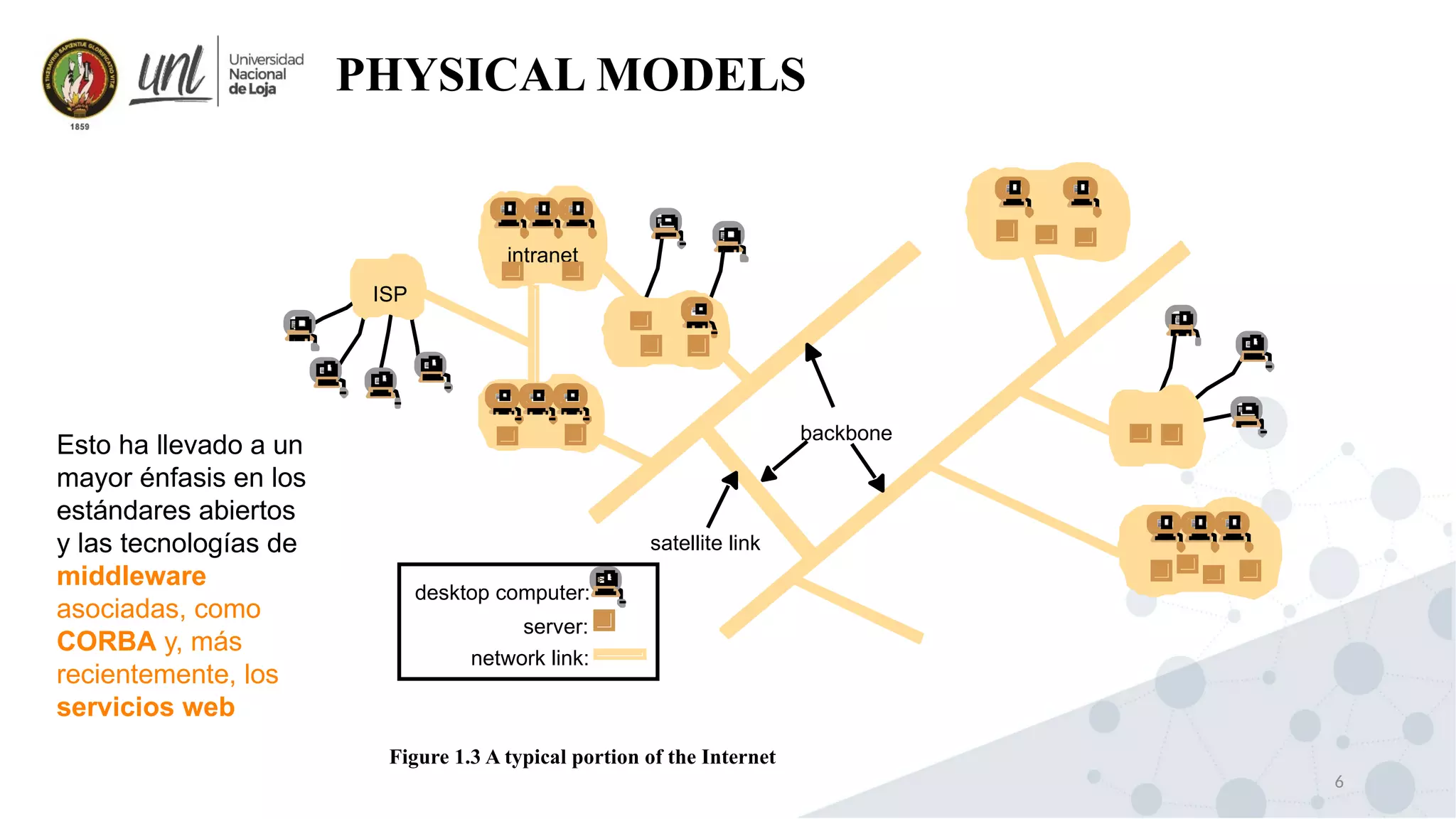
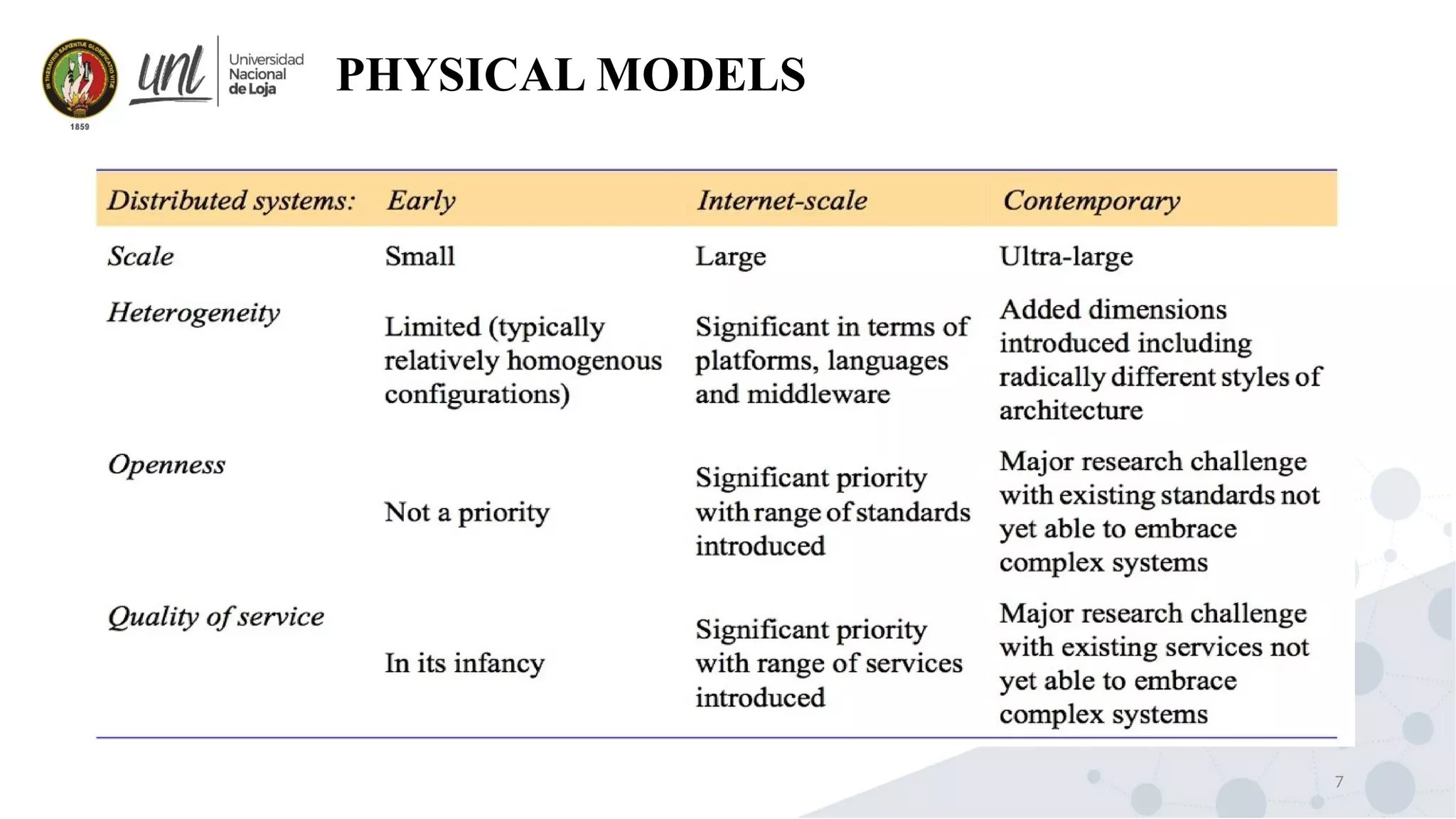
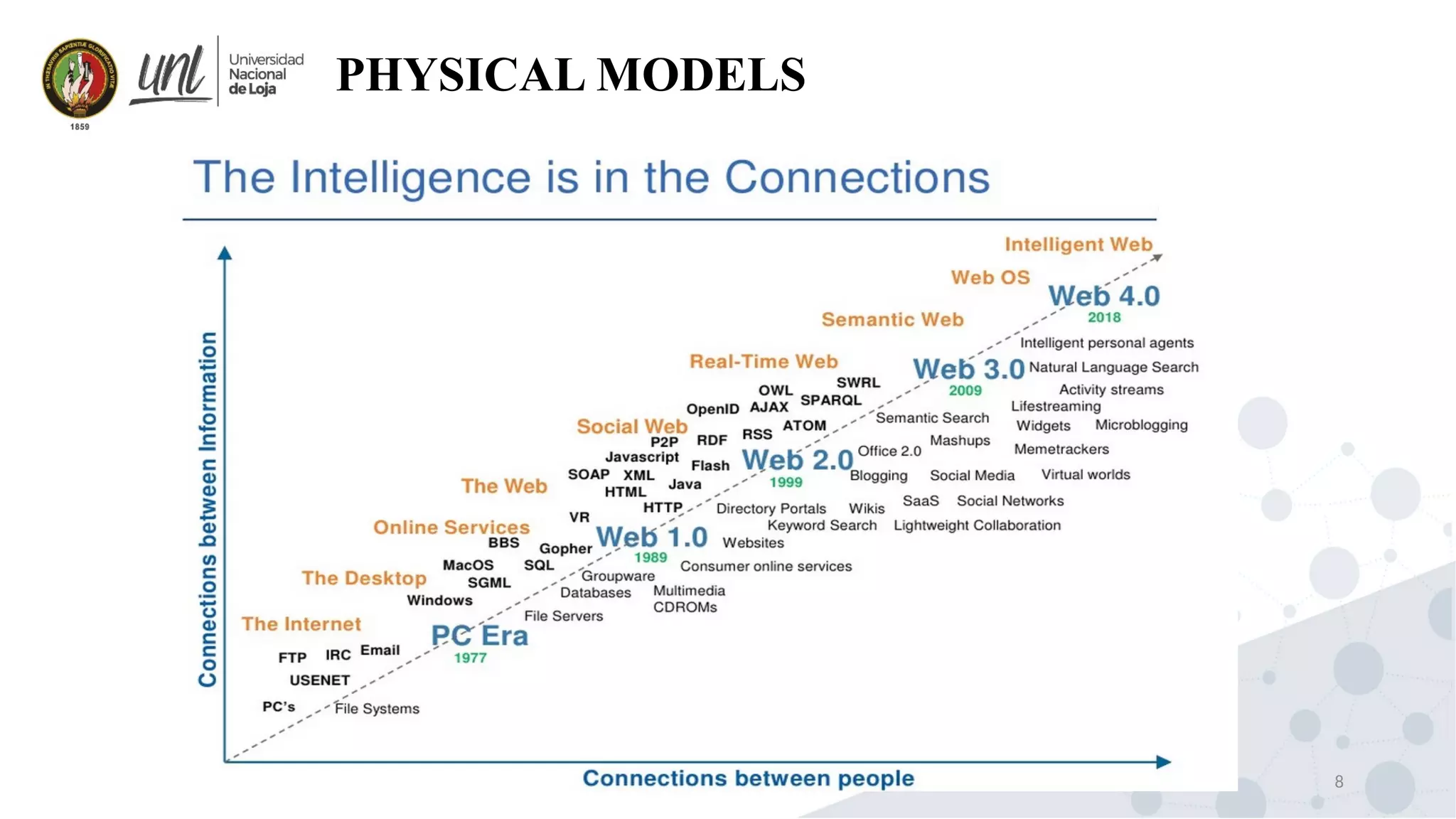
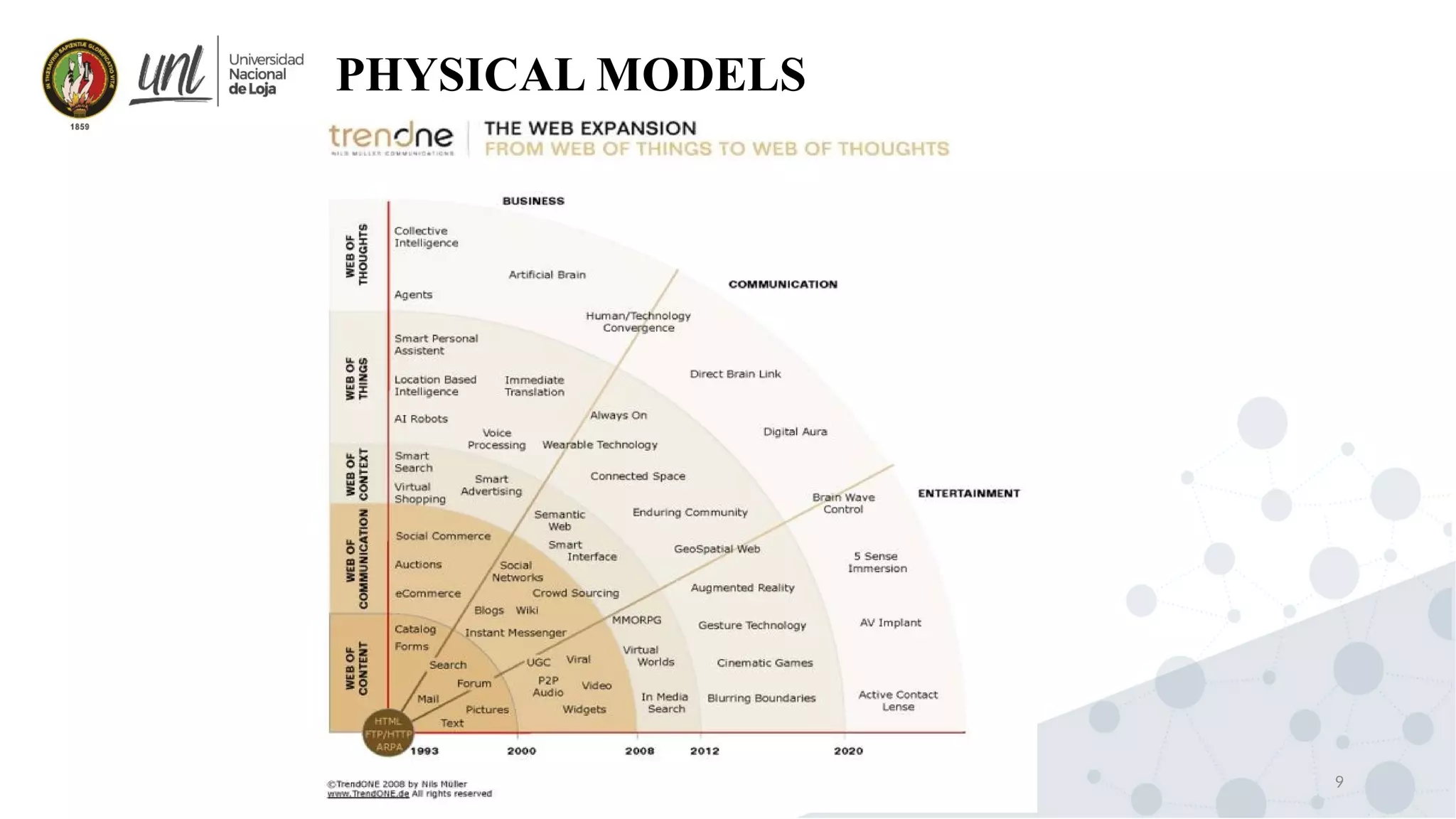
