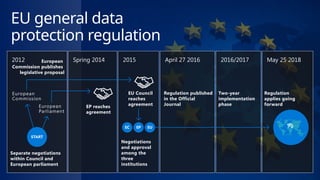
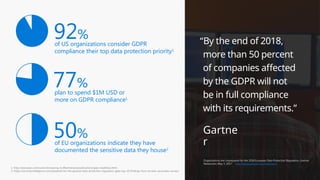
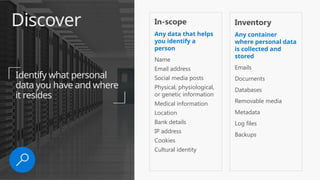
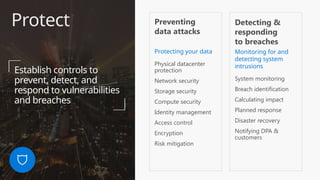
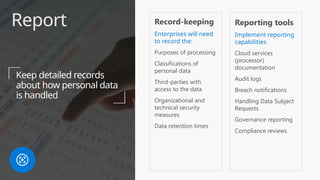
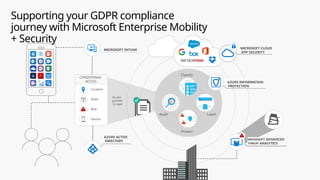
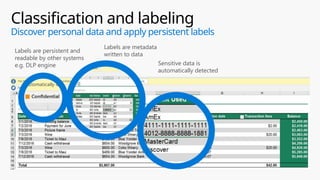
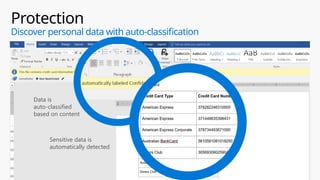
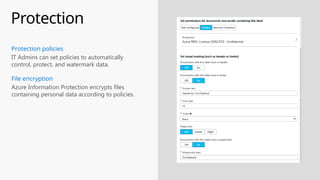
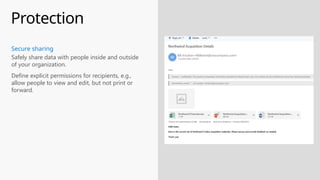
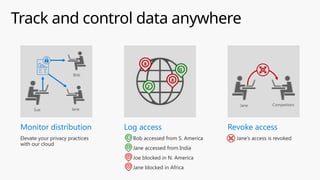
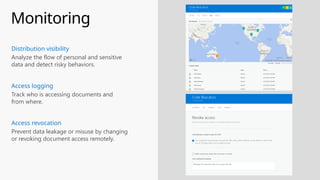
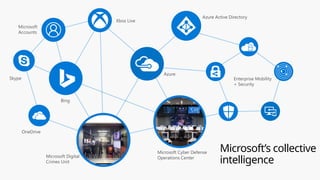
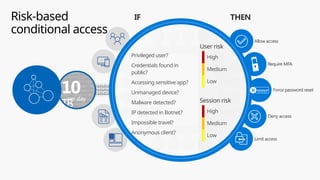
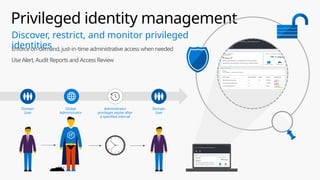
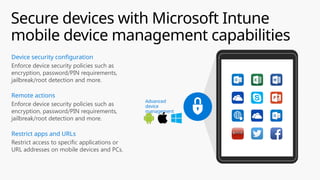
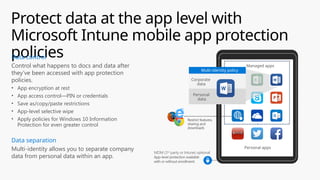
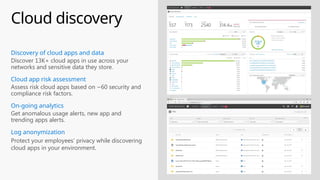
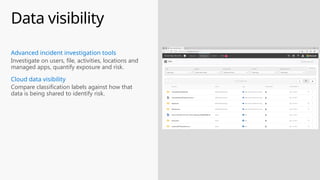
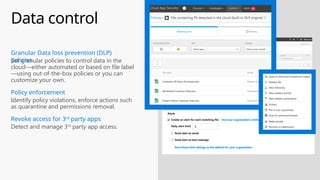
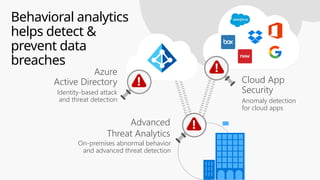
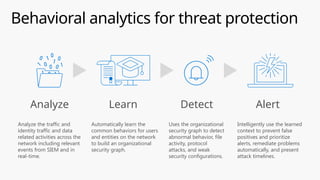
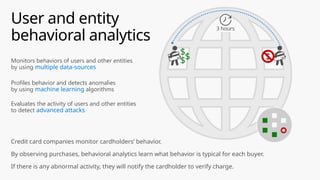
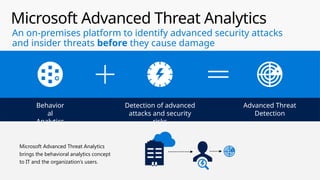
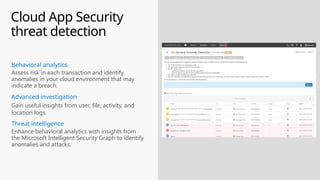
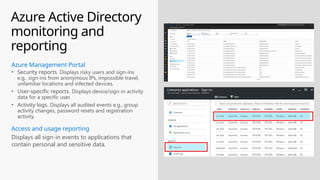
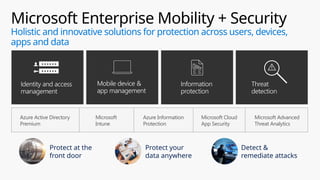
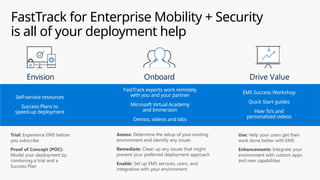
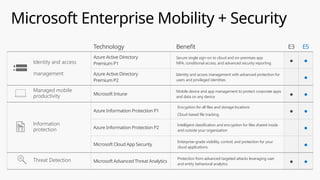
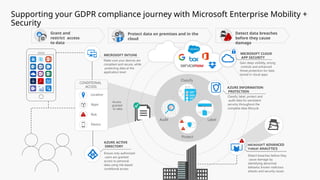
This document provides an overview of the General Data Protection Regulation (GDPR) and highlights how Microsoft's Enterprise Mobility + Security can assist organizations in achieving compliance. It outlines the key changes GDPR demands, including enhanced personal privacy rights, data protection responsibilities, and mandatory breach reporting, with significant penalties for non-compliance. Additionally, the document details steps organizations must take to manage personal data and outlines Microsoft's commitment to providing a compliant cloud solution for managing personal data effectively.