Total Network Security
•
0 likes•73 views
Messaging protection for Email, Spam, and Phishing. Endpoint protection with DNS filtering, Malware protection. Managed backup protections for Physical and Virtual Servers. Desktop and file backups, as well as Email archiving.
Report
Share
Report
Share
Download to read offline
Recommended
F-Secure E-mail and Server Security

F-Secure Email and Server Security takes server protection to the same level as F-Secure Client Security, which has been rated by AV-TEST as providing the best protection in the world. The combination of email and server security in the same package, along with several performance improving features, makes the solution easier to install and maintain.
Virtual Security

F-Secure’s Virtual Security brings best protection and top performance to all virtual environments, including mixed and hybrid environments
Internet gatekeeper

Gateway level protection for your business
- email and web virus scanning
- spam scanning
- email content filtering
- web content control
F-Secure Policy Manager - onsite security management with superior control

Get on top of your IT security and manage risks centrally.
Policy Manager gives you the control of your IT security. You decide what sites your employees are allowed to access, and what software is allowed to be run the web.
F-Secure Policy Manager automates daily operations such as protection of new computers and removal of disconnected hosts. This allows you to focus on more critical issues. Multiple administrators with different admin level rights can work simultaneously and you can control their access rights individually.
Business Suite - Gain control of your IT security

Choosing IT security does not need to be hard or time taking. Business Suite puts all the necessary elements into one package to make your life easier, and your business safer.
Business Suite puts you on the driver's seat, giving you the necessary tools to centrally manage the whole IT environment. The in-depth features give you full control to what is allowed in your network.
Business Suite includes security products from the gateway level to endpoints, with versatile management features for demanding IT environments.
Powerful email protection

Does your business deal with confidential information?
Complete protection for inbound and outbound email communication. Messaging Security Gateway blocks unwanted and harmful messages, and eliminates the possibility of data leakage.
Filter incoming mails, hide and encrypt your emails, block leaks, communicate in private, and keep your secrets truly secret.
Presentatie F-Secure 26062015

Beveiligingsdag SLBdiensten: 26 juni 2015
Presentatie F Secure: Leer hoe u uw IT-omgeving proactief en optimaal kunt beveiligen. Door Bert de Houwer, Presales Engineer, F-Secure.
HSB - DDoS Threats and Trends - Gurdeep Dhillon

Verisign is wereldwijd actief op het gebied van cyber security, en werpt met deze kennis een blik op wat in 2014 de DDoS threats en trends waren, en hoe dit zich verhoudt tot de Nederlandse situatie.
Recommended
F-Secure E-mail and Server Security

F-Secure Email and Server Security takes server protection to the same level as F-Secure Client Security, which has been rated by AV-TEST as providing the best protection in the world. The combination of email and server security in the same package, along with several performance improving features, makes the solution easier to install and maintain.
Virtual Security

F-Secure’s Virtual Security brings best protection and top performance to all virtual environments, including mixed and hybrid environments
Internet gatekeeper

Gateway level protection for your business
- email and web virus scanning
- spam scanning
- email content filtering
- web content control
F-Secure Policy Manager - onsite security management with superior control

Get on top of your IT security and manage risks centrally.
Policy Manager gives you the control of your IT security. You decide what sites your employees are allowed to access, and what software is allowed to be run the web.
F-Secure Policy Manager automates daily operations such as protection of new computers and removal of disconnected hosts. This allows you to focus on more critical issues. Multiple administrators with different admin level rights can work simultaneously and you can control their access rights individually.
Business Suite - Gain control of your IT security

Choosing IT security does not need to be hard or time taking. Business Suite puts all the necessary elements into one package to make your life easier, and your business safer.
Business Suite puts you on the driver's seat, giving you the necessary tools to centrally manage the whole IT environment. The in-depth features give you full control to what is allowed in your network.
Business Suite includes security products from the gateway level to endpoints, with versatile management features for demanding IT environments.
Powerful email protection

Does your business deal with confidential information?
Complete protection for inbound and outbound email communication. Messaging Security Gateway blocks unwanted and harmful messages, and eliminates the possibility of data leakage.
Filter incoming mails, hide and encrypt your emails, block leaks, communicate in private, and keep your secrets truly secret.
Presentatie F-Secure 26062015

Beveiligingsdag SLBdiensten: 26 juni 2015
Presentatie F Secure: Leer hoe u uw IT-omgeving proactief en optimaal kunt beveiligen. Door Bert de Houwer, Presales Engineer, F-Secure.
HSB - DDoS Threats and Trends - Gurdeep Dhillon

Verisign is wereldwijd actief op het gebied van cyber security, en werpt met deze kennis een blik op wat in 2014 de DDoS threats en trends waren, en hoe dit zich verhoudt tot de Nederlandse situatie.
Client Security - Best security for business workstations

Proactive behavior-based protection combined with automatic software updates and advanced tools to control web access provide the best protection for workstations and laptops.
Client Security offers award-winning protection for Windows computers. F-Secure has received the "Best protection" award from AV-Test four years in a row which clearly shows that you can trust us to keep your PCs safe.
Best corporate end-point protection 2013

