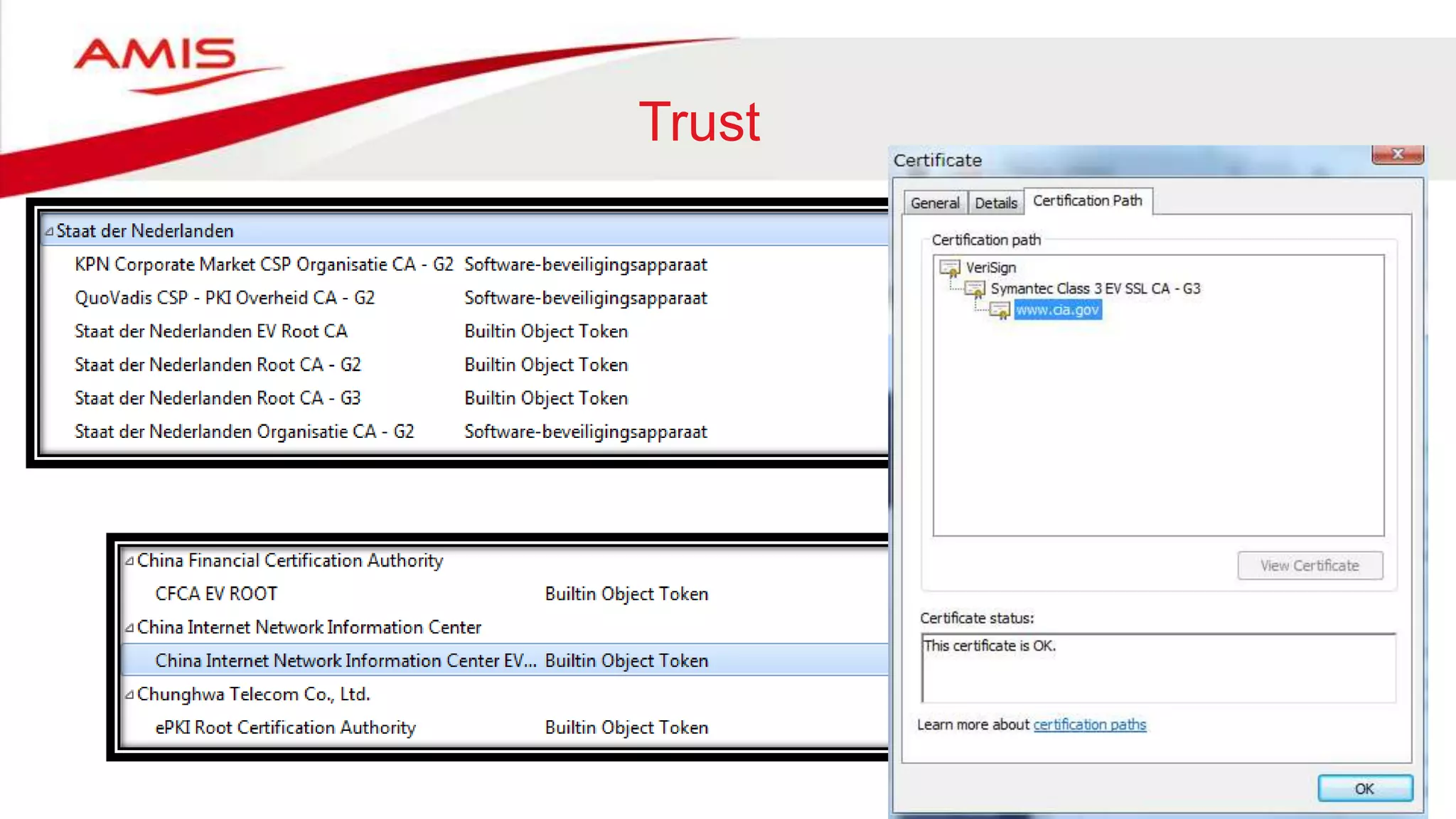
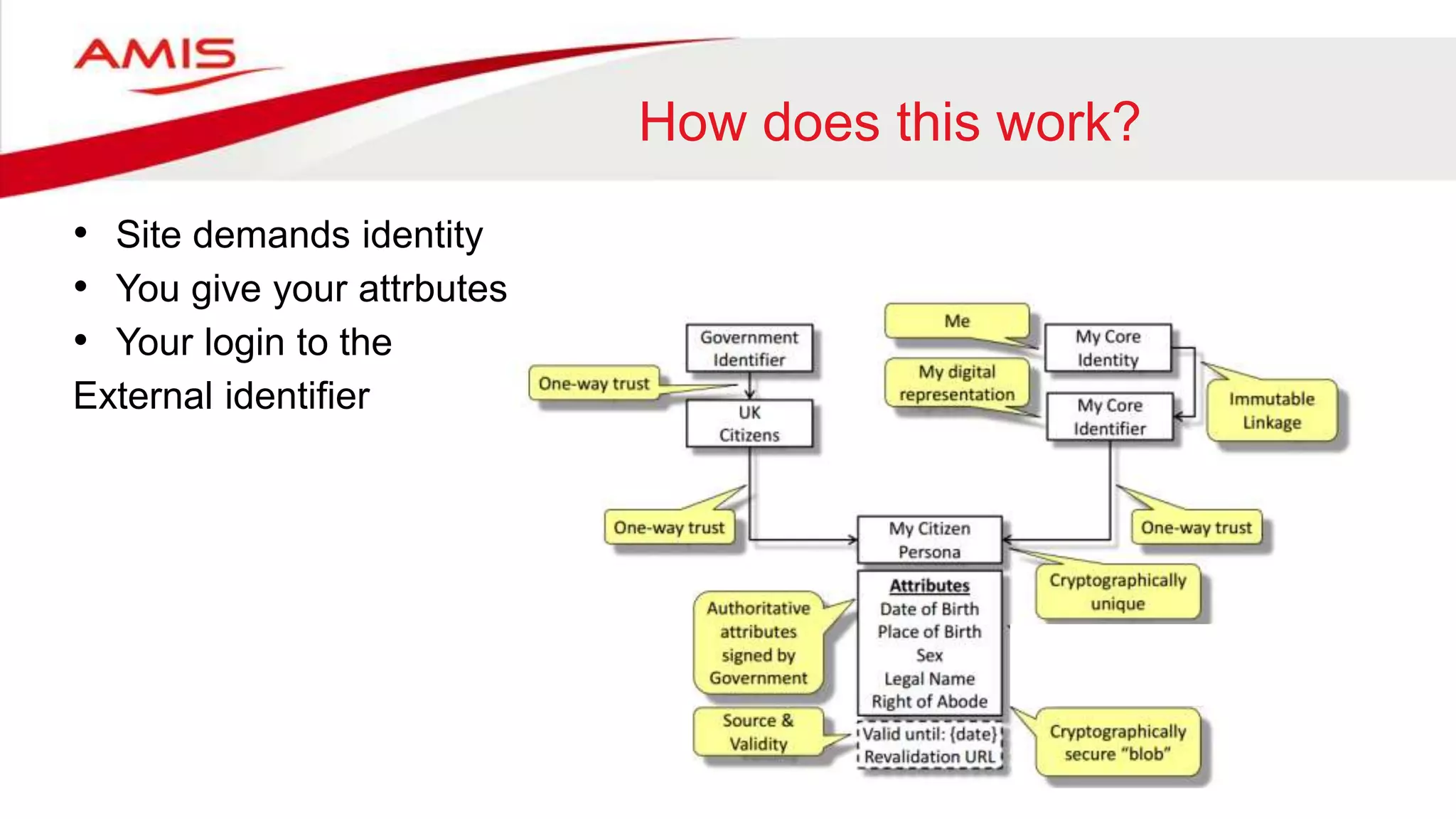
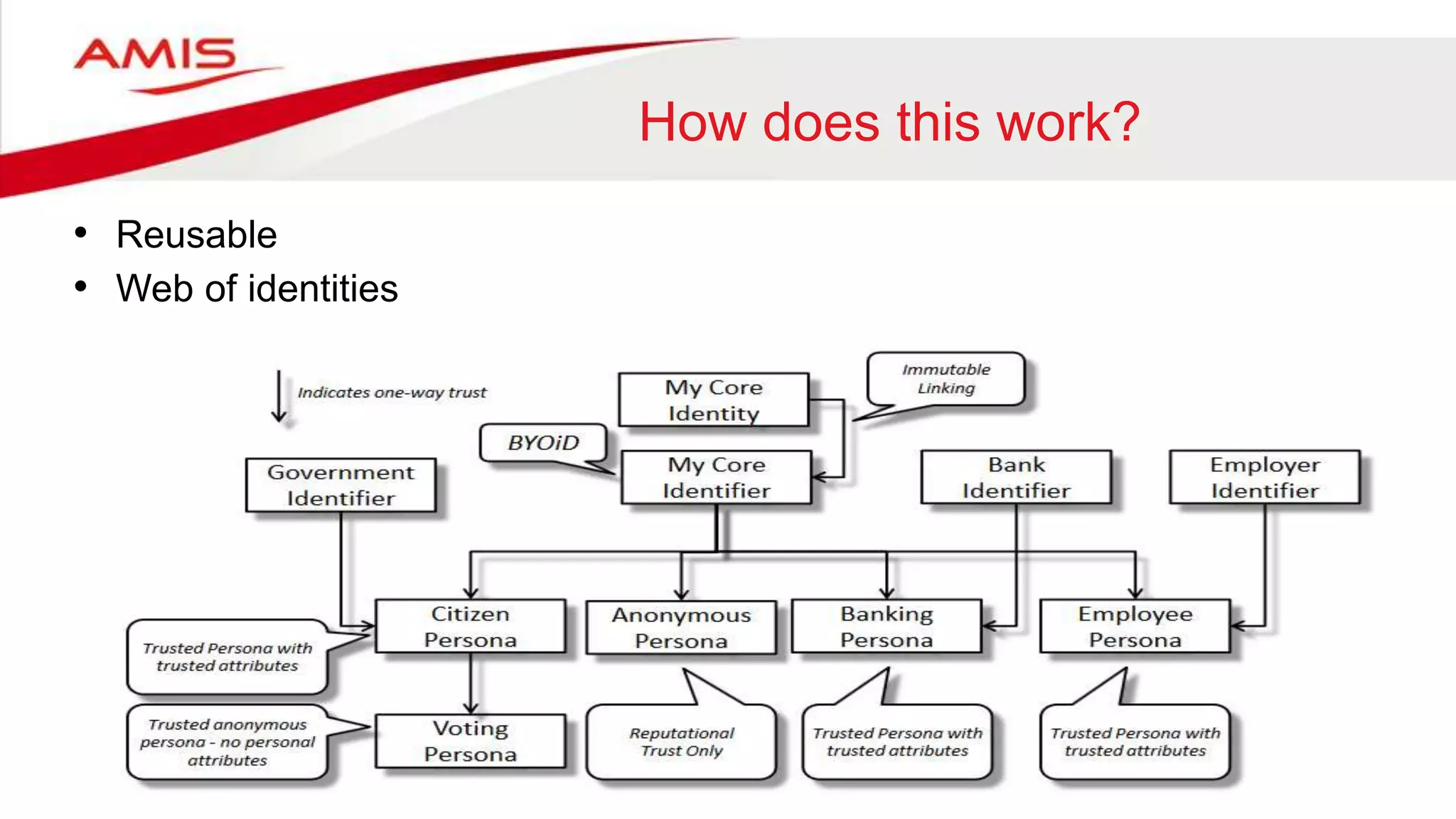
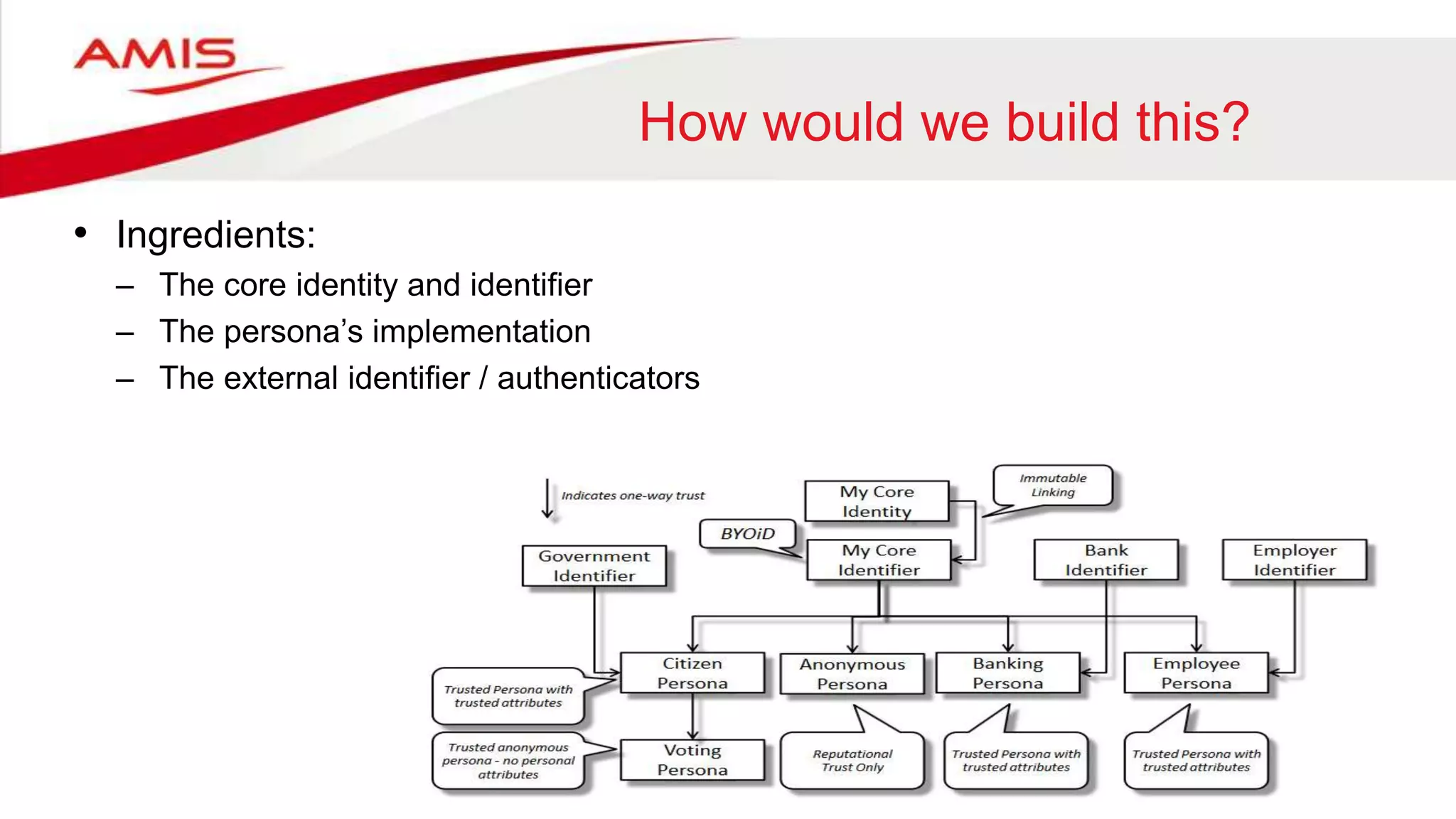
