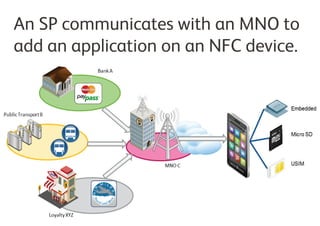
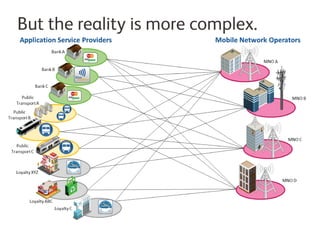
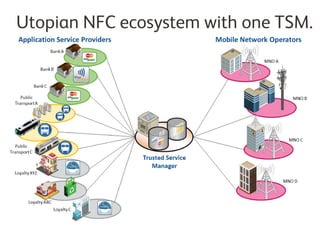
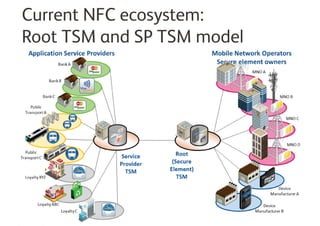
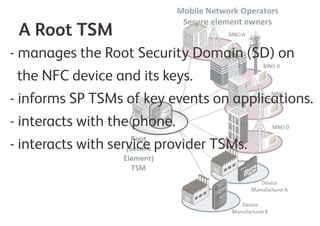
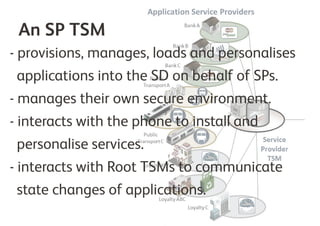
A Trusted Service Manager (TSM) is essential in the Near Field Communication (NFC) ecosystem, coordinating relationships among stakeholders and ensuring secure management of applications and consumer data. The current NFC landscape involves both root and service provider (SP) TSMs, each overseeing different aspects of application management and security. Organizations can become their own TSM to maintain control over customer interactions and adapt to changing market conditions.