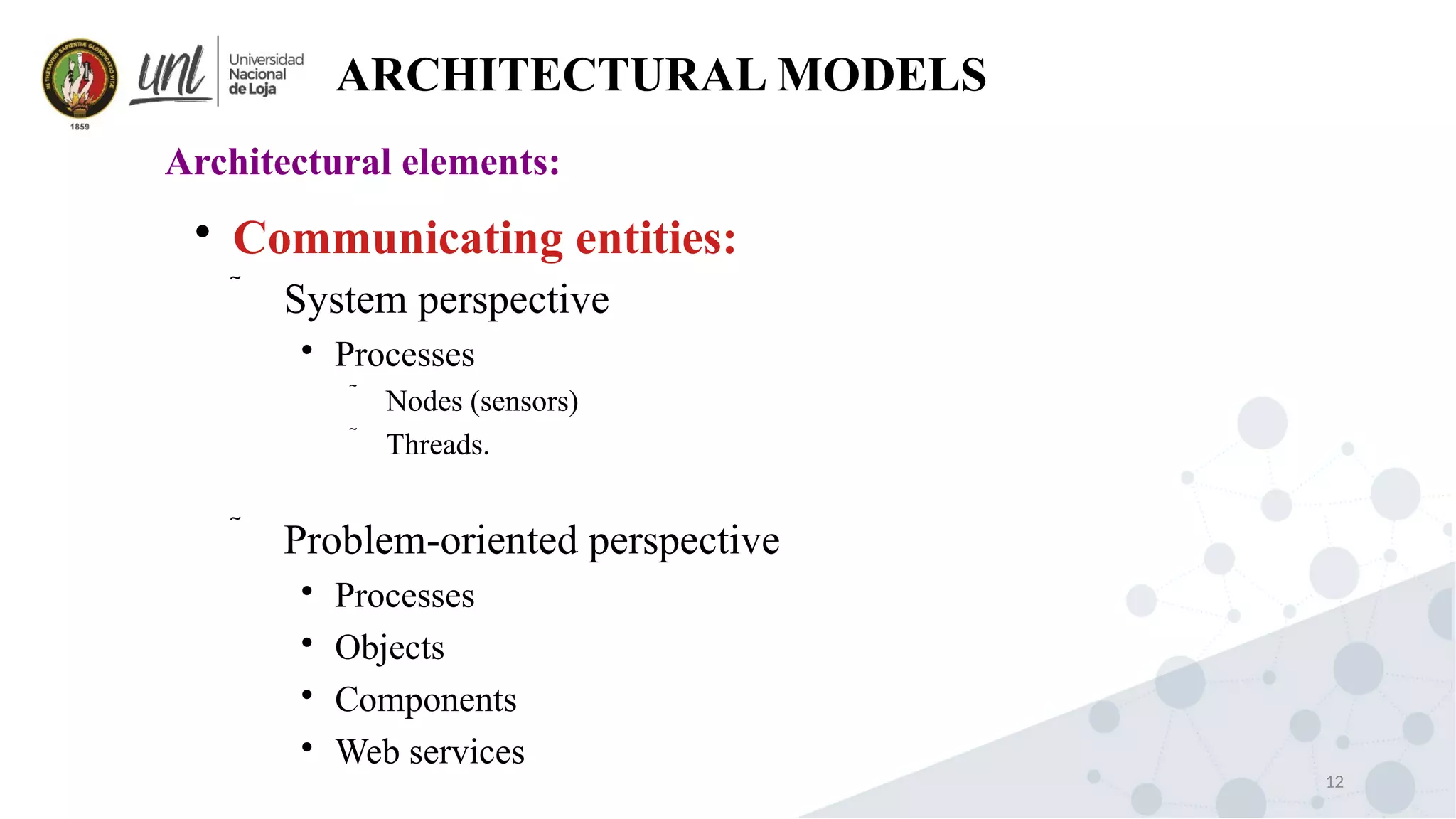
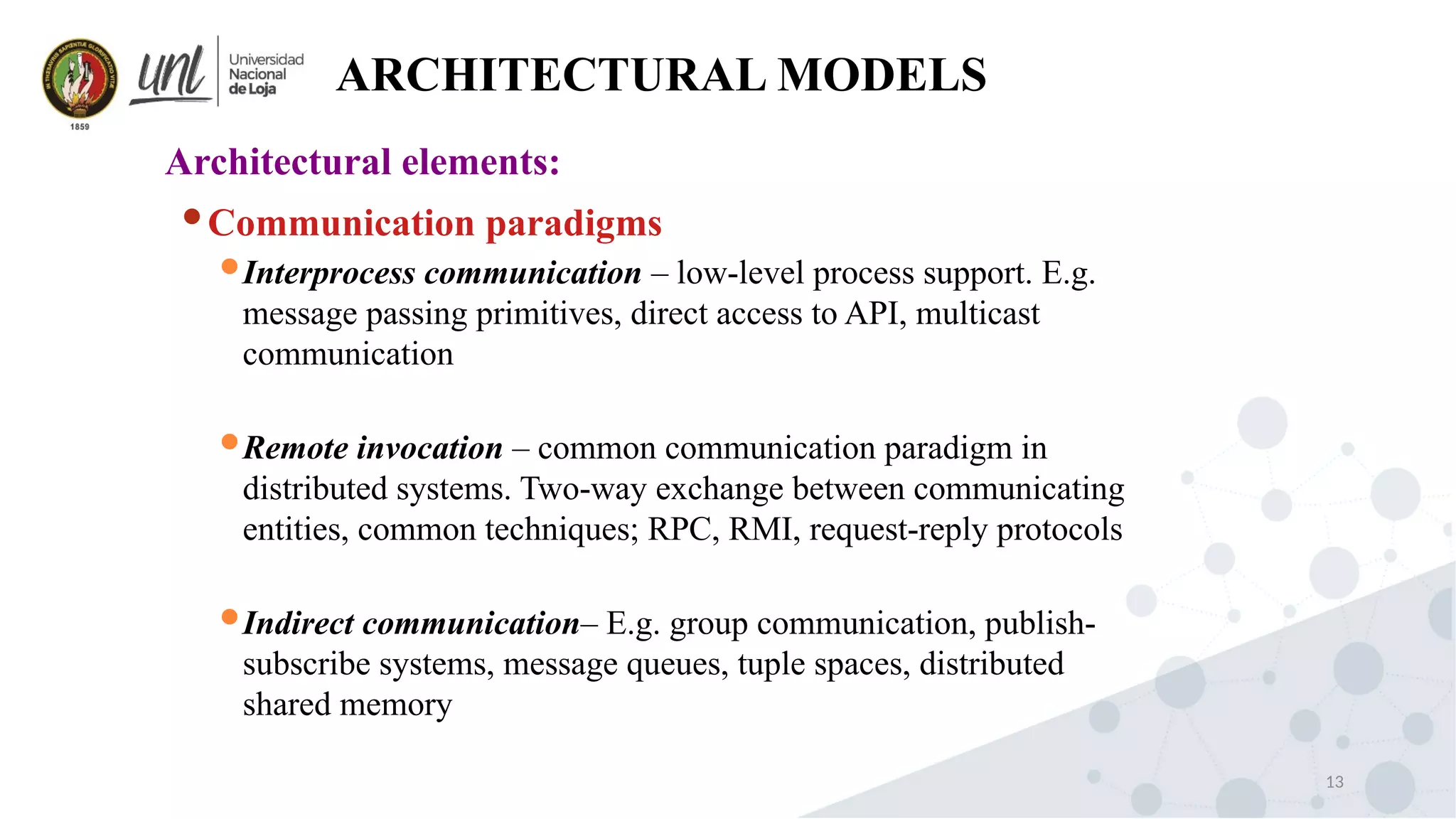
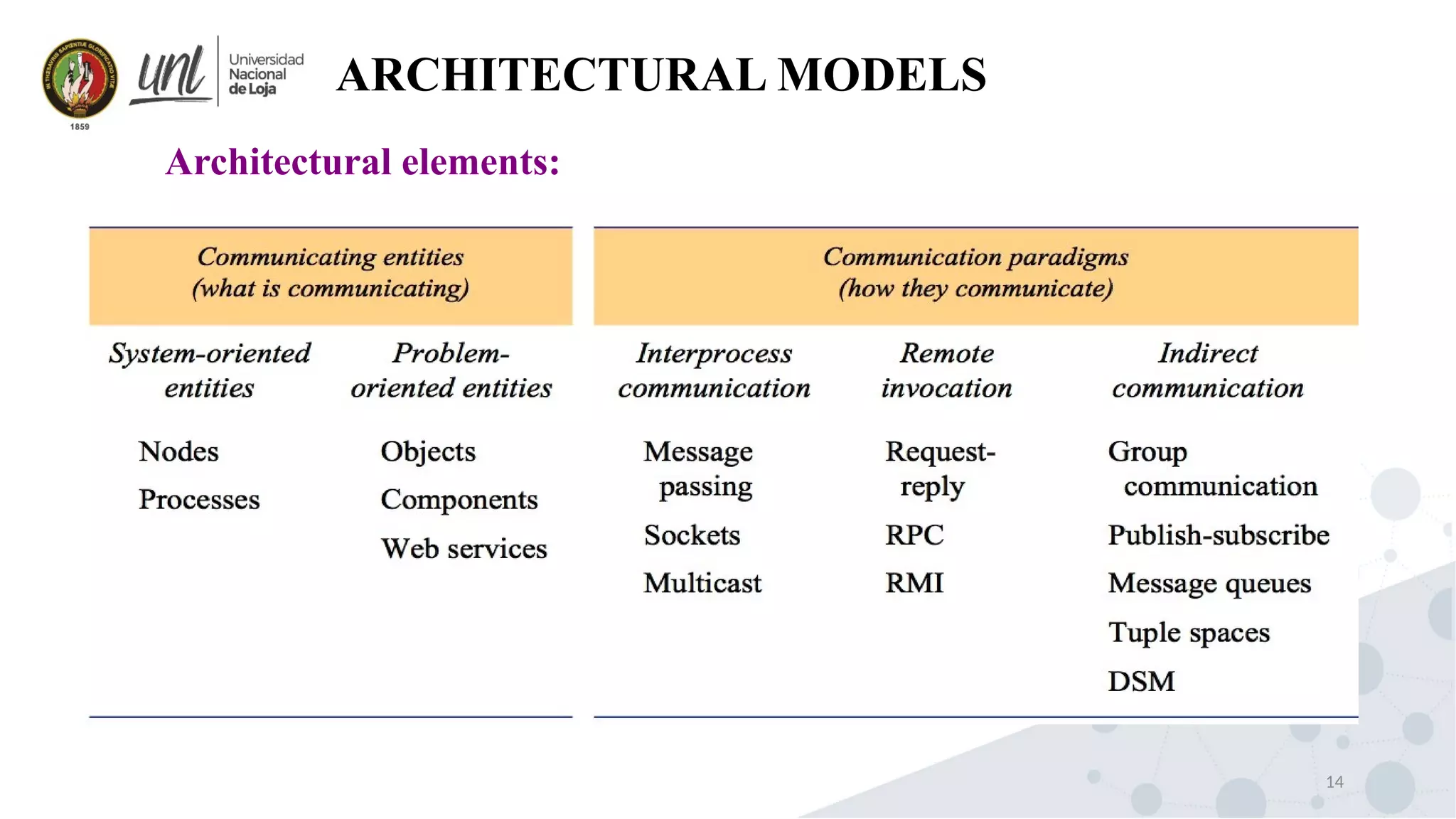
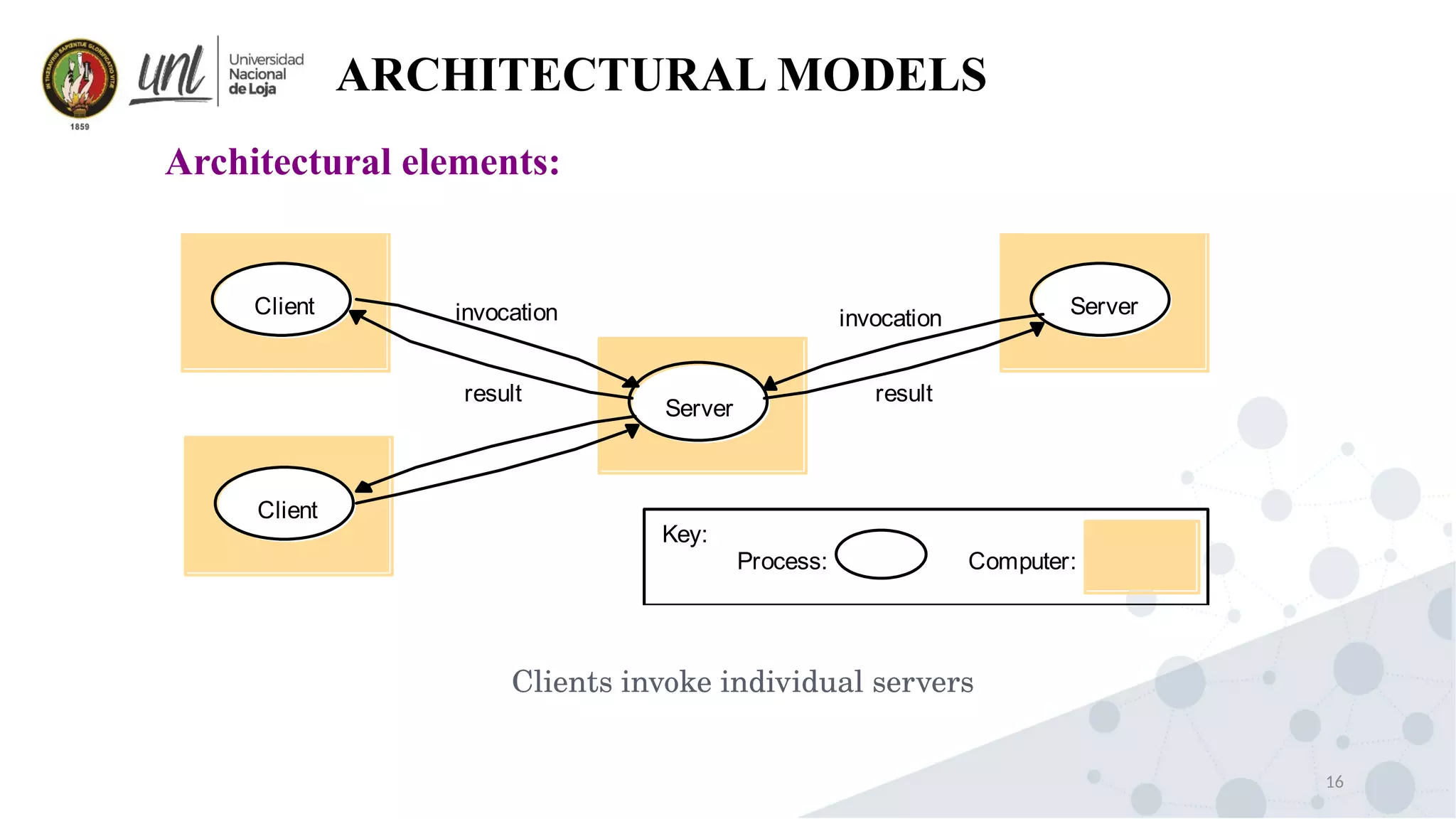
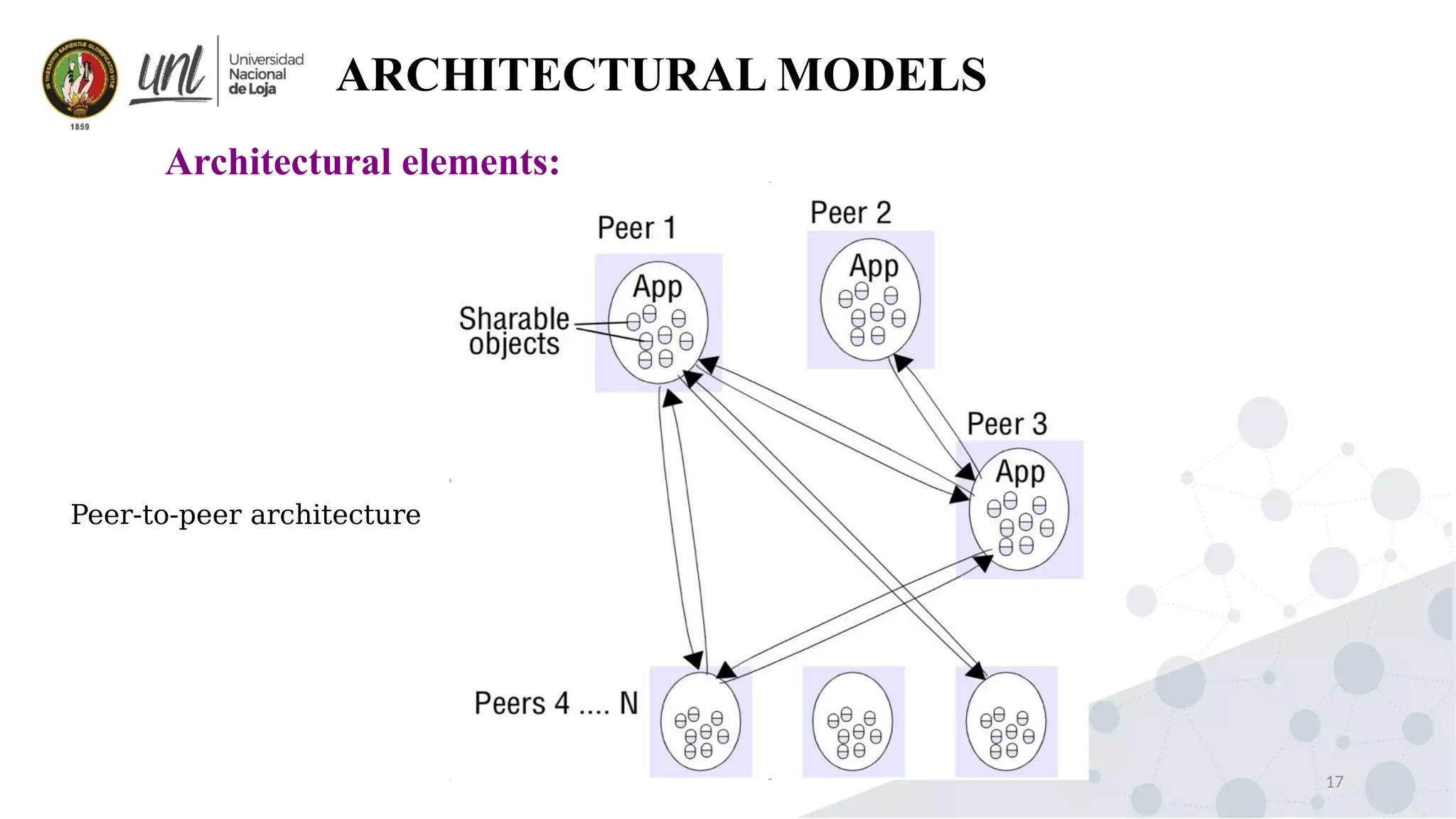
