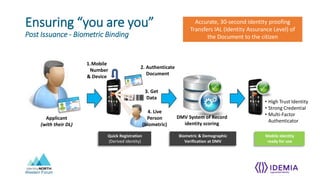
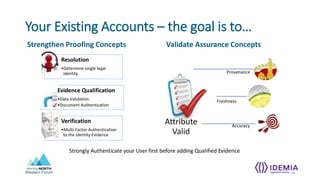
The document discusses identity proofing concepts for accurately provisioning credentials, including:
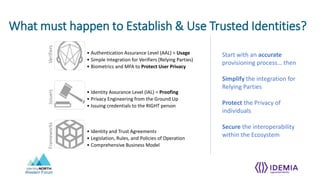
- Establishing trusted identities requires ensuring "only you can be you" through identity proofing and authentication assurance levels, and ensuring "you are you" through privacy engineering and issuing credentials to the right person.
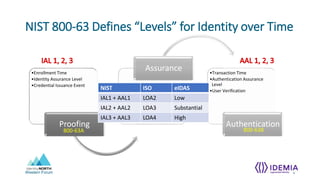
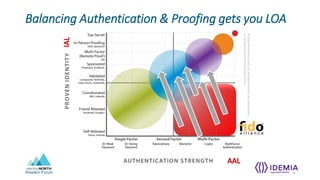
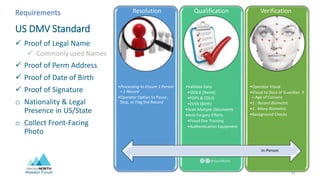
- NIST 800-63 defines levels for identity assurance over time including at enrollment, over time through credential integrity and revocation, and at authentication through multi-factor authentication.
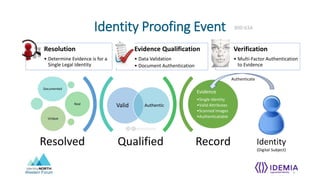
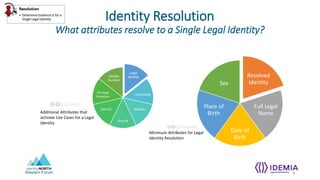
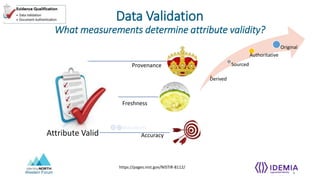
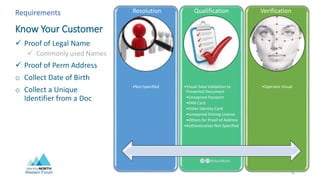
- Identity proofing events establish a qualified, unique identity record through evidence qualification, data validation, document authentication, and multi-factor authentication.
- Adding identity assurance to existing accounts can strengthen proofing by scanning identity documents, verifying the account holder's