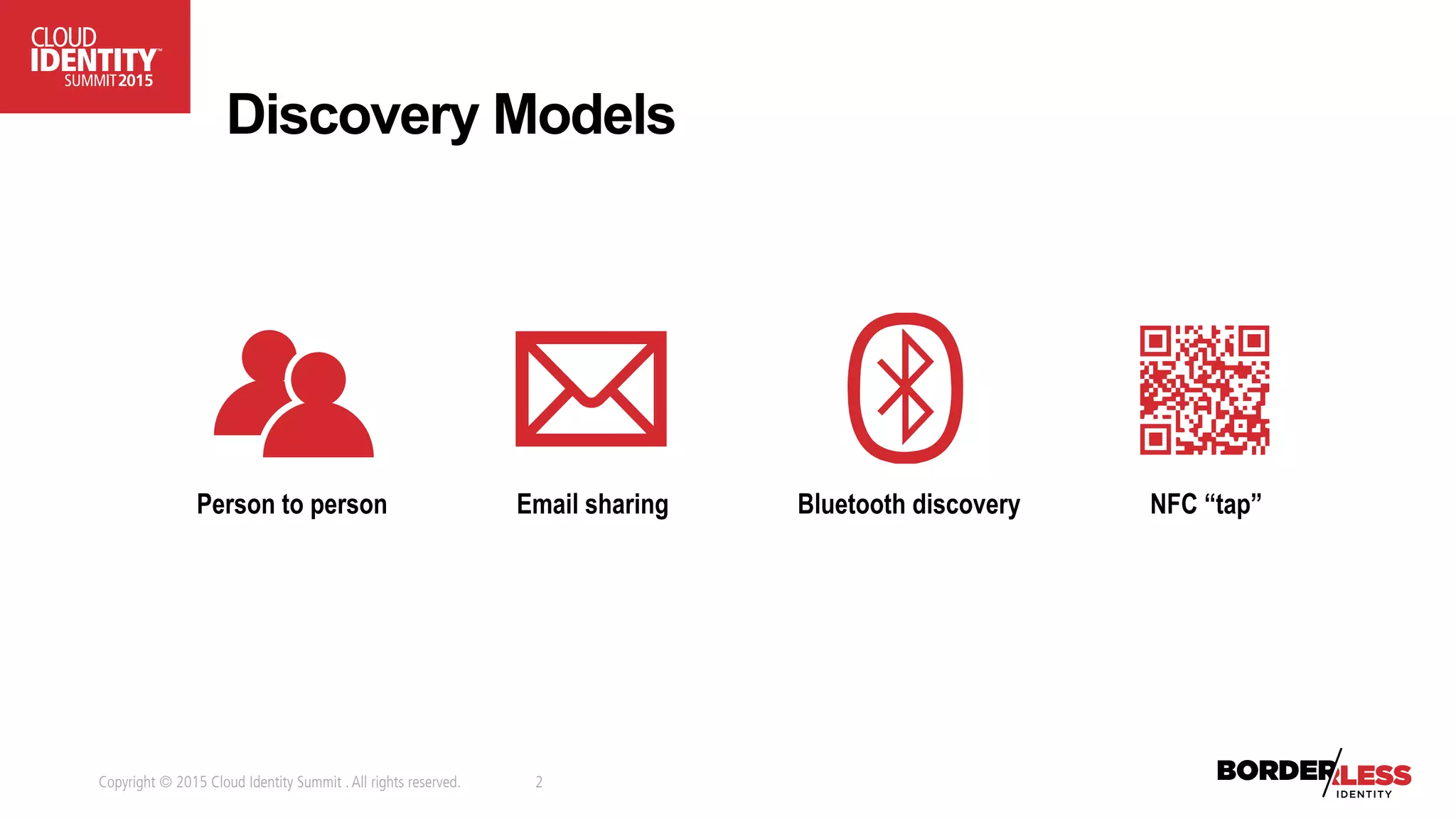
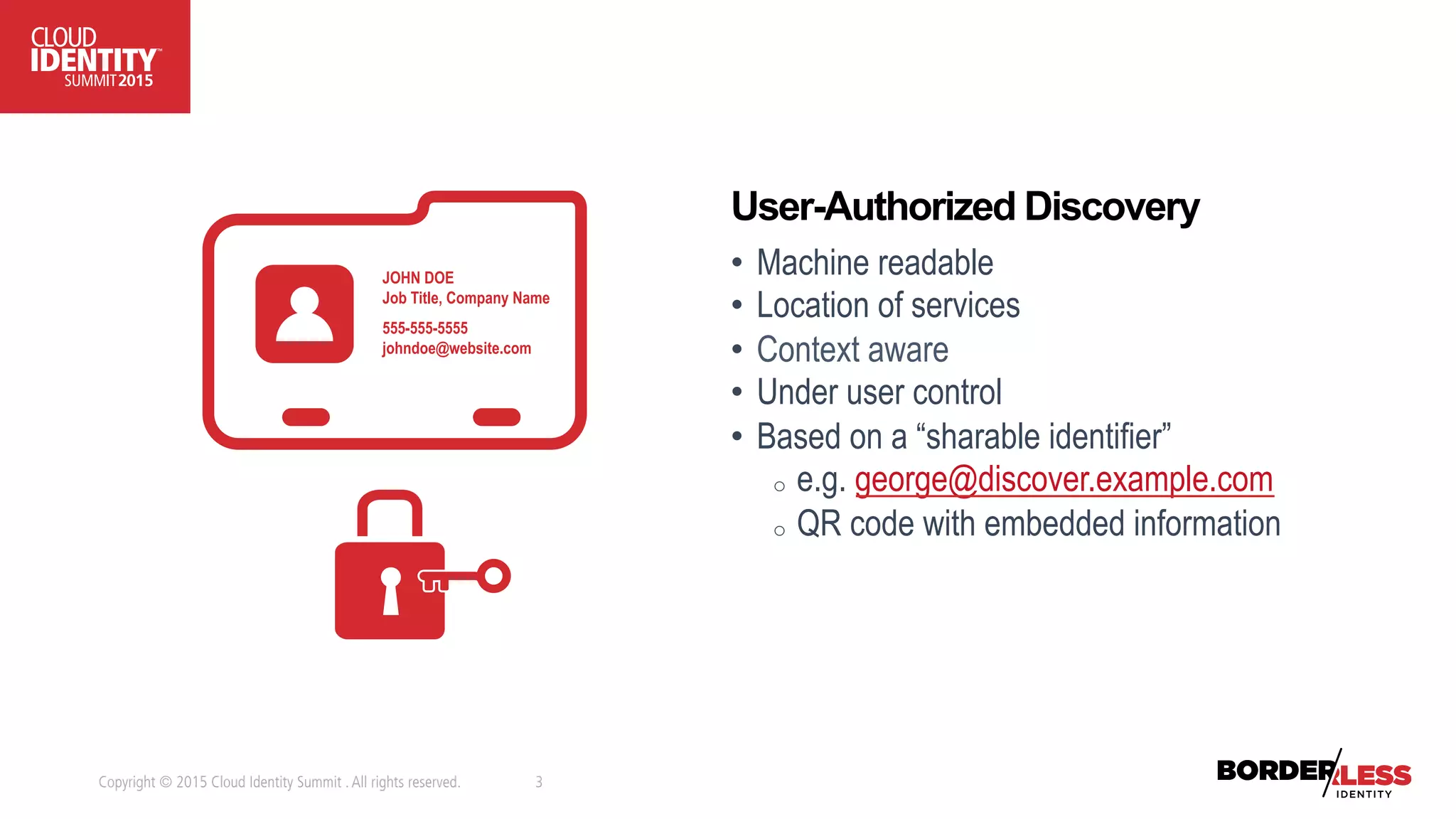
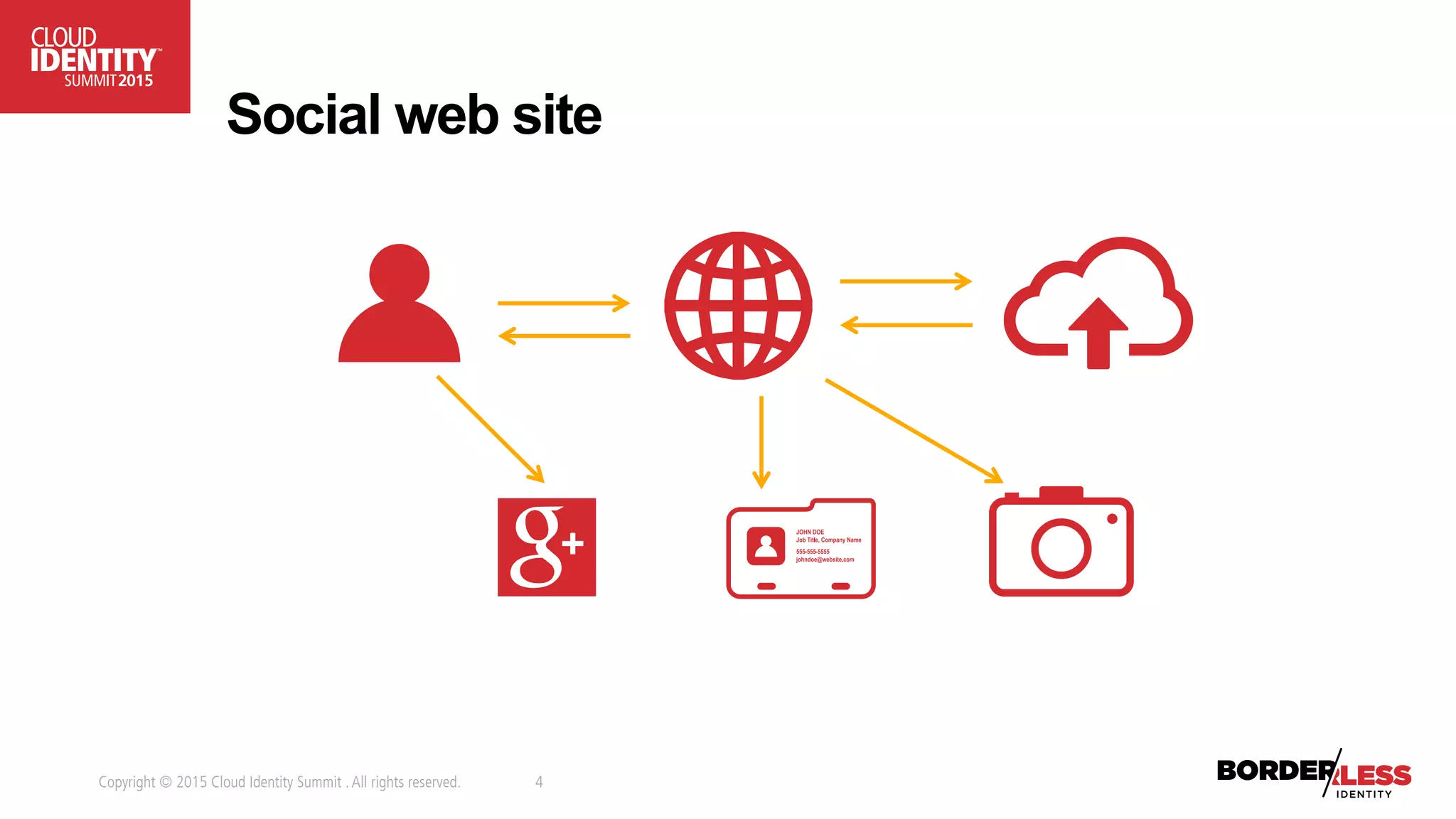
