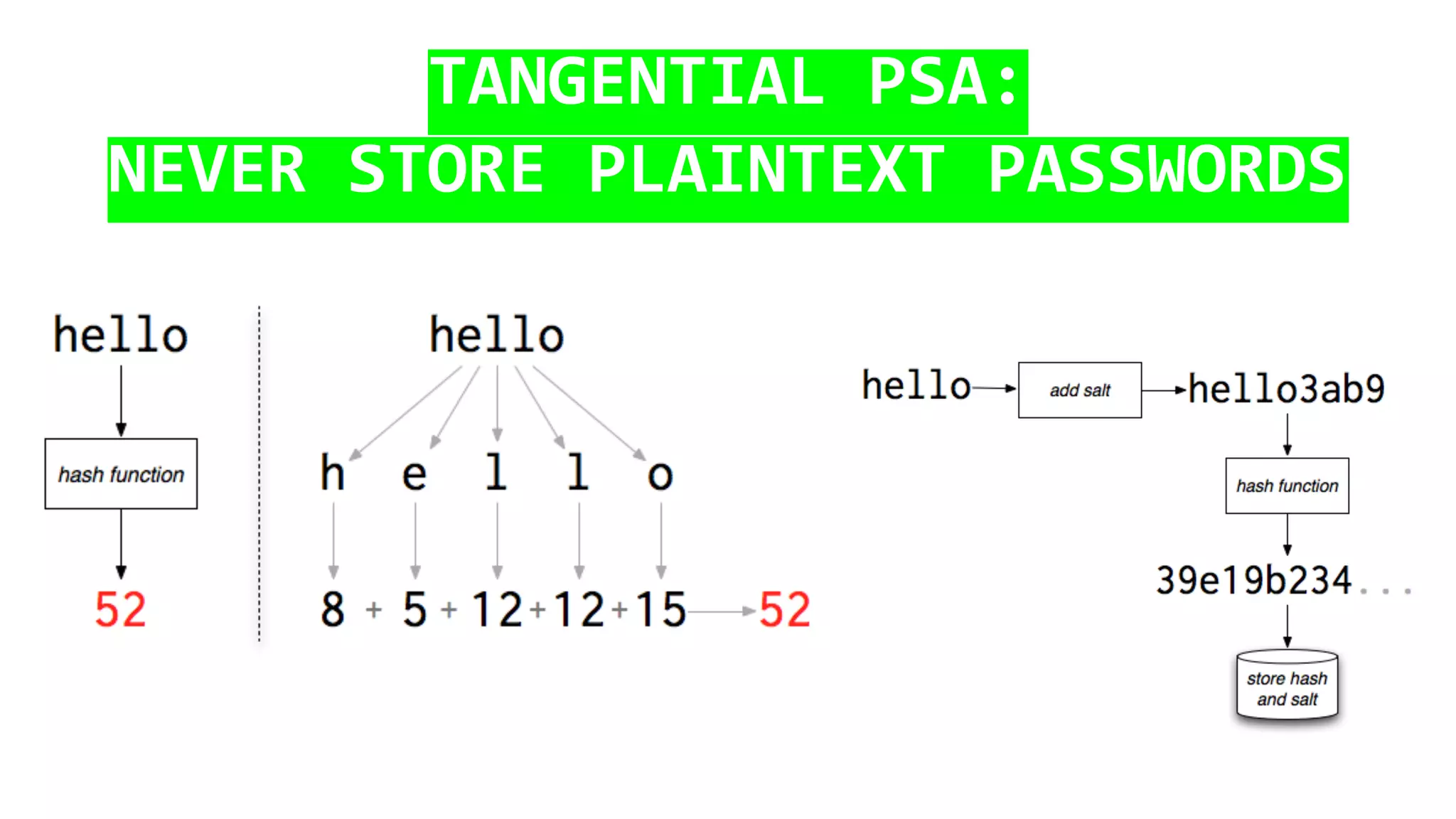
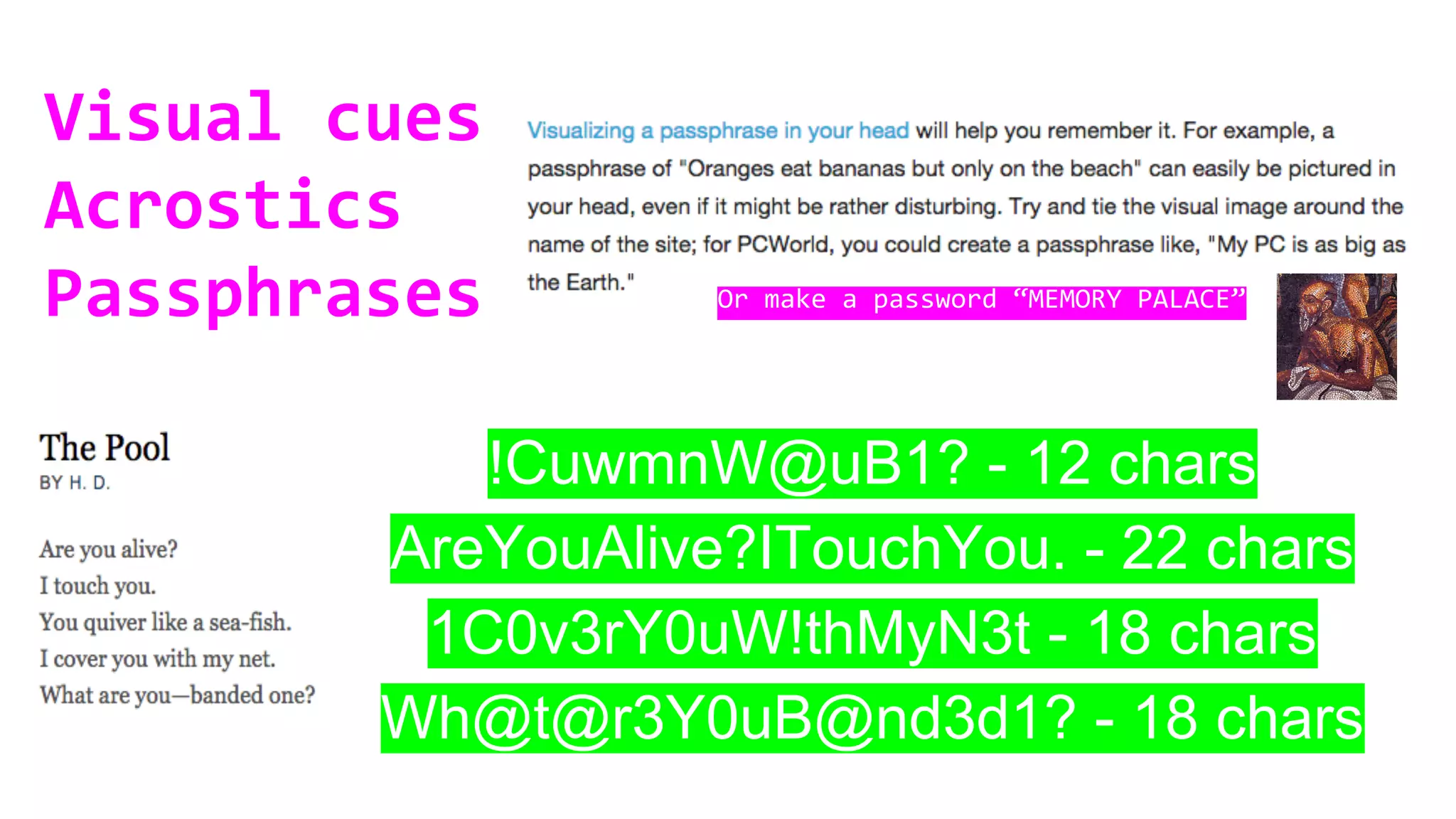
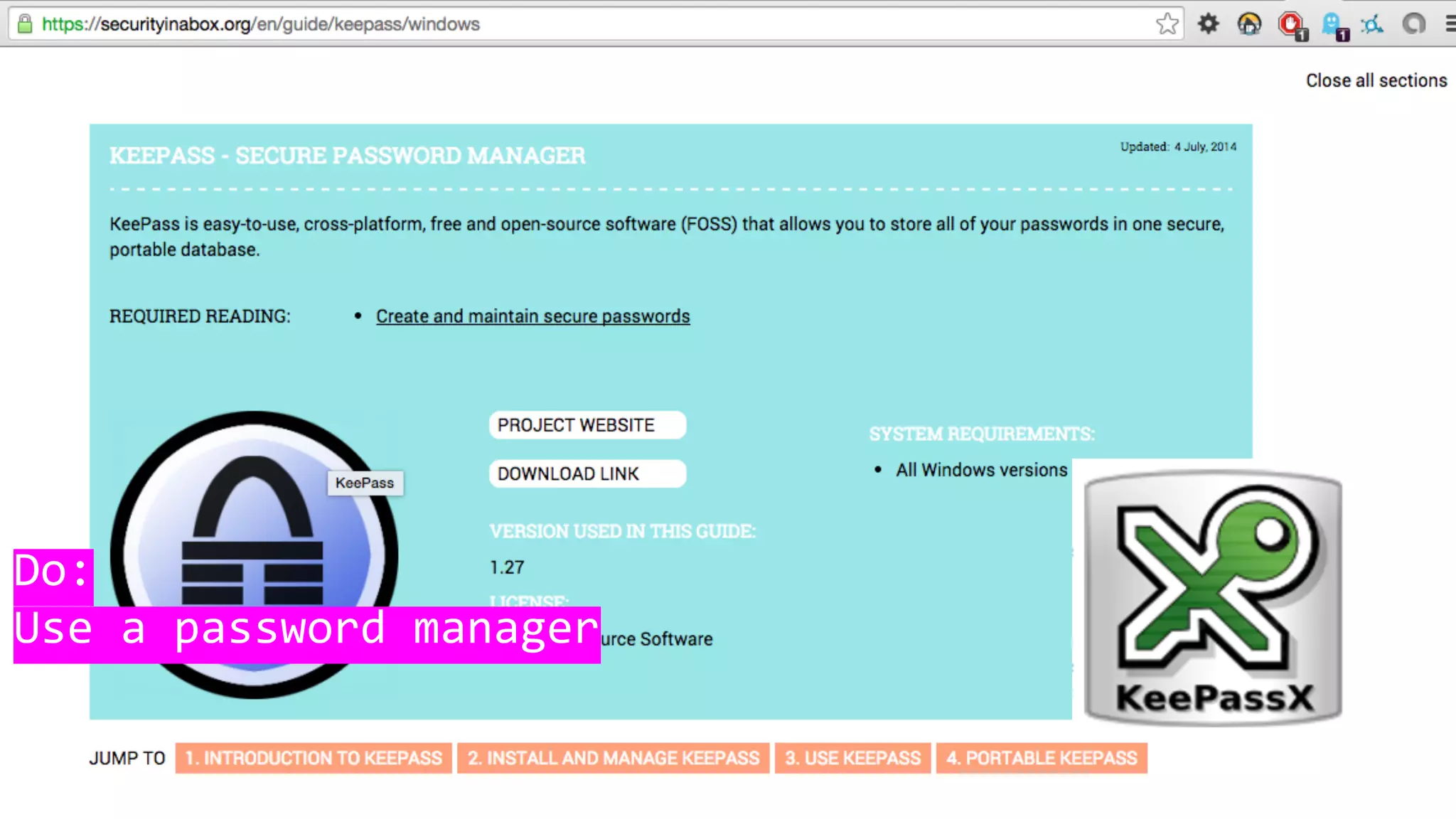
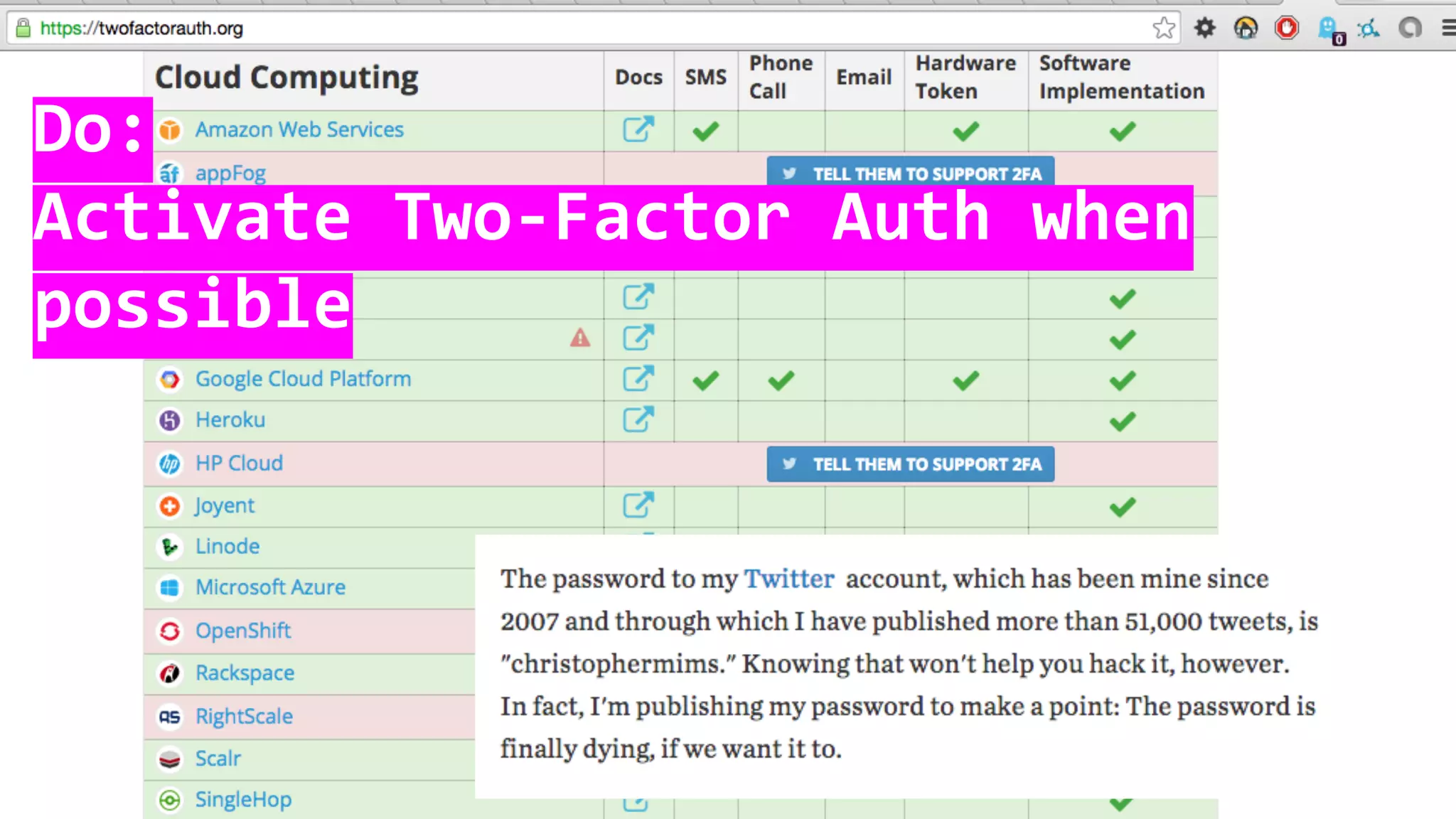
