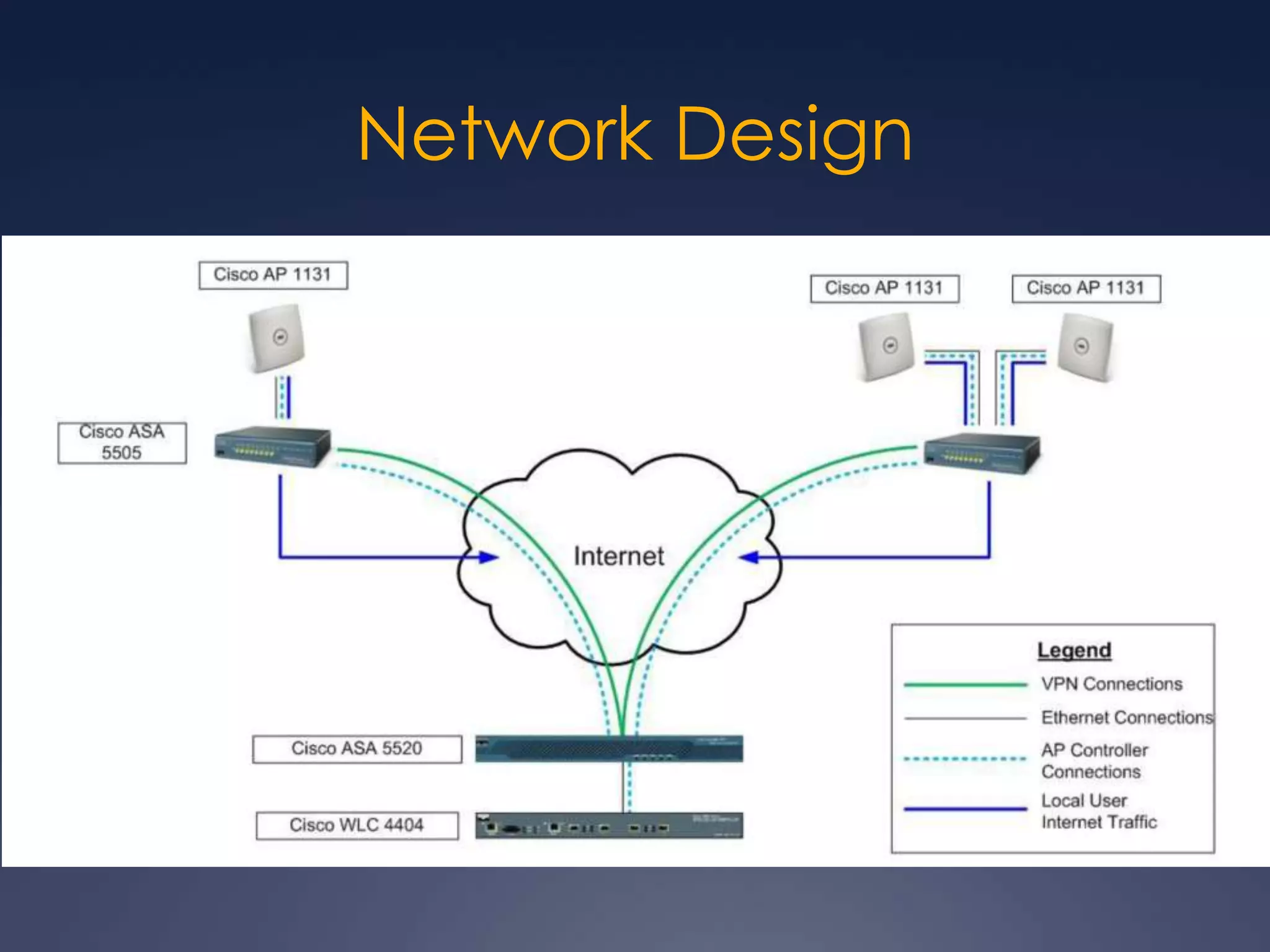
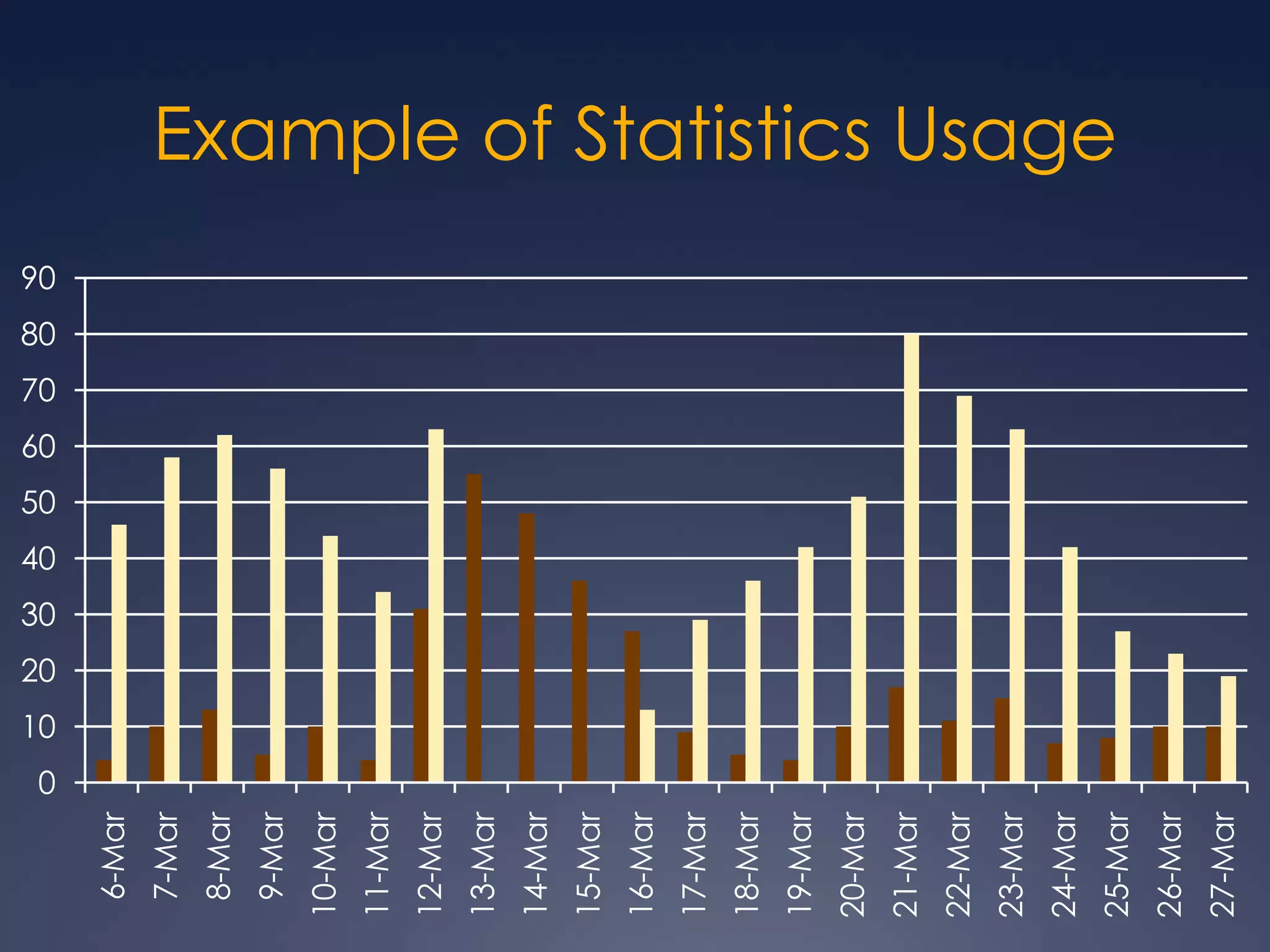
The Westchester Library System needed to upgrade its 7-year-old WiFi infrastructure to meet rising demand without increasing costs. It implemented a Cisco wireless solution with access points and a controller to provide remote management, scalability, and usage statistics. The network design included Cisco firewall equipment to enable private network features over the public internet using a VPN. This allows the library to control the number of users, enforce bandwidth limits, and gain valuable insights from usage statistics - all while saving staff time on issue diagnosis through remote monitoring.