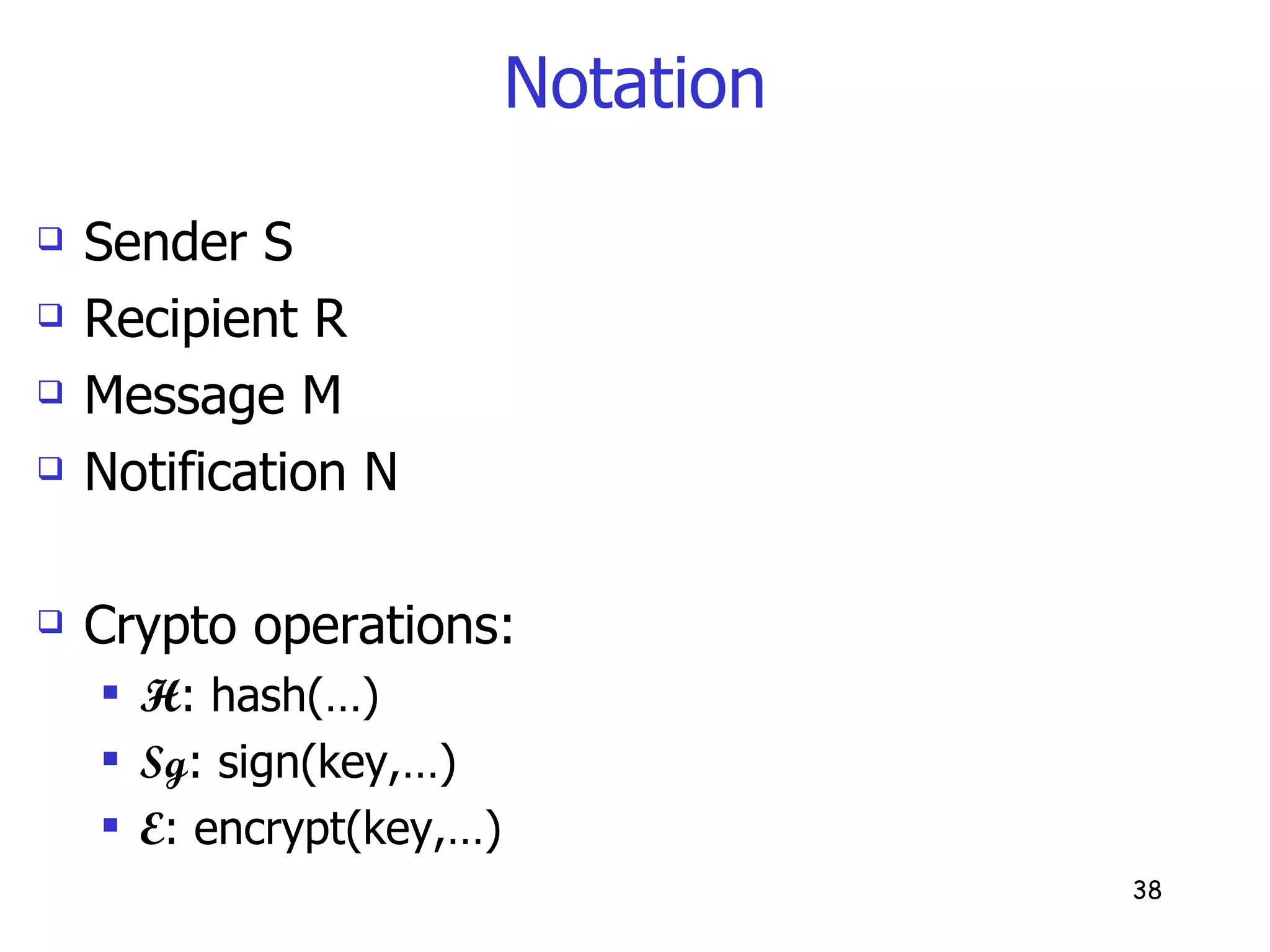
SureMail is a notification system that addresses silent email loss without modifying the email delivery infrastructure. It works by having senders post notifications to a decentralized overlay in addition to sending emails. Intended recipients periodically download notifications to check for missing emails. The system aims to protect user privacy, prevent notification spam, and authenticate senders using a reply-based shared secret between correspondents.