AV-Test, a leading international and independent service provider in the fields of IT security and anti-virus research, has awarded F-Secure with Best Protection 2013 award for Windows corporate endpoint products.
Protection Service for Business

Powerful, modern, and designed to solve challenging security needs as easily as possible,
Protection Service For Business is one of the world’s leading multi-endpoint security solutions.
Nagios Conference 2014 - Jorge Higueros - SNAPS

Jorge Higueros's presentation on SNAPS.
The presentation was given during the Nagios World Conference North America held Oct 13th - Oct 16th, 2014 in Saint Paul, MN. For more information on the conference (including photos and videos), visit: http://go.nagios.com/conference
What is network security.docx

Start your Free Trial with Comodo Dome Now: https://cdome.comodo.com/free-trials.php
Learn More about Network Security: https://cdome.comodo.com/network-security.php
CyberArk Cleveland Defend End Point Infection and Lateral Movement

We had an amazing event in Cleveland. Customers have been asking for the slides for the event. This is the CyberArk Cleveland Defend End Point Infection and Lateral Movement slide deck. Thank you for all who attended.
Siem tools-monitor-your-network

Security Information and Event Management (SIEM) is a technology for cyber security that provides real-time analysis of security alerts generated by hardware as well as network applications.
SIEM monitoring supports earliest threat detection and fastest security incident response through the real-time collection and historical analysis of security events that are compiled from a broad variety of event and contextual data sources. SIEM tools also support compliance reporting and incident investigation via historical data analysis from the sources.
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scalable Platform by VP of Product, The New York Times
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovation With Your Product by VP of Product Design, Warner Music Group
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

Reflecting on new architectures for knowledge based systems in light of generative ai
More Related Content
What's hot
Client Security - Best security for business workstations

Proactive behavior-based protection combined with automatic software updates and advanced tools to control web access provide the best protection for workstations and laptops.
Client Security offers award-winning protection for Windows computers. F-Secure has received the "Best protection" award from AV-Test four years in a row which clearly shows that you can trust us to keep your PCs safe.
Best corporate end-point protection 2013

AV-Test, a leading international and independent service provider in the fields of IT security and anti-virus research, has awarded F-Secure with Best Protection 2013 award for Windows corporate endpoint products.
Protection Service for Business

Powerful, modern, and designed to solve challenging security needs as easily as possible,
Protection Service For Business is one of the world’s leading multi-endpoint security solutions.
Nagios Conference 2014 - Jorge Higueros - SNAPS

Jorge Higueros's presentation on SNAPS.
The presentation was given during the Nagios World Conference North America held Oct 13th - Oct 16th, 2014 in Saint Paul, MN. For more information on the conference (including photos and videos), visit: http://go.nagios.com/conference
What is network security.docx

Start your Free Trial with Comodo Dome Now: https://cdome.comodo.com/free-trials.php
Learn More about Network Security: https://cdome.comodo.com/network-security.php
CyberArk Cleveland Defend End Point Infection and Lateral Movement

We had an amazing event in Cleveland. Customers have been asking for the slides for the event. This is the CyberArk Cleveland Defend End Point Infection and Lateral Movement slide deck. Thank you for all who attended.
Siem tools-monitor-your-network

Security Information and Event Management (SIEM) is a technology for cyber security that provides real-time analysis of security alerts generated by hardware as well as network applications.
SIEM monitoring supports earliest threat detection and fastest security incident response through the real-time collection and historical analysis of security events that are compiled from a broad variety of event and contextual data sources. SIEM tools also support compliance reporting and incident investigation via historical data analysis from the sources.
What's hot (10)
Client Security - Best security for business workstations

Client Security - Best security for business workstations
CyberArk Cleveland Defend End Point Infection and Lateral Movement

CyberArk Cleveland Defend End Point Infection and Lateral Movement
Viewers also liked
Viewers also liked (7)
Recently uploaded
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scalable Platform by VP of Product, The New York Times
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovation With Your Product by VP of Product Design, Warner Music Group
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

Reflecting on new architectures for knowledge based systems in light of generative ai
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Have you ever wanted a Ruby client API to communicate with your web service? Smithy is a protocol-agnostic language for defining services and SDKs. Smithy Ruby is an implementation of Smithy that generates a Ruby SDK using a Smithy model. In this talk, we will explore Smithy and Smithy Ruby to learn how to generate custom feature-rich SDKs that can communicate with any web service, such as a Rails JSON API.
Elevating Tactical DDD Patterns Through Object Calisthenics

After immersing yourself in the blue book and its red counterpart, attending DDD-focused conferences, and applying tactical patterns, you're left with a crucial question: How do I ensure my design is effective? Tactical patterns within Domain-Driven Design (DDD) serve as guiding principles for creating clear and manageable domain models. However, achieving success with these patterns requires additional guidance. Interestingly, we've observed that a set of constraints initially designed for training purposes remarkably aligns with effective pattern implementation, offering a more ‘mechanical’ approach. Let's explore together how Object Calisthenics can elevate the design of your tactical DDD patterns, offering concrete help for those venturing into DDD for the first time!
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

