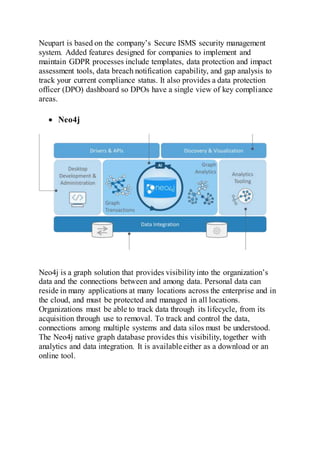
The document discusses and compares several tools that can help companies assess, implement, and maintain compliance with the General Data Protection Regulation (GDPR). It describes GDPR assessment tools that can identify personal data, conduct risk assessments, and evaluate third parties. It also outlines implementation tools that can help with consent management, data governance, protection and auditing. Finally it discusses maintenance tools that can track personal data changes, automate privacy tasks, and aid with data deletion requests.