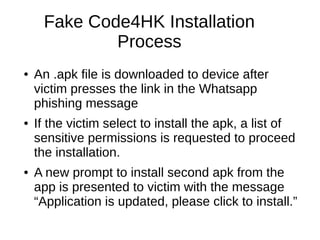
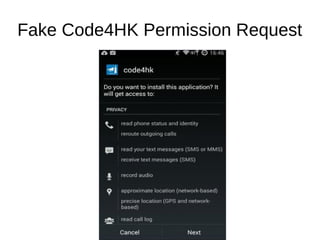
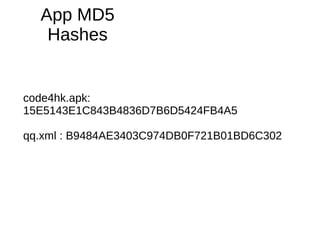
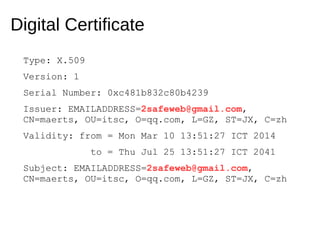
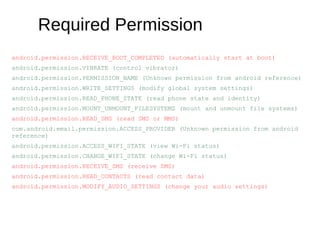
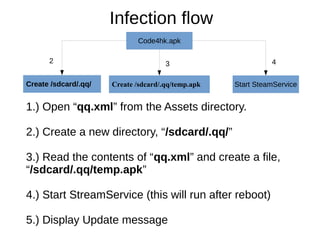
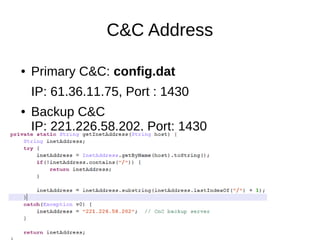
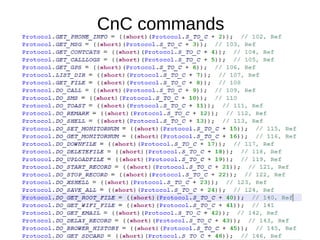
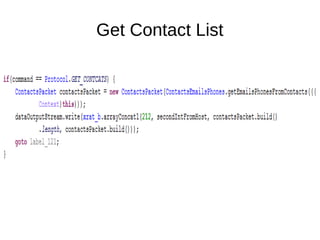
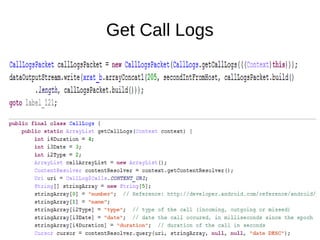
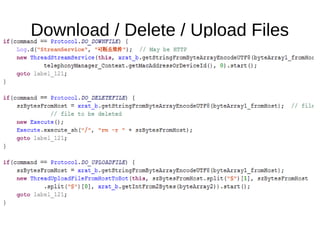
The document analyzes the Code4HK Android malware, detailing its distribution through phishing messages targeting Hong Kong activists. It outlines the extensive permissions and data the malware can access, its capabilities, and a reverse engineering methodology for analyzing such malware. Emphasis is placed on prevention strategies for users to avoid installing harmful applications from untrusted sources.