The IoT and OT threat landscape report has been prepared by the Threat Research Team at Sectrio using data from Sectrio, cyber threat intelligence farming facilities spread across over 85 cities around the world. In addition, Sectrio also runs AI-based advanced threat and payload engagement facilities that serve as sinks to attract and engage sophisticated threat actors, and newer malware including new variants and latent threats that are at an earlier stage of development.
The latest edition of the OT/ICS and IoT security Threat Landscape Report 2024 also covers:
State of global ICS asset and network exposure
Sectoral targets and attacks as well as the cost of ransom
Global APT activity, AI usage, actor and tactic profiles, and implications
Rise in volumes of AI-powered cyberattacks
Major cyber events in 2024
Malware and malicious payload trends
Cyberattack types and targets
Vulnerability exploit attempts on CVEs
Attacks on counties – USA
Expansion of bot farms – how, where, and why
In-depth analysis of the cyber threat landscape across North America, South America, Europe, APAC, and the Middle East
Why are attacks on smart factories rising?
Cyber risk predictions
Axis of attacks – Europe
Systemic attacks in the Middle East
Download the full report from here:
https://sectrio.com/resources/ot-threat-landscape-reports/sectrio-releases-ot-ics-and-iot-security-threat-landscape-report-2024/
JMeter webinar - integration with InfluxDB and Grafana

Watch this recorded webinar about real-time monitoring of application performance. See how to integrate Apache JMeter, the open-source leader in performance testing, with InfluxDB, the open-source time-series database, and Grafana, the open-source analytics and visualization application.
In this webinar, we will review the benefits of leveraging InfluxDB and Grafana when executing load tests and demonstrate how these tools are used to visualize performance metrics.
Length: 30 minutes
Session Overview
-------------------------------------------
During this webinar, we will cover the following topics while demonstrating the integrations of JMeter, InfluxDB and Grafana:
- What out-of-the-box solutions are available for real-time monitoring JMeter tests?
- What are the benefits of integrating InfluxDB and Grafana into the load testing stack?
- Which features are provided by Grafana?
- Demonstration of InfluxDB and Grafana using a practice web application
To view the webinar recording, go to:
https://www.rttsweb.com/jmeter-integration-webinar
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Presented by Suzanne Phillips and Alex Marcotte
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
Accelerate your Kubernetes clusters with Varnish Caching

A presentation about the usage and availability of Varnish on Kubernetes. This talk explores the capabilities of Varnish caching and shows how to use the Varnish Helm chart to deploy it to Kubernetes.
This presentation was delivered at K8SUG Singapore. See https://feryn.eu/presentations/accelerate-your-kubernetes-clusters-with-varnish-caching-k8sug-singapore-28-2024 for more details.
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designer, Beats by Dr Dre
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

91mobiles recently conducted a Smart TV Buyer Insights Survey in which we asked over 3,000 respondents about the TV they own, aspects they look at on a new TV, and their TV buying preferences.
Bits & Pixels using AI for Good.........

A whirlwind tour of tech & AI for socio-environmental impact.
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on the notifications, alerts, and approval requests using Slack for Bonterra Impact Management. The solutions covered in this webinar can also be deployed for Microsoft Teams.
Interested in deploying notification automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
Recently uploaded (20)
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

To Graph or Not to Graph Knowledge Graph Architectures and LLMs
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Generating a custom Ruby SDK for your web service or Rails API using Smithy
Elevating Tactical DDD Patterns Through Object Calisthenics

Elevating Tactical DDD Patterns Through Object Calisthenics
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

State of ICS and IoT Cyber Threat Landscape Report 2024 preview
JMeter webinar - integration with InfluxDB and Grafana

JMeter webinar - integration with InfluxDB and Grafana
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Assuring Contact Center Experiences for Your Customers With ThousandEyes
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
Accelerate your Kubernetes clusters with Varnish Caching

Accelerate your Kubernetes clusters with Varnish Caching
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designe...
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...
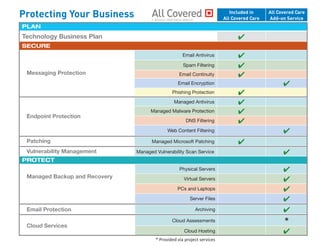
Total Network Security
- 1. PROTECT Managed Backup and RecoveryEndpoint Encryption Physical Servers ✔ Virtual Servers ✔ PCs and Laptops ✔ Server Files ✔ Email Protectioned Hosting Ticketing System Archiving ✔ Cloud Services Cloud Assessments * Cloud Hosting ✔ * Provided via project services PLAN Included in All Covered Care All Covered Care Add-on Service PLAN Technology Business Plan ✔ SECURE Messaging Protection Email Antivirus ✔ Spam Filtering ✔ Email Continuity ✔ Email Encryption ✔ Phishing Protection ✔ Endpoint Protection Managed Antivirus ✔ Managed Malware Protection ✔ DNS Filtering ✔ Web Content Filtering ✔ Patching Managed Microsoft Patching ✔ Vulnerability Management Managed Vulnerability Scan Service ✔ Protecting Your Business IT SERVICES FROM KONICA MINOLTA