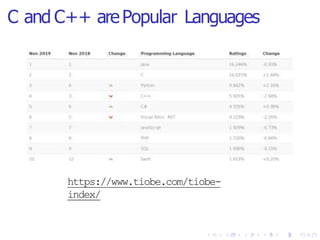
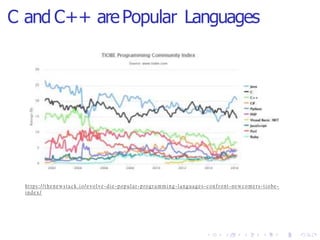
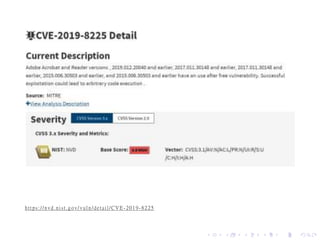
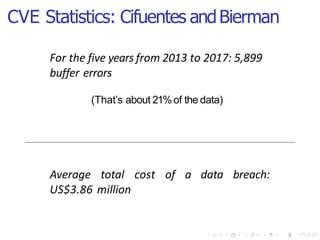
The document discusses the advantages of Rust over C and C++, particularly focusing on memory and thread safety through its ownership model which helps prevent common vulnerabilities. It highlights the prevalence of memory unsafety issues in software, which can lead to significant security risks and breaches. While Rust provides strong performance and a supportive community, it also presents challenges such as steep learning curves and complex error messages.































![Example: Use after Free in Rust
e r r o r [ E0382 ] : borrow o f moved v a l u e : ‘s‘
l e t s
- - > s r c / m a i n . r s : 1 2 : 2 4
|
8 |
|
|
|
= S t r i n g : : from ( " h e l l o " ) ;
- move o c c u r s b e c a u s e ‘s‘h a s t y p e ‘s t d : :
s t r i n g : : S t r i n g ‘, which does n o t
i m p l e m e n t t h e ‘Copy ‘ t r a i t
d o _ s t u f f ( s ) ;
- v a l u e moved h e r e
p r i n t l n ! ( " s= ’{}’",
he r e
. . .
11 |
|
12 |
|
|
s ) ;
^ v a l u e borrowe d
a f t e r move
e r r o r : a b o r t i n g due t o p r e v i o u s e r r o r](https://image.slidesharecdn.com/codeharbourdec2019-part1-191205114625/85/Why-Rust-by-Edd-Barrett-codeHarbour-December-2019-39-320.jpg)