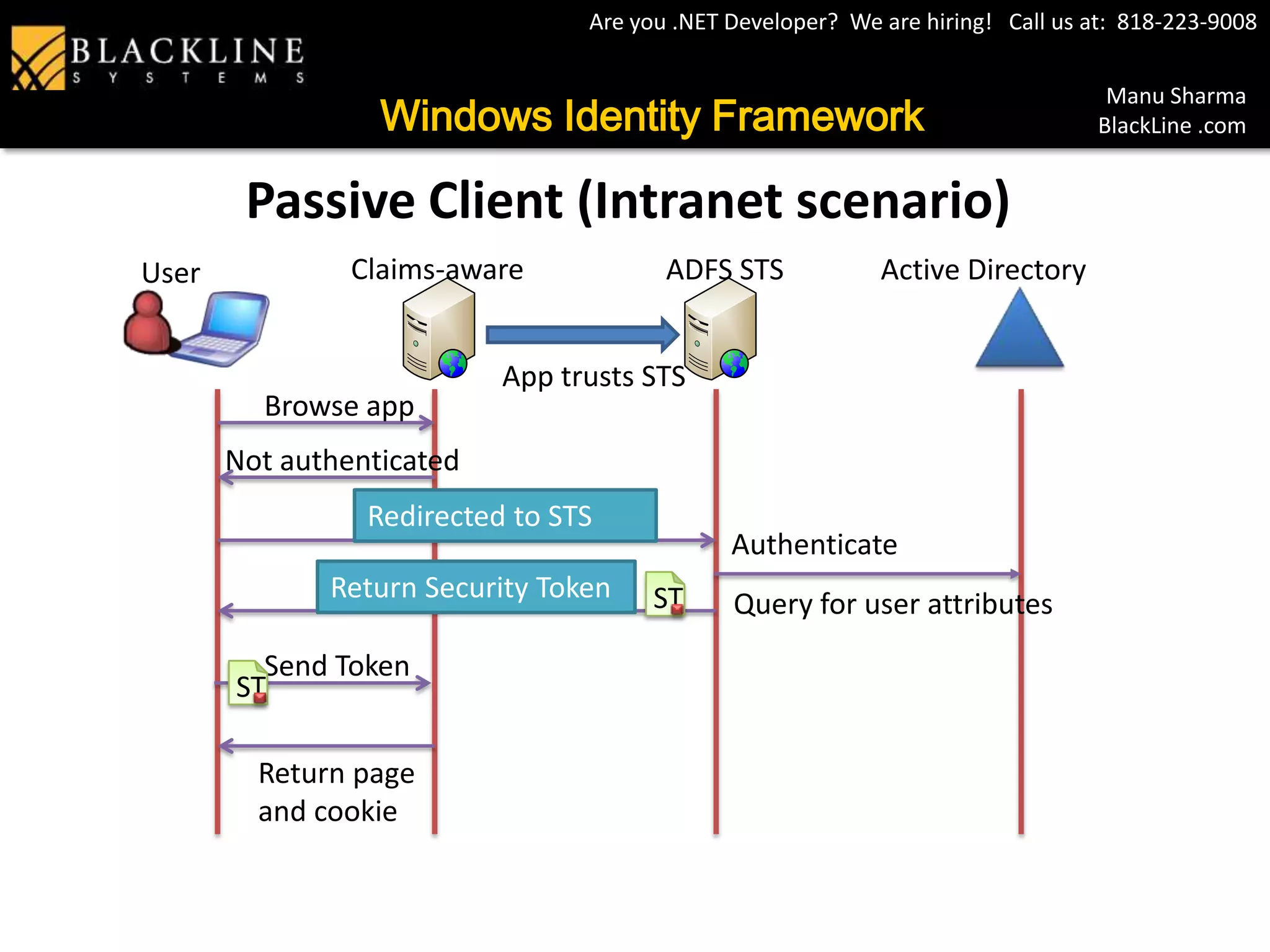
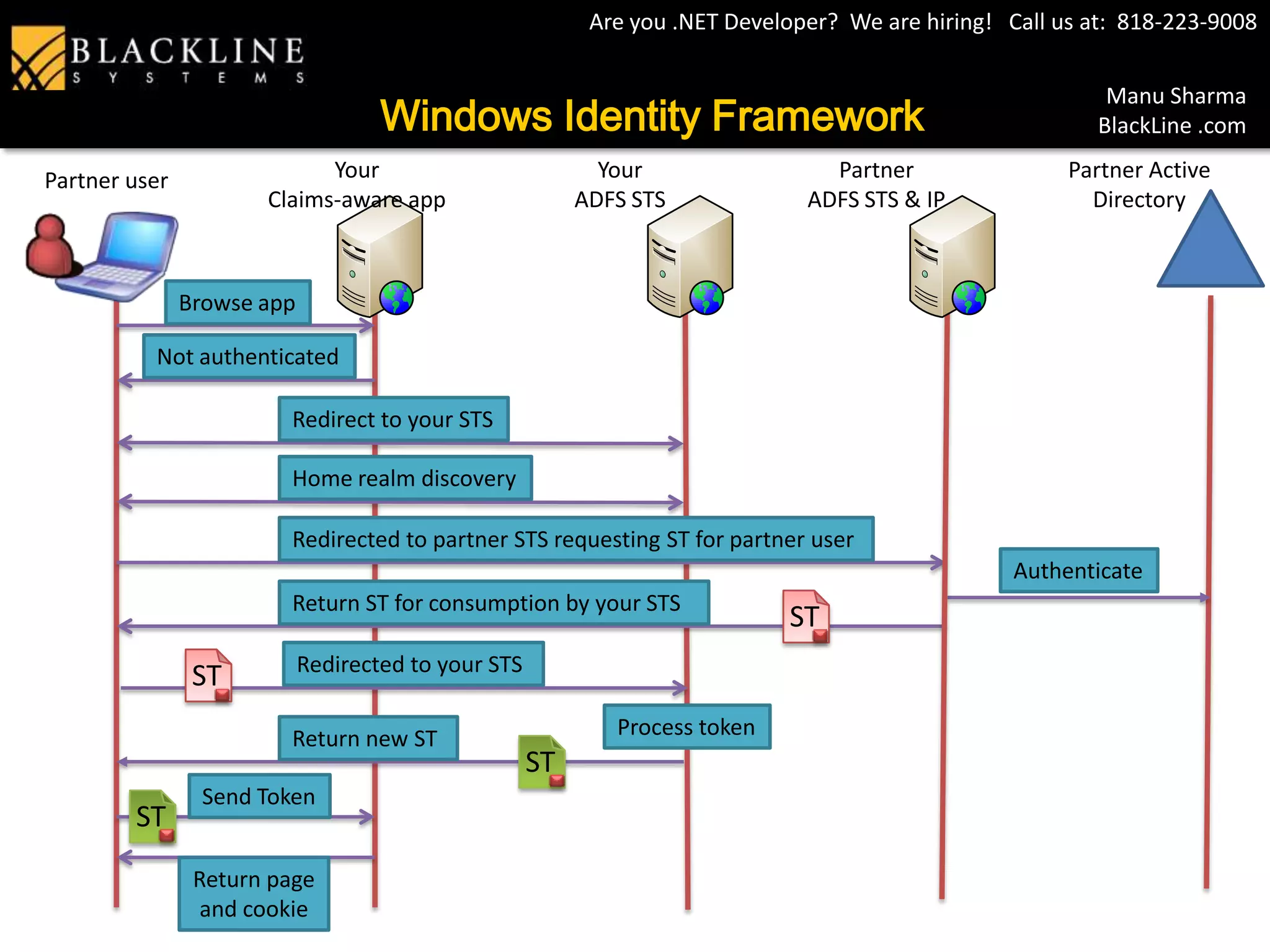
This document provides an overview of digital identity and single sign-on using Windows Identity Framework. It discusses problems with separate user stores per application and outlines how claims, security token services, Active Directory Federation Services, and Windows Identity Foundation can provide a common identity model to solve these problems. It then describes passive and partner federation scenarios and concludes with a demo.