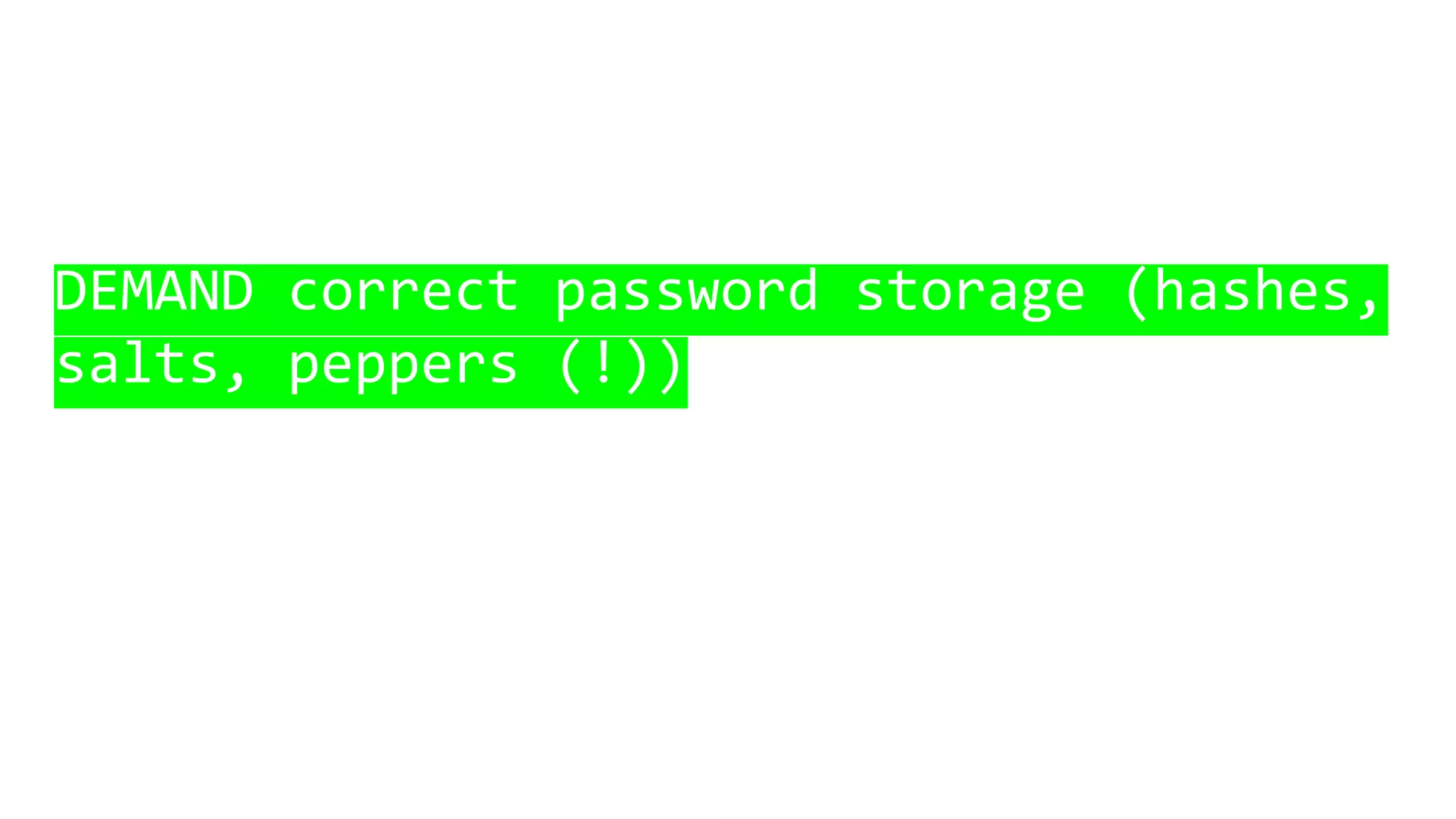
This document discusses password security and remote cloud storage options. It begins with a brief history of passwords and how they unlock interfaces. It then provides tips for choosing strong passwords and using password managers. The document also discusses demanding encryption and knowing what data companies store from users. Several open source cloud storage case studies are presented as alternatives to corporate cloud services, such as Tahoe-LAFS, Freedom Box, Occupy Here, Guifi.net, and Urbit. The future of storage is discussed as moving away from remote cloud models towards more distributed and user-controlled options.