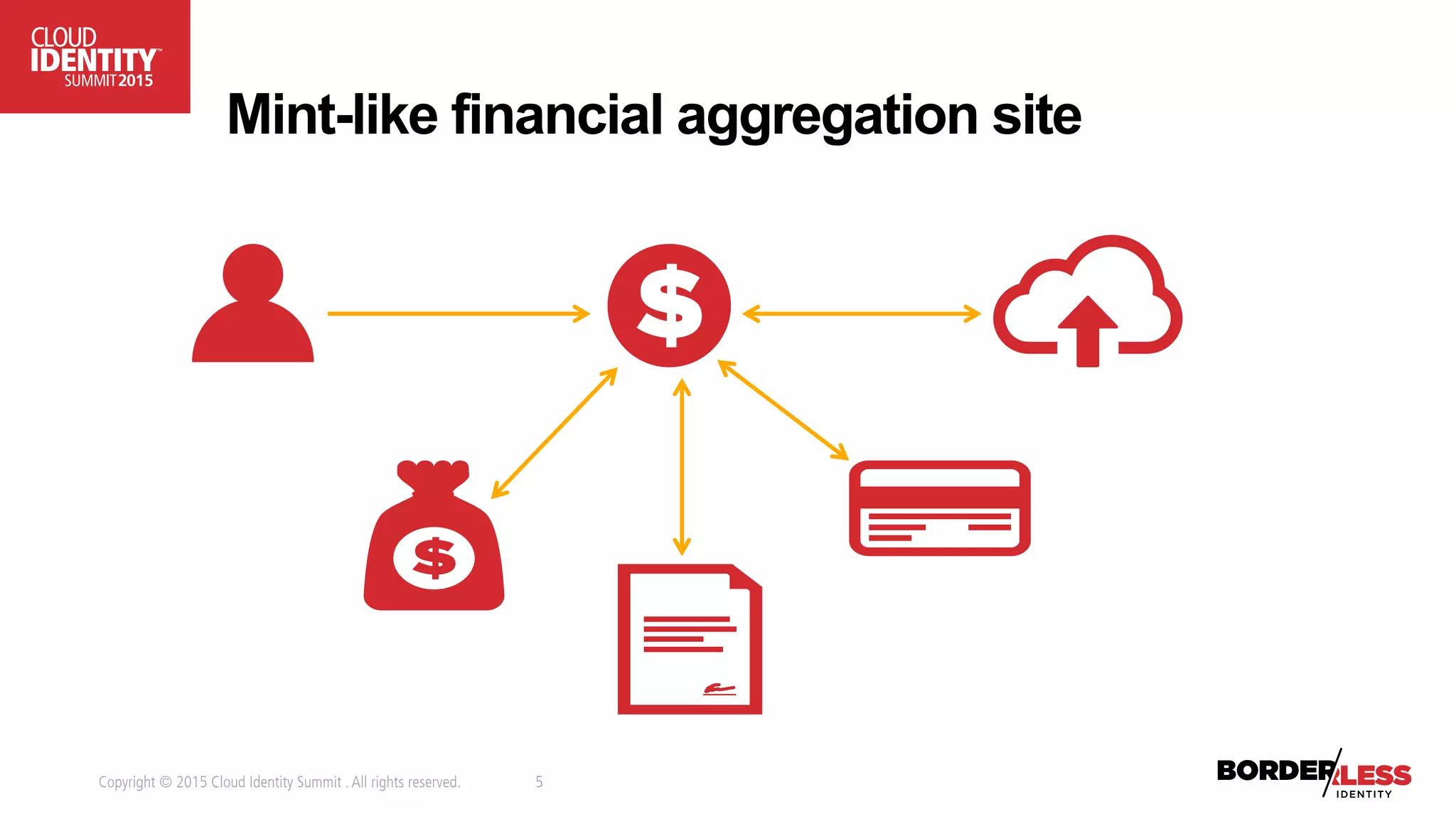
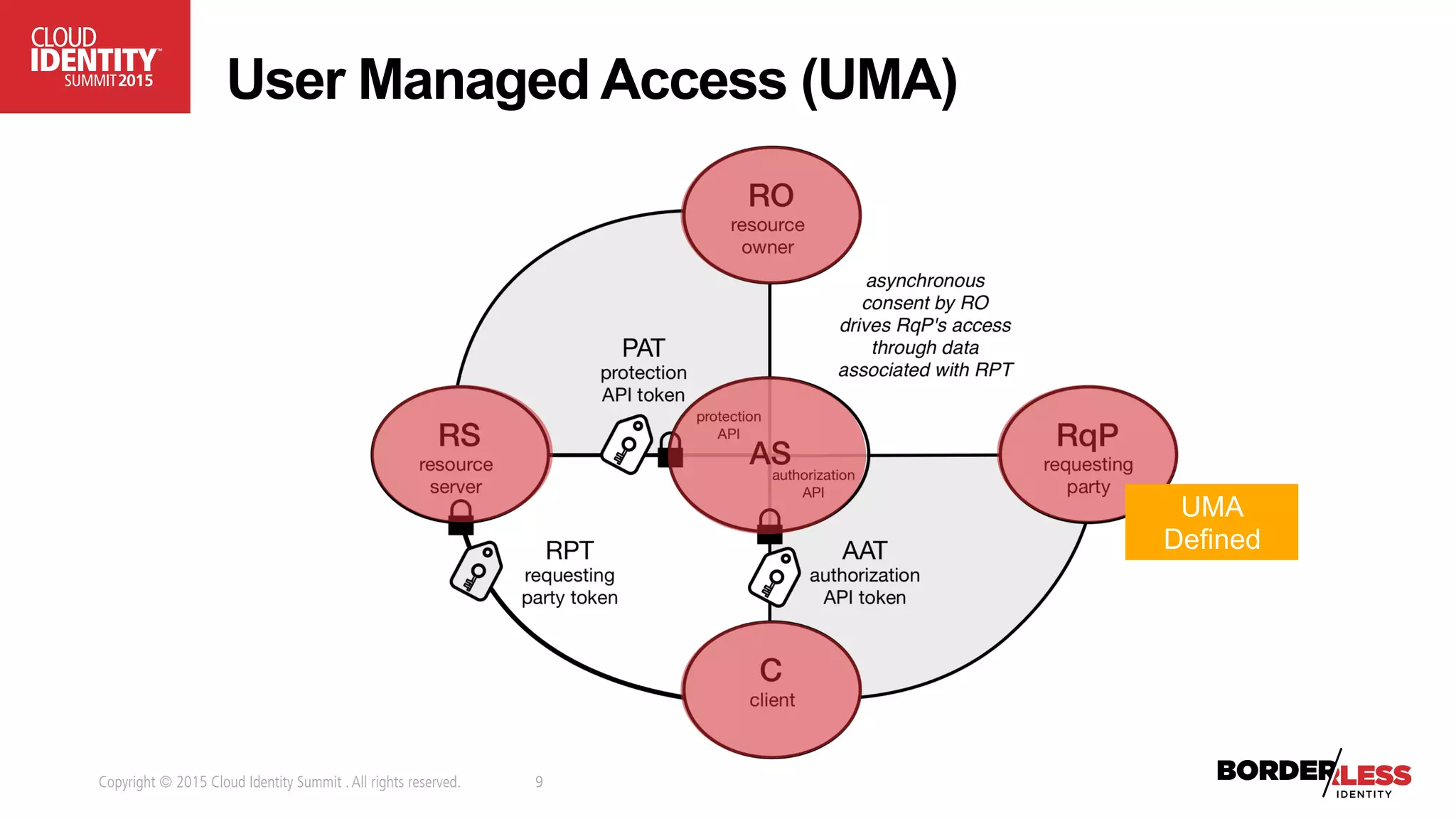
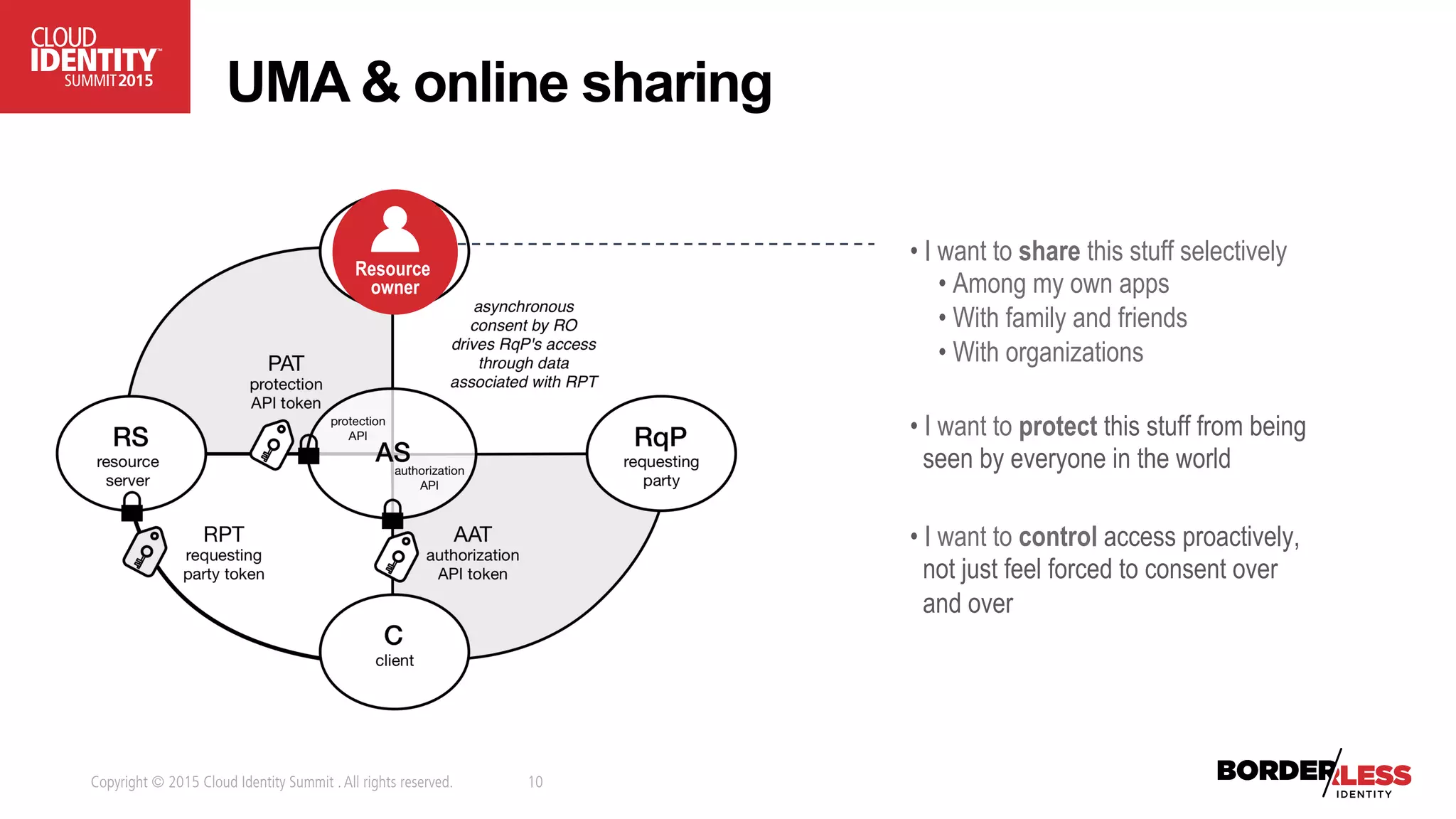