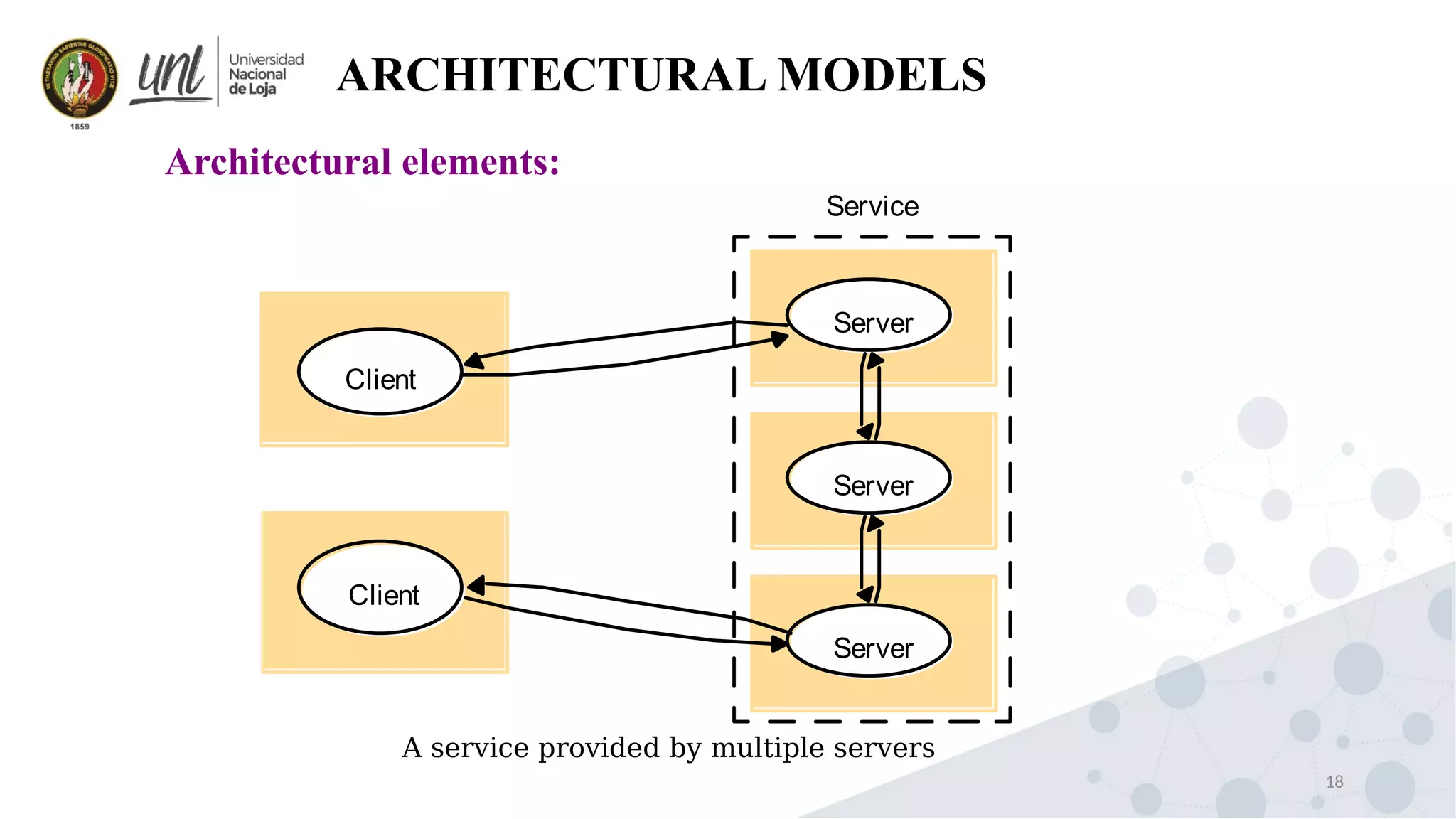
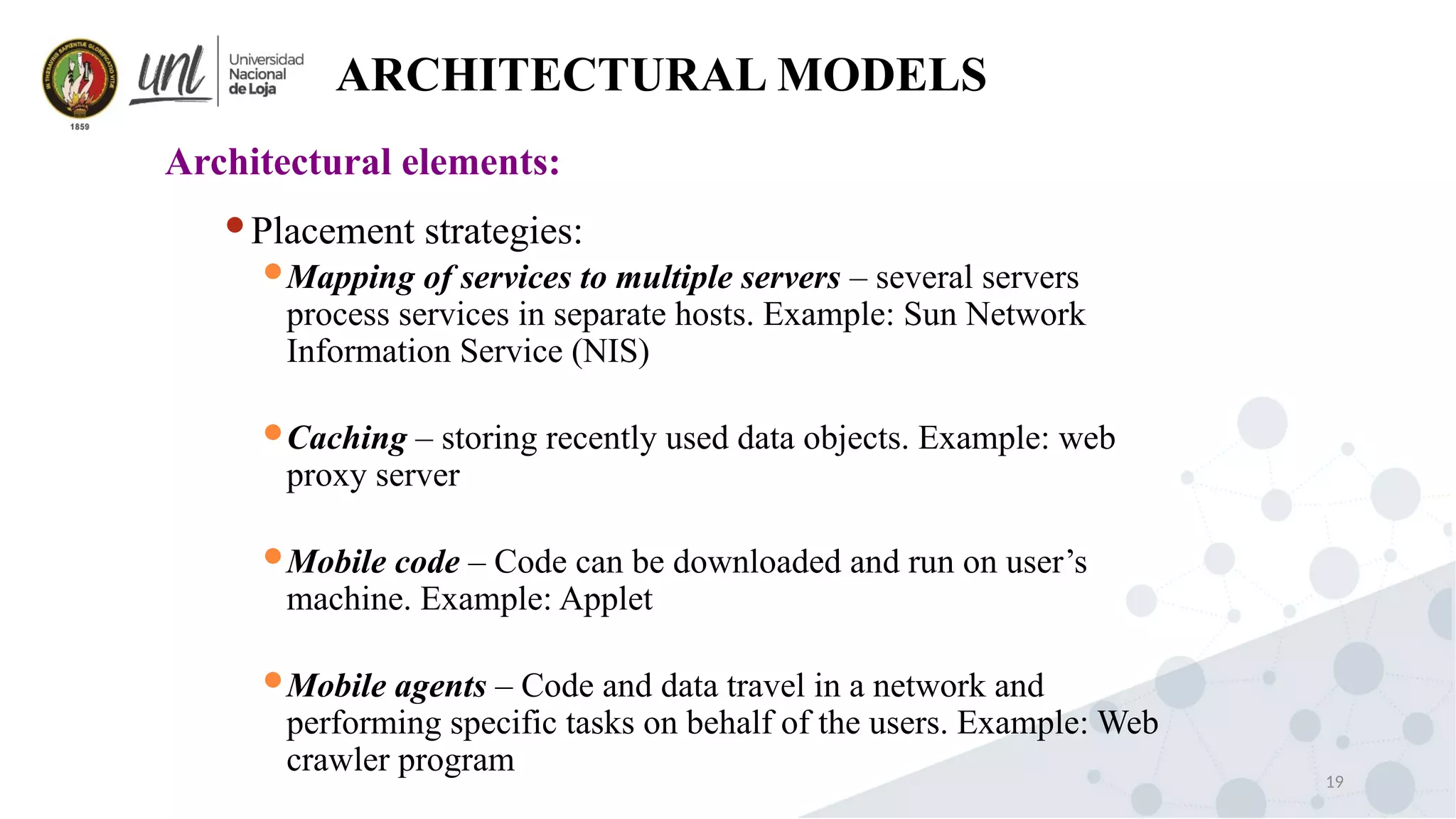
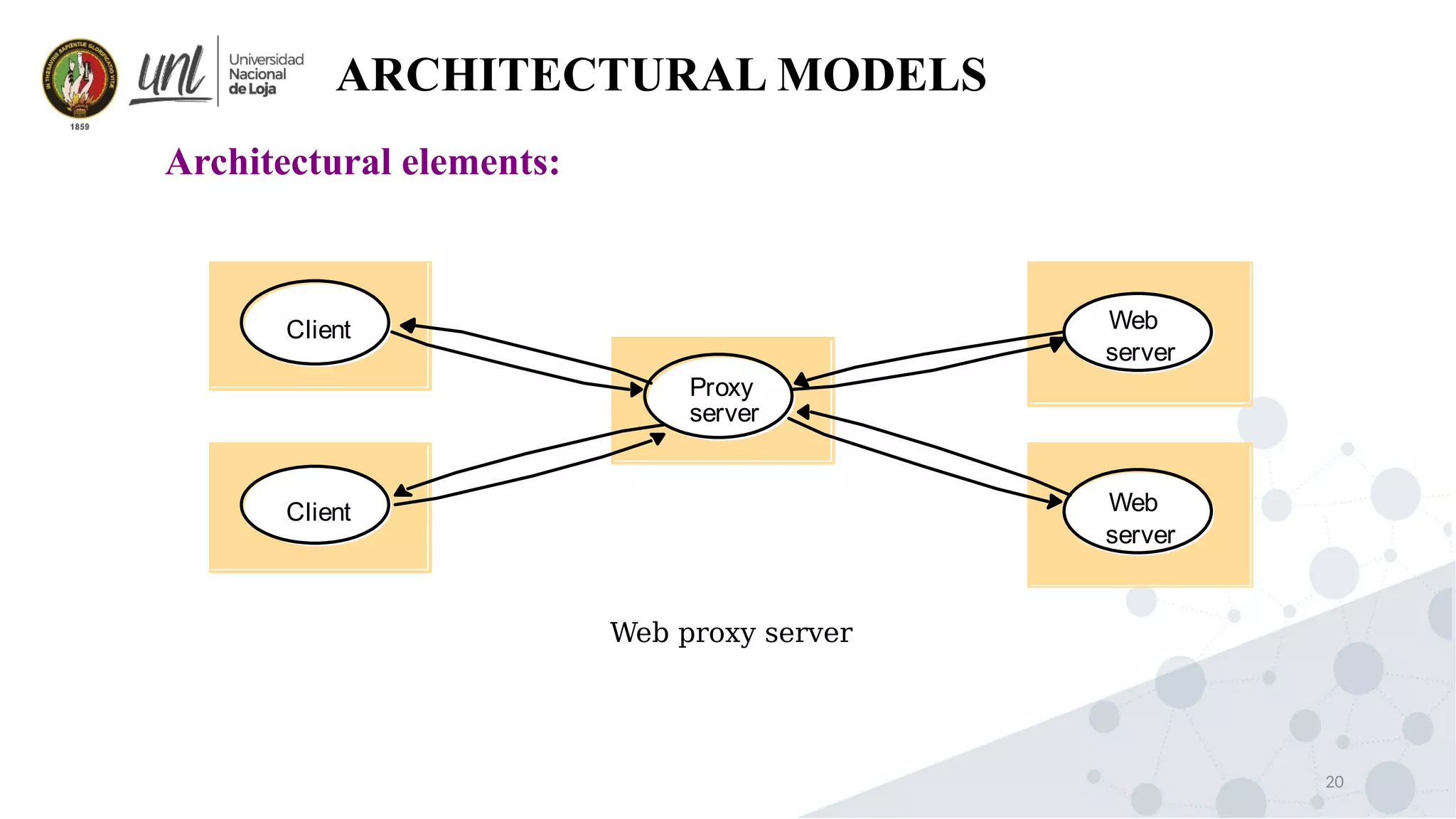
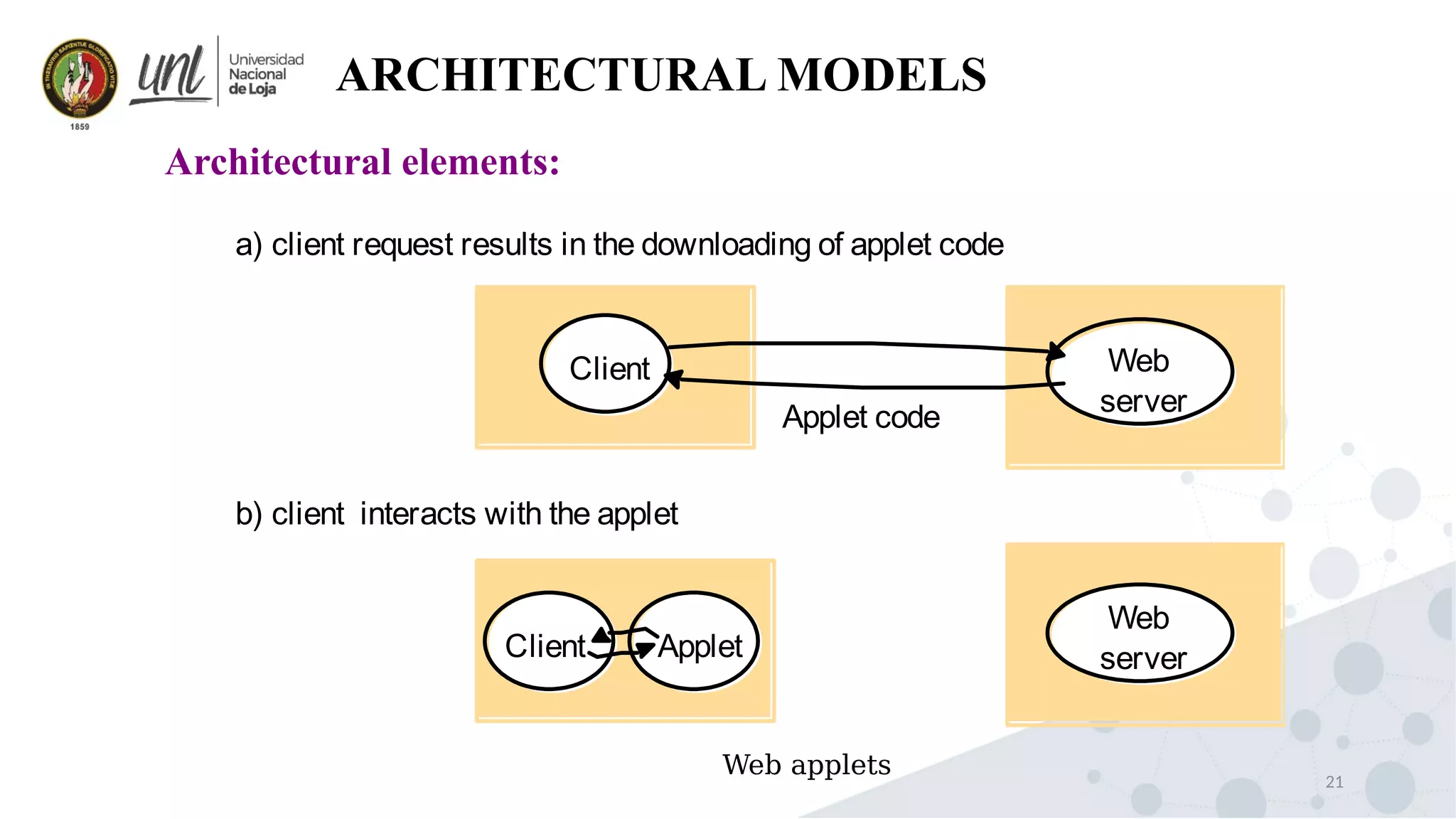
