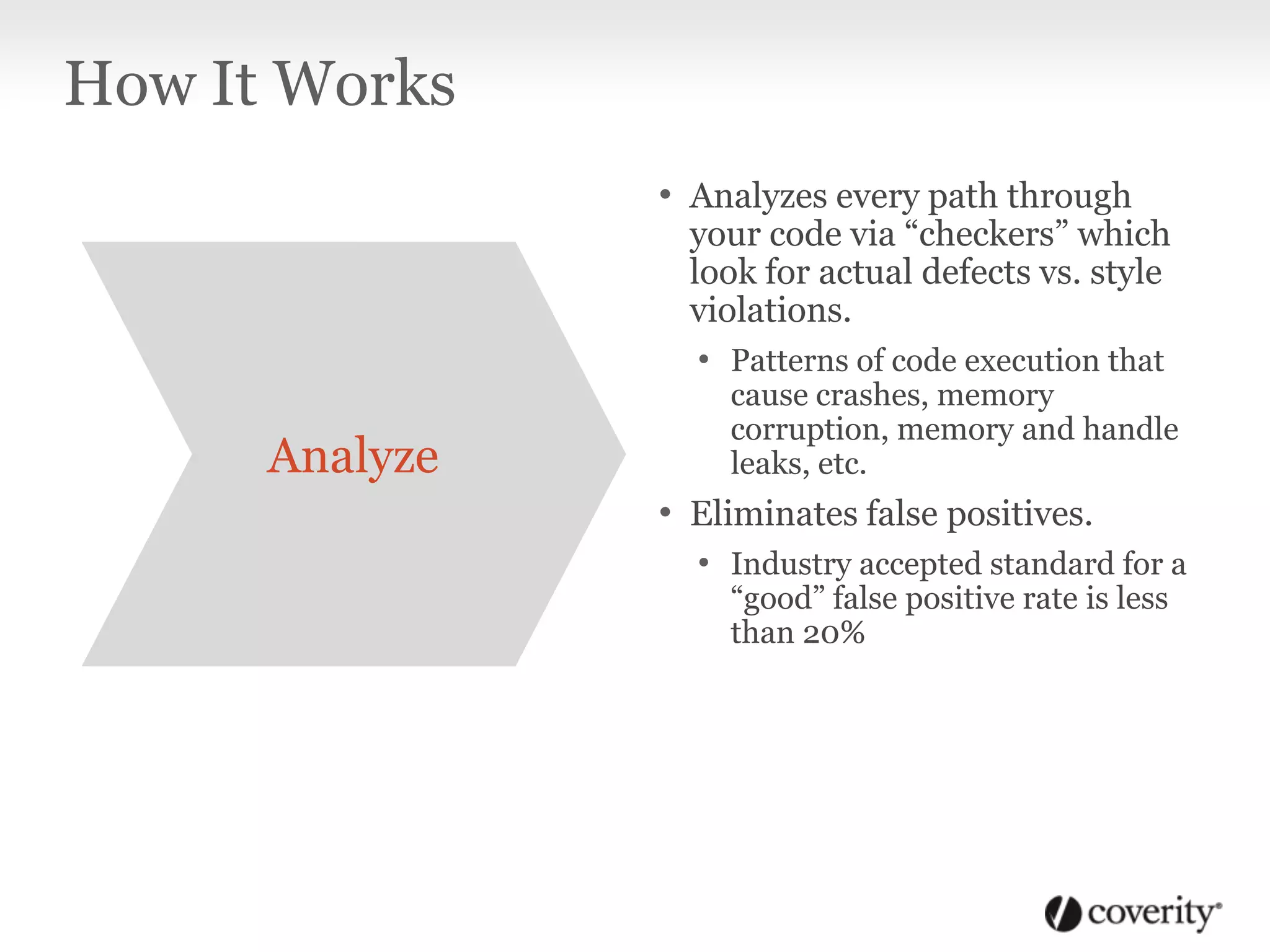
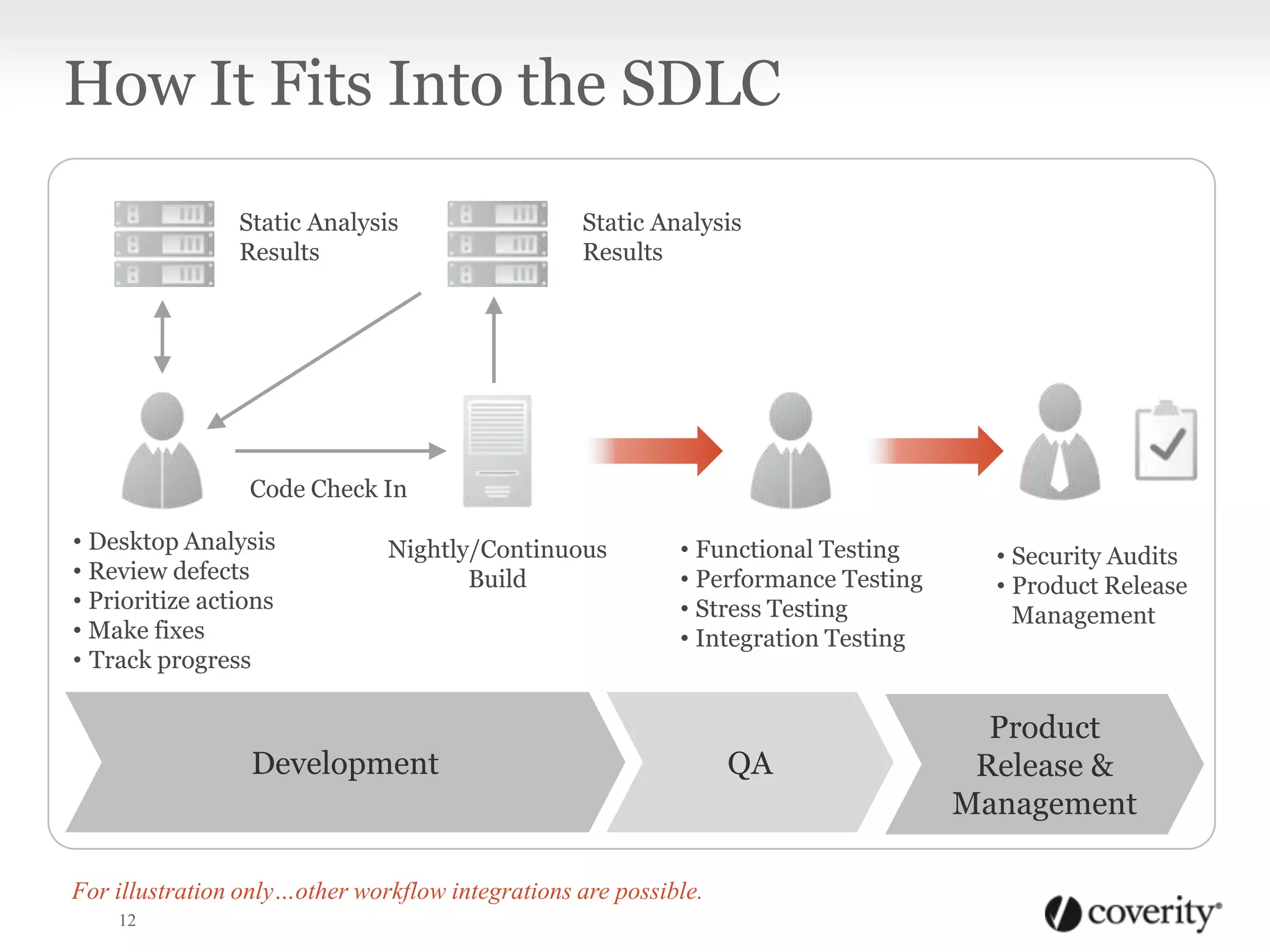
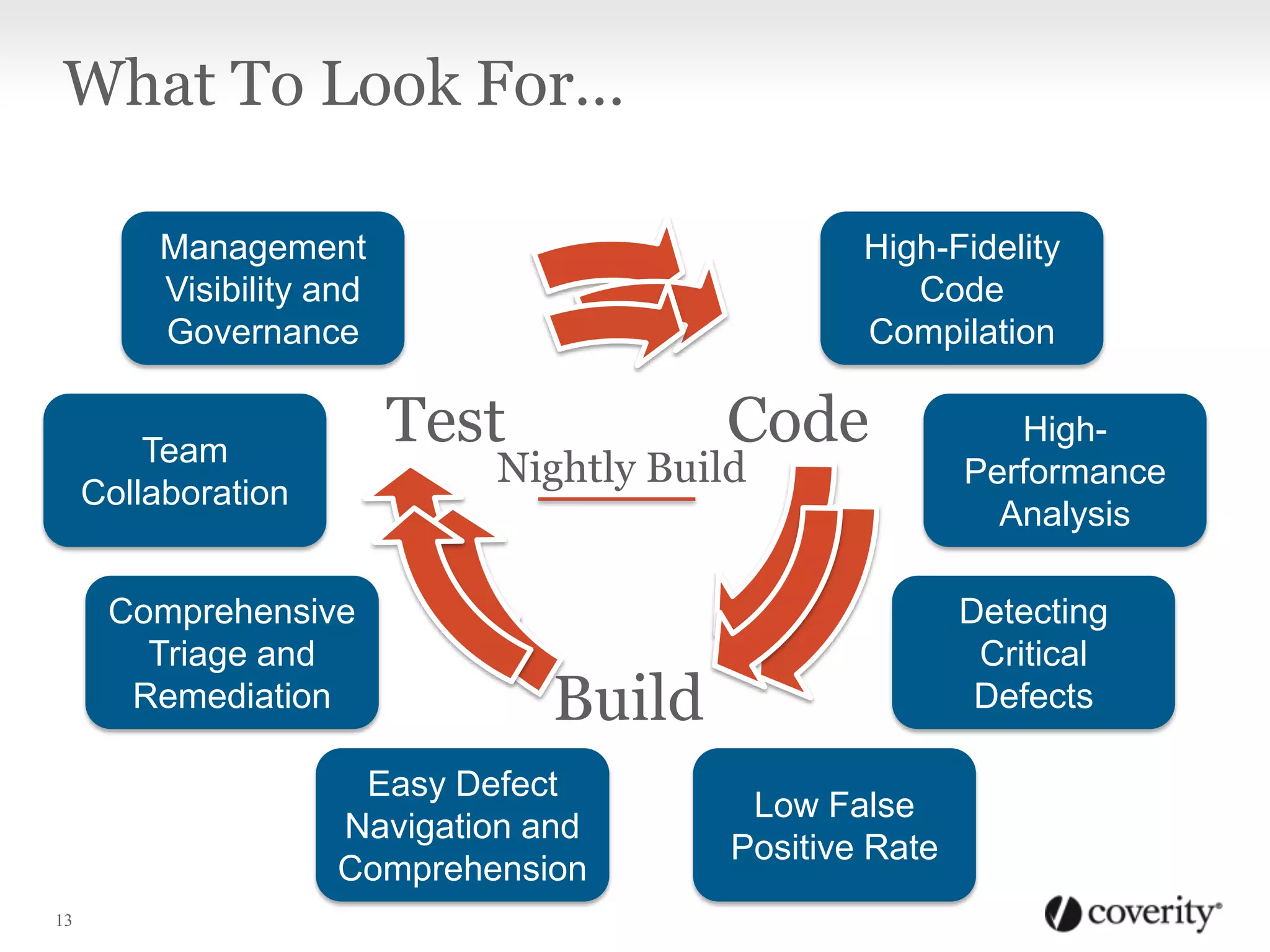
Static analysis is a technique that analyzes source code without executing it to find useful information. It works by using tools to capture how code is compiled and then analyzes every path through the code using checkers to find defects like crashes, memory issues and security vulnerabilities. It is beneficial because it can find problems early in the development process when they are cheaper to fix, and the analysis can be done continuously even when developers are not working. Static analysis fits into the software development lifecycle by integrating with activities like code checking, nightly builds, testing and security audits to surface defects.