![Silent Email Loss Silent email loss: email “vanishes” without sender/recipient knowledge missed opportunities, misunderstanding, or worse Nontrivial problem anecdotal evidence measurement studies 0.69% loss rate [LM 04] 0.1-5% loss rate [AB 05] commercial offerings to address the problem e.g., Pivotal Veracity, Zenprise](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-2-2048.jpg)
![HotNets air ticket confirmation “ We have sent it through again. If you do not receive it with in an hour or two, please let us know.” Funding proposal "No I never got and I never acked it… My last mail from you was [on] 3/10/2004.” IMC 2005 decision notification “ I recd reviews for one paper (#X) but not that of #Y.” IMAP server upgrade problems “ Some unanticipated migration problems occurred that may have caused some lost or delayed email.”](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-3-2048.jpg)
![Silent Email Loss Silent email loss: email “vanishes” without sender/recipient knowledge missed opportunities, misunderstanding, or worse Nontrivial problem anecdotal evidence measurement studies 0.69% loss rate [Lang & Moors 2004] 0.1-5% loss rate [Afergan & Beverly 2005] commercial offerings to address the problem e.g., Pivotal Veracity, Zenprise](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-4-2048.jpg)

![Fixing the Problem Improve the email delivery infrastructure more reliable servers e.g., cluster-based (Porcupine [Saito ’00]) server-less systems e.g., DHT-based (POST [Mislove ’03]) total switchover might be risky “ Smarter” spam filtering moving target mistakes inevitable non-content-based filtering still needed to cope with spam load](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-6-2048.jpg)

![Basic Operation Sender S Recipient R Notification server Request lost message GetNotifications Missing Items Folder [S, H (M)]](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-8-2048.jpg)







![Putting it all together Sender S Recipient R D reg = H ( H (R)) D not= H (R) Missing Items Folder Request lost message Register Verify GetNotifications H 1 (M) =H 1 (M old ) ,H 2 (M old )] [](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-18-2048.jpg)





![Anecdotes Funding proposal "No I never got and I never acked it… My last mail from you was [on] 3/10/2004.” Response to self-managing networks summit invitation "Yesterday's email did not bounce back, wonder where it is!” IMC 2005 decision notification “ I recd reviews for one paper (#X) but not that of #Y.” IMAP server upgrade problems “ Some unanticipated migration problems occurred that may have caused some lost or delayed email.”](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-24-2048.jpg)

![Putting it all together Registration: R contacts D reg = H ( H (R)) to register D reg sends R an email to set up registration secret Posting notifications: upon sending email M to R, S posts notification N to D not = H (R) N = [Encrypt( H 2 (M old ), H 1 (M)), H 1 (M old )]](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-26-2048.jpg)


![#1: Protecting the recipient’s identity Registration: R contacts D reg = H ( H (R)) to register D reg sends R an email to set up a shared secret Posting notifications: Upon sending email M to R, S posts notification N = [ H (M),S] to D not = H (R) Retrieving notifications: R presents an authenticator to D not and asks for the notifications corresponding to H (R) D not contacts D reg to verify the authenticator, before returning the notifications R checks if emails are missing and presents the corresponding S to the user](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-29-2048.jpg)

