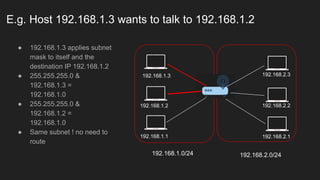
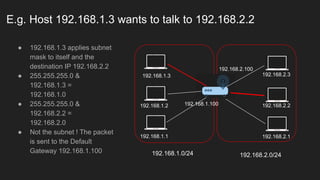
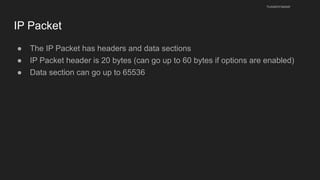
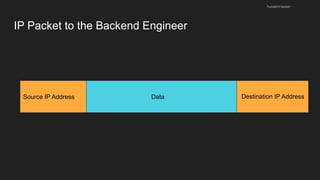
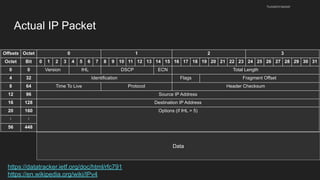
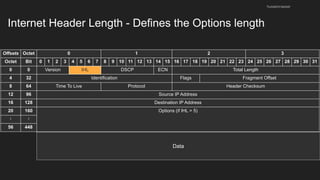
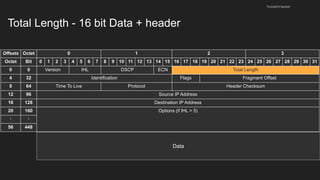
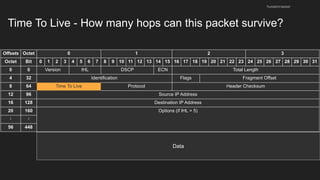
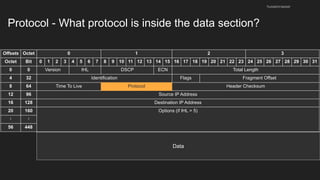
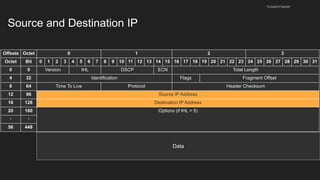
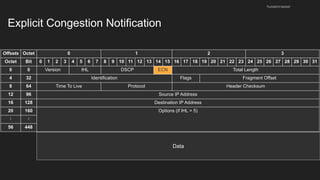
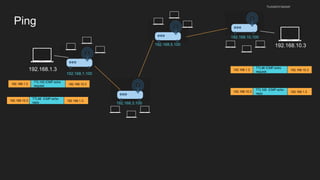
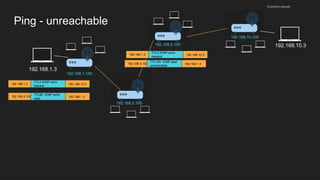
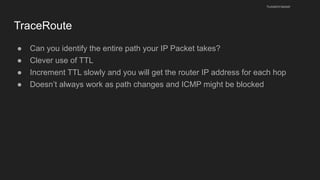
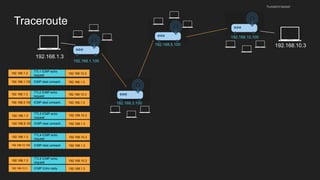
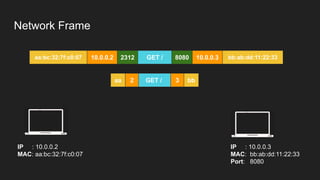
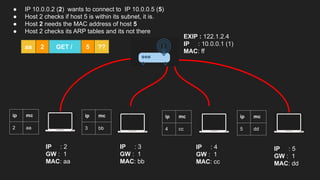
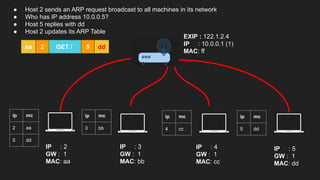
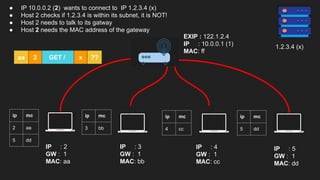
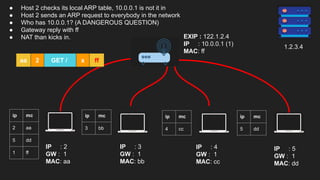
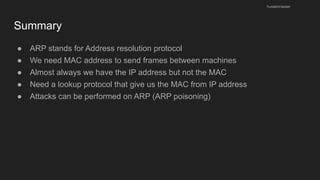
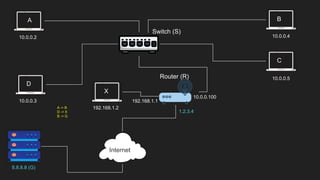
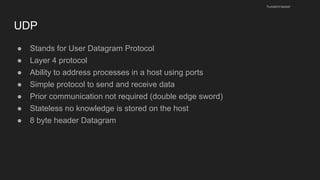
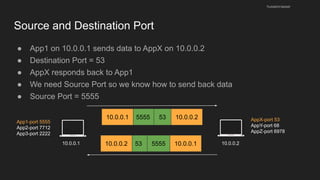
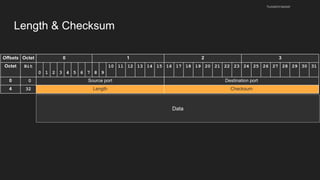
