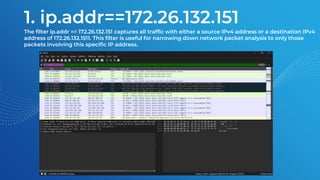
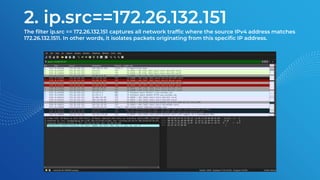
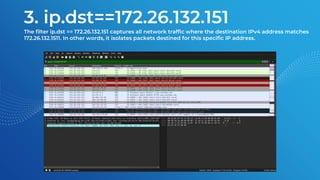
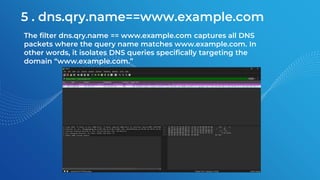
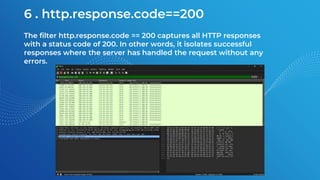
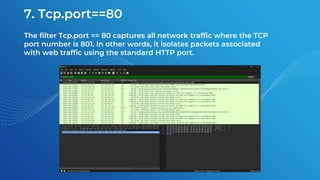
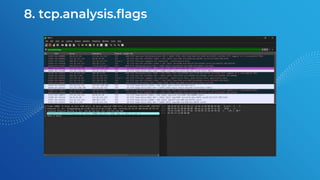
The document discusses the basics of traffic data analysis using Wireshark, including the concepts of IP addresses, URLs, and how to find an IP address from a URL. It outlines the differences between IPv4 and IPv6, as well as provides examples and commands for network packet analysis. Additionally, it covers the installation process for Wireshark on different operating systems and offers filter examples for capturing specific traffic data.