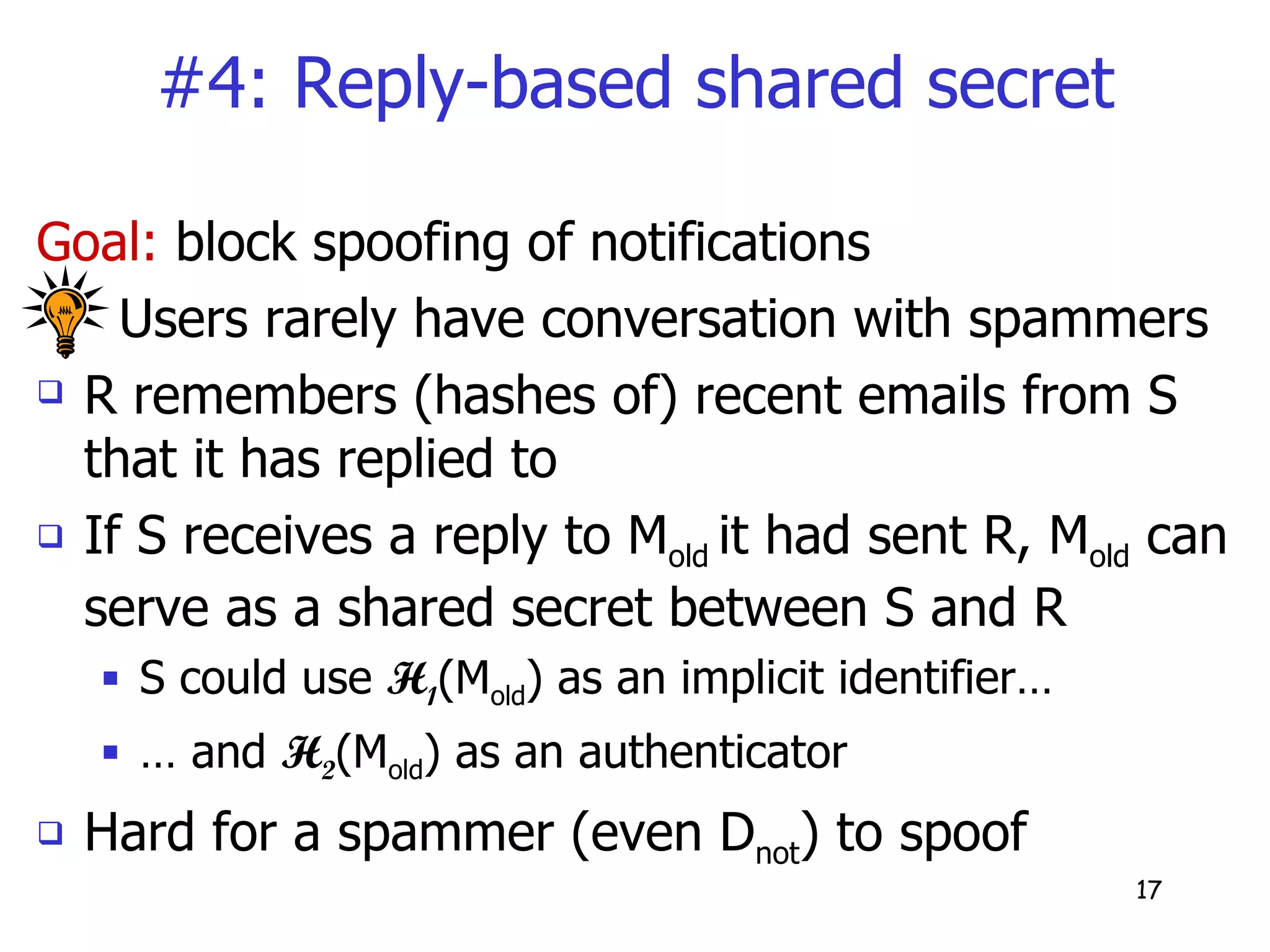
![#2: protecting the sender’s identity Goal: attackers shouldn’t be able to learn S’s identity or monitor the volume of notifications posted by S clearly N = [ H (M),S] won’t do Key idea: email-based shared secret assuming no eavesdroppers, an email M old from S to R in known only to S and R so H (M old ) could serve as an authenticator and identifier of S to R](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-31-2048.jpg)
![#2: protecting the sender’s identity Posting notifications: S’s identity is made implicit in the notification N = [ H (M), H (M old )] Retrieving notifications: R stores hashes of emails received (recently) from various senders it searches for H (M old ) to identify S if H (M old ) can’t be found, the notification is ignored](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-32-2048.jpg)

