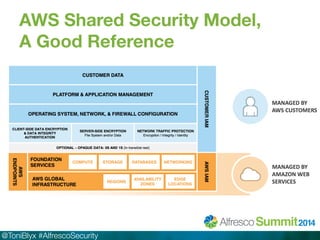
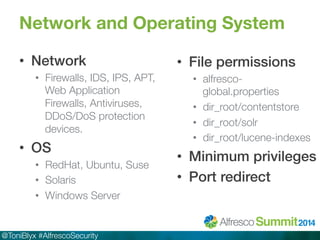
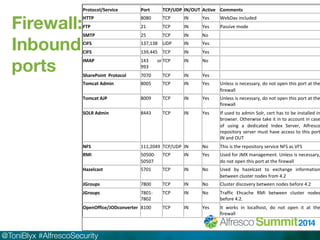
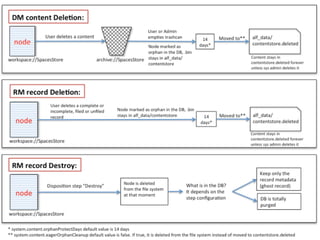
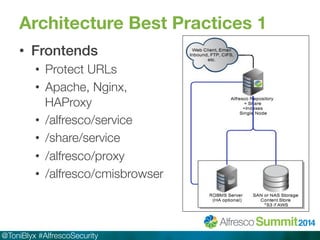
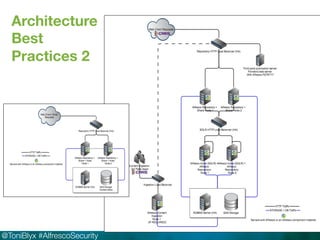
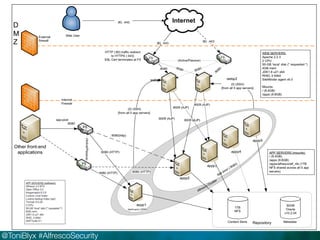
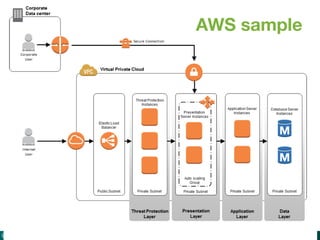
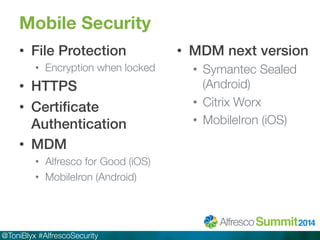
The document discusses Alfresco security best practices. It covers topics such as hardening the network and operating system, implementing firewall rules, assessing vulnerabilities, and compliance with standards. Best practices for the Alfresco implementation include staying current with patches, enforcing strong permissions, and deleting content when it is removed. The document provides an overview of security considerations for the Alfresco architecture, mobile access, and other deployment aspects.