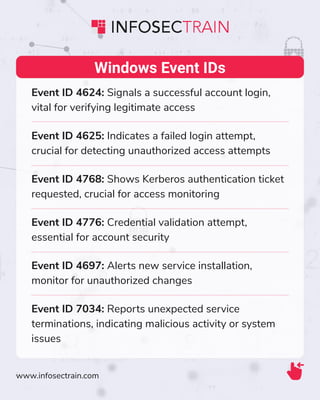
The document lists essential event IDs for monitoring and securing various systems, including Windows, Linux/Unix, network devices, SIEM, web servers, and database servers. Key events, such as successful logins, failed login attempts, and service terminations, are highlighted for their importance in detecting unauthorized access and maintaining system integrity. The information is aimed at enhancing security operations through better awareness and monitoring practices.