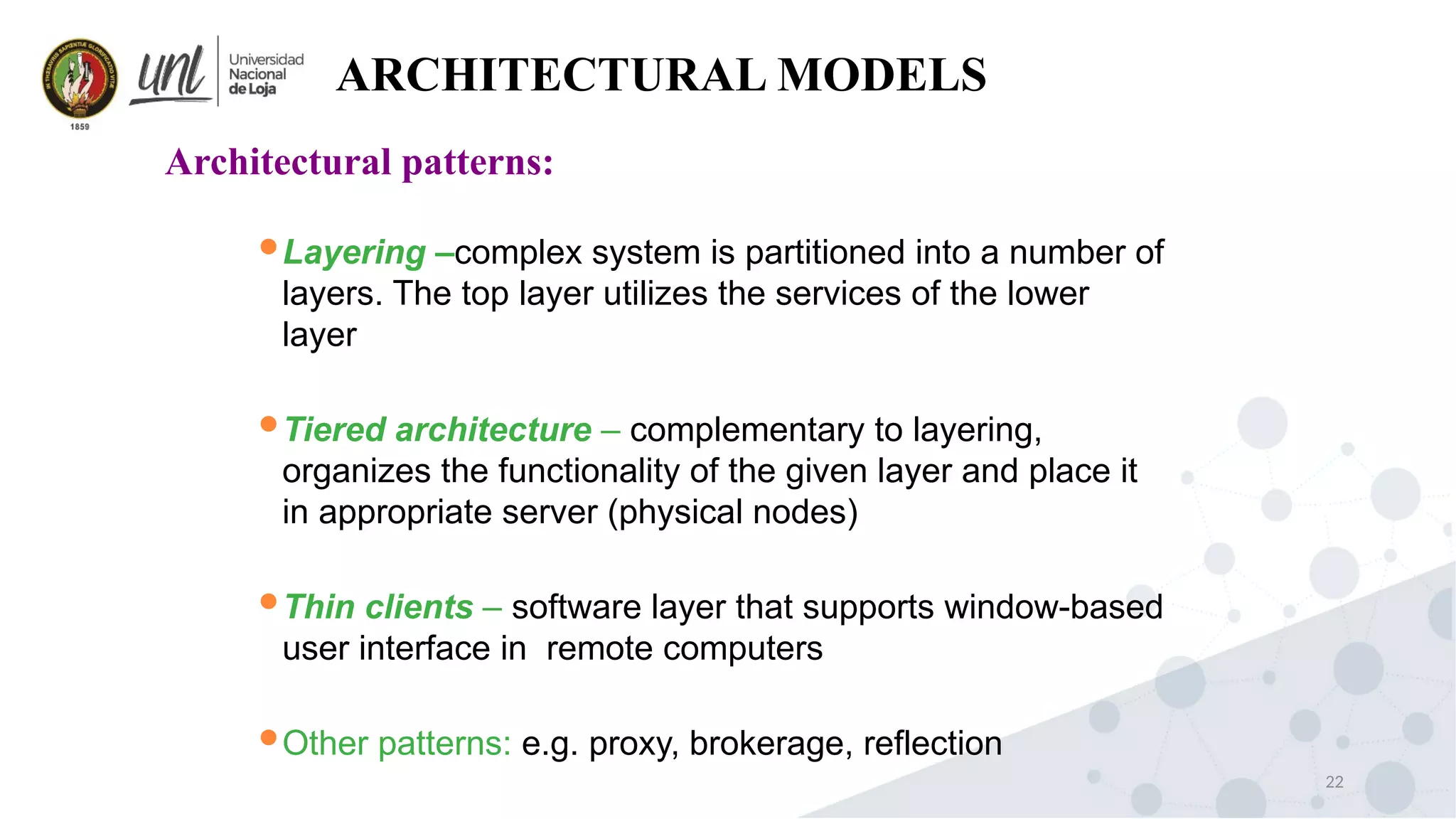
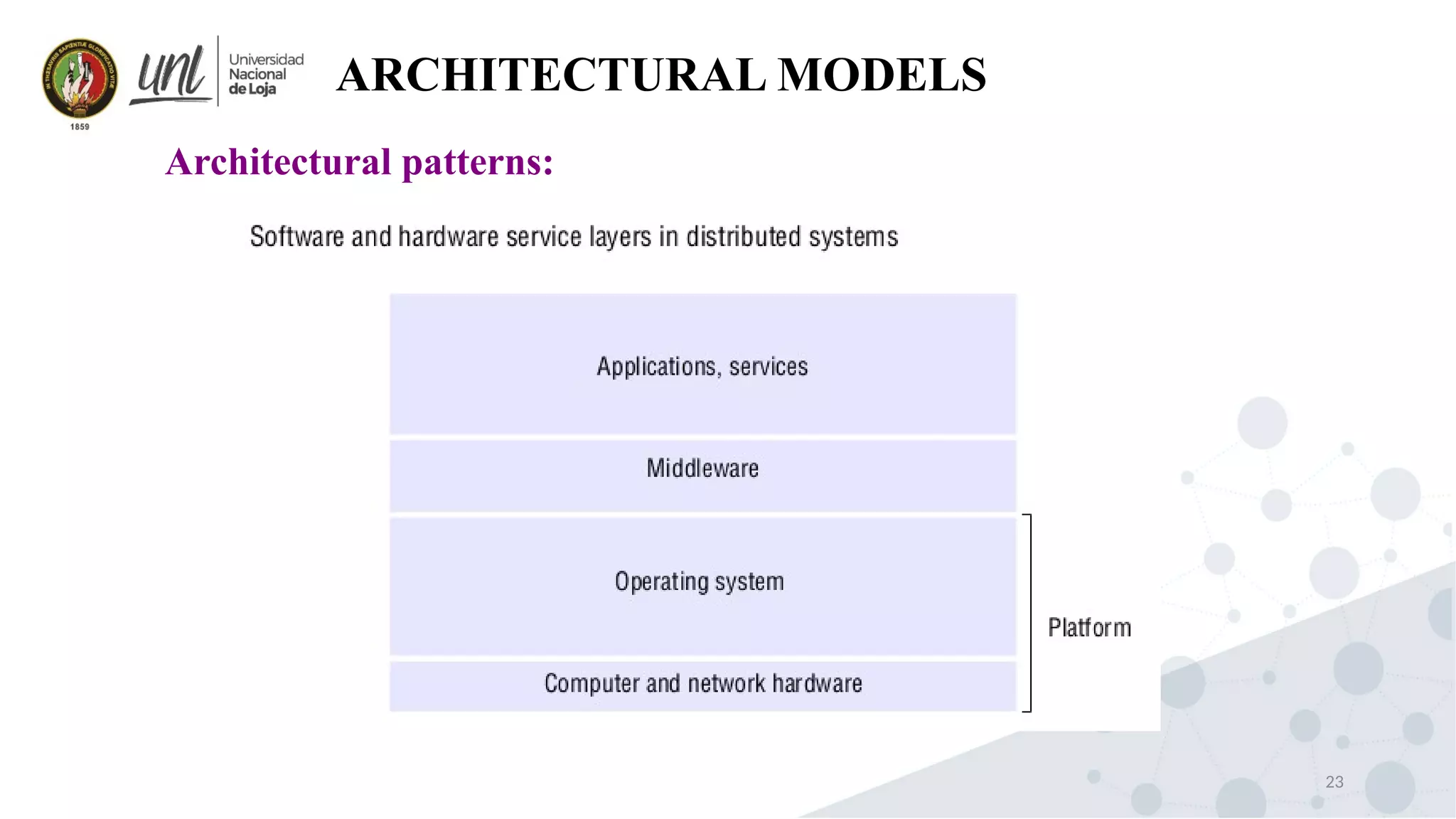
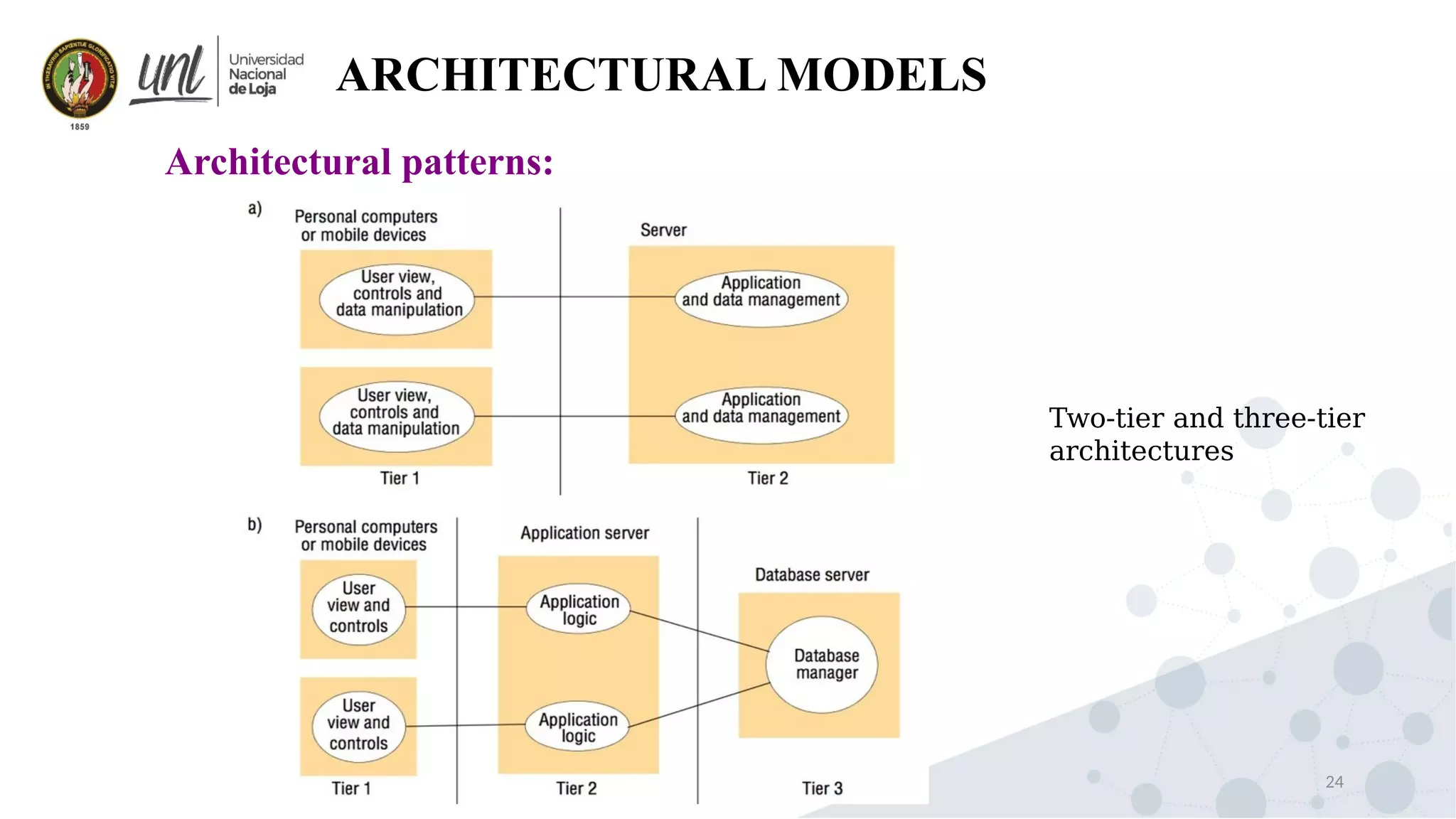
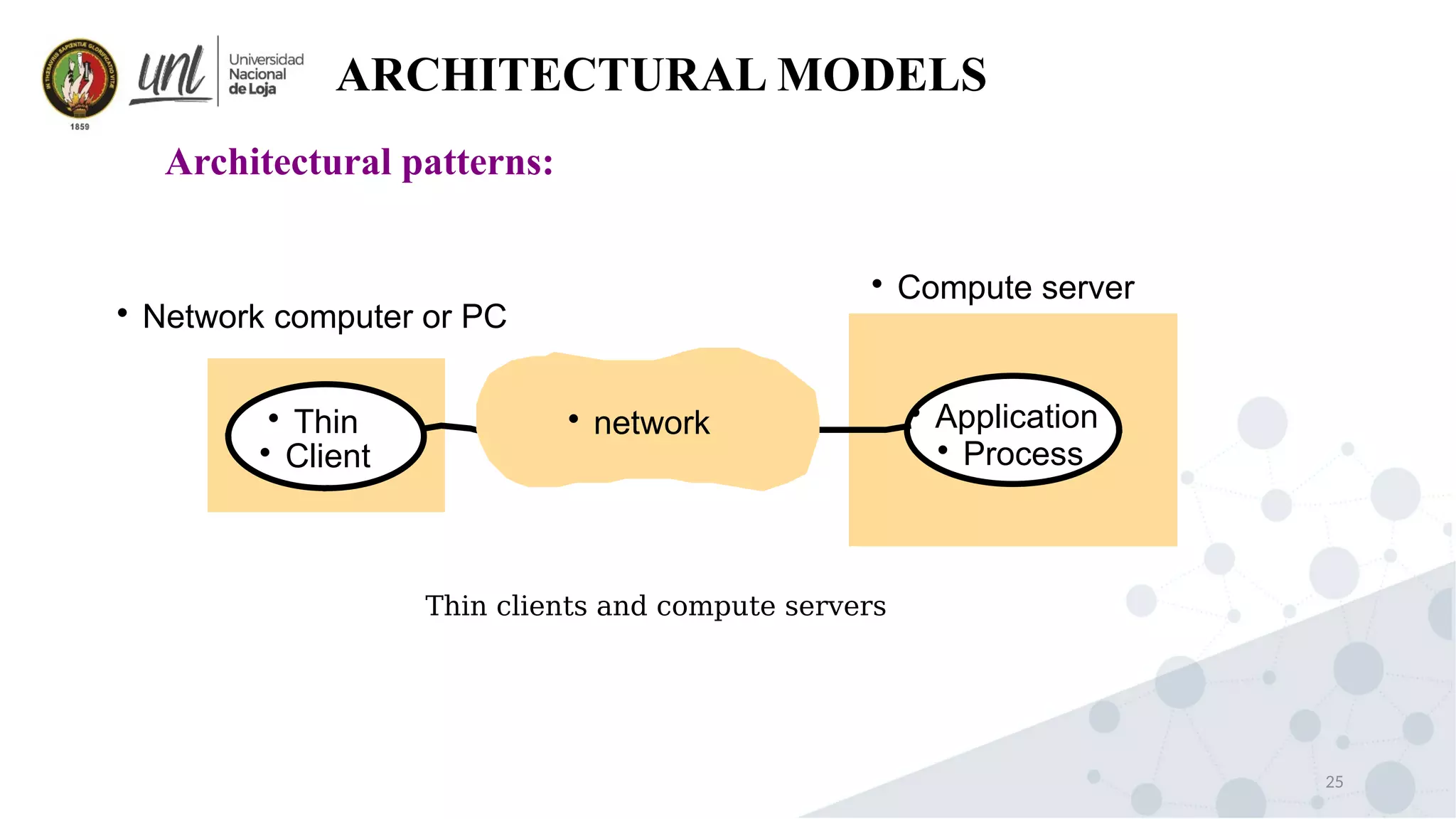
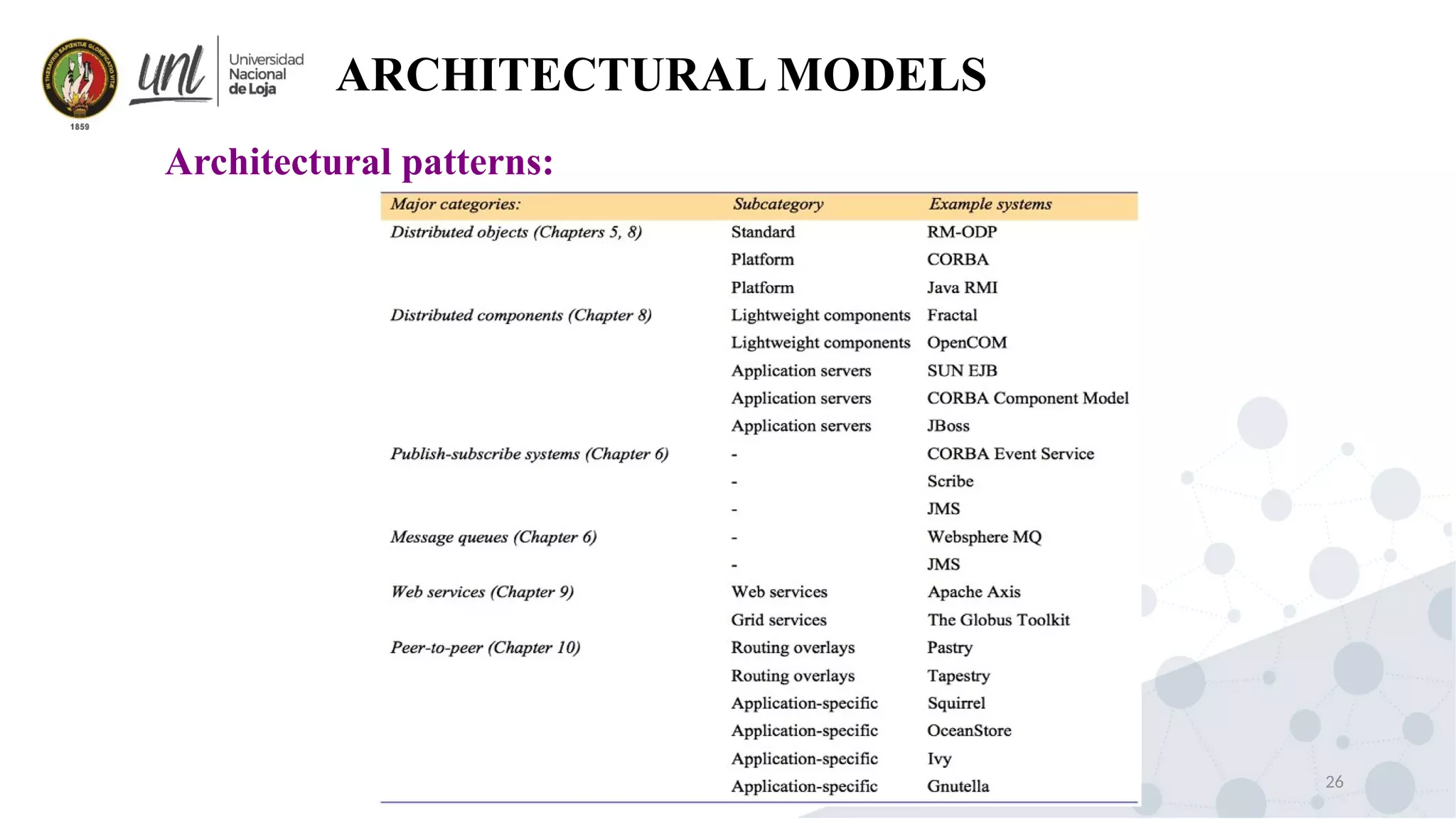