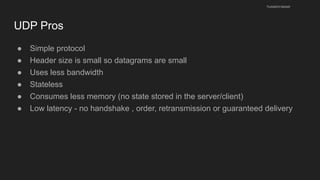
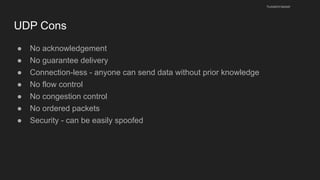
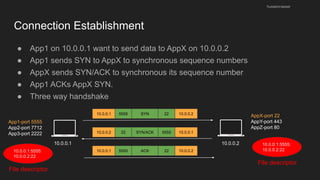
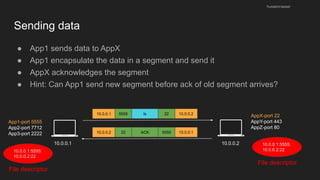
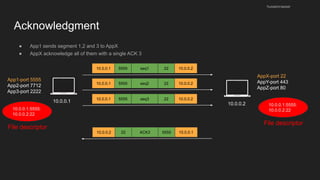
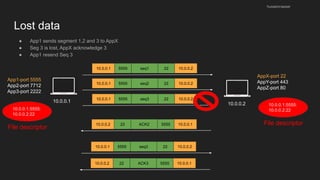
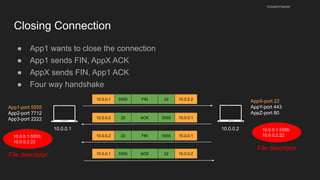
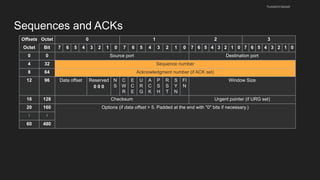
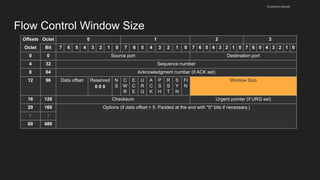
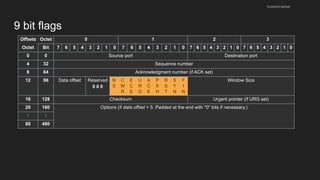
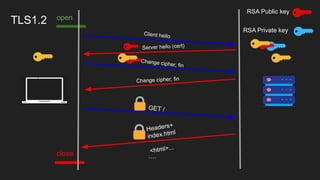
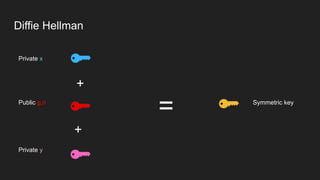
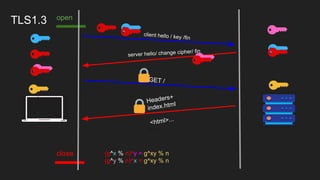
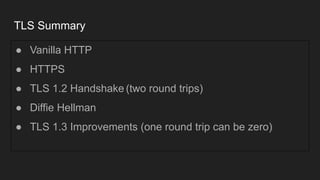
The document provides an overview of the Internet Protocol (IP) and its components, including IP addresses, subnet masks, and the concept of default gateways. It discusses the structure of IP packets, including headers, and protocols such as ICMP for handling network communication. Additionally, it covers ARP for resolving IP to MAC addresses and illustrates examples of packet transmission within and across subnets.