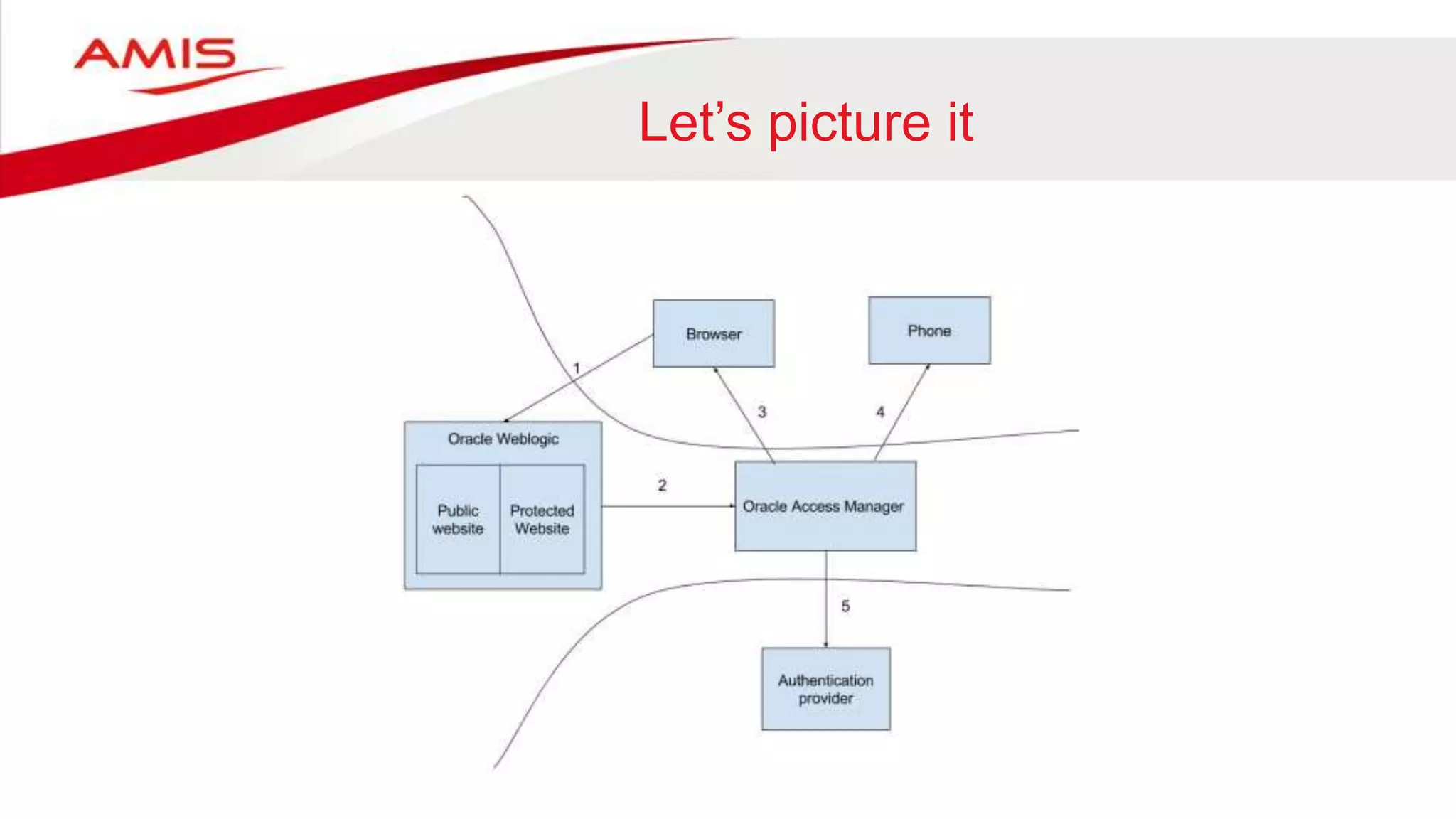
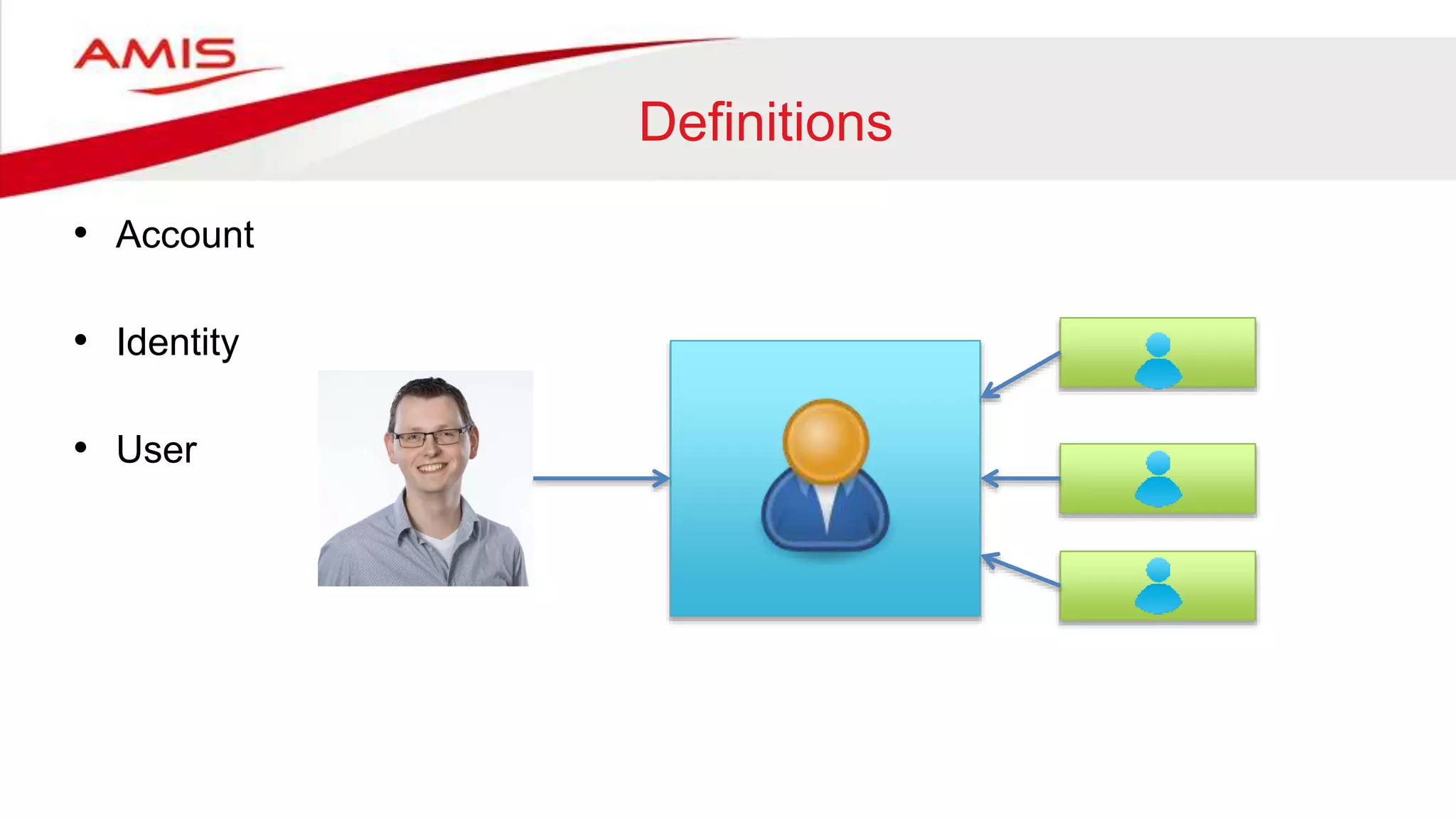
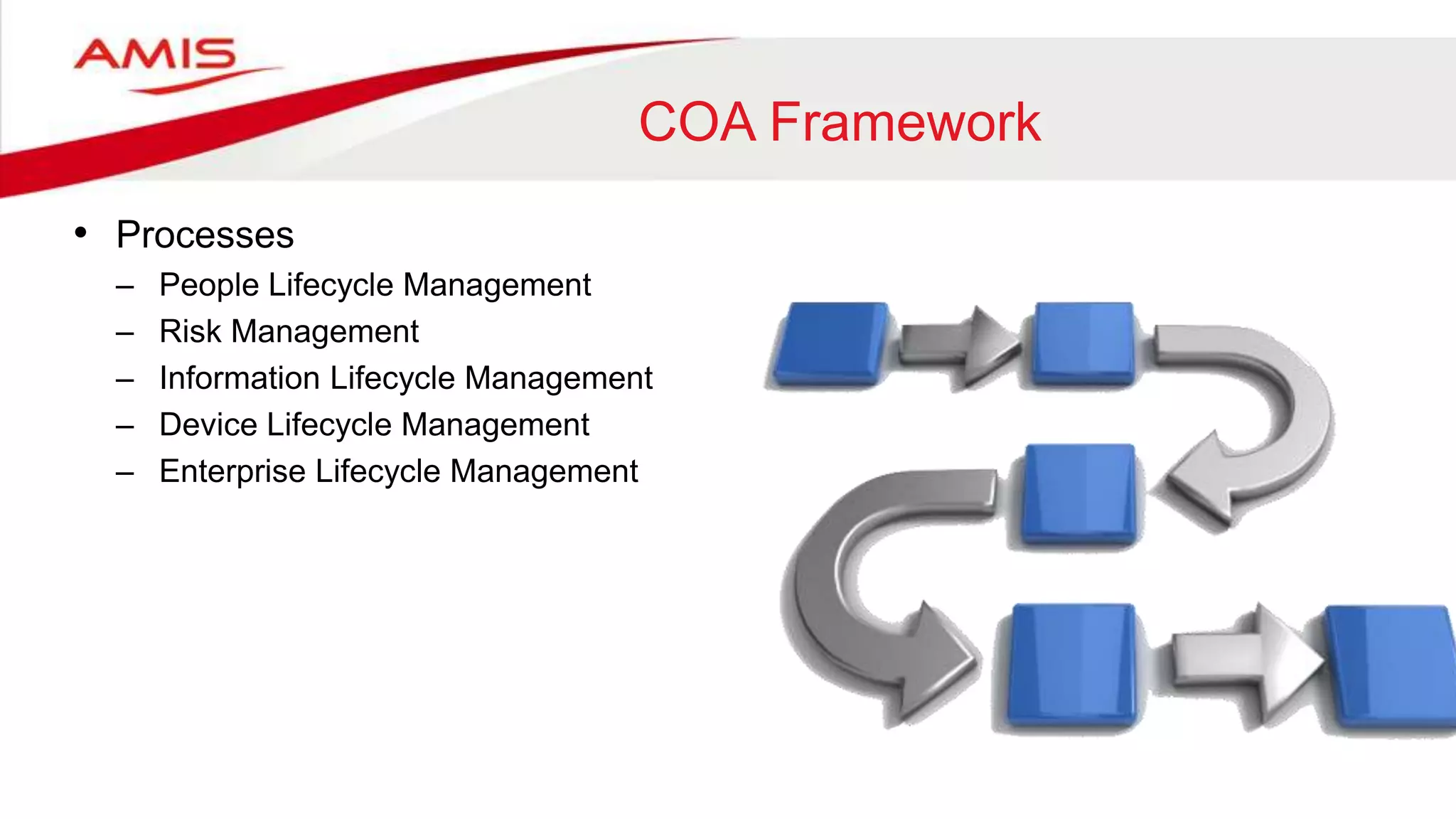
The document summarizes the evolution of digital identity from Identity 1.0 to Identity 3.0. Identity 1.0 focused on de-perimeterization and the COA framework for device and information lifecycle management. Identity 2.0 involved securely collaborating in clouds and access management commandments. Identity 3.0 brings the concept of bringing your own identity using a single global identifier with personas, enhanced privacy, and interchangeability without centralized infrastructure. The document outlines how an Identity 3.0 system could work using one-way trust between a core identifier and external identifiers to form personas with cryptographically signed attributes. It provides Oracle's WebLogic Server and Access Manager as an example platform to implement such a system.