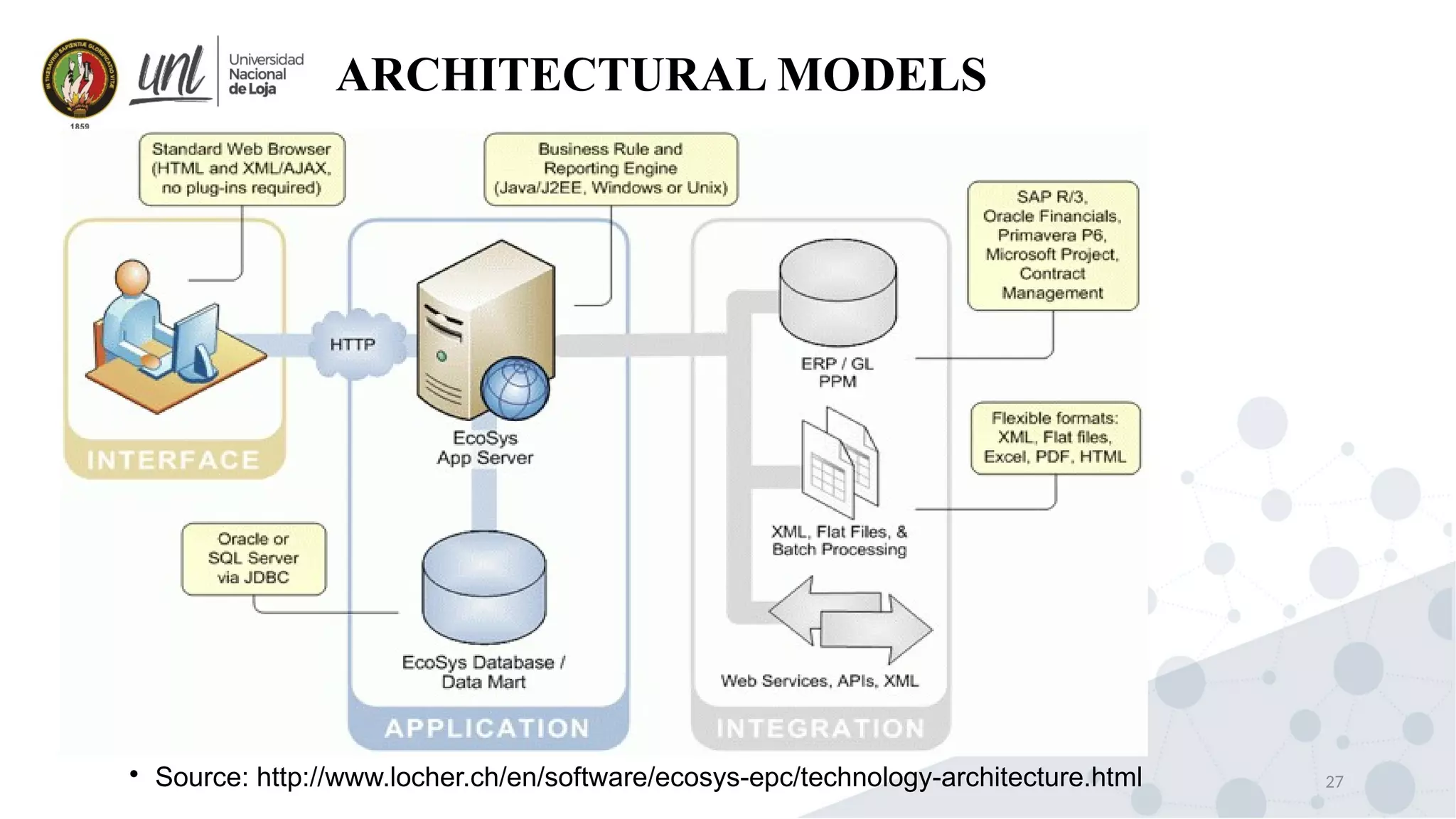
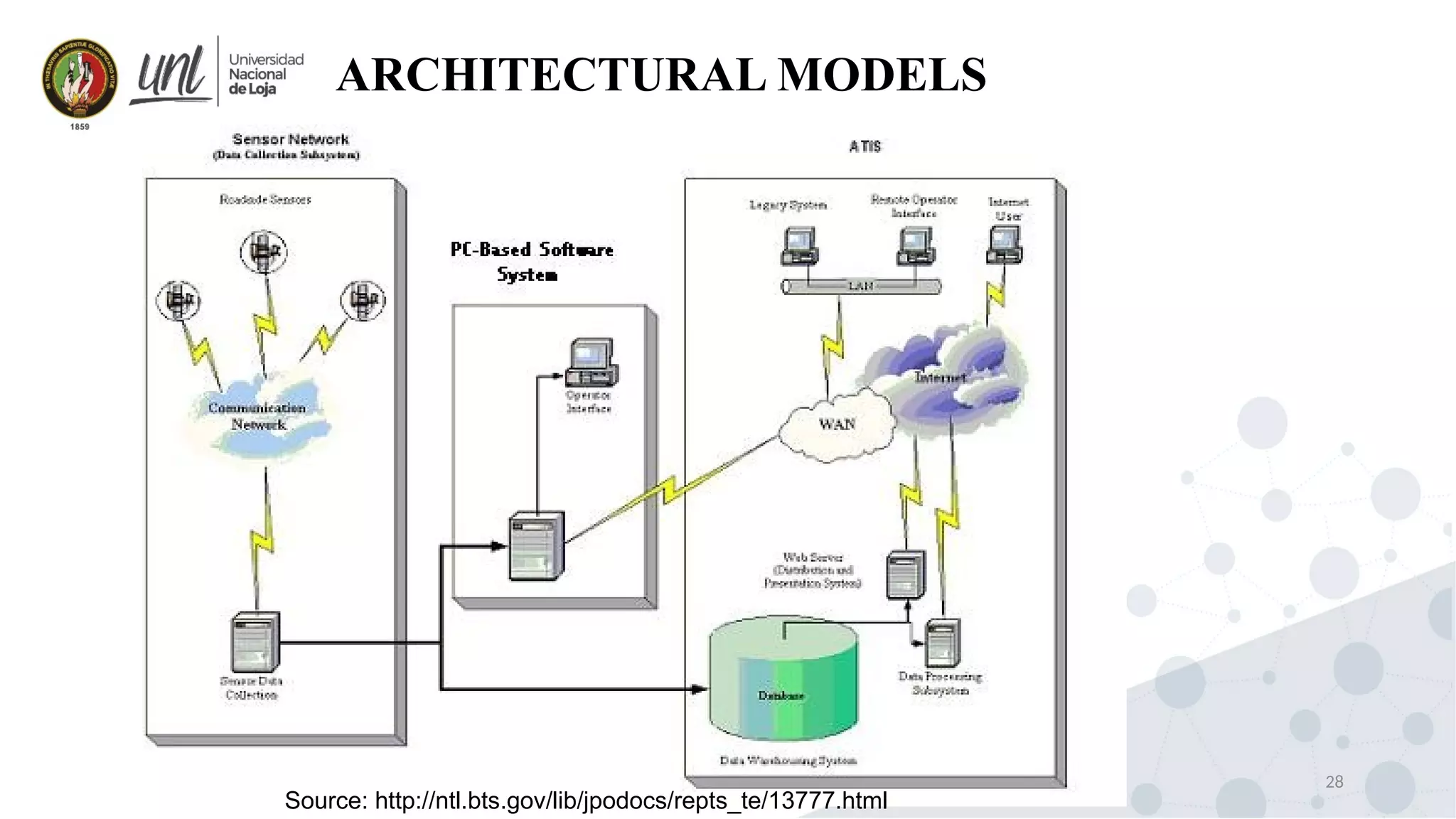
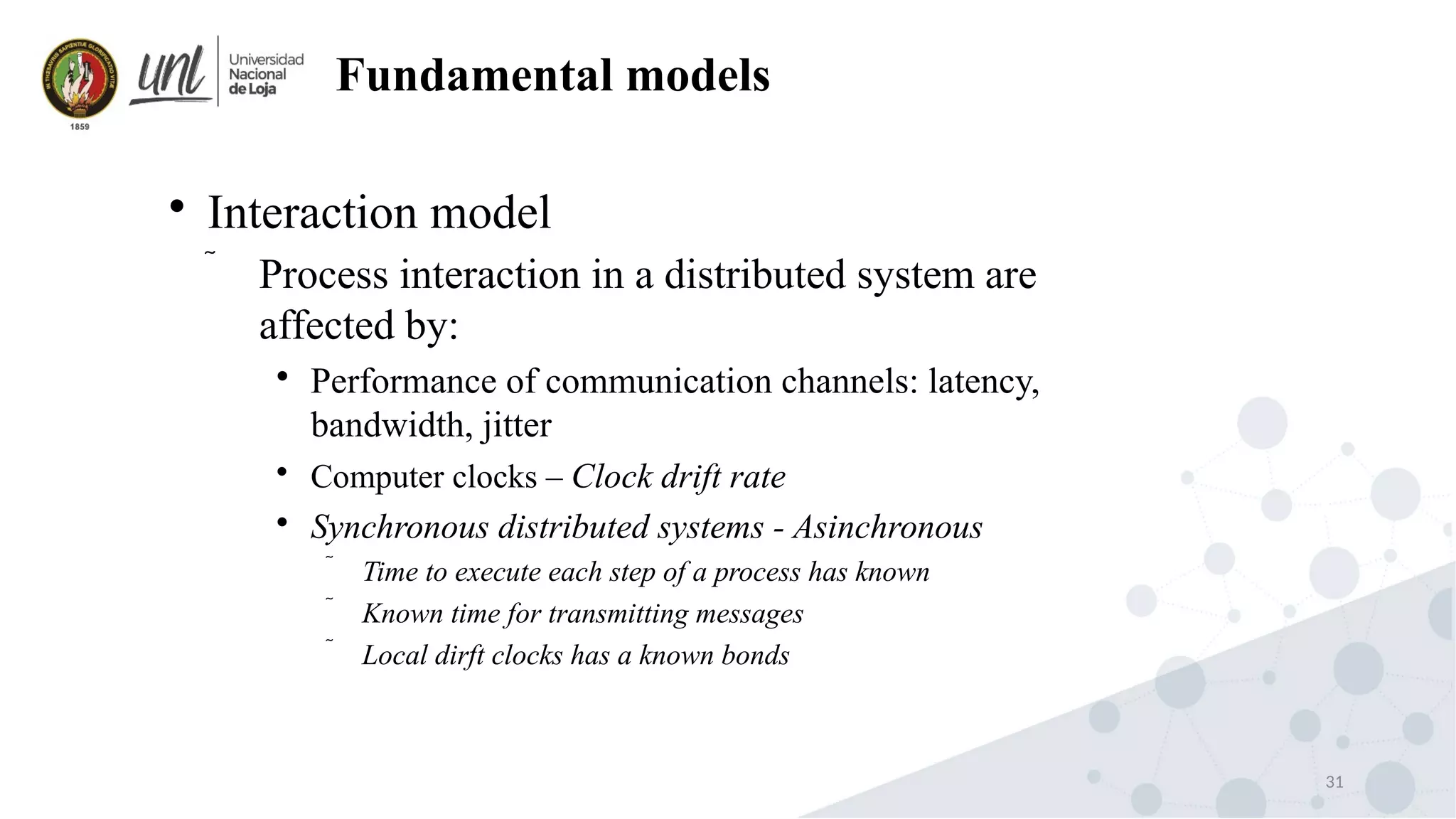
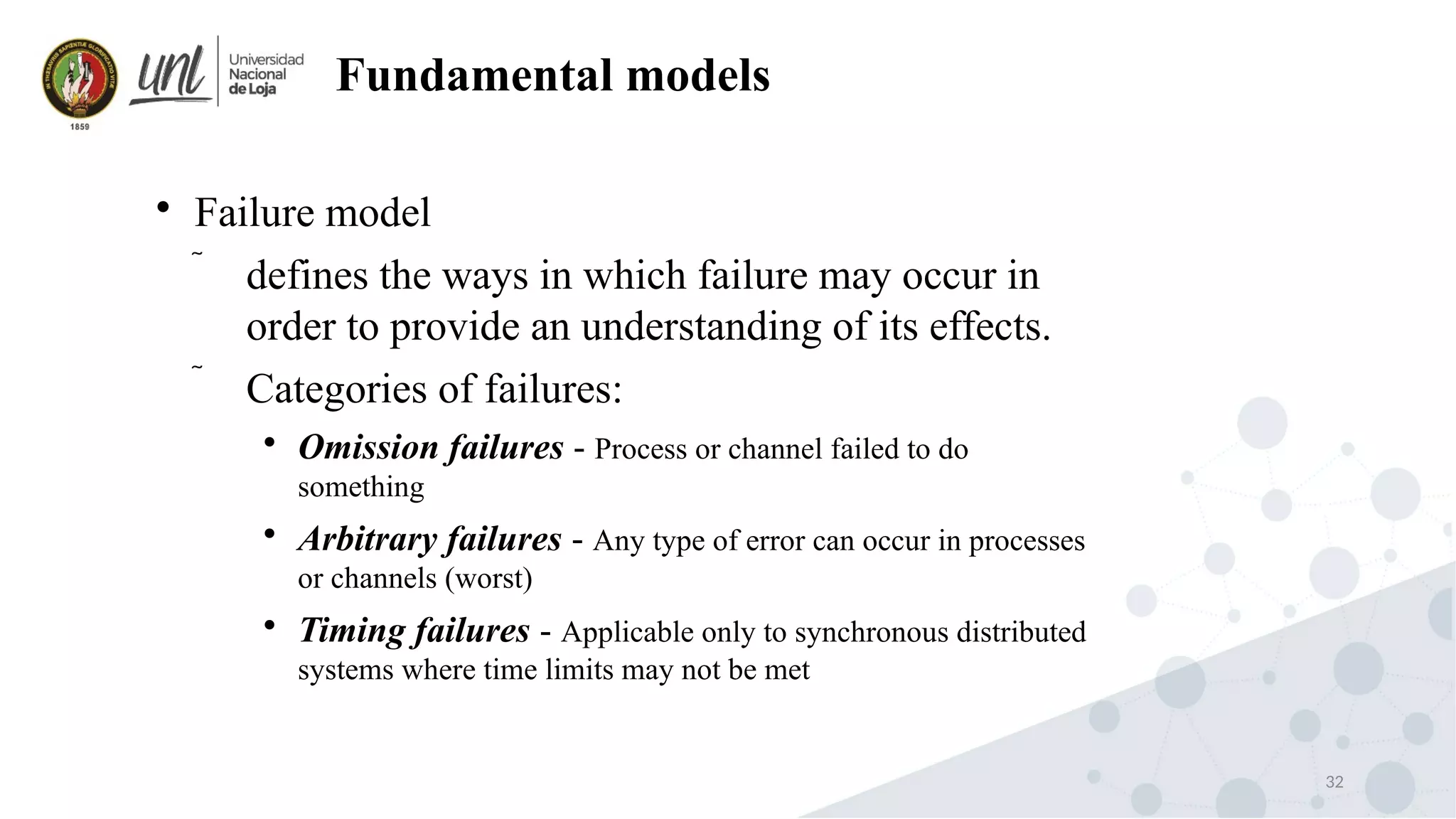
