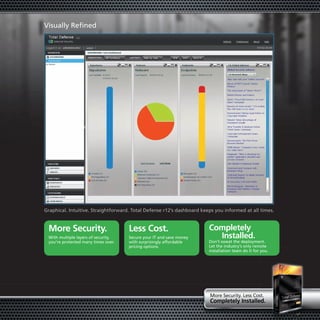
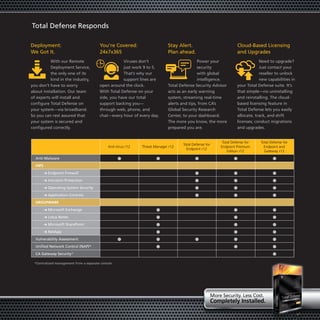
Total Defense r12 is a multi-layered Internet security solution from CA that protects against malware in a visually refined and easy to manage way. It uses multiple layers of security to protect systems many times over at a surprisingly affordable price. Total Defense simplifies security management with an intuitive dashboard and one-click policy deployment while providing 24/7 support and global security intelligence through the Security Advisor.