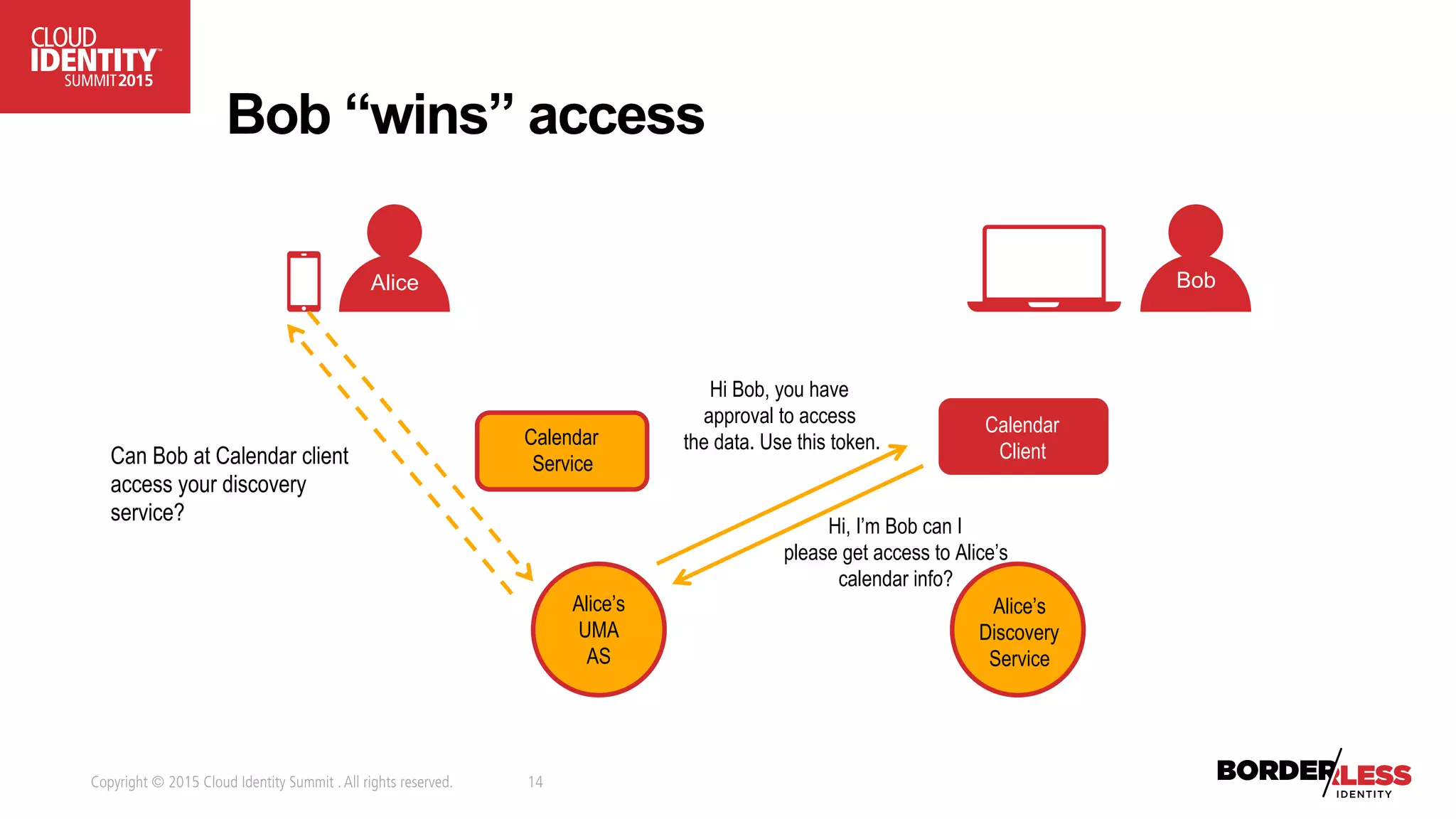
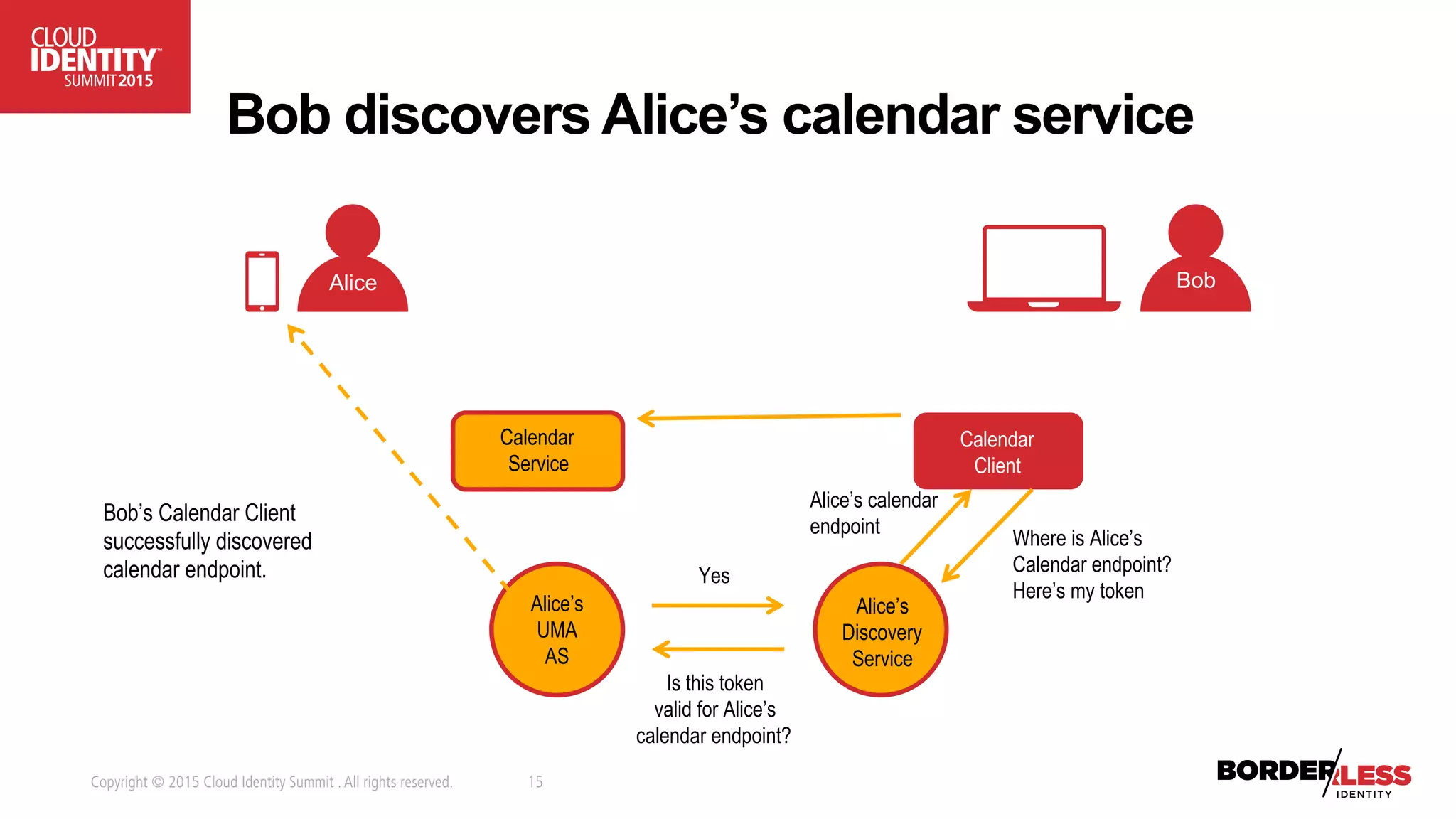
The document discusses user-authorized discovery protocols like Webfinger and User Managed Access (UMA) for improving privacy and control over shared personal information, specifically in the context of calendar sharing. It highlights the need for frameworks to manage authorization overload and to develop a taxonomy for relationship types, while proposing a pilot effort to demonstrate the viability of these combined protocols. Key concepts include proactive control over discoverable information, ensuring privacy, and managing authorization policies across various applications and devices.