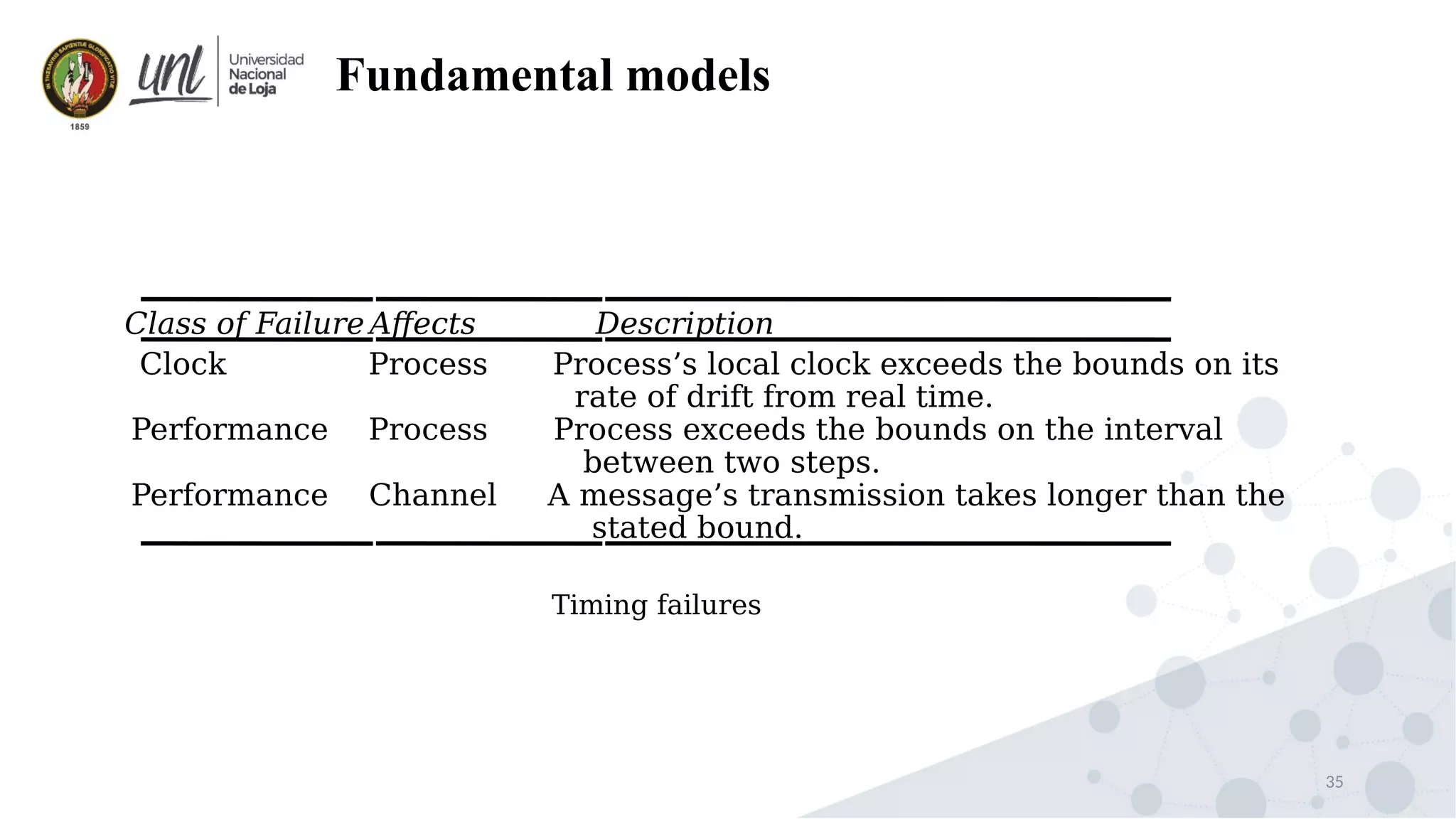
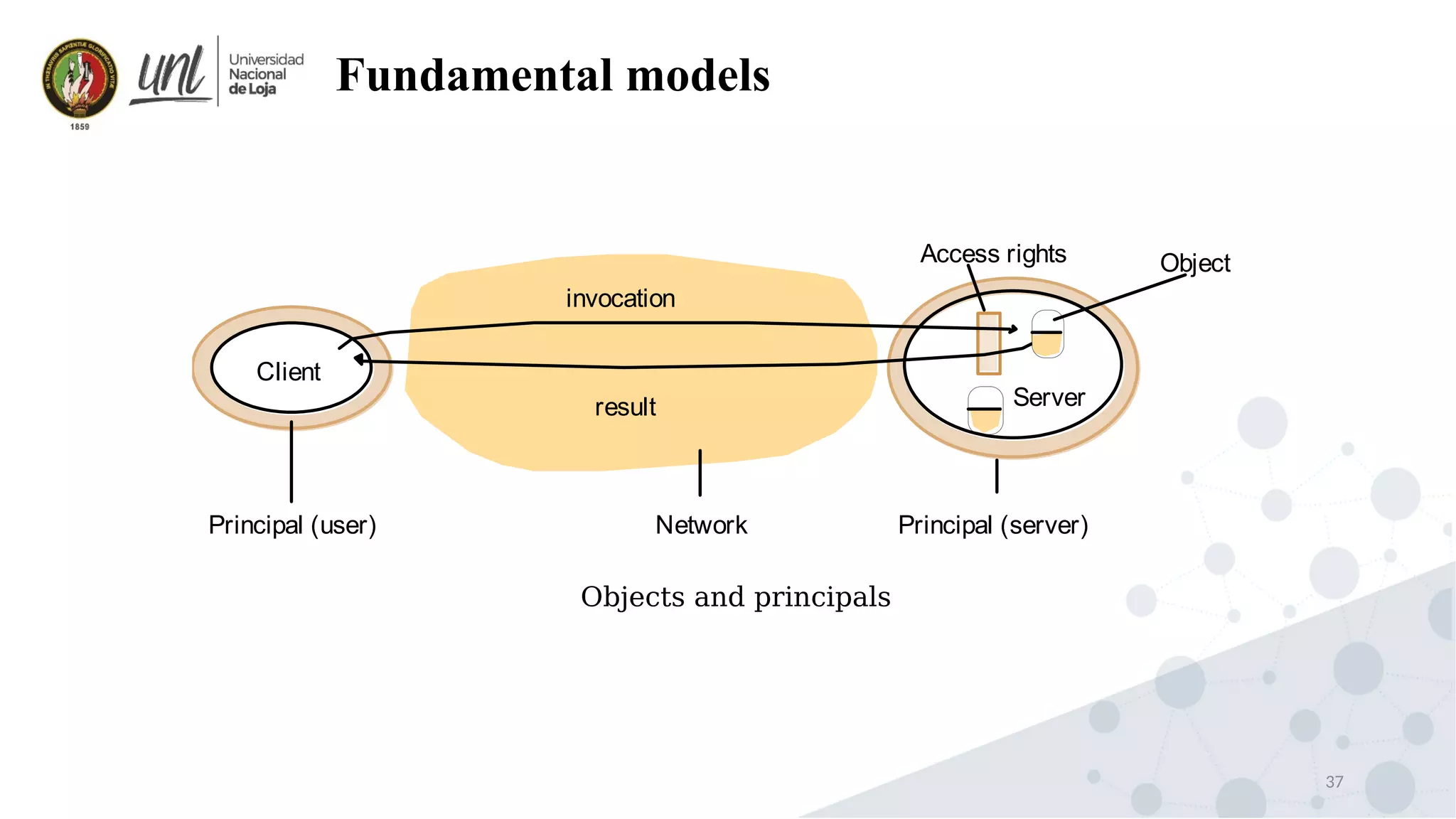
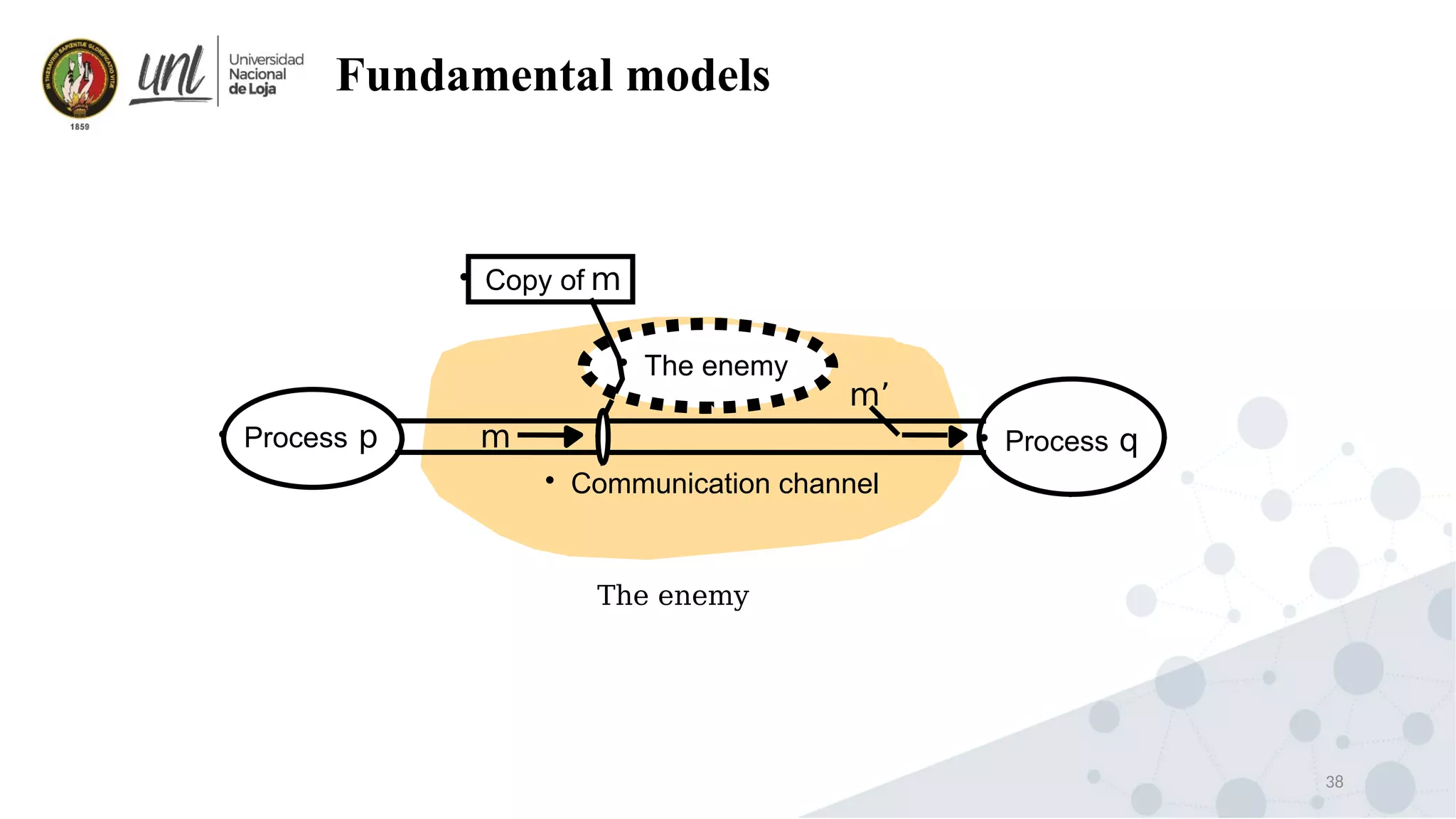
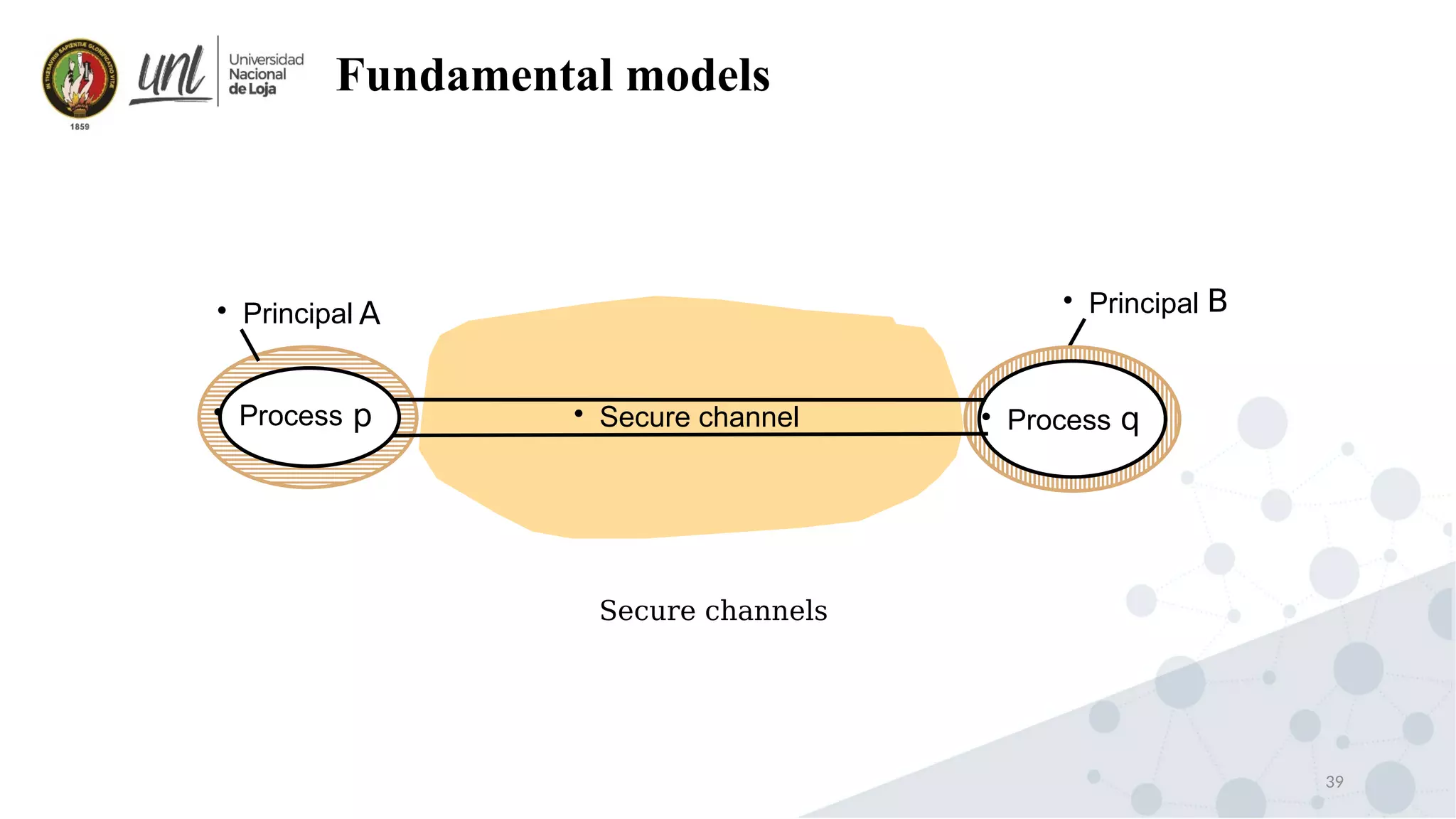
Distributed system design can be explained through three models: physical, architectural, and fundamental models. Physical models describe the hardware composition and network connections. Architectural models define the computational tasks, communication, and placement of elements. Fundamental models describe interactions, failures, and security at an abstract level.