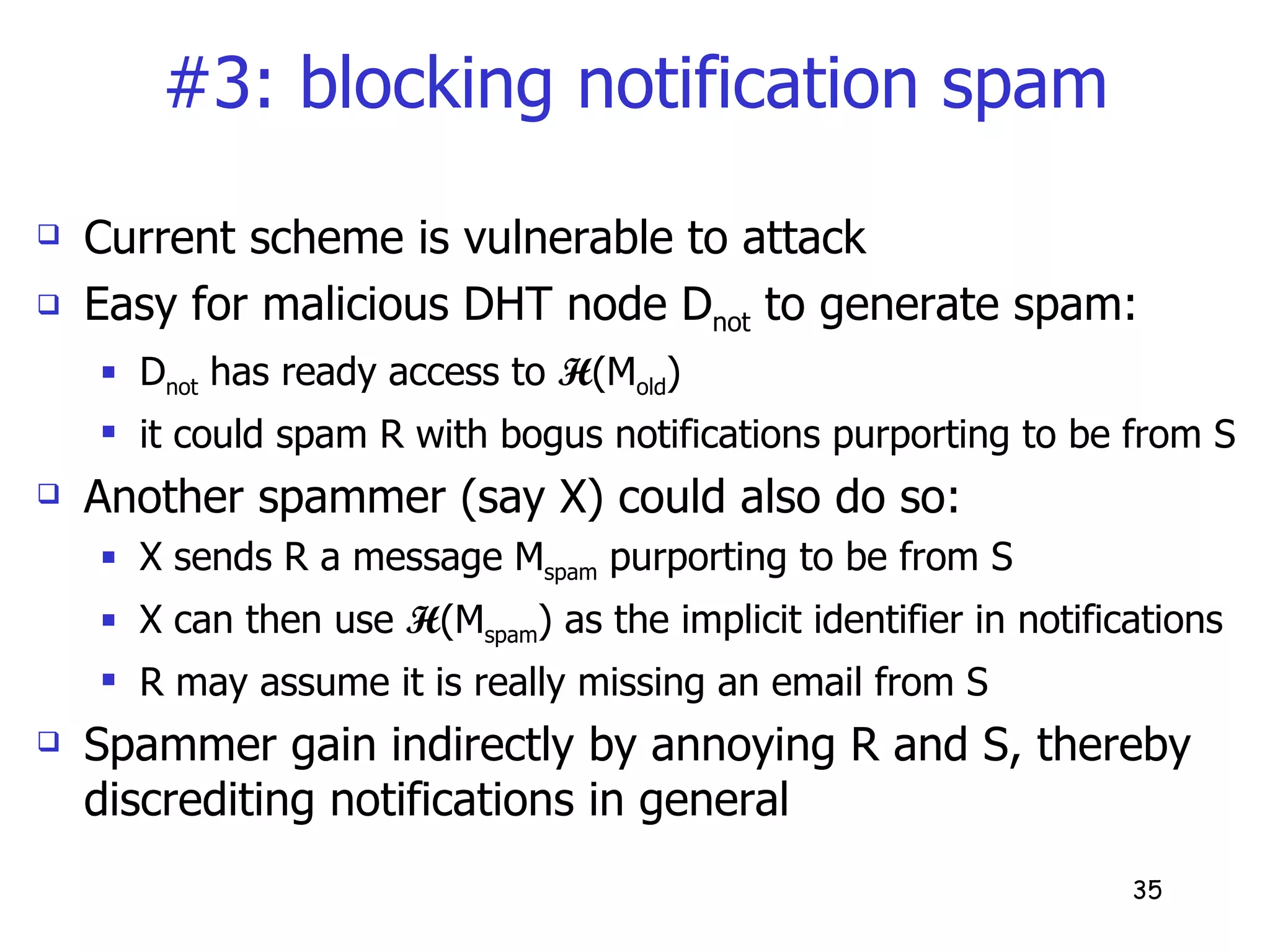
![#3: blocking notification spam Key idea: reply-based shared secret users rarely engage in conversations with spammers so if S receives a reply to a message M old that it had sent R, S could use H (M old ) as an implicit identifier hard for a spammer to spoof the identifier special construction to prevent spoofing by D not Notification format: N = [Encrypt( H ”(M old ), H (M)), H (M old )] R uses H (M old ) to identify M old and compute the encryption key H ”(M old )](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-36-2048.jpg)
![PKI-based Design R ↔ D A : RegisterRecipient(R,A) S ↔ D N : PostNotification( H (R),N) N = [ H (M), TTL, E (R pb ,S), Sg (S pv , H (M),TTL)] R ↔ D N : CheckNotification( H (R),A) D N : find D A = H ( H (R)) D N ↔ D A : AuthenticateRequest( H (R),A) D N ↔ R: ReturnNotifications() R: identify notifications corresponding to missing email and notify user if S is trusted](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-37-2048.jpg)

![Silent Email Loss Silent email loss is a non-negligible problem silent loss = no notification to sender or recipient imposes significant cost, degrades user experience Several causes spam filtering MS IT: 90% of emails discarded off the bat failures and upgrades Measurement studies 0.5-1.0% silent loss ([Lang ’04], [Afergan ’05]) ongoing measurement study at MSR quantify email delays & loss across ~25 domains](https://image.slidesharecdn.com/suremail-notification-overlay-for-email-reliability3777/75/SureMail-Notification-Overlay-for-Email-Reliability-40-2048.jpg)