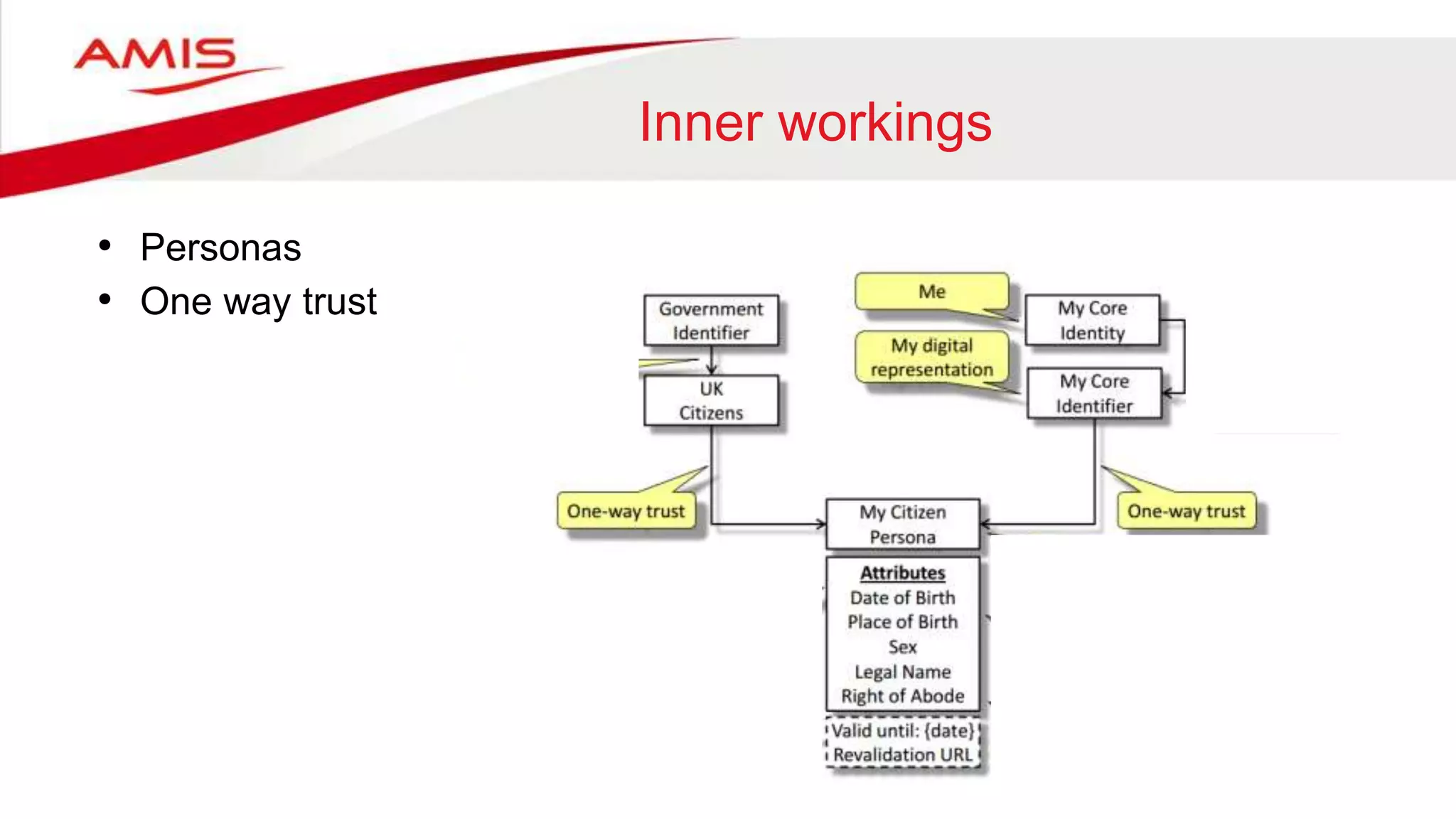
![Persona’s
19
[Entity: Organization]
Government
[Entity: Person]
Yourself
Citizen Persona with authoritative
(cryptographically) signed
attributes
Date of Birth = 01 Jan 2000
Place of Birth = London, UK
Sex at Birth = Male
Name at Birth = John Doe
Citizenship = Full British
Issued = 01 Jan 2015
Revalidation = gid.citizen.gov.uk](https://image.slidesharecdn.com/identity3-160608082446/75/Identity-3-0-and-Oracle-at-AMIS25-19-2048.jpg)